The Oil and Gas industry has seen volatile times and is affected by its own set of unique challenges ranging from commodity price fluctuations, a potential supply crunch, geo-political events, and energy policies including energy transition. Moreover, the challenges and requirements are distinct at different stages of operations – upstream, midstream and downstream. The industry has been an early adopter of a few emerging technologies and is looking to leverage them to remain competitive and better employee management.
Drivers of Transformation in the Oil and Gas Industry
Remaining competitive in an evolving market
Oil and Gas companies are having to clean up old processes, as the market gets increasingly competitive. Ecosystm research finds that the top business priorities for Oil and Gas companies do not stop at cost reduction and revenue growth. The industry also has to focus on employee experience and safety, compliance, and increasingly even customer experience. And they must remain competitive through potential disruption in supply, demand and production; the rising costs of processes; and ongoing exploration costs. Oil and Gas companies are also focusing more on their downstream operations including retail in order to remain competitive.
Shortage of skilled workforce
The industry also faces the challenge of skills shortage. A survey conducted by the Global Energy Talent Index (GETI) found that nearly 70% of Oil and Gas professionals think the industry is already facing skills shortage or will be hit by it within the next 5 years. This is due to a number of reasons, including a reluctance of younger professionals to commit to a profession that has harsher conditions than many. Moreover, as energy transition becomes a topic of global discussion, many have a perception that the industry is not sustainable in the future. The industry also goes through cycles where they cut back on exploration and production, which results in the loss of skills and inadequate knowledge transfer. It has a long-term challenge around knowledge management.
Safety and environmental regulations
The industry has to contend with green energy movements and environmental regulations. There are several country-level regulations around air and water quality. Most Oil and Gas companies have cross-border operations and have to comply with a number of regulations on harmful emissions, greenhouse gases and offshore activities, in several countries. Increasingly, all leading Oil and Gas companies have to work in alignment with the Paris Agreement when developing solutions across functions – exploration, extraction and supply chain. There are also worker safety regulations and standards that they have to comply with.
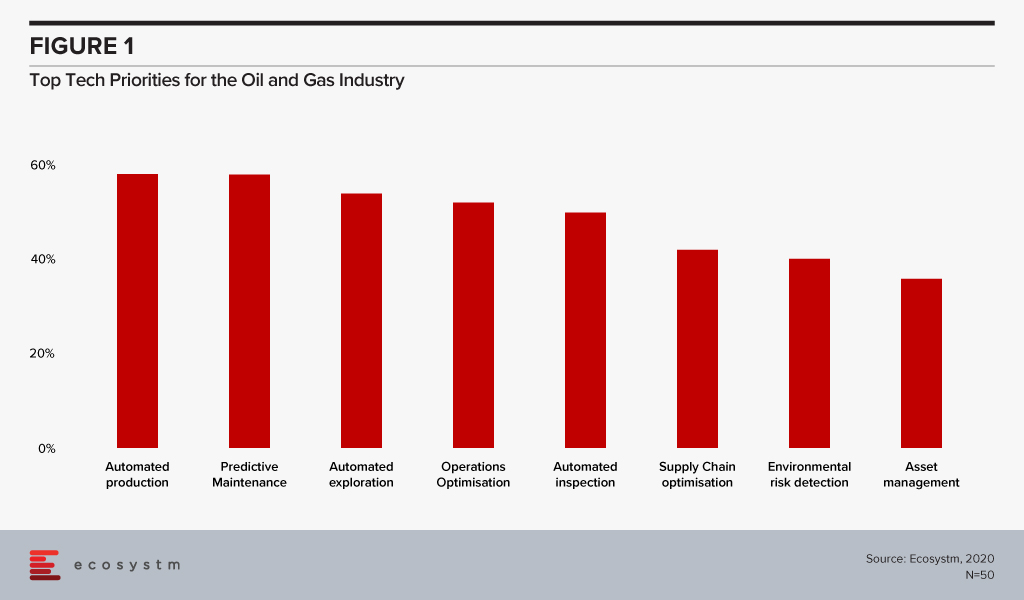
The global Ecosystm AI study reveals the top priorities for Oil and Gas companies that are focused on adopting emerging technologies (Figure 1). It is very clear that the key areas of focus are process automation, asset and supply chain management and compliance.
Technology as an Enabler of Oil and Gas Transformation
Several emerging technologies are being used by the Oil and Gas industry as they continue their struggle to remain competitive across the different stages of operations – upstream, midstream and downstream.
IIoT
As the costs of sensors go down, connectivity widens and computing power increases, the industry is seeing greater uptake of Industrial IoT (IIoT) solutions. From wearables (to monitor employee safety) to drones with smart cameras (for remote inspections, environmental monitoring), IoT solutions have an immense role to play in the Oil and Gas industry. The industry has had to be cautious about the choice of devices, however, due to pervasive inflammable hydrocarbons and the related regulations.
Not only are they implementing sensors, Ecosystm research finds that 30% of Oil and Gas companies are also leveraging the IoT sensor data for analytics and intelligence. A common application is in predictive maintenance. Two years ago, Chevron launched predictive maintenance solutions in its oil fields and refineries. While the pilot ran on heat exchangers, the company aims to connect all assets by 2024 and expects to save millions on asset management.
AI
AI and machine learning have applications across Oil and Gas operations, leveraging IoT sensor data. “Smart fields” where production is monitored centrally, has a high level of automated controls. AI/Analytics is allowing companies to run simulations, use predictive data models and identify patterns to gauge risks associated with new projects. This has an impact on production, exploration and making efficient use of existing infrastructure. Oilfield services company Baker Hughes has worked on an AI-based application that allows well operators to view real-time production data and predict future production with more accuracy.
AI is also helping organisations monitor environmental risk and has the potential to help Oil and Gas companies with their compliance requirements. Gazprom Neft, one of the largest suppliers of natural gas to Europe and Seismotech are exploring using AI for seismic data processing, for solutions that are specific to the needs of the industry.
While the applications of AI in the industry are often focused on upstream activities, AI has applications across all operations. In the midstream, transporting crude oil to refineries has always had its unique challenges. Since transport lead times are long and prices fluctuate based on the availability of products, organisations benefit from demand forecasting and price risk modelling. While the common perception of the industry does not include customer interactions, the truth is that the industry is increasingly focusing on the retail space. The need is enough for Shell to begin experimenting with virtual assistants as far back as in 2015, to interact with their retail customers. In fact, the company anticipates a higher adoption of AI in the industry and is collaborating with Udacity to bridge the skills gap.
Technologies empowering employees
As discussed earlier, one of the key challenges of the industry is the inability to manage a reliable knowledge management system that can help consistent knowledge and skills transfer. A single source of truth that can be accessed by all employees on processes, including safety requirements has an immense role to play to help with the skills shortage in the industry.
Enterprise mobility is another tech area that holds immense potential for the industry, with its huge proportion of mobile workers, many in remote locations. Mobility solutions can help in productivity, process optimisation and monitoring of health and safety of the employees and are increasingly incorporating wearables and location-based services. GIS and GPS systems are helping employees with accurate directions, easier access to drilling locations and more. Given the number of devices, platforms and OSs, the industry is seeing an increased interest in unified enterprise mobility (UEM) solutions. Ecosystm finds that more than a third of Oil and Gas companies have implemented or are evaluating UEM, while another 20% are expressing early interests.
Blockchain
The sheer quantity of documents, transaction records and contracts that a typical Oil and Gas company has to manage – including cross-border transactions – poses some difficulty for the industry. The companies have to reconcile and handle issues involving multiple contractors, sub-contractors, and suppliers. Supply chain and inventory management is also a challenge. With the adoption of Blockchain, the industry can automate the management of purchase orders, change orders, receipts, and other trade-related documentation, as well as inventory data with more efficiency and transparency. Blockchain is enabling a seamless supply chain, improved project management and simplifying contractual obligations at each point along the way. Gazprom Neft’s aviation refuelling business is an early adopter of Blockchain-based smart contracts. All refuelling operations are undertaken exclusively on the basis of digital contracts approved by both parties near real-time and eliminates the possibility of any breach of contract and makes the accounting process more transparent.
