The NCSC’s first ‘UK cyber survey’ published alongside global password risk list. The UK government’s cybersecurity organisation National Cyber Security Centre (NCSC) provides cybersecurity support and guidance to the private and public sectors.
The survey identified exploitable gaps in personal level security management. The study was carried out between November 2018 and January 2019 and revealed that 89% of the respondents used the Internet and only 15% acknowledged a greater understanding of personal security measures.
The NCSC also published an analysis of the 100,000 most commonly used passwords that have been accessed by third parties in global cyber breaches. The analysis shows that less than half of the respondents do are not concerned about the strength of passwords for their emails and online accounts. Some examples of commonly used passwords used by people rely on their own names, Premier League football teams, musicians and fictional characters for inspiration.
This general lack of understanding of the cyber world can be harmful to individuals but can be devastating to organisations. A chain is no stronger than its weakest link, and insecure passwords may pose a serious security risk to an organisation. “We rely on passwords in all facets of our online world, so this presents a massive risk to anyone taking short-cuts. Unfortunately, if organisations are not prepared, and allow the use of similarly insecure passwords, the flow on effect of a breach can escalate rapidly” says Alex Woerndle, Principal Analyst Cybersecurity, Ecosystm “The passwords in the above list are very weak. Even without the knowledge provided in the list, a hacker would be able to crack these passwords in seconds with the right tools. Even password complexity cannot always protect an organisation. What about a user that re-uses a complex password repeatedly, and that password is part of a breach? That puts all of the organisation’s logins at risk”.
There are some additional steps that system administrators and IT professionals need to consider when it comes to securing passwords and managing logins.
The global Ecosytsm Cybersecurity & Data Privacy study found the most common controls organisations implement to manage data access.
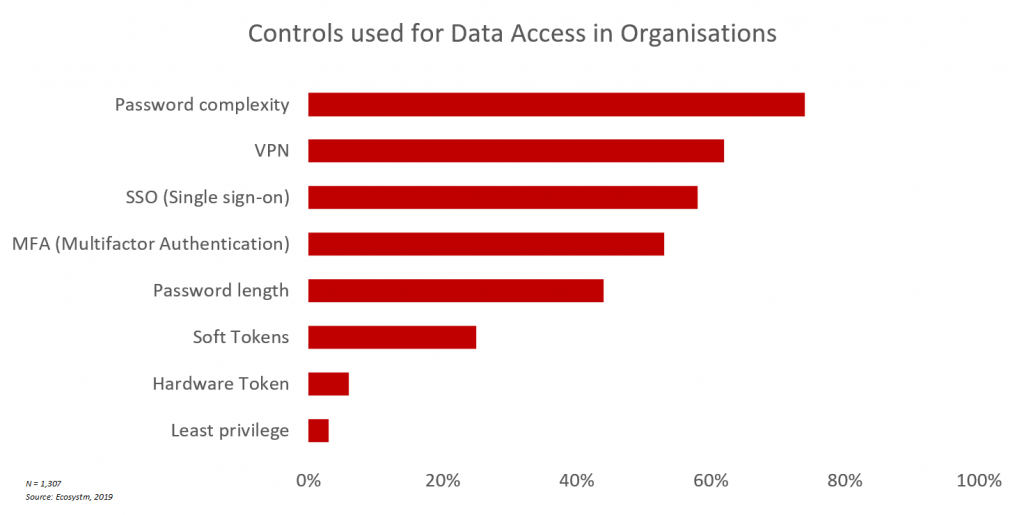
“The main step being used currently is ensuring MFA is enabled wherever possible. While not a perfect solution, it provides a circuit breaker for the most common types of attacks that would get anyone using insecure passwords into trouble” says Woerndle.
The NCSC hopes to reduce the risk of further breaches by building awareness of how attackers use easy-to-guess passwords, or those obtained from breaches and help guide developers and system administrators to protect their users. NCSC has framed guidelines covering multiple aspects of managing and maintaining security on its website.
Ultimately this problem will not go away until we find a genuine replacement for passwords. The pure scale of growth in the number of systems and applications that all users, both at a personal and on a professional level, have access to, makes password management complex and frustrating. While focusing on how to strengthen your passwords and other easy steps to avoid a cyber attack, may be a good start, it will not be enough, as long as systems and applications are dependent on passwords for better security.
The Changing Shape of Asia’s Cybersecurity Landscape
The latest in our Leaders BreakFirst series. Following the launch of our Cybersecurity and Data Privacy study, Ecosystm is delighted to share the insights from almost 7000 deployments globally.Featuring two of Ecosystm’s cybersecurity and data privacy experts on one stage- Claus Mortensen and Carl Woerndle, this session will highlight the findings from our Cybersecurity & Privacy research.



