2025 is already shaping up to be a battleground for cybersecurity. With global cybercrime costs projected to reach USD 10.5T, by year’s end, the stakes have never been higher. Cybercriminals are getting smarter, using AI-driven tactics and large-scale exploits to target critical sectors. From government breaches to hospital data leaks and a surge in phishing scams, recent attacks highlight the growing financial and operational toll of cyber threats.
As cyber threats intensify, the demand for stronger defences, top-tier cybersecurity talent, and global collaboration has never been more urgent.
Here’s a look at the recent cyber developments that are shaping 2025.
Click here to download “Cyber Lessons from the Frontlines” as a PDF.
Major Security Breaches: A Costly Wake-Up Call
Cyberattacks are becoming more targeted, disruptive, and costly – impacting governments and organisations worldwide.
In Singapore, mobile wallet fraud is surging, with phishing tactics causing USD 8.9K in losses – 80% linked to Apple Pay. In the UK, security flaws in government IT systems have exposed sensitive data and infrastructure. South Africa’s government-run weather service (SAWS) was also forced offline, disrupting a critical resource for airlines, farmers, and emergency responders. Across the Atlantic, a data breach at a Georgia hospital compromised 120,000 patient records, while BayMark Health Services, the largest addiction treatment provider in the US, alerted patients to a similar breach.
What steps are governments, tech providers, and enterprises taking to protect themselves, critical infrastructure, and individuals?
Protecting Critical Infrastructure: The Digital Backbone
As global connectivity expands, securing critical infrastructure is paramount to sustaining growth, stability, and public trust.
Undersea cables, which carry much of the world’s internet traffic, are a major focus. While tech giants like Amazon, Meta, and Google are expanding these networks to boost global data speed and reliability, the need for protection is just as urgent – prompting the EU to invest nearly a billion dollars in securing them against emerging threats.
Governments and tech providers alike are stepping up. The European Commission has introduced a cybersecurity blueprint to strengthen crisis coordination, rapid response, and information sharing. Meanwhile, Microsoft is investing USD 700M in Poland’s cloud and AI infrastructure, working with the Polish National Defense to enhance cybersecurity through AI-driven strategies.
Quantifying Cyber Risk: Standardised Threat Assessment
As cyber threats grow more sophisticated, so must our ability to detect, measure, and respond to them.
A major shift in cybersecurity is underway – one that prioritises standardised threat assessment and coordinated defense.
The UK is leading the charge with a new cyber monitoring centre that will introduce a “Richter Scale” for cyberattacks, ranking threats much like earthquake magnitudes. Emerging countries are also joining in; Vietnam is strengthening its cyber defences with a new intelligence-sharing platform designed to improve coordination between the government and private sector.
By quantifying cyber risks and enhancing intelligence-sharing, these efforts are shaping global cybersecurity norms, improving response times, and building a more resilient digital ecosystem.
Beyond Defence: Proactive Measures to Combat AI-Driven Cybercrime
Cyber threats evolve faster than defences can keep up – a single click on a malicious email can lead to a breach in just 72 minutes.
With AI making cyberattacks more sophisticated, governments are taking an active role in cyber law enforcement.
Indonesia set up a cyber patrol to monitor and regulate harmful online content while also working to create a safer digital space for children. Thailand, Cambodia, and Laos are cooperating to curb cross-border scams through intelligence sharing and joint enforcement efforts.
Building Trust Online: Digital Identity Solutions
Governments are moving beyond enforcement to strengthen security with digital identity frameworks.
The EU is leading this shift with large-scale pilots for digital identity wallets, designed to offer citizens a secure, seamless way to verify credentials for services, transactions, and age-restricted content. By 2026, each EU member state will issue its own wallet, built on unified technical standards to ensure cross-border interoperability and stronger cybersecurity.
Digital identity wallets mark a major shift in data security, giving citizens greater control over their information while strengthening online trust. By securing identity verification, governments are reducing fraud and identity theft, creating a safer digital landscape.
Closing the Gap: Global Cyber Education Push
Cybersecurity education is no longer just for IT teams – it’s essential at every level, from executives to employees, to build long-term resilience.
Again, governments and tech giants alike are stepping up to bridge the skills gap and enhance cyber awareness.
Singapore is leading by example with a cyber-resilience training program for board directors, ensuring corporate leaders understand cyber risk management. AWS is investing USD 6.35M to support cybersecurity education in the UK, and Microsoft is expanding its global training efforts. The company has partnered with Kazakhstan to strengthen public sector cybersecurity and has committed to training one million South Africans in AI and cybersecurity by 2026.

The Path Forward: A Collective Responsibility
The cybersecurity landscape underscores a crucial truth: resilience can’t be built in isolation. Governments, businesses, and individuals must move past reactive measures and adopt a collective, intelligence-driven approach. As threats grow more sophisticated, so must our commitment to collaboration, vigilance, and proactive defence.