As the market continues to be volatile for Oil and Gas companies and uncertainties loom in the future, the industry will increasingly depend on technology to remain competitive.

Artificial Intelligence (AI), machine learning and deep learning are buzz words that have organisations – especially the C-Suite – excited about future possibilities of what technology can do for their business. However, these are not merely buzz words and are actually being leveraged by early adopters. At the same time, there are organisations that are keen to adopt the technologies but are unsure of the benefits and the associated challenges act as a barrier to adoption. So, is AI over-hyped or is it a reality for enterprises today? Ecosystm research provides some answers.
The Buzz Around Artificial Intelligence
There are several factors that contribute to the curiosity around AI and why several organisations are evaluating the adoption of AI:
Promotion by large tech vendors
The world’s leading technology providers are in a race to incorporate innovations (mostly driven by AI) within their product and service offerings. Heavy investments in R&D and new patents are aimed at increased market share, as the top tech vendors continue to compete to consolidate and grow their global presence. The perception is that AI-related patents are directly proportional to future market potential. It is not uncommon for the providers to promote these future capabilities – long before they hit the market – as part of their go-to-market messaging. There has been a surge in the number of AI patent filings in recent years with Microsoft leading with more than 18,300 patents followed by IBM (more than 15,000) and Samsung (more than 11,000). As these tech giants keep investing in R&D, apply for newer patents and publicise them, it creates a positive buzz in the market.
Consumerisation of AI
Just like any emerging technology, AI is still, to some extent, an enigma. However, the consumer market gets constant glimpses of how AI can have a positive impact on people’s lifestyle. Amazon, Samsung, Microsoft, Apple – to name a few – have all introduced smart AI solutions to their consumer products. From smart voice assistants that help us with our voice searches to controlling homes with digital assistants, users have been impressed with their early interactions with AI. Many think that the same way as AI has percolated into their personal lives, it will one day be pervasive in enterprises as well. The requirements of an enterprise AI solution is completely different and complex. For example, wearables and wellness mobile apps can help you take control of your health, but for them to become part of the healthcare system, they require FDA approval, a well-documented workflow and policy implementations. But, wearables get people curious and create a buzz about the role of AI in healthcare.
Government initiatives
Several governments are engaging and getting serious about AI and are investing in AI R&D. Many have created an AI roadmap including governance, to promote the adoption of AI. AI.gov was launched by the US Government to centralise AI efforts, share knowledge on AI and drive adoption across government agencies and departments. Some departments have already adopted AI. The US National Oceanic and Atmospheric Administration (NOAA) has been using AI to improve their forecasts. This helps in better prediction of high-impact weather events. Smart city applications are also seeing increased adoption of AI, including in citizen engagement. Cities and government departments are investing in AI-based call centres to answer repeated or routine queries. For example, the United States Army uses an interactive virtual assistant to check qualifications and answer questions with more accuracy. When governments back a technology area, it creates an interest in the citizens.
Success stories
Every day we read about some AI implementation that has positively impacted an organisation or its customers. Twitter’s use of AI-driven text and image analytics to detect hate speeches and terrorist activities has been well-publicised. Gaming companies are actively using AI to improve user experience through Mixed Reality and AI technologies. The recent coronavirus outbreak was first detected by BlueDot, a Canadian company using AI technologies. Such success stories encourage other enterprises to evaluate the technology.
Beyond the Buzz
While we are adopting AI/automation as part of our consumer goods (such as phones, smart home systems) and services (such as search engines, online maps) the enterprise adoption of AI does not really match up to the hype around it.
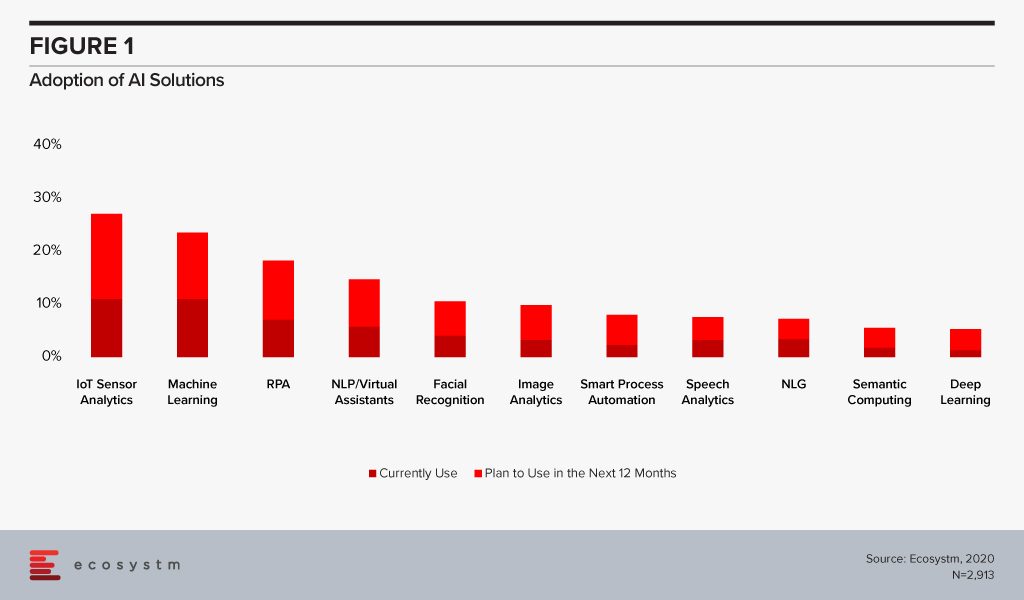
Ecosystm research shows us what the popular AI solutions are and what their current adoption is globally, as well as what it is likely to be at the end of the year (Figure 1). While some solutions have become popular, especially in industries such as Manufacturing, Mining & Resources and Construction, the reality is that we have not yet reached mass adoption. Of the organisations that are planning to implement some AI solutions, 44% consider the investment as strategic to their organisational goal. The rest are mostly looking at ad-hoc implementations to test the waters.
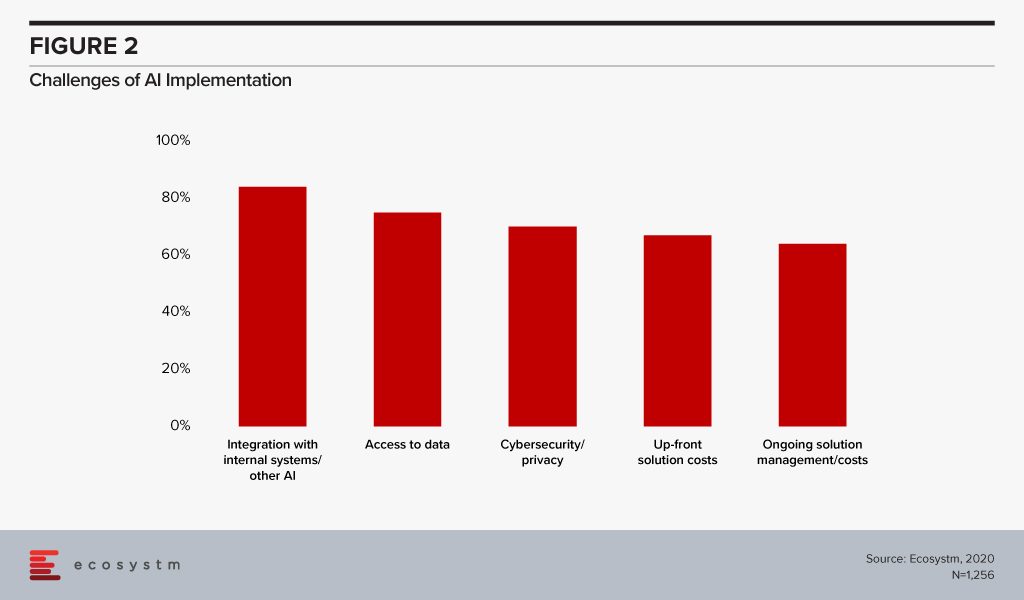
What is hampering more widespread adoption of AI? For both organisations that have embarked on their AI journeys and those who plan to in 2020, the challenges are the same (Figure 2).
