Earlier this month, Telefónica Germany announced it will use Amazon Web Services (AWS) to virtualise its 5G core for a proof of concept (POC) in an industrial use case and plans to move to commercial deployment in 2021. Part of the POC process is to ensure compliance with all applicable data protection guidelines and certifying them according to relevant industry standards.
“With the virtualisation of our 5G core network, we are laying the foundation for the digital transformation of the German economy. This collaboration with AWS is an important part of our strategy for building industrial 5G networks”, said Markus Haas, CEO of Telefónica Germany.
Sentiment about cloud – especially public cloud – has been on a slight roller-coaster ride since they emerged back in the “noughties”: From initial reluctance to reluctant acceptance – to customer driven enthusiasm to scaling back and migrating back data and apps to on-premises data centres or private clouds to a more recent acceptance, that most enterprise resources may work best in a hybrid or public cloud environment.
Still, the viewpoint of many is still that core resources for the most part belong on-premises – especially if they are essential for the running of the business or involves sensitive data.
It is in this light that the Telefónica Germany announcement is interesting. On the face of it, it may appear that this is a possible major validation of public cloud as a platform for core systems and sensitive data. Although the core network components will remain on a different platform delivered by Ericsson, there is clearly an element of that.
Perception on Public Cloud
Many organisations remain sceptical with regards to public cloud. Ecosystm data shows that almost 40% have private cloud as their primary cloud deployment model (Figure 1); roughly a third have gone for a hybrid model and only around one quarter have chosen a public cloud model.
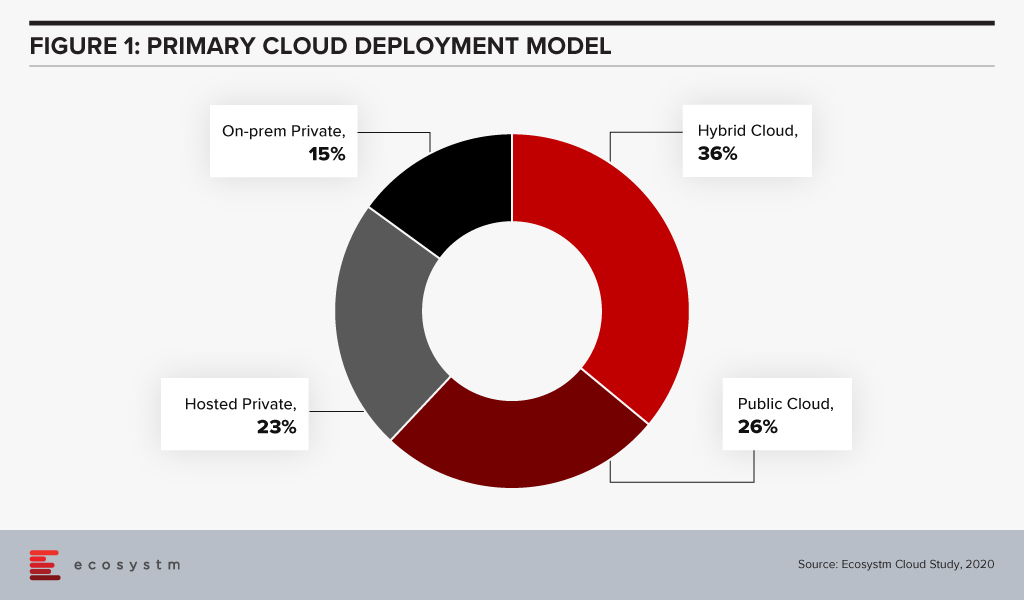
Most cloud deployment strategies ultimately come down to an evaluation of cost vs. risk and this evaluation is clearly demonstrated in Ecosystm data. Close to 80% of those choosing an on-premises private cloud model mention security and compliance as a main reason whereas cost considerations are the main reason for those opting for a public cloud model (Figure 2). What our data also shows is that public cloud providers are not necessarily winning the argument of cost savings among users.
