Cybersecurity will remain an important topic of discussion on the world forum. 2020 is predicted to see an increasing number of state-sponsored cyber-attacks especially on utilities and public infrastructure. In addition, the number of AI based devices will increase which will receive specific attention from regulators for data and cybersecurity. Finally, there will be opportunities for mergers and acquisitions and investments in established cybersecurity providers to remain innovative and growing.
Here are the Top 5 Cybersecurity Trends for 2020, that we believe, will impact both businesses and consumers in 2020.
The Top 5 Cybersecurity Trends for 2020
The Top 5 Cybersecurity Trends for 2020 are drawn from the findings of the global Ecosystm Cybersecurity Study and is also based on qualitative research by Ecosystm Principal Advisors Alex Woerndle, Carl Woerndle and Claus Mortensen.
-
API Vulnerabilities will Become a Main Hacker Target
APIs grant access and provide transparency for developers – providing access and insights from both internal and external data. But they are inherently insecure. We have already seen several high-profile API breaches and announced API bugs. For example, in October 2018, Google had to shut down Google+ after an API bug exposed details for over 500,000 users.
We believe the problem will get significantly worse in 2020, with API attacks quickly becoming one of – if not the most – frequent target for hackers.
-
Operational Technology Security will Continue to Lag in 2020
Operational Technology (OT) refers to the hardware and software used to monitor and manage how devices that run on an organisation’s infrastructure perform. These devices have become smarter, remotely accessible and increasingly connected to networks. However, they were never designed with this in mind.
With organisations continuing to focus on data breaches – the investment in OT security will continue to lag. This will create a ‘security debt’ over coming years for those that do not invest in preventative controls now.
-
AI Training will Receive Attention from Regulators and the Public as a Possible Infringement of Privacy
News that Amazon’s Alexa was eavesdropping on its users, and that Apple’s Siri and Google’s Assistant, also kept recordings to help train their AI raised many concerns about how data to train AI is collected and stored. Apart from the initial consternation in the press and on social media, nothing much seems to have happened from a regulatory perspective.
2020 will be the year when AI training relying on consumer data will start to become regulated.
-
Major GDPR Fines in 2020 will Force MNCs to Invest in Security Compliance
GDPR came into effect in May 2018, but we still have not seen huge amounts of fines being issued in the EU. Only two fines were issued in 2018, while at least 17 were known to be issued in the first half of 2019, totalling about EUR 52 million. In the third quarter of 2019, at least 12 fines were issued totalling about EUR 328 million.
The trend is clear: Expect to see a magnitude of companies across EU be penalised in 2020. We also expect several fines above EUR 100 million and GDPR impacting countries outside the EU.
-
Mergers & Acquisitions will Ratchet up Significantly in 2020
The fragmented global security market consists of thousands of vendors and consultancies. Every day a swathe of new start-ups announces their ground-breaking new technology. Coupled with significant investments in tertiary education and industry certifications for a growing workforce, the next generation of cybersecurity entrepreneurs are entering with force.
We believe that this creates both threats and opportunities for established cybersecurity providers that need to remain innovative and growing. Similarly, this presents smaller or more niche cybersecurity start-ups with an avenue for funding or acquisition.
Ecosystm in partnership with SGInnovate, the government-backed organisation that promotes Deep Tech in Singapore, released a series of four reports covering areas of mutual interest: Cybersecurity, Artificial Intelligence, Cities of the Future and Healthtech. ‘Ecosystm Predicts: The Top 5 Cybersecurity Trends for 2020’ report is a part of this collaboration and is available for download from Ecosystm and SGInnovate websites.
Download Report: The top 5 Cybersecurity trends for 2020
The full findings and implications of the report ‘Ecosystm Predicts: The Top 5 Cybersecurity Trends for 2020’ are available for download from the Ecosystm platform. Signup for Free to download the report and gain insight into ‘the top 5 Cybersecurity trends for 2020’, implications for tech buyers, implications for tech vendors, insights, and more resources. Download Link Below ?

The industry has been enthusiastic about the number of devices and sensors that are expected to increase exponentially in 2020 and beyond. The role of the Internet in Things (IoT) in delivering ‘Smart’ solutions is seeing unprecedented interest in technology. However, 2020 will be the year when IoT adoption will see a sharp increase in uptake as 5G rollouts gather steam and governments across the world focus on Smart City initiatives.
Here are our predictions on the Top 5 IoT Trends for 2020, that we think, will shape the Internet of Things landscape over the next 12 months.
The Top 5 IoT Trends for 2020
The Top 5 IoT Trends for 2020 are based on the findings of the global Ecosystm IoT and AI studies, and is also based on qualitative research by Ecosystm Principal Advisors Francisco Maroto and Kaushik Ghatak.
-
5G Providers Will Be Forced to Operate Outside their Comfort Zone
Network and communications equipment providers have much to gain and more to lose as organisations look to leverage 5G for their IoT use cases. Each industry will have their different and distinct use cases – the use cases for Oil & Gas will be different from Retail use cases, which will be different from Healthcare industry requirements.
Telecommunications providers will find themselves depending on systems integrators (SIs) with relevant industry experience, to translate the value proposition of what they are offering. However, the telecommunications providers are not companies with actual skin in the game. If 5G uptake does not take off, the bigger losers will be the network and communications equipment providers – the real investors in the technology.
-
Satellite IoT Connectivity Solutions Will Start to Compete Against and Work with LPWANs
Current satellite communications technologies have not been designed specifically for IoT and may fail to meet the specific requirements of the IoT market, especially when it comes to price and ease of use.