AI integration is a complex process. The more organisations want to integrate AI investments into their transformation journey, the more complicated the integration becomes. There needs to be an identification of the expected outcomes, mapping of the data that will be required to help the algorithms, real-time or near real-time data sources and consistency in data infrastructure and sources. Organisations have legacy systems that run in siloes. Integration requires a clear roadmap and dedicated resources, often a third party.
Even in industries that have access to huge organisational data repositories, data access can be a challenge, for technological or compliance reasons. AI requires a huge amount of data to train and run algorithms. Data scientists are often challenged with access to quality training data at the scale required to train the AI systems.
Cybersecurity concerns are natural for any emerging technology area. AI systems have access to enormous organisational data. With threats ranging from ransomware, data breaches to hackers tampering with physical and industrial systems, it is dangerous if AI system falls in the hands of cybercriminals. Instances such as when criminals used an AI-based software to impersonate the voice of a company CEO to commit a €220,000 fraud, also add to the concerns around cybersecurity and AI.
Another reason why organisations find deploying AI solutions difficult is that they do not involve the right organisational stakeholders in the AI decision-making process (Figure 3). While IT is likely to know where the data resides and have a better understanding of the systems implemented, the true success of AI deployments will be measured in user acceptance. An AI solution will obviously impact the existent workflows in an organisation, and if the stakeholders are not convinced, or are unsure of the benefits, it will be difficult for AI to have an organisation-wide impact.
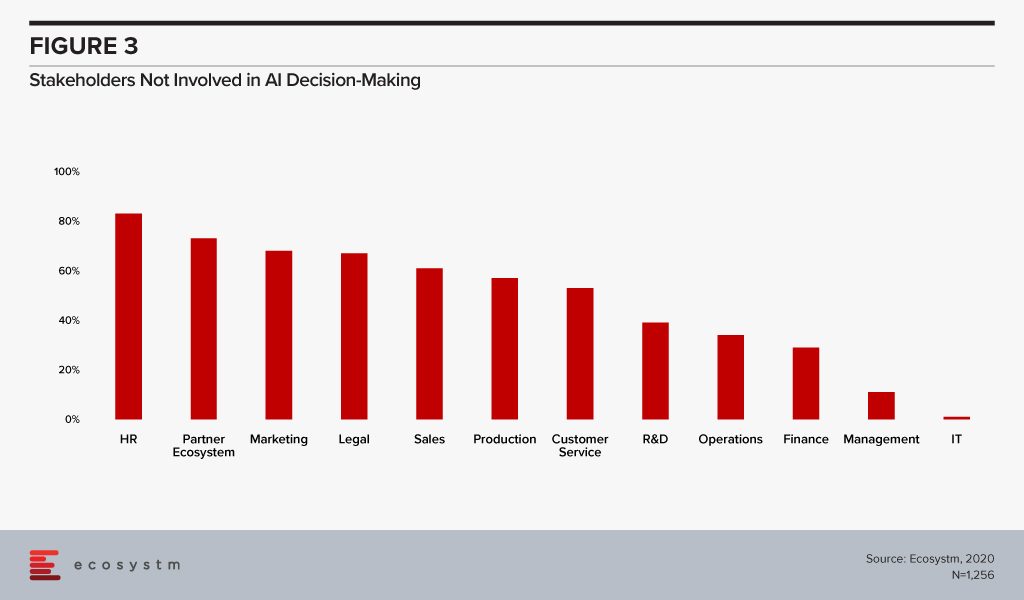
Moreover, internal IT may not have the right skills to implement and maintain an AI solution. It will become important for organisations to involve strategic partners who can guide the implementations, at least in the initial stages. While 51% of organisations that have an AI solution engage an external strategic partner, only 33% of organisations that are planning to adopt AI have planned for a strategic partner to guide them. A strategic partner – with the right technical expertise and business experience – can help combat some of the challenges around integration issues and provide guidance on cybersecurity best practices.
AI clearly has immense possibilities and indeed is a revolutionary technology that will bring value to almost all industries. What is required for a successful AI implementation however is a roadmap – including a cross-departmental Centre of Excellence (CoE), a clear timeframe and KPIs to measure both business and technological success of the AI models. Unless organisations can plan their AI investments, the technology will not translate from hype to reality.

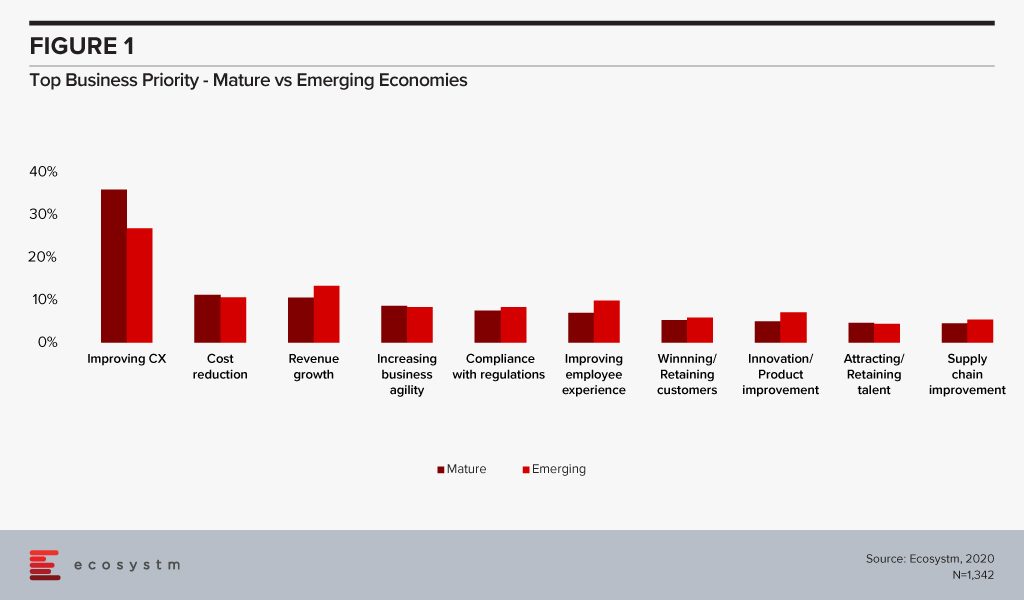
In the Top 5 Customer Experience Trends for 2020 Ecosystm Principal Advisors, Tim Sheedy and Audrey William say that emerging Asia will catch up with the mature economies of the world in their customer obsession. Have emerging economies really embraced Customer Experience (CX) fully or are they just responding to the hype? Do consumers really care about how they connect with brands or do organisations think product offerings is the main differentiator? The business priorities of global organisations reveal that there is a universal focus on improving CX (Figure 1). It is the top business priority across emerging and mature economies, though mature economies are still ahead in their customer focus. Organisations in emerging economies prioritise revenue growth and improving Employee Experience (EX) more than those in mature economies.
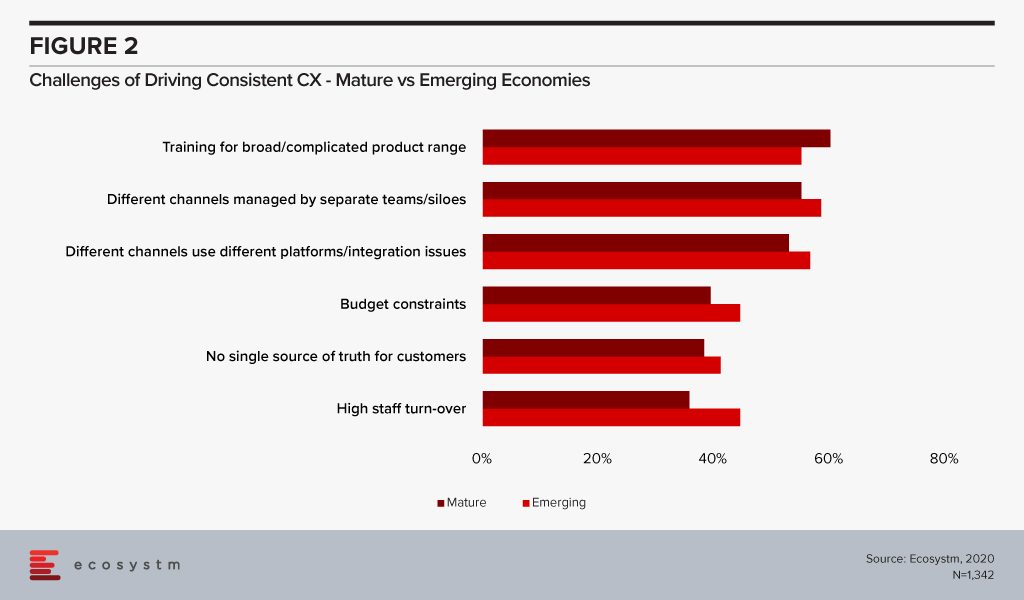
Delivering Better CX – The Challenges
Whether these organisations can actually fulfill their CX goals, depends on what their key challenges are. In the end, what consumers want is a consistent CX – across multiple channels and touchpoints. Organisations in emerging economies seem to find it more challenging to drive a more consistent CX (Figure 2). Information siloes are a challenge across all organisations. But organisations in mature economies cite training of their agents as their biggest challenge.