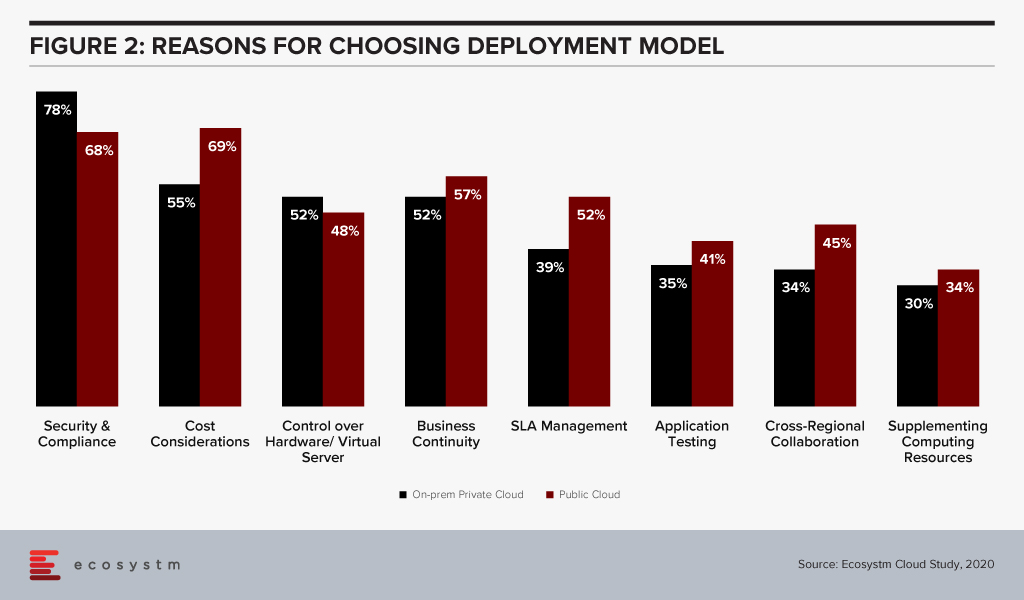
For many organisations today, security and compliance concerns are still a valid point against public cloud as a primary deployment model. However, as we see more and more initiatives like Telefónica Germany, this argument diminishes – and it will become harder for IT organisations to convince senior management that this is still the way to go.
The Edge Complements the Cloud
The other noteworthy take-away from the Telefónica Germany initiative is how cloud-enabled edge computing is being embraced by the network design to ensure lower latencies for those who need it. The company states, “If companies use 5G network functions based on the cloud-based 5G core network of Telefónica Germany / O2 in the future, they will no longer need a physical core network infrastructure at their logistics and production sites, for example, but only a 5G radio network (RAN) with corresponding antennas.”
As I’m sure that you are an avid reader of Ecosystm Predicts every year, this should not come as a surprise as we wrote about something like this in the Top 5 Cloud Trends for 2020. Although some are touting Edge computing as the ultimate replacement of Cloud, we then believed – and still do – that it will be complimentary rather than competing technology. Cloud-based setups can benefit from pushing computing heavy workloads to the Edge in much the same way as IoT and provides a great platform for managing the Edge computing endpoints.
But to go back to the private cloud bit – while private cloud is not going away in the foreseeable future, we may be starting to see its demise in the more distant future.
To paraphrase a famous Brit: Now this is not the end. It is not even the beginning of the end. But it is, perhaps, the end of the beginning for private cloud.
Identifying emerging cloud computing trends can help you drive digital business decision making, vendor and technology platform selection and investment strategies.Gain access to more insights from the Ecosystm Cloud Study.

Alibaba has been actively expanding its global reach over the last year. There have been several announcements this year to indicate that the cloud provider is looking to benefit from the recent uptick in cloud adoption and support the global recovery initiatives. In April, Alibaba announced its plans to invest USD 28 billion, focusing on infrastructure and technologies related to operating systems, servers, chips and networks, over the next three years. Later in June, Alibaba announced the intention to recruit 5,000 people globally showing serious intentions to become a global cloud player. It is also strengthening capabilities in markets where they already have a strong market presence. By 2021 Alibaba intends to have 64 availability zones with 21 regions across the globe.
Consolidating Partnership with Equinix
Alibaba’s partnership with Equinix, the interconnection and data centre company dates back a few years. In 2017 the partnership started providing enterprises with direct, scalable access to Alibaba Cloud via the Equinix Cloud Exchange in 5 of their global data centres.