This is set to change as both incumbents and new entrants in the satellite space seek to grow their IoT markets in 2020. Satellite communications companies are designing a spectrum strategy and a go-to-market strategy that include collaboration with Low Power WAN (LPWAN) vendors.
-
IoT Sensor Analytics Will Become the Fastest Growing AI Workload
Many organisations will actually start their digital journey and their investments in AI even before they invest in automation – when they start to analyse the data from their IoT sensors and make sense of the ‘data sprawl’ that is created as the number of data collection points proliferate. Organisations’ desire to transform, starting with automation, will further drive the adoption of IoT. The global Ecosystm AI study reveals that organisations investing in IoT sensor analytics also look to invest in computer vision and automation solutions. IoT adoption will enable organisations to focus on incorporating AI/machine learning to make automation smart and intelligent.
-
Construction Will Become the Unsuspecting Influencers for IoT Adoption
The construction industry is fast emerging as the arena for end-to-end IoT-driven services especially as new-age companies link architects with contractors with building managers with facilities management to create a new meaning of ‘Smart Buildings’. Realtors become unsuspecting influencers as they establish Smart Building ecosystems. According to the findings of the global Ecosystm IoT study, the top solutions that construction companies have implemented and are evaluating, are primarily aimed at ensuring operational and employee safety. However, the industry will also see an uptake of customer management IoT solutions aimed at providing better customer experience (CX).
-
The Edge Will No Longer Be at the Edge
2020 will mark the end of the hype around the Edge and the way we think about it. Real-time analytics will be performed at so many places along with the network and infrastructure that IT management will be forced to rethink their distributed and enterprise computing strategies. The main industries that will see a growth in Edge uptake in 2020 will be Manufacturing, Retail, Energy, Healthcare, Transportation and Logistics.
As the Edge technology develops, the application of AI will steadily move away from centralised servers (on-premise or cloud) to the edge devices themselves. There are two important benefits to this – Firstly, it minimises time lag between data acquisition and secondly, any targeted hacking attempt can be immediately identified and mitigated, rather than being at the mercy of the security systems implemented by the cloud provider.While AI-enabled edge devices tend to be costlier than
their “dumb” counterparts, the value they can bring in terms of being able to immediately act upon the data, and the additional security they can potentially provide, can be significant factors that offset the high initial cost of deployment.
Download Report: The Top 5 IoT Trends For 2020
The full findings and implications of the report ‘Ecosystm Predicts: The Top 5 IoT Trends For 2020’ are available for download from the Ecosystm website. Signup for Free to download the report and gain insight into ‘the top 5 IoT trends for 2020’, implications for tech buyers, implications for tech vendors, insights, and more resources. Download Link Below ?
The benefits of cloud computing are well documented, and it is at the core of most organisations’ modernisation and transformation initiatives. With the predicted increase in IoT uptake, and the associated increase in data collection and processing, technology providers are looking at methods to simplify, secure and speed-up IoT devices connected to the cloud.
5G Edge computing
To this end, in order to provide data processing closer to where it is needed, Amazon Web Services (AWS) and Verizon recently announced a partnership to bring the power of cloud computing closer to the edge with 5G network edge computing.

Edge computing brings various cloud services such as computing, networking and applications closer to the devices for local processing. It allows complex processing at the point where the data enters the network and eliminates round-trips involved in sending data from the edge, to the data centre where it gets processed and back to the edge again. To accomplish this, Verizon will offer 5G network and high-volume connections between users, devices and applications and will use AWS’s Wavelength service to deploy applications and process data at the edge. It will then seamlessly connect back to the AWS cloud.
The providers are piloting the project and aiming to deliver a wide range of services which depend on millisecond latencies.
New Demand, New Markets
By using AWS Wavelength and Verizon 5G Edge, the resulting edge computing solution will enable developers to build applications that can deliver enhanced user experiences like near real-time analytics for instant decision-making, improve services such as immersive game streaming, and automate robotic systems in manufacturing facilities.
The Ecosystm top 5 IoT Trends For 2020 report authored by Ecosystm Principal Advisors Francisco Maroto and Kaushik Ghatak stated that organisations are currently generating about 10% of their data outside a traditional data centre or cloud. This is predicted to dramatically increase in 2020 with IoT deployments fuelling investments in edge computing. The next year will see a sharp increase in IoT adoption as 5G rollouts gather steam, and this partnership is another indication of the increased interest in edge computing.
“As devices multiply and become smarter, 5G technology will become progressively more important to transfer data at a faster rate and drive edge computing. Real-time analytics will be performed at so many places along the network and infrastructure that IT management will be forced to rethink their distributed and enterprise computing strategies,” the report states.
Another Ecosystm report, the Top 5 Cloud Trends for 2020 report authored by Ecosystm Principal Advisors Claus Mortensen and Craig Baty mentions that “with IoT being a major part of the business case behind 5G, the number of connected devices and endpoints is set to explode in the coming years, potentially overloading an infrastructure based fully on data centres for processing the data.”
Edge computing will allow Cloud providers such as AWS to better cater to companies that need low latency, quick access to data and data processing. On the mobile side, it will allow them to push workloads to the device, reducing the backend workload and potentially enhancing data privacy.
The full findings and implications of the report ‘Ecosystm Predicts: The Top 5 IoT Trends For 2020’ and ‘The Top 5 Cloud Trends for 2020‘, implications for tech buyers and tech vendors, insights, and more are available for download from the Ecosystm platform.


Google recently announced its ‘Google Cloud Acceleration Program’ to support SAP customers in simplifying their transition to the cloud.