A desire to improve CX must be backed with both vision and budget. The vision should be for the entire organisation to have a single source of truth – not just for the employees – but also a common source of truth that is accessible easily and consistently by customers, across multiple channels. Without this, customer self-service measures will be inadequate. Increasingly customers will want to engage with brands when they want to (very often beyond working hours), how they want to (avoid lengthy voice calls) and where they want to (web and mobile apps). Interoperability of enterprise systems and a robust knowledge base are important factors.
How do Organisations Improve Service Delivery?
If we compare the top CX measures by organisations in mature and emerging economies, we notice a clear difference in priority. In mature economies, organisations appear to have a clear roadmap. They focus on the customers first; followed by empowering the staff to perform their jobs better; invest in technology that will enable both; work on process optimisation; and finally set KPIs and metrics to evaluate the efficacy of the CX measures in place. Also, what they are increasingly doing is setting CX KPIs across the entire organisation – involving all stakeholders. A customer-focused business is one where everything is second to the customers and that should be built firmly into the organisational culture.
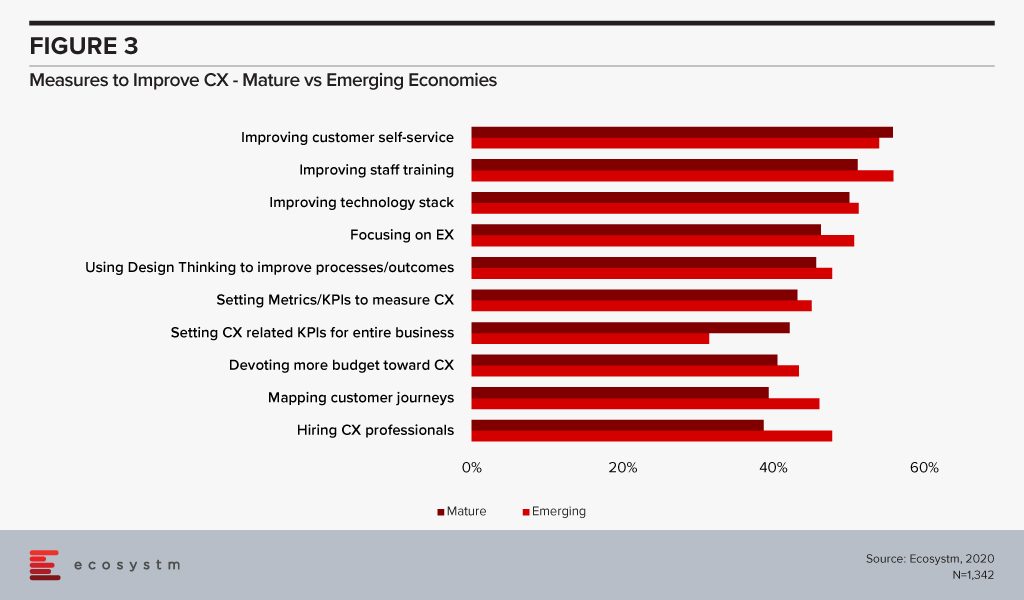
In emerging economies, organisations do not appear to follow a clear roadmap in their CX measures. While self-service is an important aspect of their CX programs, they are more tied down by improving their customer service staff capabilities. They are more challenged by high staff turnover (Figure 2) and appear to be focused on their employees in multiple ways – hiring experts, improving EX and investing in staff training. What they do far less than their counterparts from mature economies is setting organisation-wide CX KPIs.
Web apps are still the most important self-service CX touchpoint, followed by mobile apps. However, emerging economies are ahead when it comes to the importance they place on mobile apps for CX. This is reflective of the high mobile penetration in emerging economies, and the propensity to use mobile devices for all transactions – social and business.
We have seen that organisations in mature economies set CX KPIs more consistently. What are the top CX metrics and are there any differences based on the maturity of the economy (Figure 4)?
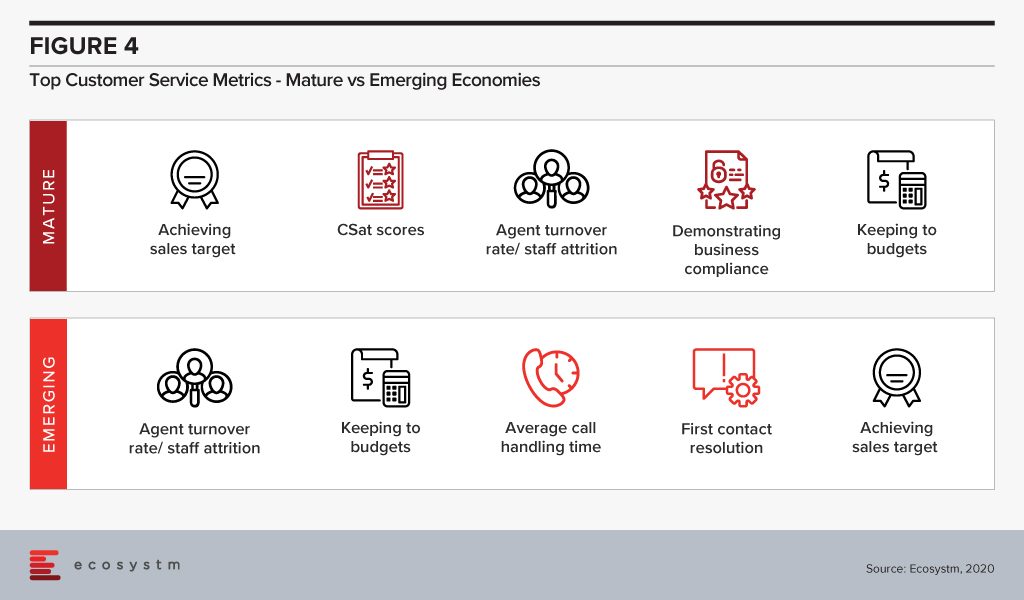
Organisations in emerging economies, continue to be more concerned about attracting and retaining employees. In fact, when asked about their security concerns, these organisations cite agents leaving with data as the key challenge. In mature economies, the key security challenge is improper use of confidential customer data, which can be handled best by continued staff training. In emerging economies, while organisations measure individual areas such as average call duration and first contact resolution, they do not measure customer satisfaction, in its entirety, using CSat scores, for instance. Organisations in mature economies are better at setting KPIs for their CX initiatives and tying them down to outcomes beyond the customer service teams – such as sales and adherence to compliance requirements.
Organisations in mature economies are focused on CX, but to become truly customer-obsessed they need to:
- Evaluate what will enable them to deliver better customer self-service – it is not only about apps, but also about the knowledge base
- Create a clear CX roadmap, focused on the multiple stakeholders and the technology – the steps have to be focused and not ad-hoc
- Inculcate customer obsession across the entire organisation – not just the customer-facing teams
In the Top 5 Cloud Trends for 2020, Principal Analyst Claus Mortensen observed that 2020 is a do-or-die year for Oracle if they wanted to remain as a key contender in the Cloud market. Mortensen said, “Oracle has not been able to break into Cloud in the same way as their competitors and has so far not made the same “leap of faith” into this area as similar companies have. Unless the company makes a clear decision about their Cloud strategy and succeeds in communicating it to the market in 2020, Oracle may quickly find itself more of a niche Cloud player going forward.”
