2025 is already shaping up to be a battleground for cybersecurity. With global cybercrime costs projected to reach USD 10.5T, by year’s end, the stakes have never been higher. Cybercriminals are getting smarter, using AI-driven tactics and large-scale exploits to target critical sectors. From government breaches to hospital data leaks and a surge in phishing scams, recent attacks highlight the growing financial and operational toll of cyber threats.
As cyber threats intensify, the demand for stronger defences, top-tier cybersecurity talent, and global collaboration has never been more urgent.
Here’s a look at the recent cyber developments that are shaping 2025.
Click here to download “Cyber Lessons from the Frontlines” as a PDF.
Major Security Breaches: A Costly Wake-Up Call
Cyberattacks are becoming more targeted, disruptive, and costly – impacting governments and organisations worldwide.
In Singapore, mobile wallet fraud is surging, with phishing tactics causing USD 8.9K in losses – 80% linked to Apple Pay. In the UK, security flaws in government IT systems have exposed sensitive data and infrastructure. South Africa’s government-run weather service (SAWS) was also forced offline, disrupting a critical resource for airlines, farmers, and emergency responders. Across the Atlantic, a data breach at a Georgia hospital compromised 120,000 patient records, while BayMark Health Services, the largest addiction treatment provider in the US, alerted patients to a similar breach.
What steps are governments, tech providers, and enterprises taking to protect themselves, critical infrastructure, and individuals?
Protecting Critical Infrastructure: The Digital Backbone
As global connectivity expands, securing critical infrastructure is paramount to sustaining growth, stability, and public trust.
Undersea cables, which carry much of the world’s internet traffic, are a major focus. While tech giants like Amazon, Meta, and Google are expanding these networks to boost global data speed and reliability, the need for protection is just as urgent – prompting the EU to invest nearly a billion dollars in securing them against emerging threats.
Governments and tech providers alike are stepping up. The European Commission has introduced a cybersecurity blueprint to strengthen crisis coordination, rapid response, and information sharing. Meanwhile, Microsoft is investing USD 700M in Poland’s cloud and AI infrastructure, working with the Polish National Defense to enhance cybersecurity through AI-driven strategies.
Quantifying Cyber Risk: Standardised Threat Assessment
As cyber threats grow more sophisticated, so must our ability to detect, measure, and respond to them.
A major shift in cybersecurity is underway – one that prioritises standardised threat assessment and coordinated defense.
The UK is leading the charge with a new cyber monitoring centre that will introduce a “Richter Scale” for cyberattacks, ranking threats much like earthquake magnitudes. Emerging countries are also joining in; Vietnam is strengthening its cyber defences with a new intelligence-sharing platform designed to improve coordination between the government and private sector.
By quantifying cyber risks and enhancing intelligence-sharing, these efforts are shaping global cybersecurity norms, improving response times, and building a more resilient digital ecosystem.
Beyond Defence: Proactive Measures to Combat AI-Driven Cybercrime
Cyber threats evolve faster than defences can keep up – a single click on a malicious email can lead to a breach in just 72 minutes.
With AI making cyberattacks more sophisticated, governments are taking an active role in cyber law enforcement.
Indonesia set up a cyber patrol to monitor and regulate harmful online content while also working to create a safer digital space for children. Thailand, Cambodia, and Laos are cooperating to curb cross-border scams through intelligence sharing and joint enforcement efforts.
Building Trust Online: Digital Identity Solutions
Governments are moving beyond enforcement to strengthen security with digital identity frameworks.
The EU is leading this shift with large-scale pilots for digital identity wallets, designed to offer citizens a secure, seamless way to verify credentials for services, transactions, and age-restricted content. By 2026, each EU member state will issue its own wallet, built on unified technical standards to ensure cross-border interoperability and stronger cybersecurity.
Digital identity wallets mark a major shift in data security, giving citizens greater control over their information while strengthening online trust. By securing identity verification, governments are reducing fraud and identity theft, creating a safer digital landscape.
Closing the Gap: Global Cyber Education Push
Cybersecurity education is no longer just for IT teams – it’s essential at every level, from executives to employees, to build long-term resilience.
Again, governments and tech giants alike are stepping up to bridge the skills gap and enhance cyber awareness.
Singapore is leading by example with a cyber-resilience training program for board directors, ensuring corporate leaders understand cyber risk management. AWS is investing USD 6.35M to support cybersecurity education in the UK, and Microsoft is expanding its global training efforts. The company has partnered with Kazakhstan to strengthen public sector cybersecurity and has committed to training one million South Africans in AI and cybersecurity by 2026.

The Path Forward: A Collective Responsibility
The cybersecurity landscape underscores a crucial truth: resilience can’t be built in isolation. Governments, businesses, and individuals must move past reactive measures and adopt a collective, intelligence-driven approach. As threats grow more sophisticated, so must our commitment to collaboration, vigilance, and proactive defence.
In an increasingly interconnected world, securing the digital landscape is not just necessary – it’s a shared responsibility.