Earlier this year, Google initiated a program known as Lighthouse, in partnership with system integrators, to streamline its customers’ SAP journeys to the cloud. The Google Cloud Acceleration Program is a progression of Lighthouse and will provide technical resource, blueprints, employee training and consulting services to partners and customers for migrating SAP to the cloud, as well as upgrading to SAP S/4HANA.
Google Cloud Acceleration Program Partners’ contributions
Several ISV’s and technology providers are already participating in the program. One of these providers, HCL Technologies, recently announced plans for a 5,000-employee division which will focus entirely on helping enterprise customers plan and execute large-scale migration of workloads and applications to Google Cloud. Accenture and Google set up a similar collaboration earlier this year.
Google’s Cloud Acceleration Program will be supported by partners such as Accenture, Atos, Deloitte, and HCL to help migrate workloads. In addition, these partners will also work alongside Capgemini, DXC Technologies, Hitachi oXya, Infosys, NTT, TCS, and Wipro, to create SAP centres of Excellence for Google Cloud.
Commenting on Google’s Cloud Acceleration Program for SAP platform, Principal Analyst at Ecosystm Claus Mortensen said, “Migrating SAP to the cloud has proven to be a notoriously complex task over the years. To help the migration to Google’s Cloud, Google launched its SAP Lighthouse program. The Cloud Acceleration Program can be seen as an evolution of Lighthouse.”
Mortensen added, “Google Cloud Acceleration Program is intended to make migration as simple as it can be under the circumstances – but I don’t think it will ever be easy to migrate SAP to the cloud – it is too complex a system to become simple to migrate. Whether it will succeed in convincing SAP customers to migrate much depends on how well the program partners perform.”
The primary aim of the Cloud Acceleration Program is to boost the adoption of Google cloud services and benefit customers with greater innovation, operational efficiency, and risk mitigation. Google has been active in promoting the programme and in the same spirit, Google recently acquired CloudSimple, a provider of secure, dedicated environments to run VMware workloads in the Cloud. Many organisations are running VMware in their on-premises environments to run a variety of workloads and this acquisition will boost abilities to run VMware on Google Cloud Platform.
As we recently stated in our predictions for ‘the top 5 cloud trends for 2020′, the ability for even the top cloud players to compete will increasingly come down to their ability to expand their service capabilities beyond their current offerings. Ecosystm expects these players to further enhance their focus on expanding their services, management and integration capabilities through global and in-country partnerships. One particular area might be partnerships focusing on Cloud migration between Clouds and from Cloud to on-premises. Google’s Cloud Acceleration program is a prime example of a framework, that has such partnerships in mind.
Speaking on the benefits of Google Cloud acceleration program for SAP customers, Mortensen said “cloud offers a lot of flexibility and agility that would be hard to achieve using an on-premises deployment. So, from that perspective, the Google Cloud Acceleration program should be good news to both new customers and existing customers, who see a benefit from migrating partly or fully to the cloud.”
Brands are not built overnight, and today’s customers tend to regard a brand’s worth by the innovativeness of the products and services and by the customer experience (CX). CX is by no means a new concept but has gained significance and organisations focus on ways to stand out from the competition and drive deeper engagement with their customers. In today’s ‘Experience’ economy CX is key to attracting new customers and retaining the ones the firms already have and cuts across the entire organisation – vertical marketing, strategy, product development or technology. Every business today needs to ‘delight’ its customers – offer a substandard experience and your brand might not survive long.
The global Ecosystm CX study discovered that improving CX is a key business priority for over 70% of organisations across industries – even in industries that are not considered customer-focused. These organisations were also asked why driving a consistent CX was challenging.
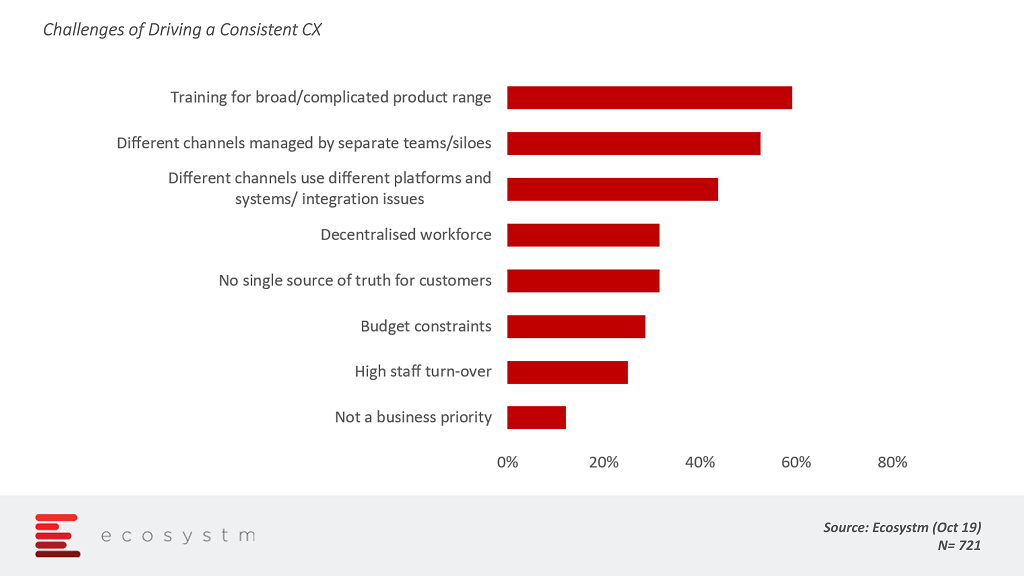
The key challenges boil down to managing the different stakeholders within the organisation – giving visibility and knowledge on all product offerings; managing the siloes created by each department and; in the end not being able to provide customers with one single source of truth. While many of these challenges are business-related, technology can be a key contributor to enhancing CX.