In an increasingly interconnected world, securing the digital landscape is not just necessary – it’s a shared responsibility.

Ecosystm research reveals a stark reality: 75% of technology leaders in Financial Services anticipate data breaches.
Given the sector’s regulatory environment, data breaches carry substantial financial implications, emphasising the critical importance of giving precedence to cybersecurity. This is compelling a fresh cyber strategy focused on early threat detection and reduction of attack impact.
Read on to find out how tech leaders are building a culture of cyber-resilience, re-evaluating their cyber policies, and adopting technologies that keep them one step ahead of their adversaries.
Download ‘Cyber-Resilience in Finance: People, Policy & Technology’ as a PDF

Ransomware attacks have become a real threat to organisations world-wide – SonicWall reports that there were 304.7 million attacks globally in the first half of 2021, surpassing the full-year total for 2020. Organisations today are challenged with having the right cybersecurity measure in place, with cyber-attacks considered an inevitability.
This also challenges tech providers and cybersecurity vendors, as they have to constantly evolve their security offerings to protect their client organisations.
Ecosystm analysts, Alan Hesketh, Andrew Milroy and Claus Mortensen discuss the challenges tech providers face and how they are evolving their capabilities – organically, through acquisitions (Microsoft) and through partnerships (Google).

Ecosystm recently partnered with Asavie to conduct a study into the opportunity and outlook for the “Branch of One”. One of the challenges was actually defining what the Branch of One is. Here’s what we came up with:
Branch of One enables Office Anywhere by delivering secure, frictionless access to all business resources, with full mobility – meeting the security and manageability requirements of CIOs and CISOs.
Basically it is all the data and systems you need to get your job done, in your pocket. Secure. Easy to manage.
What I really like about the idea is that it describes what business is trying to achieve and it gives a common language and outcome for IT and business leaders. Consider all the things that IT and security teams need to do to enable access to applications and data in remote branches – from connectivity to security to data and system access. Often it takes days, weeks or months to open a new office or branch, or to provision a new retail store. Now, imagine having the ability to roll out all of these systems and services in seconds. To a single user or to thousands. Without consideration for location. Business leaders will understand this benefits and will support it.
It also has the opportunity to help nearly every business today. Of the 1005 businesses we interviewed across the globe in our Global CxO Study 2020, 44% admitted to suffering cyber-attack incidents during COVID-19 due to employees working from home – and over half of these attacks were on mobile devices. Compromised devices were the number one target for cyber-attacks in 2020.
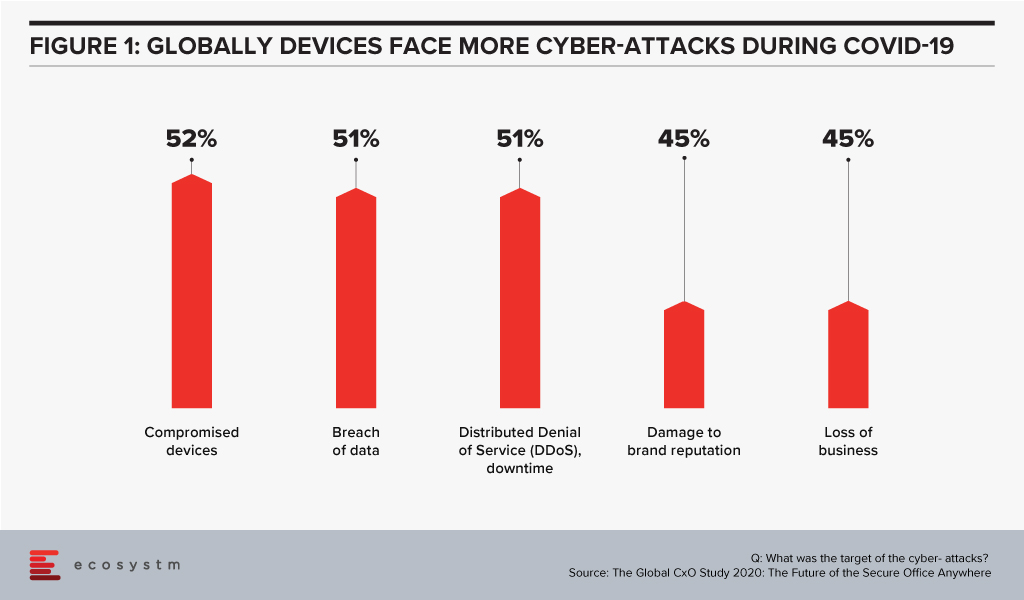
Businesses need a new way to manage the devices and applications of their remote employees. They need to be able to extend the benefits of the WAN to them without the downsides of VPNs. Every business we interviewed saw benefits of bringing devices, locations and offices inside the WAN. Turning every device and office into a Branch of One.