Last week the partnership was further strengthened by Equinix extending the reach of Alibaba Cloud via its network of Equinix Cloud Exchange Fabric (ECX Fabric) Cloud interconnection platform. The deal will widen Alibaba’s cloud reach in the US, EMEA, and the Asia Pacific region for customers to privately connect with Alibaba’s cloud. Under the partnership, Alibaba will integrate its API with Equinix ECX Fabric to facilitate direct and secured connections to Alibaba Cloud, across these regions:
- 9 US metros. Chicago, Dallas, Denver, Los Angeles, Miami, New York, Seattle, Silicon Valley and Washington DC
- 5 Asia Pacific hubs. Hong Kong, Jakarta, Singapore, Sydney and Tokyo
- 3 hubs in EMEA. Dubai, Frankfurt and London
The deal also gives Alibaba direct access to Equinix’s interconnected ecosystem of over 9,700 customers including enterprises, cloud and network operators, and IT service providers.
The Hybrid Cloud Push
In the last 18 months or so, the industry has seen a greater push in private/hybrid cloud or multi-cloud adoption. Ecosystm Principal Advisor Andrew Milroy says, “As enterprises move to hybrid cloud infrastructures, the world’s leading IaaS providers, including Alibaba Cloud, are expanding their private cloud and hybrid cloud services.”
Many of these IaaS providers may not have the capabilities to provide a hybrid cloud offering at a global level. Partnerships such as the one between Equinix and Alibaba Cloud may well be the solution. Milroy says, “Equinix offers interconnection services from multiple sites across the globe. These interconnection services are necessary for the provision of private and hybrid cloud services, on a global scale, offering the level of performance and security that organisations want.”
“In order to compete with AWS, GCP and Microsoft, Alibaba Cloud needs to be able to scale its private and hybrid cloud offerings globally. Equinix can enable them to do this. At the same time, Equinix will also benefit from Alibaba Cloud’s growth into newer markets, which will lead to an increased demand for its interconnection services.”
Organisations across the globe, are facing disruption on a scale never seen before, and are urgently seeking ways of remaining viable. Predictably, cybersecurity is a secondary concern and is often handled reactively. To make matters worse, a chronic cybersecurity skills shortage is being made much more severe by the crisis.
Remote working has reached unprecedented levels as organisations try hard to keep going. This is massively expanding the attack surface for cyber criminals, weakening security and leading to a cybercrime pandemic. Hacking activity and phishing, inspired by the COVID-19 crisis, are growing rapidly. Containing and suppressing this cybercrime pandemic is proving to be almost impossible.
Remote working intensifies known threats posed by phishing and ransomware. More alarming are the distinctive cybersecurity vulnerabilities associated with home working including reliance on home Wi-Fi, increased use of unpatched VPNs and devices, and the exponential growth of network access points. These vulnerabilities increase the likelihood of a breach enormously.
Corporate IT is in a very challenging position. It needs to ensure that organisations can operate in a way that they have never operated before, while ensuring that their assets are secure – a very difficult, if not an impossible task for which there is no precedent.
Some important cybersecurity considerations, during and after the COVID-19 pandemic include:
Re-enforce Basic Cyber Hygiene
As massive numbers of people work from home, basic cyber hygiene becomes more critical than ever before. Organisations must maintain awareness of security threats among employees, ensure security policies are being followed and be certain that corporate software is being updated and patched on time. With a dispersed workforce, these basic practices are more challenging, and training becomes more critical. Phishing attacks are often the primary attack vector for malicious actors, so employees must be able to identify these attacks. They increasingly exploit shortages of goods such as protective equipment and sometimes claim to offer official information relating to COVID-19.
Remote employees often access sensitive business data through home Wi-Fi networks that will not have the same security controls – such as firewalls – that are used in offices. There is more connectivity from remote locations, which requires greater focus on data privacy, and hunting for intrusions from a much larger number of entry points.
Place More Focus on Endpoint Security
The unprecedented switch to remote working is radically increasing the number of vulnerable endpoints. Given that endpoints are located at a distance from corporate premises, it is frequently difficult for IT departments to configure endpoint systems and install necessary security software.