Technologies that can help you improve CX
There are many technologies that allow organisations to provide better CX, but the key to these technologies is how they collect, classify and provide actions on customer data. This is where AI comes into the picture, and why AI is at the heart of many CX offerings, making sense and aiding in the decision making around customer data.
AI-Enabled IoT
AI-enabled IoT devices are helping to enhance Customer Experience. The sensors in IoT devices such as wearables or personal assistants produce data which can be processed to derive useful insights, activity patterns and develop personalised communication. AI is improving the ability to take IoT generated data to personalise and customise actions and communication. For example, customers in gyms and fitness clubs can share their wearables data with their fitness trainers to customise their exercise routine and provide dietary recommendations.
Similarly, cars can be embedded with sensors which assess the users’ driving habits. This can then be used to suggest improvements to driving style or adjust insurance premiums based on how they drive.
Progressive Insurance, for instance, offers its customers discounts based on their driving through its “Snapshot” program. Progressive is using its usage-based-insurance (UBI) telematics programme to monitor how its car insurance customers drive. Using an ODB telematics dongle and machine learning, the insurer is able to judge how a driver is performing on each journey.
Location-Based Targeting
With location-based tracking technology and GPS systems on smartphones and devices, more businesses are working to enable and provide geo-location services to customers. This presents opportunities to offer personalised shopping experiences and customised promotions and offers to the customers. Businesses are already using geo-location services to extend offers to customers – such as cinemas and theatres pushing notifications on movie timings and available discounts when customers are in the vicinity.
Location-based services also help to enhance the actual shopping experience. Lowe’s has an app which allows their customers to navigate the large warehouse-like stores, helping them find products faster and easier. The app called The Lowe’s Vision: In-Store Navigation app works using a combination of VR and location-based services.
Customer-Centric AR and VR
AR and VR technologies are enhancing the way customers engage with businesses. Companies adopting AR/VR can distinguish themselves from the competition by introducing higher touchpoints and deeply personalised experiences designed specifically for their customer journey. The retail industry has been at the forefront when it comes to experimenting with AR and VR technologies, in the customer space. Retailers have rolled out applications and services that lets consumers virtually try makeup, clothing, accessories and seek out the best look for them.
Financial institutions are also leveraging AR and VR to build customer-centric solutions for self-service and user training. Citibank worked with a mixed reality technology company to develop a trading platform combining 2D and 3D working environment to extrapolate insights from data. Traders work with hundreds of financial instruments, and with the mixed reality workstation, they can quickly identify market hotspots that they should be focusing on. The consequences – better trades!
The hospitality industry is also leveraging AR to improve CX, AR-based menus is a good example. Various fine dining restaurants have started offering AR based food menus which can display virtual food items and live 3D models of food to accurately represent both the appearance and the serving portion.
Obviously, the entertainment industry will leverage mixed reality to the fullest. For instance, The New York Times leverages VR for storytelling where readers can visualise the events described in some editions of the newspaper. The technology thus allows the description of the setup of a story making the viewers witness an emotional connect with the characters.
Voice capabilities for a seamless experience
With the advent of digital voice assistants and voice recognition AI, voice recognition has opened up avenues and opportunities for businesses to enhance the way customers interact with them whether through mobile apps or their call centres.
Nowadays, voice-capable apps enable customers to interact with services very easily. A good example is Starbuck’s My Barista app, which allows customers to order via voice command or messaging. The coffee chain expanded its application by incorporating voice features to boost speed and convenience for placing and processing orders.
In conclusion, implementing technologies in a business could help businesses change the way the customers see and respond to a business. In addition to this, Improving customer service and using technologies can significantly reduce human inaccuracy, improve employee confidence and rapidly improve the character of a brand. By bridging the gap between a company and its client’s, businesses are becoming CX oriented and are dedicating themselves to enhance CX.
Besides the above, which technologies do you think are beneficial in enhancing your CX?
Let us know in your comments below.
As organisations look to leverage better operational and business insights, adopting Cloud has become imperative for them, especially for those that intend to make use of other technologies like analytics and IoT. All the imperatives for moving to Cloud continue to grow stronger, while at least some of the reasons for resisting the trend are becoming indefensible. The key inhibitors continue to be security and data privacy concerns and back-up/connectivity issues. Also, as the Cloud ecosystem has matured, an important inhibitor has become cost considerations as many organisations are now evaluating whether the Cloud is indeed more cost-effective than on-premises options.
This article presents the Top 5 Cloud Trends for 2020 for the Cloud market in 2020. It is based on the latest data from the global Ecosystm Cloud, IoT and Cybersecurity studies, that are live and ongoing on the Ecosystm platform, and qualitative research by Ecosystm Principal Advisors Claus Mortensen and Craig Baty.
The Top 5 Cloud Trends for 2020
Here are the Top 5 Cloud Trends for 2020 that we believe will impact both businesses and consumers in 2020.
-
Major Cloud Providers Will Push for Open Source
Open Source has always played a big role in Cloud and as we move into 2020, its role will only grow bigger. Infrastructure and Platform Clouds may not have been dominated by Open Source in the past, but all major Cloud players such as AWS, Microsoft, and IBM have been focusing on Open Source recently.
In 2020, major cloud providers will switch to Open Source to create a development environment that can achieve more than they would be able to develop fully in-house.