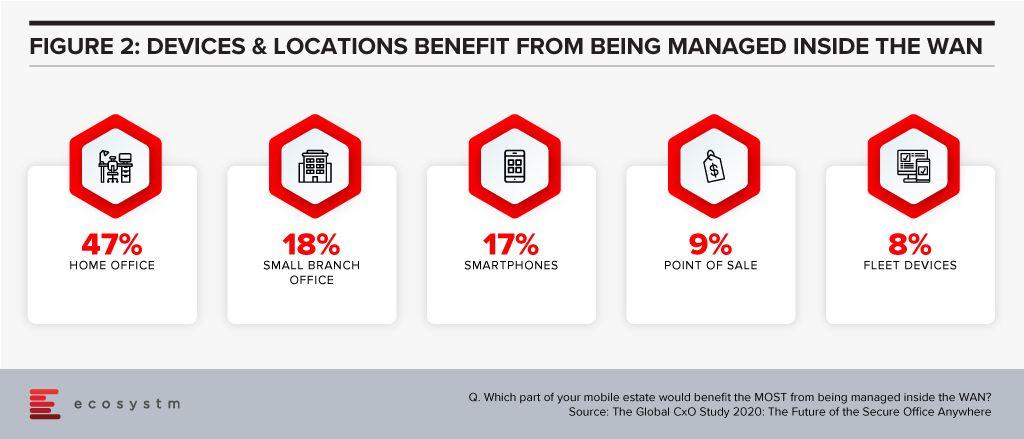
A few security and network technologies have promised this capability – SDNs can offer a similar service, but they require client software to be installed. 78% of businesses we interviewed are using VPNs to bring devices inside the WAN – but again, they require client software, and can be inconsistent (and insecure!) on mobile devices.
Companies that embrace the Branch of One can provision new users in a few clicks. No software to install, no cables to connect, no hardware to provision – it makes life easier for technology and security professionals. The Branch of One gives your employees the systems and data they need to get their job done – delivered securely across the mobile network.
Download the report based on ‘The Global CxO Study 2020: The Future of the Secure Office Anywhere’, conducted by Ecosystm on behalf of Asavie. The report presents the key findings of the study and analyses the market perceptions of Office Anywhere and the need for a ‘Branch of One’, which will be the foundation of enterprise mobile security in the future.

Privileged accounts are gold mines for malicious actors. They offer persistent access to valuable corporate resources and pose massive risk to organisations. Once authentication has been breached and credentials are obtained by an adversary, moving laterally, and accessing multiple resources, is too easy.
The most privileged access is not always granted to the most senior employees. Administrative and personal assistants often have the greatest access to corporate resources. They are low hanging fruit for attackers -usually among the least well-prepared to deal with breaches or attacks like phishing emails. Privilege promiscuity like this creates challenges around not only Privileged Access Management (PAM), but also other digital risk controls.
Scaling PAM is Complex
Think of PAM as a way of stopping people from abusing privilege. Imagine that you need a handyman for some repairs. The handyman is granted access to your house through the front door and is guided to the kitchen. The handyman is monitored and exits the kitchen as soon as the job is completed. The handyman then leaves the house. The worst outcome is a shoddy job or perhaps the theft of small pieces of cutlery or a few fridge magnets. In other words, the handyman’s access has been managed and privilege was only granted as needed. This is good PAM.
Bad PAM is a scenario where the handyman is granted access to your home and nobody is in to monitor the handyman’s activities. The handyman could be honest do the job and then depart. But, there is a significant risk that the handyman takes advantage of the privileged access granted. The handyman has access to all the rooms in the house and all the items in the house. The handyman can invite other people into the house, including a friend who can remove and copy data from all resident hard drives in the house. This access enables the handyman to steal credit cards, jewelry, PII, credentials and more.
Now, imagine that there are hundreds of handymen and other workers entering and exiting a house at varying times and for different purposes – each with distinct tasks and a need for access to different rooms and items, 24/7. This is the challenge faced by security operations – there are often hundreds or thousands of users with differing privileges to manage. Organisations are struggling to keep up with the sheer scale of the PAM challenge with all its moving parts. PAM also needs to consider the ongoing change in roles and responsibilities of staff, which directly impacts requirements for privileged access.
Privilege Sprawl and Privilege Overkill is Rife In Asia
Once an adversary breaches a privileged account, and is able to move laterally, they can access email accounts, intellectual property, employee data, customer data, sales data, invoicing approvals, expense approvals, and many other systems and processes. In addition to being exposed to short-term financial risk, an organisation also faces operational, legal, and reputational risk from such a breach. The attacker can unload ransomware or other malware to sabotage operations. They can steal PII and credentials, to sell them or use them to cause reputational and legal damage to the victim.
Privilege sprawl is common in Asian organisations. IT departments often struggle to keep track of who has access to what. Worse, IT departments typically over-provision their stakeholders with access. They are usually more concerned with getting positive feedback for the IT resources they provide from the business, than in aggressive risk management.