Oracle’s intentions to remain one of the leading global Cloud providers becomes clear as they actively expand their global coverage. Last week Oracle announced that, as part of their ongoing regional expansion plan, they have added local regions in Jeddah (Saudi Arabia), Melbourne (Australia), Osaka (Japan), Montreal (Canada) and Amsterdam (The Netherlands). This expands the reach of Oracle’s Generation 2 Cloud to 21 independent locations, and Oracle intends to further add 15 locations by the end of 2020. At OpenWorld last year, Oracle had announced their plans to have Cloud sites dedicated to the enterprise market as well as government customers.
Dr Alea Fairchild, Principal Advisor Ecosystm, thinks that Oracle appreciates the needs of their enterprise customers. “Oracle understands the sensitivity of the enterprise to the location and availability of their data, which remains an issue with Cloud implementations involving large data sets. They have broken some ground as the first public Cloud vendor with data centres in Saudi Arabia, and are putting efforts in to offer a minimum of two regions in almost every country in which they operate,” says Dr Fairchild. “From a corporate user’s perspective, regional data management and appropriate licensing models are still sensitive spots when it comes to database management.”
Getting Ready for the Hybrid Cloud Market
Oracle also appears to be ramping up for the growing hybrid Cloud market. Ecosystm research shows that more than a third of global organisations have adopted the hybrid Cloud and this will only increase. Given the increased uptake of hybrid and multi-cloud environments, Oracle offers preconfigured links between Oracle and Microsoft Azure cloud regions in the eastern states of the US, London, and Toronto, as part of the Cloud interoperability partnership announced in June 2019. Last year, saw another mutually beneficial partnership between VMWare and Oracle, that supports their customers’ hybrid cloud strategies, allowing the VMware Cloud Foundation to run on Oracle Cloud Infrastructure. Organisations can also avail technical support for Oracle software running in VMware environments both in on-premise data centres and Oracle-certified cloud environments.
“Oracle’s Generation 2 Cloud is now available in 21 locations and is on track to have a total of 36 Cloud regions up and running by the end of the year,” adds Dr Fairchild. “But when compared to AWS, Microsoft and IBM, Oracle still holds a fraction of the market share. They can be seen as a niche infrastructure provider, but indeed the partnerships with Microsoft and VMware are set to help Oracle’s Cloud business make traction with companies that are adopting multi-cloud strategies.”
At the end of last year, Ecosystm published The Top 5 IoT Trends for 2020. Principal advisors, Kaushik Ghatak and Francisco Maroto predicted that in 2020 5G providers will be forced to operate outside their comfort zone. While the impact on network and communications equipment providers will be immense, 5G will also force telecom providers to re-think their existing business models. They may not be the best equipped to take 5G technology to market, they way the operate now.
Traditionally telecom providers have been focused on horizontal technologies and on connecting people. They have not had to have conversations around connecting machines – where every industry has their own unique use cases. This verticalisation, will force telecom providers to deal with newer stakeholders in their client organisations – not just IT infrastructure and Facilities. Several telecom providers have in the past become public cloud providers, as their markets becomes smaller and they face competition from global cloud storage providers. Now, telecom providers will increasingly look to partner with cloud providers and systems integrators with relevant industry experience, to translate the value proposition of what they are offering. “Strategic partnerships between leading technology and telecom operators are taking place especially in building various 5G use cases and applications centred on the cloud computing platform,” says Shamir Amanullah, Principal Advisor Ecosystm.
Maxis Strengthening their Market Position in Malaysia
The recently announced partnership between Maxis and Microsoft is an example of how these partnerships will pan out. Maxis does not want to be viewed only as a telecom provider and wants to be the leading Malaysia-based solutions provider. As telecom providers also start to tap the enterprise market, cloud and IoT will be key technology areas, that they should focus on.
“Maxis is leading the way as a converged solutions provider in Malaysia and following the appointment of Gökhan Ogut as the CEO in 2019, there has been a focus to grow the enterprise business which promises a lucrative opportunity,” says Amanullah.
“While the mobile connectivity market is effectively about customer retention in a saturated market, new opportunities lie in enterprise needs for fixed connectivity, managed services, cloud and IoT which is largely untapped. The expected deployment of the 5G network will spur new applications, business models and partnerships.”
Maxis’ move appears to be well-thought. Amanullah thinks that the strategic partnership with Microsoft will help Maxis accelerate its enterprise solutions offering combined IoT and 5G capabilities with Microsoft’s Azure IoT technology. It will also allow for hybrid environments, which is important given the rise of hybrid and multi-cloud adoption. Ecosystm research shows that hybrid cloud adoption in Malaysia is at a nascent 7%. But if they take a lesson from their neighbour, the rise in adoption will be steep. Our research finds that hybrid cloud adoption in Singapore is around 42%.
Telecom providers are also focusing on Digital Transformation (DX). In the Top 5 Telecommunications & Mobility Trends for 2020, Liam Gunson, Director Ecosystm says, “In 2020, operators will focus on transforming the core – remove unnecessary costs, improve customer experience, capture new opportunities – and on building telecom networks with scalability, flexibility, efficiency and agility.” Microsoft’s enterprise Modern Workplace solutions including Microsoft Teams will aid Maxis’ own DX efforts. Maxis will offer fixed line voice calls with the unified communications service.
Mutually Beneficial Partnership
Amanullah also sees this as a positive move for Microsoft. “Microsoft is poised to lead efforts in 5G network deployment which promises to enhance capabilities and drive new economic growth, especially with the focus on Industry 4.0. Maxis’ position as a leading enterprise communications provider and Microsoft’s enterprise technology experience and offerings promises a mutually beneficial partnership.”
Ecosystm research finds that Microsoft is the leading cloud provider in Malaysia when it comes to brand perception, and about a third of enterprise cloud deployments use Microsoft. Amanullah thinks that, “Microsoft’s leading position in cloud platforms is an attractive proposition for enterprises that are looking at speed, performance, reliability, global scale, security and lower costs.”
Talking about the 5G applications that the Malaysia market will see, Amanullah sees tremendous business opportunities in areas such as smart city, autonomous driving, smart traffic management, virtual reality (VR), augmented reality (AR), cloud gaming, and healthcare, to name a few.
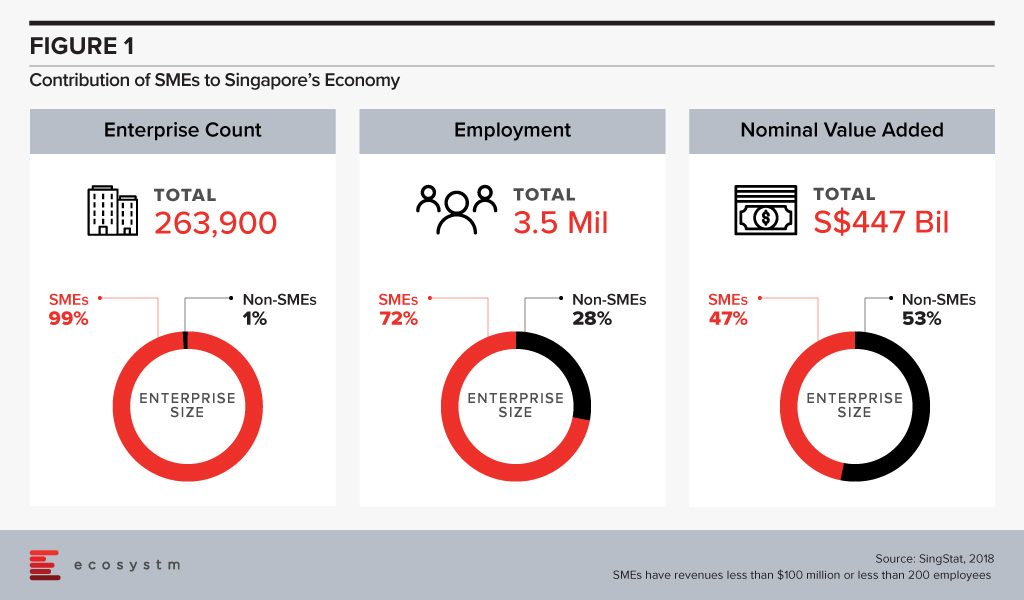
Singapore maintains its competitiveness through strong Government support and an environment that encourages trade and investments. The economy sees a huge contribution from start-ups and small and medium enterprises (SMEs), which receives financial incentives and technology guidance from the Government.