-
Open Source will Drive the Adoption of Serverless Computing
Serverless computing is a cloud model where the Cloud provider runs and manages the server and the allocation of machine resources. Beyond just the individual servers, many vendors are now offering to totally replace the data centre with a virtual version that runs in the Cloud.
It has the potential to become a widely used solution for mid-range businesses. A dynamically scaled and priced data centre could offer them a much more flexible IT environment where they do not have to worry about capacity planning and scaling – even when compared to a more traditional Cloud environment.
-
Cloud and IoT Will Drive Edge Computing
Edge computing has been widely touted as a necessary component of a viable 5G setup, as it offers a more cost-effective and lower-latency set up than more traditional infrastructure. Also, with IoT being a major part of the business case behind 5G, the number of connected devices and endpoints is set to explode in the coming years, potentially overloading an infrastructure based fully on data centres for processing the data
Although some are touting Edge computing as the ultimate replacement of Cloud, we believe it will be complementary rather than a competing technology – at least in the foreseeable future and certainly as far as 2020 is concerned. Edge computing will allow Cloud providers to better cater to companies that need low latency, quick access to data and data processing. On the mobile side, it will allow them to push workloads to the handset, reducing the backend workload and potentially enhancing data privacy.
-
‘Cloud Creep’ Will Get Worse Before It Gets Better
What we have previously referred to as “shadow IT” is rapidly spreading – and worsening – as organisations move to the Cloud and many organisations are now suffering from what is referred to as “cloud creep”. There are several implications of cloud creep – the most significant ones being security issue and cost.
As the use of stand-alone Cloud services grows, the risk of sensitive data being used, stored and shared in non-compliant ways increases. As for cost, while LoB sourcing of Cloud services may save the strain on the IT department’s budget as the money may come from a different “bucket”, it makes it very difficult to get a true picture of the organisations total IT spend and it may mean that consolidation benefits from well-managed sourcing and usage cannot be achieved. A third and increasingly important factor is energy footprint and savings. A fall-out from cloud creep is increased “server sprawl” whereby virtual machines (VMs) and applications remain under-utilised, leading to poor productivity and proficiency.
-
Alliances and Partnerships Will be Formed as the Battle for the Top Heats Up
The global Cloud market has been consolidating around 5 players: AWS, Microsoft, Alibaba, Google and IBM. Nothing really suggests that this trend will change in 2020.
But even for the current top 5 players, their ability to compete will increasingly come down to their ability to expand their service capabilities beyond their current offerings. Ecosystm expects these players to further enhance their focus on expanding their services, management and integration capabilities through global and in-country partnerships. One particular area might be partnerships – focusing on Cloud migration between Clouds and from Cloud to on-premises.
Download Report: The Top 5 Cloud Trends For 2020
The full findings and implications of the report ‘Ecosystm Predicts: The Top 5 Cloud Trends For 2020’ are available for download from the Ecosystm website. Signup for Free to download the report and gain insight into ‘the top 5 Cloud trends for 2020’, implications for tech buyers, implications for tech vendors, insights, and more resources. Download Link Below ?

Organisations across the globe are increasingly moving their infrastructure, storage and computing capabilities on the cloud. With the adoption of different cloud models and modernisation of computing and data storage practices, cloud providers have formed their own data models and technology stacks making interoperability difficult. This brings a lot of challenges for developers to create and run applications across different cloud environments.
Establishing the Open-source models for data interoperability
To remove the hurdles of information created by different cloud providers, AWS, Genesys, and Salesforce have come together with the Linux Foundation’s joint Development Foundation (JDF) to create a Cloud Information Model (CIM). This program comes shortly after Microsoft, SAP and Adobe announced the Open Data initiative.
The operation of these two data models is quite similar. Indeed, they allow both to store data and to apply a common open model.
Cloud Information Model vs. Open Data Initiative
What’s Cloud Information Model (CIM)
Cloud Information Model (CIM) is based on open-source standards that will standardise data interoperability across cloud applications and the environment. CIM will work on MuleSoft’s open-source modeling technology which will provide various file formats to work with varying applications. The new open-source data model will reduce the existing complexities of migrating data across cloud applications. The model aims to form interoperability guidelines to improve the working of POS Systems, digital marketing platforms, Contact centres or CRM platforms.
Instead of creating custom code, developers can implement the CIM and quickly be able to create data lakes, generate analytics, train machine learning models and translate data across systems. The model will be backed by an open-source community that will assist with faster and consistent development.
What’s the Open Data Initiative?
Open Data Initiative is a common data model to eliminate costly and complex disconnected data silos. The three partners, Microsoft, Adobe and SAP will drive this by improving interoperability and data exchange amongst their platform and applications; Adobe Experience Cloud and Adobe Experience Platform, Microsoft Dynamics 365, SAP C/4HANA and S/4HANA.
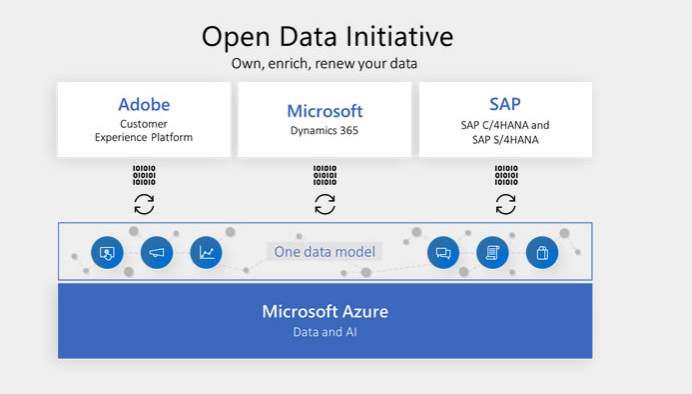
The program partners can easily leverage an open and extensible data model to extend solutions. This integrated data store will let customers explore more choices on applications development, building, and deployment.