Specialised PAM solutions have emerged to mitigate the risk associated with unauthorised account access. The term privileged access management is a bit of misnomer. Today’s organisations need to ensure that all access is managed correctly. With an expanding number of devices, bots and people accessing corporate resources, the scope of PAM solutions is much broader than managing privileged accounts alone.
A Zero Trust Approach to PAM is Necessary
Organisations need to take a zero trust approach to PAM. Just-in-time access (JITA) needs to become the norm, ending persistent privileged access. Access needs to be granted for the minimum amount of time with the minimum rights required, ending privilege promiscuity. Zero standing privilege needs to be the default state of systems and networks. Access must be denied as soon as necessary work is complete and only provisioned when needed again. This approach is needed for risk management but few organisations in Asia have achieved this goal. The sheer number of moving parts involved in such an exercise makes it particularly onerous – this is where PAM solutions play a role.
Here’s a list of Ecosystm’s top five predictions that will affect enterprises, cybersecurity leaders, remote workers and the security posture in 2021. Signup for Free to download the report.

Public sector organisations are looking at 2021 as the year where they either hobble back to normalcy or implement their successful pilots (that were honed under tremendous pressure). Ecosystm research finds that 60% of government agencies are looking at 2021 as the year they make a recovery to normal – or the normal that finally emerges. The path to recovery will be technology-driven, and this time they will look at scalability and data-driven intelligence.
Ecosystm Advisors Alan Hesketh, Mike Zamora and Sash Mukherjee present the top 5 Ecosystm predictions for Cities of the Future in 2021. This is a summary of our Cities of the Future predictions – the full report (including the implications) is available to download for free on the Ecosystm platform here.
The Top 5 Cities of the Future Trends for 2021
#1 Cities Will Re-start Their Transformation Journey by Taking Stock
In 2021 the first thing that cities will do is introspect and reassess. There have been a lot of abrupt policy shifts, people changes, and technology deployments. Most have been ad-hoc, without the benefit of strategy planning, but many of the services that cities provide have been transformed completely. Government agencies in cities have seen rapid tech adoption, changes in their business processes and in the mindset of how their employees – many who were at the frontline of the crisis – provide citizen services.
Technology investments, in most cases, took on an unexpected trajectory and agencies will find that they have digressed from their technology and transformation roadmap. This also provides an opportunity, as many solutions would have gone through an initial ‘proof-of-concept’ without the formal rigours and protocols. Many of these will be adopted for longer term applications. In 2021, they will retain the same technology priorities as 2020, but consolidate and strengthen on their spend.
#2 Cities Will be Instrumented Using Intelligent Edge Devices
The capabilities of edge devices continue to increase dramatically, while costs decline. This reduces the barriers to entry for cities to collect and analyse significantly more data about the city and its people. Edge devices move computational power and data storage as close to the point of usage as possible to provide good performance. Devices range from battery powered IoT devices for data collection through to devices such as smart CCTV cameras with embedded pattern recognition software.
Cities will develop many use cases for intelligent edge devices. These uses will range from enhancing old assets using newer approaches to data collection – through to accelerating the speed and quality of the build of a new asset. The move to data-driven maintenance and decision-making will improve outcomes.
#3 COVID-19 Will Impact City Design
The world has received a powerful reminder of the vulnerability of densely populated cities, and the importance of planning and regulating public health. COVID-19 will continue to have an impact on city design in 2021.
A critical activity in controlling the pandemic in this environment is the test-and-trace capabilities of the local public health authorities. Technology to provide automated, accurate, contact tracing to replace manual efforts is now available. Scanning of QR codes at locations visited is proving to be the most widely adopted approach. The willingness of citizens to track their travels will be a crucial aid in managing the spread of COVID-19.
Early detection of new disease outbreaks, or other high-risk environmental events, is essential to minimise harm. Intelligent edge devices that detect the presence of viruses will become crucial tools in a city’s defence.
Intelligent edge devices will also play a role in managing building ventilation. Well-ventilated spaces are an important factor in controlling virus transmission. But a limited number of buildings have ventilation systems that are capable of meeting those requirements. Property owners will begin to refit their facilities to provide better air movement.
#4 Technology Vendors Will Emerge as the Conductors of Cities of the Future
The built environment comprises not only of the physical building, but also the space around the buildings and building operations. The real estate developer/investor owns the building – the urban fabric, the relationship of buildings to each other, the common space and the common services provided to the city, is owned by the City. The question is who will coordinate the players, e.g. business, citizens, government and the built environment. Ideally the government should be the conductor. However, they may not have sufficient experience or knowledge to properly implement this role. This means a capable and knowledgeable neutral consultant will at least initially fill this role. There is an opportunity for a technology vendor to fill that consulting role and impact the city fabric. This enhanced city environment will be requested by the Citizen, driven by the City, and guided by Technology Vendors. 2021 will see leading technology vendors working very closely with cities.