It is vital to assess the security posture of all endpoints connecting to the corporate network. This practice enables an organisation to determine whether or not an endpoint requesting to access internal resources meets security policy requirements. It requires the ability to monitor and enforce policy across all devices, while making onboarding and offboarding seamless.
It is essential that endpoint solutions can be rapidly deployed for remote workers, as needed on both personal and corporate devices. Devices used for remote work need much more than the basic antivirus and antispyware protection. Multi-factor authentication (MFA) and on-board endpoint detection and response (EDR) capabilities are crucial.
Be More Selective About How and When Video Conferencing and Collaboration Platforms are Used
Since lockdowns spread around the world, the use of video conferencing and collaboration tools has grown beyond the wildest expectations of suppliers of these tools. The extraordinary growth of Zoom has made it a target for attackers. Many security vulnerabilities have been discovered with Zoom such as, a vulnerability to UNC path injection in the client chat feature, which allows hackers to steal Windows credentials, keeping decryption keys in the cloud which can potentially be accessed by hackers and gives the ability for trolls to ‘Zoombomb’ open and unprotected meetings. Zoom has so far managed to augment its security features in part by its recent acquisition of Keybase, a secure messaging service.
Switching to an alternative video conferencing platform will not necessarily offer greater levels of security as privacy is typically not a strength of any collaboration platform. Collaboration platforms tend to tread a fine line between a great experience and security. Too much security can cause performance and usability to be impacted negatively. Too little security, as we have seen, allows hackers to find vulnerabilities. If data privacy is critical for a meeting, then perhaps collaboration platforms should not be used, or organisations should not share critical information on them.
Protect all Cloud Workloads
In today’s remote working paradigm, cloud computing is being used more than ever. This frequently exposes organisations to risks that are not adequately mitigated.
Organisations typically need to manage a mix of on-premises technology together with multiple clouds, which are often poorly integrated. These complexities are compounded by the increasing risk from cyberattacks associated with cloud migration and hybrid cloud implementations. In cloud environments, the leading cybersecurity risks include insecure interfaces and APIs, data breaches and data loss, unauthorised access, DDoS attacks, and a lack of a unified view of assets.
Protection requirements for securing hybrid multicloud environments are evolving rapidly. In addition to tightening up endpoint security, organisations must also place greater emphasis on cloud workload protection. Cloud security solutions need to offer a unified and consistent view across all physical machines, virtual machines, serverless workloads and containers, used by an organisation.
Amend Incident Response Plans
It is the containment of breaches that often determines the success of security policies and procedures. Basic cyber hygiene as well as changes to IT architecture, such as micro segmentation, play an essential role in breach containment. But incident response plans also need to be made relevant to the current pandemic scenario.
Employees and IT teams are now working in a completely different environment than envisaged by most incident response plans. Existing plans may now be obsolete. At the very least, they will need to be modified. Usually, incident response plans are designed to respond to threats when most employees are operating in a corporate environment. This clearly needs to change. Employees need to be trained in the updated plan and know how to reach support if they believe that a security breach has occurred in their remote location.
Critically, new alert and warning systems need to be established, which can be used by employees to warn of threats as well as to receive information on threats and best practices.
Organisations are struggling to keep the lights on. In this battle to remain operational, cybersecurity has been taking a back seat. This cannot last for long as the deluge of new vulnerabilities is creating easy pickings for attackers. Cyber hygiene, endpoint security, cloud security, security policies and incident response plans must be continually reviewed.
Click here to download the full report ?

In the Top 5 Cloud Trends for 2020, Principal Analyst Claus Mortensen observed that 2020 is a do-or-die year for Oracle if they wanted to remain as a key contender in the Cloud market. Mortensen said, “Oracle has not been able to break into Cloud in the same way as their competitors and has so far not made the same “leap of faith” into this area as similar companies have. Unless the company makes a clear decision about their Cloud strategy and succeeds in communicating it to the market in 2020, Oracle may quickly find itself more of a niche Cloud player going forward.”