Phil Hassey, Ecosystm Principal Advisor, says “whilst every partner brings along its own expectations and capabilities, the initiatives are looking to make the connection and flow of data easier through using open source models. In theory, this will accelerate solutions for clients and enable faster business outcomes if they are executed effectively and with positive intentions”.
Two Competing Models, do we need both?
We currently have two separate models involving a competitive and closed environment, with Microsoft, Adobe and SAP supporting Open Data Initiative on one side whereas AWS, Genesys, and Salesforce backing up the Cloud Information Model (CIM) on the other end. They are both aiming to bring standardisation for data interoperability across various products. With two competing models, we can see some friction developing between these projects.
“When it comes to the crunch competitive pressures within the two models, it will not be eliminated, for example, Microsoft and SAP partner in key areas, but also have competitive overlap in CRM and analytics,” said Hassey. “It might be positive to think that open source will provide some standards, unfortunately, the reality is different. Execution is often difficult in these types of attempts partly due to the inherent nature of the Open Source community. At best, it will create two different standards, that may be a progressive step.”
The two models may bring opportunities for the developers, open source community and adopters. “The open-source community is very strong as is the developer market aligned with both platforms. If the models commit to investing in the developer community then the opportunity is very strong for positive and desired outcomes, but a lot of success is reliant on developer community investment on top of already existing investments” said Hassey.
Hassey further added, “It is also interesting to see what the likes of Oracle, IBM and Google will do, do they join one of the existing groups or establish yet another branch of the overall environment.”
Both models have the potential to provide common standards and open source codes to the adopters and community thus working on methods to connect data across multiple cloud platforms and disparate systems. They might help but only time, ease of implementation, adoption and support by the community will tell the whole story.
Do you think that these two competing models will merge or only one out of both will be triumphant? Let us know in your comments below.
Gain access to more insights from the Ecosystm Cloud Study

++Update: A few days after we added this story, Australia released its AI roadmap focused on future investment in AI and machine learning, and Artificial Intelligence: Australia’s Ethics Framework.
Over the last few years, many countries have created plans to harness Artificial Intelligence (AI) for better citizen services. At this week’s SFFXSWITCH (Singapore FinTech Festival and Singapore Week of Innovation and TeCHnology), Singapore announced the next step in its Smart Nation initiative with the release of the “National AI Strategy”. The AI strategy will focus on social and economic benefits by providing modern infrastructure, intelligent services, and an excellent education system to citizens.
Commenting on Singapore’s AI adoption and implementation strategies, Ecosystm Principal Advisor, Tim Sheedy said “being a smaller country, Singapore is one of the few around the globe that can make investments into AI at a ‘country level’. Singapore has the luxury of having a progressive public sector that operates at the same speed as the private sector, and has the opportunity to become one of the leading economies in the world for both the deployment of AI in everyday services AND in ensuring the economy has the required skills.”
The key approach of the AI strategy
Singapore is aiming to position itself as a global hub for the development and implementation of AI solutions. National AI Office established under the Smart Nation and Digital Government Office (SNDGO) will be heading Singapore’s AI initiatives.
To begin with, the SNDGO will be initially working on key high-value sectors:
- Transport and Logistics: Intelligent Freight Planning
- Smart Cities and Municipal Services: Infra management and smart services
- Healthcare: Chronic Disease Prediction and Management
- Education: Personalised Education
- Safety and Security: Seamless border clearance operations
Speaking on AI strategies devised for transportation, smart cities, healthcare, education and safety and security in Singapore, Sheedy said “all of these investments are ones that you would make as an economy if you had the opportunity. They are all logical and will all benefit the lives of citizens and the success of the overall economy.”
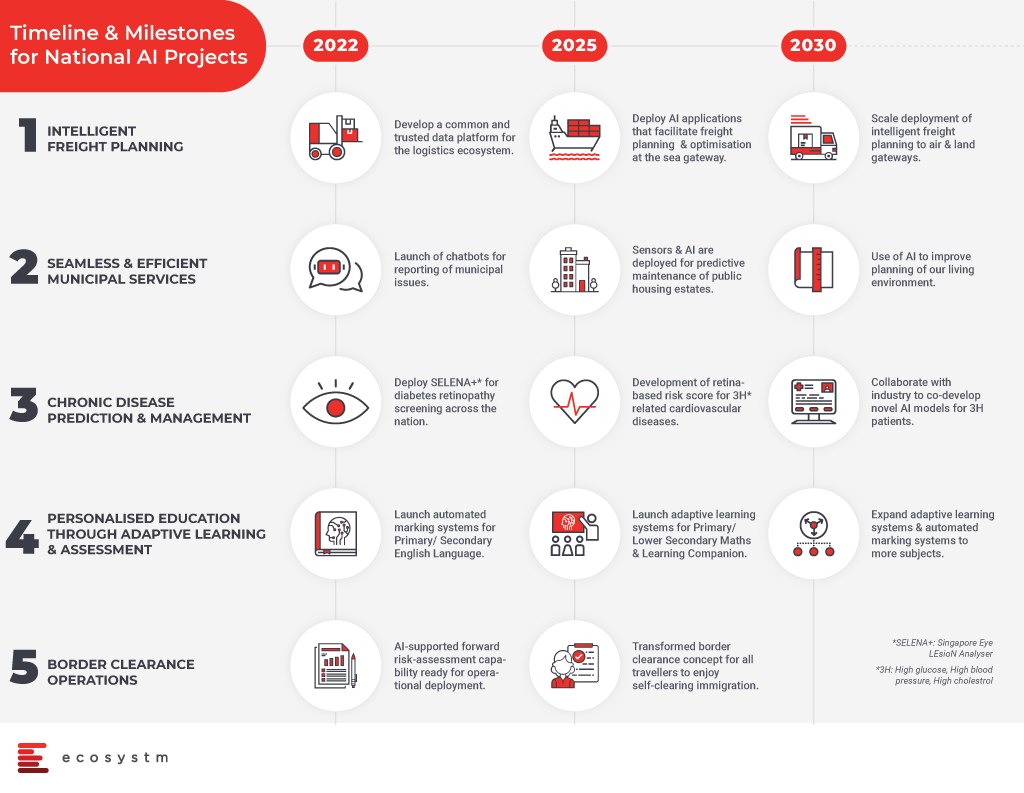
Transport and Logistics: To optimise the freight and delivery services, a common data platform will be built. The aim is to bring in efficient transportation and logistics with intelligent AI systems in place by 2022 and further AI developments will scale deployment, enable optimised delivery processes and routing of services for freight planning.