#5 Compliance Will be at the Core of Citizen Engagement Initiatives
Many Smart Cities have long focused on online services – over the last couple of years mobile apps have further improved citizen services. In 2020, the pandemic challenged government agencies to continue to provide services to citizens who were housebound and had become more digital savvy almost overnight. And many cities were able to scale up to fulfill citizen expectations.
However, in 2021 there will be a need to re-evaluate measures that were implemented this year – and one area that will be top priority for public sector agencies is compliance, security and privacy.
The key drivers for this renewed focus on security and privacy are:
- The need to temper the focus of ‘service delivery at any cost’ and further remind agencies and employees that security and privacy must comply with standard to allow the use of government data.
- The rise of cyberattacks that target not only essential infrastructure, but also individual citizens and small and medium enterprises (SMEs).
- The rise of app adoption by city agencies – many that have been developed by third parties. It will become essential to evaluate their compliance to security and privacy requirements.

In recent times, there appears to be a shift in motive for cyber-attacks – along with common data theft, there is a proliferation of attacks aimed at the business interruption and physical incapacitation of business operations. We have witnessed an alarming increase in high-profile attacks on manufacturing businesses and critical infrastructure providers, globally.
This appears to be a global phenomenon. Honda manufacturing plants went offline in June after a cyber-attack compromised some of the Japanese automaker’s facilities. The same pattern emerged in a separate attack at the same time targeting Edesur S.A., a company belonging to the Enel Group that confirmed its internal IT network was disrupted due to a ransomware attack, which was caught by antivirus software before the malware could infect. Both companies had machines with Internet-accessible remote desktop servers, which is a favorite infection method among attackers nowadays. One of Australia’s largest brewers, Lion also faced a ransomware outbreak, last month. In Israel, it was reported that a cyber-attack very nearly poisoned the water supply with the attackers attempting to overload the water system with chlorine, and in recent days, a fire and explosion at an Iranian nuclear plant is suspected of being caused by cyber-attack.
These attacks highlight the need for appropriate investments in cybersecurity by companies and municipalities that own or operate critical infrastructure, properties (including places of public congregation, retailers and others) that are rapidly deploying a suite of operational technologies, and businesses in the manufacturing sector.
Operational Technology (OT) is the backbone of modern industrial operations and is a network of multiple computing systems that perform operations including production line management, operations control and industrial monitoring. OT can further include specific computing systems like industrial control systems (ICS) which is a collection of control systems used to operate and/or automate industrial processes. There are several types of ICSs, the most common of which are Supervisory Control and Data Acquisition (SCADA) systems, and Distributed Control Systems (DCS). With such industrial systems and smart end-user products connected by a common network, several vulnerabilities may appear.
In OT security, the focus is much less on information, but more on the industrial process that technology controls. Hence, availability and integrity are often more important than confidentiality. Any organisation employing OT should employ continual risk-based assessments of their cybersecurity posture to prioritise and tailor recommended guidelines and solutions to fit specific security, business, and operational requirements.
Why is OT More Vulnerable?
OT systems are versatile and can be found in all kinds of industrial settings and infrastructures like smart buildings, oil and gas, energy generation/distribution, mining, wastewater treatment/distribution, manufacturing, food production, consumer devices and transport. In fact, almost every business in 2020 has an element of IoT within their operations.
A big issue with OT is that a lot of the technology in place is over 20 years old and therefore was not designed to provide the security capabilities required to face cyber threats in 2020. Legacy technology often requires legacy hardware and software to support it – much of which is the end of life and unsupported by the vendors (for example, consider SCADA systems still reliant on Windows NT or older Unix based systems, which have not been supported by their vendors for many years).
OT systems have also been damaged as unintended side effects of problems starting in corporate networks that took advantage of increasing connectivity, proving clearly that the standard PCs that now form part of a typical organisation’s IT environment are in turn used to manage OT systems and become a major vector for such cyber-attacks.
When it comes to OT, safety and reliability are the primary concerns as attackers aim to disrupt the critical services industry and their customers rely upon them. Given the increasing propensity of connecting OT systems with corporate networks for ease of management and the growing use of IoT systems, the likelihood of such systems being affected by vulnerabilities exploitable over the network is increasing exponentially.
For almost every business – not just critical infrastructure providers – most technologies we deploy include connectivity to the internet. Not knowing what systems and external access to these systems that your business is introducing in its everyday technology investment create significant risks to the broader business operations.