The success of SMEs in Singapore is at the core of national economic growth with approximately 261,000 SMEs contributing to nearly 50% of the country’s GDP.
A survey conducted by United Overseas Bank (UOB) in November 2019 illustrates that SMEs in Singapore are focusing on boosting productivity as they grapple with macro-economic and socio-political uncertainties this year. The UOB survey included 615 local SMEs with a revenue of less than S$100 million. Nearly half of the SMEs surveyed have a positive outlook for their business in 2020, while nearly a third are not so optimistic about it.
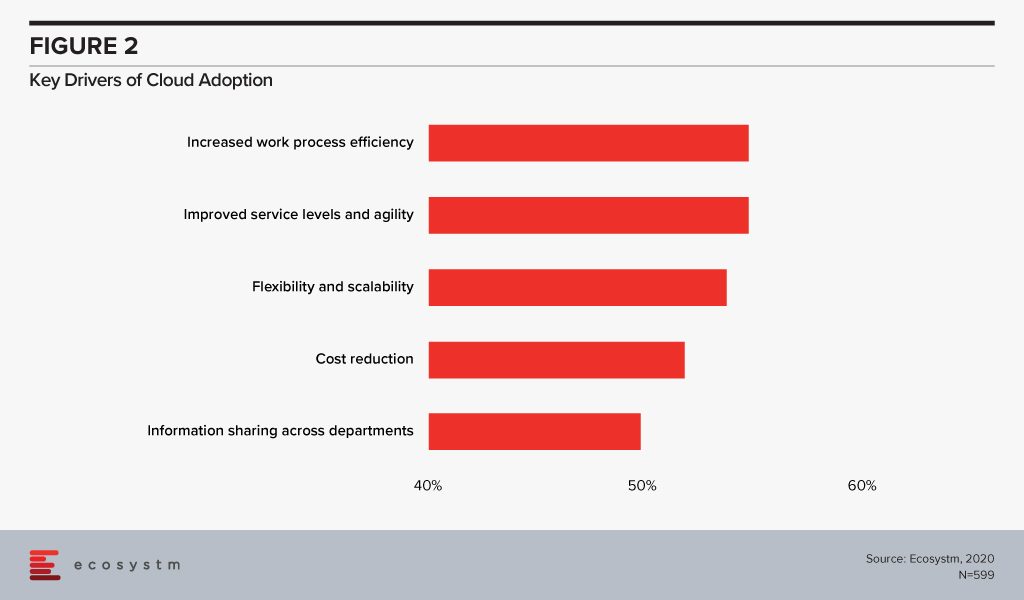
While cost reduction and new streams of revenue generation are top business priorities, more than half of the SMEs polled, mentioned increasing productivity as their top priority. Technology adoption has often been linked to an increase in productivity. SMEs in Singapore appear to be on the right track as currently 65% use digital solutions, mostly geared towards accounting, HR and customer relationship management. Digitalisation involves a widespread adoption of cloud and automation solutions. If we look at the key drivers of cloud adoption across all global organisations (Figure 2), we find that optimisation and productivity are key incentives.
Interestingly, the UOB survey also finds that more than half of SMEs in Singapore have sustainability goals. Resource optimisation and energy efficiency will also see higher adoption of technology in the future.
Government Initiatives Empowering SMEs
Government agencies and industry bodies have always been proactive in empowering SMEs with technological knowledge. There are various programs and initiatives to promote digitalisation, which have made Singapore SMEs competitive at a global level.
The Infocomm Media Development Authority (IMDA) is helping Singapore SMEs to scale and improve their digital capabilities, expand their network and go global through collaboration with multinational companies (MNCs). The SMEs Go Digital program launched in 2017, has seen an estimated 4,000 SMEs adopting pre-approved digital solutions.
Several organisations in Singapore – such as A*Star and Enterprise Singapore – have targeted programs for the SME community. One of the key challenges for SMEs that impacts their ability to invest in technology is a lack of internal IT skills. Initiatives such as the Technology Adoption Programme (TAP) recognise this and bring in multiple industry and technology stakeholders to translate new technologies into Ready-to-Go (RTG) solutions, aimed at SMEs.
Apart from technology, access to financing is a key factor that determines the success of an SME and remains a key focus of Singapore’s banking and financial sector. The digital wholesale licenses are also aimed at SME financing, especially targeting those that are unable to procure funds from traditional sources.
Technologies Enabling Digitalisation in Singapore SMEs
Cloud
As mentioned earlier, cloud is the key enabler of digitalisation, giving organisations the ability to access solutions anywhere and anytime. Ecosystm research shows that 80% of SMEs in Singapore use an IaaS solution, while more than 75% use a SaaS solution.
There are programs that boost cloud adoption in Singapore SMEs as well. As an example, SMECEN, developed by the Association of Small & Medium Enterprises (ASME), and supported by Enterprise Singapore, Accounting and Corporate Regulatory Authority (ACRA) and Inland Revenue Authority of Singapore (IRAS) is a SaaS solution with accounting, HR and compliance modules – integration with other business tools is on the cards.
AI/Automation
Digitalisation will eventually involve investments in Automation and AI. For Singapore, AI is a key technology as it continues to focus on IoT, smart buildings, smart electricity, autonomous electric vehicles and other smart city solutions. The Government is working to open up access to data and AI tools so everyone can experiment. It especially wants to encourage SMEs to adopt AI and work on government use cases.
Singapore SMEs are ramping up their AI investments, especially in IoT sensor analytics (27%), machine learning (21%) and robotic process automation (16%), according to the Ecosystm AI study. Their key short-term drivers are insights into the competition and enhanced internal process monitoring. However, in the longer term, they are looking at cost reduction and better profit margins.
Fintech
According to an OCBC survey in 2018, which polled 200 such companies, two-thirds of SMEs in Singapore are likely to go cashless by 2023. It is estimated that over 75% of Fintech transactions in Singapore are digital payments and it receives over a quarter of Fintech funding. Government initiatives such as FAST and SGQR, have opened up digital payment options for consumer use as well as for SMEs.
However, the UOB survey notes some concerns that SMEs have over digital payments adoption, including customer/supplier acceptance and security. This is an encouraging sign, which indicates that SMEs are not just adopting technology because of the hype – but are evaluating the pros and cons of tech adoption before embarking on a digitalisation project.

The telecommunications industry has long been an enabler of Digital Transformation (DX) in other industries. Now it is time for the industry to transform in order to survive a challenging market, newer devices and networking capabilities, and evolving customer requirements. While the telecom industry market dynamics can be very local, we will see a widespread technology disruption in the industry as the world becomes globally connected.
Drivers of Transformation in the Telecom Industry
Remaining Competitive
Nokia Bell Labs expects global telecom operators to fall from 10 to 5 and local operators to fall from 800 to 100, between 2020 and 2025. Simultaneously, there are new players entering the market, many leveraging newer technologies and unconventional business models to gain a share of the pie. While previous DX initiatives happened mostly at the periphery (acquiring new companies, establishing disruptive business units), operators are now focusing on transforming the core – cost reduction, improving CX, capturing new opportunities, and creating new partner ecosystems – in order to remain competitive. There is a steady disaggregation in the retail space, driving consolidation in traditional network business models.
“The telecom industry is looking at gradual decline from traditional services and there has been a concerted effort in reducing costs and introducing new digital services,” says Ecosystm Principal Advisor, Shamir Amanullah. “Much of the telecom industry is unfortunately still associated with the “dumb pipe” tag as the over-the-top (OTT) players continue to rake in revenues and generate higher margins, using the telecom infrastructure to provide innovative services.”
Bringing Newer Products to Market
Industries and governments have shifted focus to areas such as smart energy, Industry 4.0, autonomous driving, smart buildings, and remote healthcare, to name a few. In the coming days, most initial commercial deployments will centre around network speed and latency. Technologies like GPON, 5G, Wifi 6, WiGig, Edge computing, and software-defined networking are bringing new capabilities and altering costs.