Smart Cities and Estates: The country aims to launch AI powered chatbots by 2022 to record municipal issues and allocate them to the responsible authorities. AI powered services will be introduced to better serve the residents. By 2025, efforts will be established to optimise estate maintenance through AI and sensors and by the year 2030, data driven insights will be used to improve the infrastructure and living environment in Singapore.
Healthcare: An all-new AI system known as SELENA+ will be in place to screen and detect diabetic eye disease. SELENA+ is a first artificial intelligence algorithm which performs automated retinal photo analysis to detect retinopathy and systemic complications in diabetics. In addition to this, AI capabilities will also be used to predict cardiovascular diseases and create personalised chronic risk scores. All of these will help to detect diseases and take early preventive measures by the healthcare teams for the welfare of country and betterment of the economy.
“This could detect chronic issues early, and reduce the impact of them on individuals, families and the economy. Being able to make investments at a macro level – like this happening in Singapore – will make sure everyone benefits” said Sheedy.
Education: AI in education will bring the benefits of automated marking systems for English language in primary and secondary education. Further, AI-enabled learning systems will help students on learning and mastery of topics. The government has planned to expand automated AI and adaptive learning systems to more subjects at a later stage.
Sheedy said, “with the government being able to influence and change the syllabus in schools and universities, as well as the skills in the public and private sector, Singapore is uniquely positioned to drive real economic benefit from their investment into AI.”
Safety and Security: AI systems will help in border security and clearance procedures. AI will enhance travel experience with automated immigration clearance systems involving face and iris scans. The immigration processes will develop into seamless self-clearance systems and become faster.
“A few countries have the ability to drive this level of planning – most countries have many levels of government which make this planning – or execution of plans – difficult.” said Sheedy. “Many are also leaving the investment to the private sector, which means it will happen eventually, but may see many competing initiatives or different capabilities emerge that only benefit a single company, not an entire economy.”
Smart Nation drive
Singapore’s government is highly active in transforming the country into a smart nation. Singapore was working with the World Economic Forum’s Centre for Fourth Industrial Revolution (WEF C4IR) in order to come out with a framework for ethical and responsible AI adoption and deployment by the Asian governments.
Singapore is also set to invest US$ 360 million on AI and other digital technologies through 2020 and has invited Chinese and American companies to be a part of this.
According to Sheedy, there are many benefits of having deep investments in AI and AI capabilities in an economy.
It will make Singapore a more attractive investment location. If access to government and other services are seamless, then the barriers to entry to starting a new business or creating a new business capability will be much lower. It will mean that it is easier to build a business case for businesses to move to Singapore or start in Singapore – attracting investment funds and employment into the island state.
It will boost export capabilities – both for the skills that will be in demand through technology and business service providers and for the intelligent products and services that will likely emerge from the early AI investments. If Singapore can make more of the products and services that they produce “smart” – then these products and services will see increased demand – both locally and outside of Singapore.
It will make Singapore a better place to live and visit. With seamless government services, easier travel into and out of the country, and a government that anticipates the needs of its citizens, the quality of life for residents will increase.
The country can get ahead of the challenges and downsides of AI – and legislate or plan for these challenges, to ensure these challenges are understood and managed before they become problems.
In the escalating initiatives to become an AI superpower, Singapore has clearly indicated they are fully committed to leveraging AI to drive growth and citizen services.
++Update
An AI roadmap report was published by the Australian Government in November 2019, co-developed by CSIRO’s Data61 and the Department of Industry, Innovation and Science. The report identifies the opportunities and benefits of AI that Australia could capture.
The report classifies the strategies to help develop AI capabilities to boost the productivity of industry, generate jobs, bring economic growth, and enhance the quality of citizens’ life. To drive this, Australia has identified 3 key areas where it has the best opportunity to create new value-
Health, Ageing, and Disability – To develop AI to improve healthcare, aged care, and disability services while reducing healthcare costs.
Cities, Towns, and Infrastructure – To develop an AI system for the cities and infrastructure to provide better services, safety efficiency in a smart and cost-effective way.
Natural resource and environment management – Develop AI for better natural resource management and improve the productivity of agriculture, mining, fisheries, forestry, and environmental management.

As technology continues to permeate all aspects of business and influence how employees execute their roles, there is a growing need for more technologically proficient employees to quickly become future-ready. To enable this, organisations need to develop strategies and support parameters to reskill and upskill their workers.