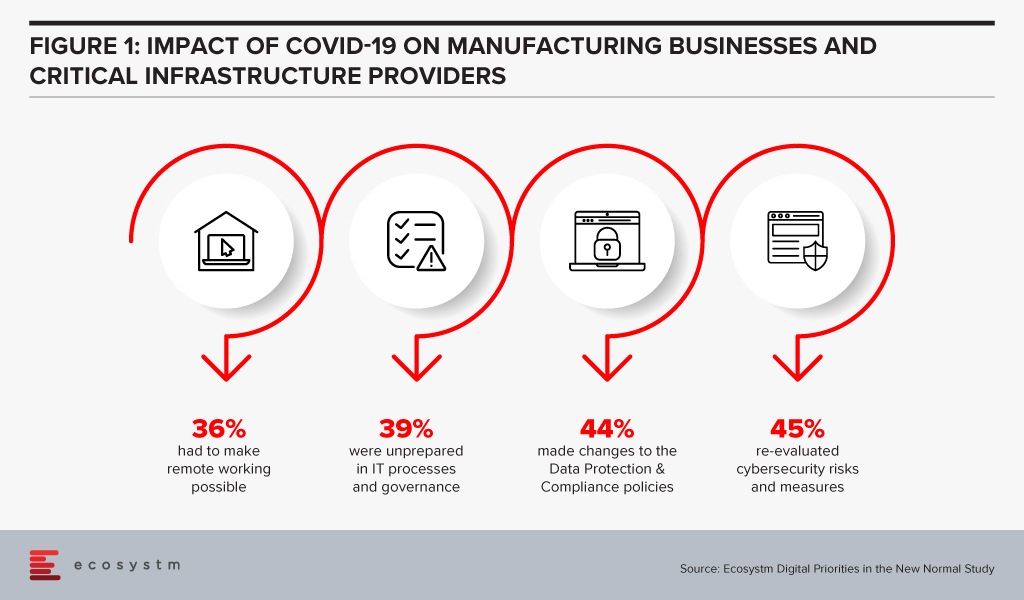
Manufacturing businesses and critical infrastructure providers realise that there is need to re-evaluate their cybersecurity measures, in the wake of the COVID-19 crisis, according to the findings of the Ecosystm’s ongoing “Digital Priorities in the New Normal” study (Figure 1).
But these measures may not be sufficient, as indicated by the slew of cyber-attacks on these organisations.
Why are these attacks successful?
There are several reasons why OT attacks are successful:
- Unauthorised access to internet-facing systems (e.g. deploying an IoT with the default username and password)
- Introduction of a compromised device (e.g. USB stick) to the environment that infects the network (often employee action)
- Exploitation of zero-day vulnerabilities in control devices and software
- Propagated malware infections within isolated computer networks (i.e. The attacker can place a receiving device to make contact over a channel that can propagate across the isolated network)
- SQL injection via exploitation of web application vulnerabilities
- Network scanning and probing
- Lateral movement (i.e. inadequate segmentation which results in attackers being able to move between systems, groups of systems, network zones and even geographical locations.)
How can they be prevented?
The mitigation cannot rely solely on the organisation building security around the deployment nor can it be a reactive approach to fixing vulnerabilities in production, as they are identified. It begins with the OT vendors building security within; however, as with most IT systems and applications, this will evolve over time. For example, there is an initiative in Australia – driven by the IoT Alliance Australia (IOTAA) – to introduce a ‘Trust Mark’ for IoT devices that pass a certification process for security and privacy in product development. This is targeted to launch in September 2020 but could take many years to gain real traction. Thus, for the foreseeable future, the best operational outcomes must be planned and managed by the consumers of the technologies.
Here are the best practices to reduce exploitable IoT weaknesses and attacks occurring in your business:
- Maintain an accurate inventory of Operational Systems and eliminate any exposure of these systems to external networks
- Establish clear roles and responsibilities for your organisation and your vendors, to ensure cybersecurity risk is being addressed and managed throughout the OT lifecycle
- Implement network segmentation and apply firewalls between critical networks and systems.
- Use secure remote access methods
- Establish Role-Based Access Controls (RBAC) and implement system logging
- Use only strong passwords, change default passwords, and consider other access controls (especially for any elevated privileges) such as multi-factor authentication, privileged access management solutions, etc.
- Establish threat intelligence feeds from your OT vendors and security vendors to ensure you remain abreast of new vulnerabilities, software/firmware patches and threats targeting systems you employ
- Develop and enforce policies on mobile devices, including strict device controls for any device connecting to OT systems or network zones
- Implement an employee cybersecurity training program
- Establish and maintain rigorous testing and patching program including vulnerability assessment and penetration testing
- Implement measures for detecting compromises and develop a cybersecurity incident response plan with a specific focus on responding to a disruptive attack on your OT environment
- Maintain an up-to-date Business Continuity Plan that can be deployed rapidly in response to a significant disruption

Last week, the Australia government joined other countries in the Asia Pacific region in highlighting the growth of attack surface in the midst of the COVID-19 pandemic.