Ecosystm’s telecommunications and mobility predictions for 2020, discusses how 5G will transform the industry in multiple ways. For example, it will give enterprises the opportunity to incorporate fixed network capabilities natively to their mobility solutions, meaning less customisation of enterprise networking. Talking about the opportunity 5G gives to telecom service providers, Amanullah says, “With theoretical speeds of 20 times of 4G, low latency of 1 millisecond and a million connections per square kilometre, the era of mobile Internet of Everything (IoE) is expected to transform industries including Manufacturing, Healthcare and Transportation. Telecom operators can accelerate and realise their DX, as focus shifts to solutions for not just consumers but for enterprises and governments.”
Changing Customer Profile
Amanullah adds, “Telecom operators can no longer offer “basic” services – they must become customer-obsessed and customer experience (CX) must be at the forefront of their DX goals.” But the real challenge is that their traditional customer base has steadily diverged. On the one hand, their existent retail customers expect better CX – at par with other service providers, such as the banking sector. Building a customer-centric capability is not simple and involves a substantial operational and technological shift.
On the other hand, as they bring newer products to market and change their business models, they are being forced to shift focus away from horizontal technologies and connecting people – to industry solutions and connecting machines. As their business becomes more solution-based, they are being forced to address their offerings at new buying centres, beyond IT infrastructure and Facilities. Their new customer base within organisations wants to talk about a variety of managed services such as VoIP, IoT, Edge computing, AI and automation.
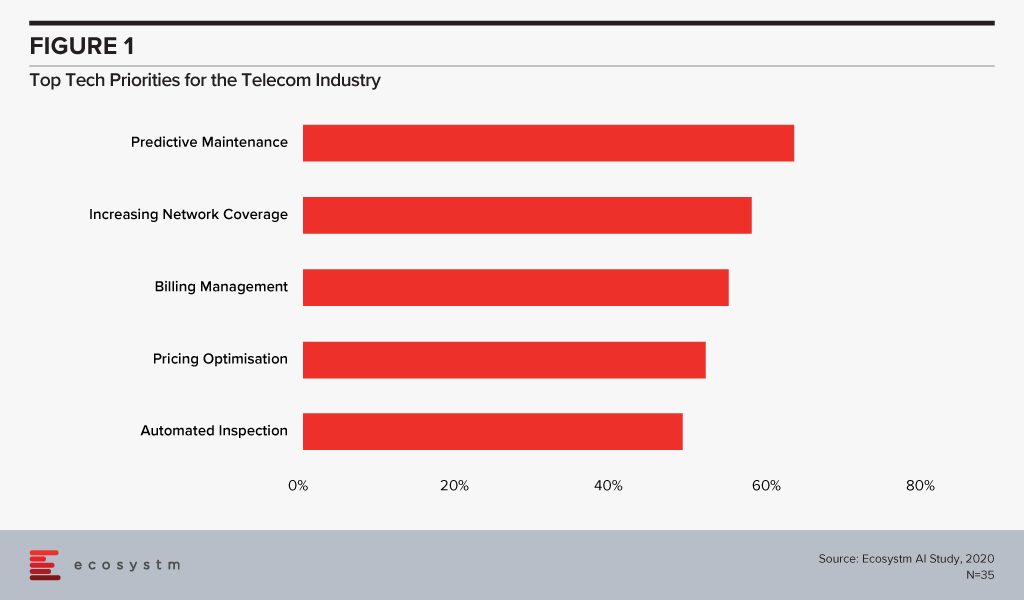
The global Ecosystm AI study reveals the top priorities for telecom service providers, focused on adopting emerging technologies (Figure 1). It is very clear that the top priorities are driving customer loyalty (through better coverage, smart billing and competitive pricing) and process optimisation (including asset maintenance).
Technology as an Enabler of Telecom Transformation
Several emerging technologies are being used internally by telecom service providers as they look towards DX to remain competitive. They are transforming both asset and customer management in the telecom industry.
IoT & AI
Telecom infrastructure includes expensive equipment, towers and data centres, and providers are embedding IoT devices to monitor and maintain the equipment while ensuring minimal downtime. The generators, meters, towers are being fitted with IoT sensors for remote asset management and predictive maintenance, which has cost as well as customer service benefits. AI is also unlocking advanced network traffic optimisation capabilities to extend network coverage intelligently, and dynamically distribute frequencies across users to improve network experience.
Chatbots and virtual assistants are used by operators to improve customer service and assist customers with equipment set-up, troubleshooting and maintenance. These AI investments see tremendous improvement in customer satisfaction. This also has an impact on employee experience (EX) as these automation tools free workforce from repetitive tasks and they be deployed to more advanced tasks.
Telecom providers have access to large volumes of customer data that can help them predict customer usage patterns. This helps them in price optimisation and last-minute deals, giving them a competitive edge. More data is being collected and used as several operators provide location-based services and offerings.
In the end, the IoT data and the AI/Analytics solutions are enabling telecom service providers to improve products and solutions and offer their customers the innovation that they want. For instance, Vodafone partnered with BMW to incorporate an in-built SIM that enables vehicle tracking and provides theft protection. In case of emergencies, alerts can also be sent to emergency services and contacts. AT&T designed a fraud detection application to look for patterns and detect suspected fraud, spam and robocalls. The system looks for multiple short-duration calls from a single source to numbers on the ‘Do Not Call’ registry. This enables them to block calls and prevent scammers, telemarketers and identity theft issues.
Cybersecurity
Talking about the significance of increasing investments in cybersecurity solutions by telecom service providers, Amanullah says, “Telecom operators have large customer databases and provide a range of services which gives criminals a great incentive to steal identity and payment information, damage websites and cause loss of reputation. They have to ramp up their investment in cybersecurity technology, processes and people. A telecom operator’s compromised security can have country-wide, and even global consequences. As networks become more complex with numerous partnerships, there is a need for strategic planning and implementation of security, with clear accountability defined for each party.”
One major threat to the users is the attack on infrastructure or network equipment, such as routers or DDoS attacks through communication lines. Once the equipment has been compromised, hackers can use it to steal data, launch other anonymous attacks, store exfiltrated data or access expensive services such as international phone calls. To avoid security breaches, telecom companies are enhancing cybersecurity in such devices. However, what has become even more important for the telecom providers is to actually let their consumers know the security features they have in place and incorporate it into their go-to-market messaging. Comcast introduced an advanced router to monitor connected devices, inform security threats and block online threats to provide automatic seamless protection to connected devices.
Blockchain
Blockchain can bring tremendous benefits to the telecom industry, according to Amanullah. “It will undeniably increase security, transparency and reduce fraud in areas including billing and roaming services, and in simply knowing your customer better. With possibilities of 5G, IoT and Edge computing, more and more devices are on the network – and identity and security are critical. Newer business models are expected, including those provided for by 5G network slicing, which involves articulation in the OSS and BSS.”
Blockchain will be increasingly used for supply chain and SLA management. Tencent and China Unicom launched an eSIM card which implements new identity authentication standards. The blockchain-based authentication system will be used in consumer electronics, vehicles, connected devices and smart city applications.
Adoption of emerging technologies for DX may well be the key to survival for many telecom operators, over the next few years.

The race for digital bank licenses in Singapore is on as the Monetary Authority of Singapore (MAS) deadline for applications closed at the end of last year.
The Singapore Government continues to promote fintech initiatives in the banking industry such as the FAST network (giving fintech and non-banking organisations access to the real-time payments network) and Project Ubin (focusing on inter-bank funds transfer using Blockchain). The digital bank licenses continue in the same vein and will offer the same banking services as traditional banks but operate online and without any physical infrastructure.
“The biggest gamechanger of the app-based and shared economy is that it puts the power of decision making and choice in the hands of the consumer. It also removes entry barriers for non-traditional market entrants, but the flipside is it also weakens a number of regulatory barriers that were put in place for safeguarding the consumer,” says Amit Gupta, Ecosystm CEO. “With digital banking at the verge of becoming mainstream, it will help spur the app-based economy with the advent of more complete ecosystems and the added benefit of stronger governance measures and frameworks that will come into play simply because financial regulators in Singapore are driving it.”