Why the Need to Retrain and Reskill
Retraining and reskilling are nothing new, and industries have witnessed it several times in the past. The Industrial Revolution replaced many workers with mechanised tools and machinery. Workers who embraced change, and learned how to use the machines, replaced those who did not or could not. It is true that every new technology creates its own turbulence. What is unique this time is that the shift is happening faster as technology advances exponentially. So, people need to retrain and upskill quicker if they are to keep pace with the changing technology landscape.
Both manual and cognitive tasks are being empowered by machines and AI algorithms. There is also a shortage of a skilled workforce with the right technical training. Here is why the need for technological skills has increased exponentially over the last few years:
Productivity. Organisations are looking for ways to increase productivity and are spending time on identifying technologies that can help them compete in the future. The introduction of AI and automation is replacing legacy systems and displacing positions such as junior executives, administrative staff, customer service executives and so on. Chatbots and novel interactive robotic companions are offering better productivity with an ability to work 24×7 without taking breaks and can be updated and taught new skills with some minor changes in their algorithm. To understand and to work on AI and chatbot queries, employees require special training and skills. For instance, in a customer care team, if a chatbot is not able to respond to a query it can then be passed to a customer service executive who is able to work in tandem with the AI tool to solve the query.
Profitability. The primary reason why organisations look to technology-driven automation is to create an impact on their profit margin. While making the investment in the technology often requires an upfront cost, once the systems are in place there is a positive impact on productivity and hence more profits. Organisations should ideally invest part of the profits to implement more advanced technology and upskilling their current employees. The lower productivity workers often add up to the costs and reskilling them can save money and lead to more seamless workforce integration. For instance, Fintech is being used increasingly to automate decisions such as instant loan approval, KYC, fraud detection and other financial crimes. This does not remove the need for subject matter experts and those that have experience and expertise in the domain – they can train those automated systems by feeding queries, analysing outputs and helping the organisation improve their automated process.
Avoiding being Obsolete. In this digital era, even individuals possessing decades of work experience might get outdated if they do not keep pace with an evolving landscape. Lacking an ability to understand and empathise with technology is often a consequence of improper training. Employees require training at regular intervals – if they do not have the expertise and cannot give the right feedback to these automated systems, there might be serious consequences. As an example, most organisations planning to procure software will also evaluate SaaS solutions. This requires employees to be flexible to adapt to the Cloud environment and to look beyond the legacy systems that they are comfortable with.
Mergers and Acquisitions. In today’s competitive market, we witness mergers and acquisitions almost on a daily basis, with organisations wanting to gain skills, services, technology and ultimately market share. When a company is bought or merges with another, along with a change in leadership and organisational culture, there is also a change in technology used. If organisations want to retain the expertise of the newly acquired firm, retraining becomes essential. In these new set-ups, what will matter more than seniority is the ability of the employees to adapt to and learn the new technologies.
Being Competitive. Technology is seen as an enabler for business differentiation. Increasingly the twin focus areas for all organisations are customer experience (CX) and employee experience (EX) – how to retain and win both customers and employees. When it comes to outperforming the competition, the technology used for the eCommerce platform, point-of-sale solution, back-office operations – virtually every part of the operation, can be a key component of the overall competitive edge. Having workers that are properly trained in the technology they use, and those who buy into the organisational culture will be a crucial advantage in this competitive world.
How to incorporate retraining and reskilling in your Transformation Journey
Organisations should follow best practices when embarking on reskilling initiatives, in order to rapidly drive ROI. It is always a good idea to invest in people who are invested in your organisation. Amit Gupta, CEO, Ecosystm interviewed Parry Singh, Chief Commercial & Digital Officer, Mediacorp where they discussed how emerging technologies such as AI, are impacting the media industry, how to carry an organisation through the digital transformation journey and how to upskill employees for the future. The key takeaways for organisations looking to retain their valuable staff are:
- Realise that learning is a continuous process. Companies should analyse technologies that will impact their business and their industry. But should also be aware that these technologies will evolve continually. To handle this learning should also be continuous. Walmart, for instance, has set up more than 100 “academies” in the US that provide continual classroom and hands-on training for various positions. Having the right talent in place is critical to the prospects of any organisation.
- Make arrangements for just-in-time learning. Learning works best when people can apply their new-found knowledge and skills almost immediately. Organisations should identify the skills that employees will need in their immediate role. This also helps employees appreciate the value of the training and be open to future upskilling. NUS Business School offers a 3-day course, Leveraging Fintech for Business aimed at leaders and managers, to explore the business impact of Fintech – aimed at entrepreneurs and mid-career financial professionals who wish to upskill and those who are impacted by Fintech. Organisations can provide employees with on-demand learning tools and resources. Tools like mobile apps and online courses can help employees to learn and grow and allow them to engage with the program at their convenience and at their own pace instead of forcing them to adhere to a pre-planned schedule.
- Partner if you do not have the right training process. An organisation cannot always be expected to have the right training resources available in-house – it might also prove to be expensive in the long run. Organisations that lack expertise or do not have enough resources to train and reskill employees, should partner with technology providers and dedicated external training programs. SkillsFuture in Singapore has partnered with IBM to train 2,500 Singaporeans on AI skills within the next three years, in a bid to help them apply AI in areas such as human resources, supply chain management, and media.
Technology-enabled automation will displace some workers while at the same time provide a platform for them to grow their careers and play a larger part in the success of the organisations. Companies can enable this transition through investments in training and education and provide a platform for workers to transition to new jobs. With the right tools, companies can continue to forge a long-term and mutually beneficial association with their employees in the face of rapid and increasing digital transformation.