In our recently launched study Digital Priorities in the New Normal, we find that 87% of organisations in the Asia Pacific have increased investments in one or more cybersecurity solutions. However, this has to be backed by a reassessment of organisations’ risk positions and a re-evaluation of data protection and compliance policies.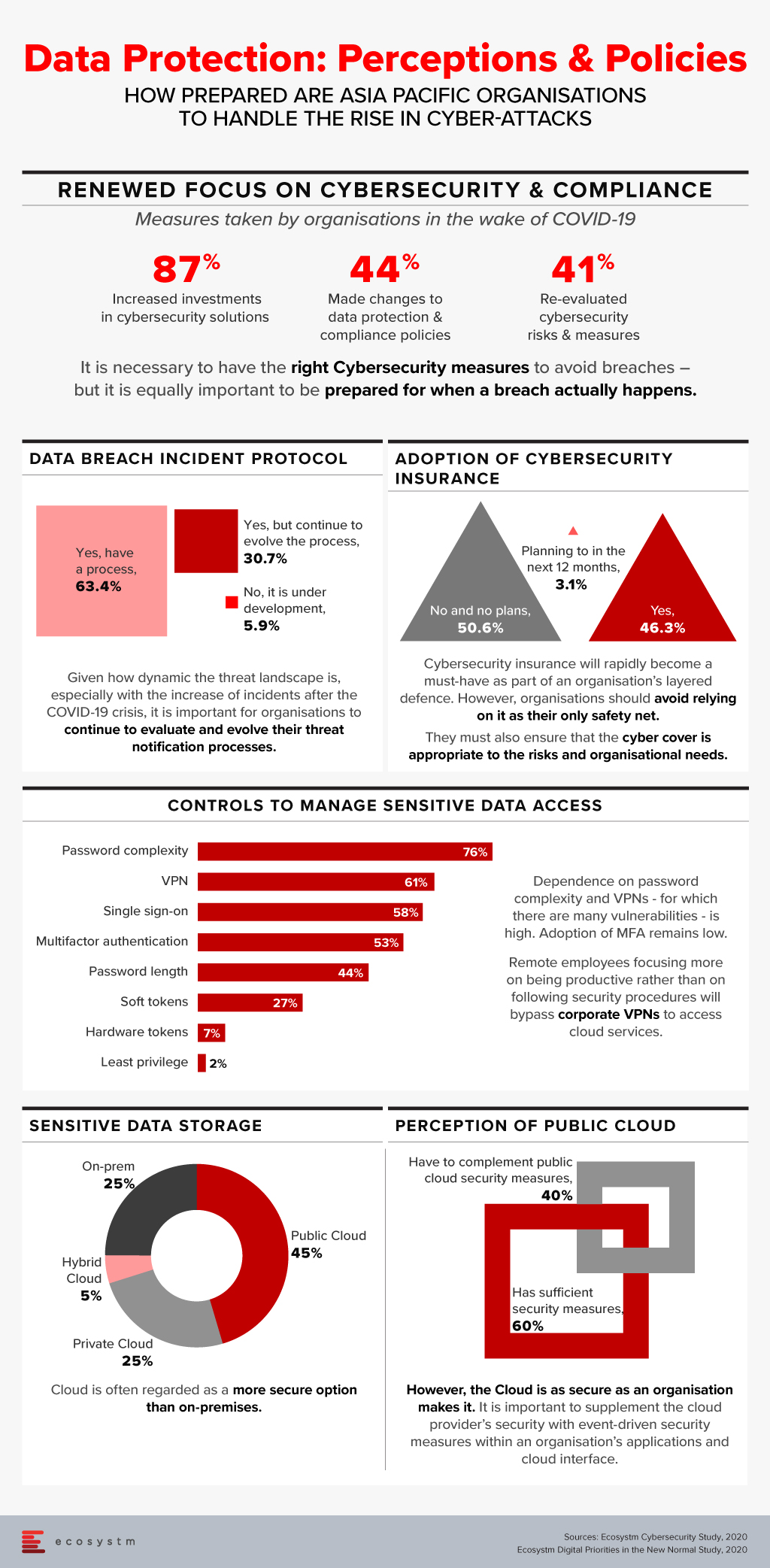

Last week, the Australia Government announced that they have been monitoring persistent and increasing volumes of cyber-attacks by a foreign state-based actor on both government and private sector businesses. The Australian Cyber Security Centre (ACSC) reported that most of the attacks make use of existing open-source tools and packages, which ACSC has dubbed as “copy-paste compromises”. The attackers are also using other methods to exploit such as spear phishing, sending malicious files and using various websites to harvest passwords and more, to exploit systems.
Cybercrime has been escalating in other parts of the world as well. The World Health Organisation (WHO) witnessed a dramatic increase in cyber-attacks directed with scammers impersonating WHO personnel’s official emails targeting the public. The National Cyber Security Centre (NCSC) in the UK alerted the country’s educational institutions and scientific facilities on increased cyber-attacks attempting to steal research associated with the coronavirus. Earlier this month, the Singapore Computer Emergency Response Team (SingCERT) issued an advisory on potential phishing campaigns targeting six countries, including Singapore that exploit government support initiatives for businesses and individuals in the wake of the COVID-19 crisis.