Digital banking is not new, and MAS has been encouraging banks to offer digital services since 2000. Taking it a step forward, in June 2019, MAS announced their intentions to issue 5 digital bank licences in Singapore, opening up the banking industry to the non-banking sector.
Following the announcement, in August 2019, MAS invited applications for 2 digital full banks (DFBs) aimed primarily at retail banking, and 3 digital wholesale banks (DWBs) primarily for SMEs and other non-retail segments. While DFB licenses are restricted to Singapore based companies (including foreign joint ventures with a Singapore entity and headquarters), DWB licenses have no such restrictions, opening the market to overseas players.
Applicants for the New Digital Bank License
MAS announced on January 7, 2020, that it had received 21 applications (7 for DFB and 14 for DWB licenses). A list of applicants has not been made available, and confirmation of application has typically come from the applicants themselves. The licences will be issued in mid-2020 with the commencement of business expected about a year later.
The race for the digital bank license in Singapore has seen several non-banking contenders. MAS has mentioned that applicants will be selected based on their market reputation, a proven track record, financial strength, innovative business models, and a commitment to develop the skills of the Singaporean workforce. The contenders who have announced their applications cover a wide range – from the Sea Group (whose eCommerce site, Shoppee has a strong presence in Singapore) to the Enigma Group (a financial organisation based in the UK). Here are some organisations that may well be ahead of the race:
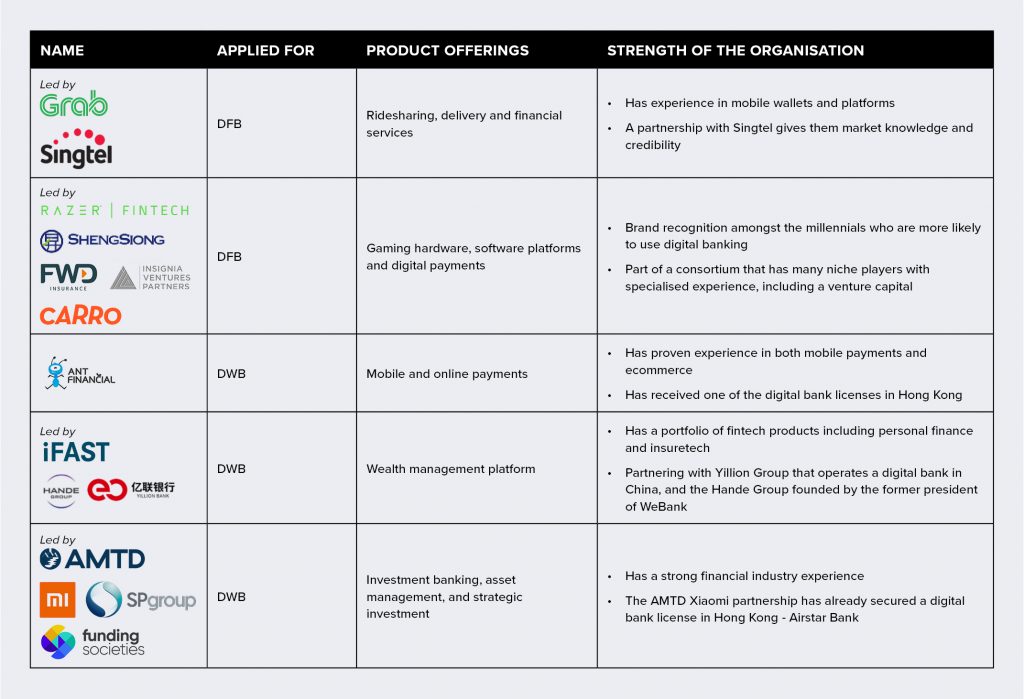
“From the nature of consortium of bidders for DFBs and DFWs in Singapore, we can safely anticipate that the financial ecosystems will be aligned very closely with certain consumer demographics that make up the core target segments. As an example, Razer will be in a position to meet the specific needs of the millennial consumer base,” adds Gupta. “In saying that, it will also be important to evaluate how digital banks deal with educating consumers on wealth creation offerings and financial literacy, which is currently being achieved through personal touchpoints by the traditional banks.”
Ecosystm Comments
Singapore has emerged as one of the global leaders in fintech due largely to the maturity of the technology infrastructure, the banking sector and data compliance laws, as well as the tech-savviness of its citizens. The buzz created in the market when MAS announced the initiative last year is partly because a successful implementation in Singapore carries weight globally, especially in the relatively untapped Southeast Asian market.
Singapore also collaborates with the countries in the region empowering them with talent development and co-creation of fintech solutions. Initiatives such as the ASEAN Financial Innovation Network (AFIN) further promote fintech adoption through its open-architecture platform. Several countries in the region will take inspiration from Singapore and evaluate digital banks as a means to better financial inclusion. Thailand’s central bank has already indicated its interest in digital banks, prompted by the Singapore and Hong Kong initiatives.
Talking specifically about the competition in the Singapore financial industry, Gupta says, “Unlike some of the other markets, traditional banks in Singapore will continue to offer competing digital offerings as local banks such as DBS have been very savvy in building their digital offerings over the years. If their digital innovation keeps evolving at the pace they have been setting in recent years, they will present very stiff competitive barriers to the new digital bank entrants, especially given their ability to continue offering personalised service and touchpoints, coupled with compelling digital offerings.”
Insight Partners – an American venture capital and private equity firm based in New York City – has announced that it will acquire Veeam at a valuation of US$5 billion. Last year, Insight Partners invested US$500 Million in Veeam to boost its growth as a data management solutions provider for cloud environments.
The news comes days after Insight Partners confirmed another significant acquisition of Israeli IoT security start-up, Armis at a valuation of US$1.1 billion.
The deal between the venture capital firm and the Switzerland-based cloud data management company is expected to close in the first quarter of this year. With its acquisition by Insight Partners, Veeam’s growth is expected to accelerate into new geographies especially the US market.
Veeam was founded in 2006 and has a portfolio including backup solutions, security offerings and data management solutions for virtual environments and more recently cloud native platforms such as AWS and Microsoft Azure. The company was ranked #27 on the Forbes 2019 Cloud 100 list and has a global customer base of 365,000, including 81% of the Fortune 500 companies. Veeam has partnerships with large enterprise vendors and resellers such as IBM, Dell EMC, Lenovo, HPE, NetApp and Cisco.
The acquisition comes almost a year after the initial U$500 million investment by Insight Partners and Veeam’s announcement of ‘Act II” of its growth strategy – expanding its data management capabilities from virtual environments to the cloud. This move is a logical progression of Veeam’s successful ‘Act I’ as Ullrich Loeffler, Ecosystm Chief Operating Officer mentioned in an earlier blog. However, Loeffler notes, “Executing on ‘Act II’ significantly increases the complexity of Veeam’s business across product portfolio, technology partnerships, SaaS applications and addressable markets. Insight Partners will enable Veeam to fast track this transition from the top down by leveraging additional funding and dedicated internal growth teams and experience from over 200 M&As and 40+ IPOs.”
Veeam’s leadership team is expected to change significantly with the company now moving its headquarters from Switzerland to the US. Co-founders Andrei Baronov and Ratmir Timashev will step down from their positions on the board and in the operation, making way for an US leadership team.
Phil Hassey, Principal Advisor Ecosystm, states that the new ownership and announced leadership team under CEO Bill Largent is a gamechanger for Veeam. “Veeam simply had no choice. It has had limited US penetration to date and has been restricted from growth by the ownership structure despite best efforts on their part. It has had to back out of a significant acquisition deal, divesting N2WS after failing to get full regulatory approval in the US,” Hassey says. “In my view, this acquisition is about more than Veeam’s intention to deepen its product portfolio. It is about ensuring an access to the US market in a level playing field and it will also help with the hyper cloud vendor relationships given their strong push to US Federal Government and their US home turf.”
However, while Loeffler also sees the acquisition as a step towards an IPO, he warns, “The rapid transition to a US leadership team is likely to impact Veeam’s unique company culture. Clients repeatedly state the ease of engagement as key selection criterion, besides the solution capabilities, when choosing to partner with Veeam. The fact that both co-founders will not just step off the board but also leave as Veeam employees, will create a gap which will be challenging to fill.”