Oracle’s intentions to remain one of the leading global Cloud providers becomes clear as they actively expand their global coverage. Last week Oracle announced that, as part of their ongoing regional expansion plan, they have added local regions in Jeddah (Saudi Arabia), Melbourne (Australia), Osaka (Japan), Montreal (Canada) and Amsterdam (The Netherlands). This expands the reach of Oracle’s Generation 2 Cloud to 21 independent locations, and Oracle intends to further add 15 locations by the end of 2020. At OpenWorld last year, Oracle had announced their plans to have Cloud sites dedicated to the enterprise market as well as government customers.
Dr Alea Fairchild, Principal Advisor Ecosystm, thinks that Oracle appreciates the needs of their enterprise customers. “Oracle understands the sensitivity of the enterprise to the location and availability of their data, which remains an issue with Cloud implementations involving large data sets. They have broken some ground as the first public Cloud vendor with data centres in Saudi Arabia, and are putting efforts in to offer a minimum of two regions in almost every country in which they operate,” says Dr Fairchild. “From a corporate user’s perspective, regional data management and appropriate licensing models are still sensitive spots when it comes to database management.”
Getting Ready for the Hybrid Cloud Market
Oracle also appears to be ramping up for the growing hybrid Cloud market. Ecosystm research shows that more than a third of global organisations have adopted the hybrid Cloud and this will only increase. Given the increased uptake of hybrid and multi-cloud environments, Oracle offers preconfigured links between Oracle and Microsoft Azure cloud regions in the eastern states of the US, London, and Toronto, as part of the Cloud interoperability partnership announced in June 2019. Last year, saw another mutually beneficial partnership between VMWare and Oracle, that supports their customers’ hybrid cloud strategies, allowing the VMware Cloud Foundation to run on Oracle Cloud Infrastructure. Organisations can also avail technical support for Oracle software running in VMware environments both in on-premise data centres and Oracle-certified cloud environments.
“Oracle’s Generation 2 Cloud is now available in 21 locations and is on track to have a total of 36 Cloud regions up and running by the end of the year,” adds Dr Fairchild. “But when compared to AWS, Microsoft and IBM, Oracle still holds a fraction of the market share. They can be seen as a niche infrastructure provider, but indeed the partnerships with Microsoft and VMware are set to help Oracle’s Cloud business make traction with companies that are adopting multi-cloud strategies.”
IBM is aggressively pushing their products and services with multiple partnerships being announced over the last few months.
In the recent announcement, HCL Technologies and IBM stated that they were collaborating to assist organisations on their hybrid cloud journey. The joint services will offer seamless integration of their customers’ cloud across any private, public and on-premise environment. The hybrid cloud approach is aimed at eliminating the concerns of mixing the different cloud environments yet maintaining scalability and security. HCL will feature new refactoring and re-platforming services to allow organisations to migrate, integrate and manage apps and workloads on IBM’s cloud.
Speaking on the subject, Phil Hassey, Principal Advisor ,Ecosystm, thinks that “the most attractive aspect of this collaboration is that it will bring together the best of both vendors. IBM has such a long history in Infrastructure Management, whereas HCL has – most particularly in the past 5 years or so – built up capability in the space.”
The good news for tech buyers is that they will derive benefits from HCL’s customer knowledge and hands-on approach with the combination of IBM technology, cloud and – of course – Watson. HCL has acquired significant IBM assets that they could extract more value from. The infusion of AI into hybrid cloud will lead to increased automation, improved outcomes and effective investments by clients.
When we look at the individual benefits to IBM and HCL from this deal, Hassey says, “IBM needs new customer logos and HCL can provide that. Conversely, IBM can provide larger enterprise clients to HCL. However, it is not a straight customer swap, they will work to maintain relationships independently.”
IBM is pushing hard towards their plans to capture more market with many big deals announced recently – and undoubtedly many more yet to happen. It is well-documented that IBM has gone through many reinventions but is still deeply entrenched in many of the world’s largest organisations. “IBM is such a large machine that different aspects and offerings are always operating at different speeds”, says Phil. “It needs to accelerate the uptake of Watson, and Watson being available on any cloud will help this.”
The hybrid cloud is desperately looking for big scale integration and transformation capabilities, so this agreement between HCL and IBM will hopefully help kickstart that.