Such announcements are a timely reminder to government agencies and private organisations to implement the right cybersecurity measures against the backdrop of an increased attack surface. These cyber attacks can have business impacts such as theft of business data and destruction or impairment to financial data, creating extended business interruptions. The ramifications can be far-reaching including financial and reputational loss, compliance breaches and potentially even legal action.
A Rise in Spear-Phishing
In Australia, we’re seeing attackers targeting internet-facing infrastructure relating to vulnerabilities in Citrix, Windows IIS web server, Microsoft Sharepoint, and Telerik UI.
Where these attacks fail, they are moving to spear-phishing attacks. Spear phishing is most commonly an email or SMS scam targeted towards a specific individual or organisation but can be delivered to a target via any number of electronic communication mediums. In the spear-phishing emails, the attacker attaches files or includes links to a variety of destinations that include:
- Credential harvesting sites. These genuine-looking but fake web sites prompt targets to enter username and password. Once the gullible target provides the credentials, these are then stored in the attackers’ database and are used to launch credential-based attacks against the organisation’s IT infrastructure and applications.
- Malicious files. These file attachments to emails look legitimate but once downloaded, they execute a malicious malware on the target device. Common file types are .doc, .docx, .xls, .xlsx, .ppt, .pptx, .jpg, .jpeg, .gif, .mpg, .mp4, .wav
- OAuth Token Theft. OAuth is commonly used on the internet to authenticate a user to a wide variety of other platforms. This attack technique uses OAuth tokens generated by a platform and shares with other platforms. An example of this is a website that asks users to authenticate using their Facebook or Google accounts in order to use its own services. Faulty implementation of OAuth renders such integration to cyber-attacks.
- Link Shimming. The technique includes using email tracking services to launch an attack. The attackers send fake emails with valid looking links and images inside, using email tracking services. Once the user receives the email, it tracks the actions related to opening the email and clicking on the links. Such tracking services can reveal when the email was opened, location data, device used, links clicked, and IP addresses used. The links once clicked-on, can in- turn, lead to malicious software being stealthily downloaded on the target system and/or luring the user for credential harvesting.
How do you safeguard against Cyber-Attacks?
The most common vectors for such cyber-attacks are lack of user awareness AND/OR exploitable internet-facing systems and applications. Unpatched or out-of-support internet-facing systems, application or system misconfiguration, inadequate or poorly maintained device security controls and weak threat detection and response programs, compound the threat to your organisation.
Governments across the world are coming up with advisories and guidelines to spread cybersecurity awareness and prevent threats and attacks. ACSC’s Australian Signals Directorates ‘Essential 8’ are effective mitigations for a large majority of present-day attacks. There were also guidelines published earlier this year, specifically with the COVID-19 crisis in mind. The Cyber Security Agency in Singapore (CSA) promotes the ‘Go Safe Online’ campaign that provides regular guidance and best practices on cybersecurity measures.
Ecosystm’s ongoing “Digital Priorities in the New Normal” study evaluates the impact of the COVID-19 pandemic on organisations, and how digital priorities are being initiated or aligned to adapt to the New Normal that has emerged. 41% of organisations in Asia Pacific re-evaluated cybersecurity risks and measures, in the wake of the pandemic. Identity & Access Management (IDAM), Data Security and Threat Analytics & Intelligence saw increased investments in many organisations in the region (Figure 1).
However, technology implementation has to be backed by a rigorous process that constantly evaluates the organisation’s risk positions. The following preventive measures will help you address the risks to your organisation:
- Conduct regular user awareness training on common cyber threats
- Conduct regular phishing tests to check user awareness level
- Patch the internet-facing products as recommended by their vendors
- Establish baseline security standards for applications and systems
- Apply multi-factor authentication to access critical applications and systems – especially internet-facing and SaaS products widely used in the organisation like O365
- Follow regular vulnerability scanning and remediation regimes
- Conduct regular penetration testing on internet-facing applications and systems
- Apply security settings on endpoints and internet gateways that disallow download and execution of files from unfamiliar sources
- Maintain an active threat detection and response program that provides for intrusion detection, integrity checks, user and system behaviour monitoring and tools to maintain visibility of potential attacks and incidents – e.g Security Information & Event Monitoring (SIEM) tools
- Consider managed services such as Managed Threat Detection and Response delivered via security operations (SOC)
- Maintain a robust incident management program that is reviewed and tested at least annually
- Maintain a comprehensive backup regime – especially for critical data – including offsite/offline backups, and regular testing of backups for data integrity
- Restrict and monitor the usage of administrative credentials






