Cybersecurity is essential to every organisation’s resilience, yet it often fails to resonate with business leaders focused on growth, innovation, and customer satisfaction. The challenge lies in connecting cybersecurity with these strategic goals. To bridge this gap, it is important to shift from a purely technical view of cybersecurity to one that aligns directly with business objectives.
Here are 5 impactful strategies to make cybersecurity relevant and valuable at the executive level.
1. Elevate Cybersecurity as a Pillar of Business Continuity
Cybersecurity is not just a defensive strategy; it is a proactive investment in business continuity and success. Leaders who see cybersecurity as foundational to business continuity protect more than just digital assets – they safeguard brand reputation, customer trust, and operational resilience. By framing cybersecurity as essential to keeping the business running smoothly, leaders can shift the focus from reactive problem-solving to proactive resilience planning.
For example, rather than viewing cybersecurity incidents as isolated IT issues, organisations should see them as risks that could disrupt critical business functions, halt operations, and destroy customer loyalty. By integrating cybersecurity into continuity planning, executives can ensure that security aligns with growth and operational stability, reinforcing the organisation’s ability to adapt and thrive in a constantly evolving threat landscape.
2. Translate Cyber Risks into Business-Relevant Insights
To make cybersecurity resonate with business leaders, technical risks need to be expressed in terms that directly impact the organisation’s strategic goals. Executives are more likely to respond to cybersecurity concerns when they understand the financial, reputational, or operational impacts of cyber threats. Reframing cybersecurity risks into clear, business-oriented language that highlights potential disruptions, regulatory implications, and costs helps leadership see cybersecurity as part of broader risk management.
For instance, rather than discussing a “data breach vulnerability”, frame it as a “threat to customer trust and a potential multi-million-dollar regulatory liability”. This approach contextualises cyber risks in terms of real-world consequences, helping leadership to recognise that cybersecurity investments are risk mitigations that protect revenue, brand equity, and shareholder value.
3. Build Cybersecurity into the DNA of Innovation and Product Development
Cybersecurity must be a foundational element in the innovation process, not an afterthought. When security is integrated from the early stages of product development – known as “shifting left” – organisations can reduce vulnerabilities, build customer trust, and avoid costly fixes post-launch. This approach helps businesses to innovate with confidence, knowing that new products and services meet both customer expectations and regulatory requirements.
By embedding security in every phase of the development lifecycle, leaders demonstrate that cybersecurity is essential to sustainable innovation. This shift also empowers product teams to create solutions that are both user-friendly and secure, balancing customer experience with risk management. When security is seen as an enabler rather than an obstacle to innovation, it becomes a powerful differentiator that supports growth.
4. Foster a Culture of Shared Responsibility and Continuous Learning
The most robust cybersecurity strategies extend beyond the IT department, involving everyone in the organisation. Creating a culture where cybersecurity is everyone’s responsibility ensures that each employee – from the front lines to the boardroom – understands their role in protecting the organisation. This culture is built through continuous education, regular simulations, and immersive training that makes cybersecurity practical and engaging.
Awareness initiatives, such as cyber escape rooms and live demonstrations of common attacks, can be powerful tools to engage employees. Instead of passive training, these methods make cybersecurity tangible, showing employees how their actions impact the organisation’s security posture. By treating cybersecurity as an organisation-wide effort, leaders build a proactive culture that treats security not as an obligation but as an integral part of the business mission.
5. Leverage Industry Partnerships and Regulatory Compliance for a Competitive Edge
As regulations around cybersecurity tighten, especially for critical sectors like finance and infrastructure, compliance is becoming a competitive advantage. By proactively meeting and exceeding regulatory standards, organisations can position themselves as trusted, compliant partners for clients and customers. Additionally, building partnerships across the public and private sectors offers access to shared knowledge, best practices, and support systems that strengthen organisational security.
Leaders who engage with regulatory requirements and industry partnerships not only stay ahead of compliance but also benefit from a network of resources that can enhance their cybersecurity strategies. Proactive compliance, combined with strategic partnerships, strengthens organisational resilience and builds market trust. In doing so, cybersecurity becomes more than a safeguard; it’s an asset that supports brand credibility, customer loyalty, and competitive differentiation.
Conclusion
For cybersecurity to be truly effective, it must be woven into the fabric of an organisation’s mission and strategy. By reframing cybersecurity as a foundational aspect of business continuity, expressing cyber risks in business language, embedding security in innovation, building a culture of shared responsibility, and leveraging compliance as an advantage, leaders can transform cybersecurity from a technical concern to a strategic asset. In an age where digital threats are increasingly complex, aligning cybersecurity with business priorities is essential for sustainable growth, customer trust, and long-term resilience.

In my last Ecosystm Insight, I spoke about the 5 strategies that leading CX leaders follow to stay ahead of the curve. Data is at the core of these CX strategies. But a customer data breach can have an enormous financial and reputational impact on a brand.
Here are 12 essential steps to effective governance that will help you unlock the power of customer data.
- Understand data protection laws and regulations
- Create a data governance framework
- Establish data privacy and security policies
- Implement data minimisation
- Ensure data accuracy
- Obtain explicit consent
- Mask, anonymise and pseudonymise data
- Implement strong access controls
- Train employees
- Conduct risk assessments and audits
- Develop a data breach response plan
- Monitor and review
Read on to find out more.
Download ‘A 12-Step Plan for Governance of Customer Data’ as a PDF

What is happening to the data that you are sharing with your ecosystem of suppliers?
Just before Christmas, a friend recommended reading “Privacy is Power” by Carissa Véliz. But the long list of recommendations that the author provides on what you could and should do is quite disheartening. I feel that I have to shut off a lot of the benefits that I get from using the Internet in order to maintain my privacy.
But then over the past couple of days came a couple of reminders of our exposure – our suppliers will share our data with their suppliers, as well as be prepared to use our resources to their benefit. I am reasonably technical and still find it difficult, so how does a person who just wants to use a digital service cope?
Bunnings’ Data Breach with FlexBooker
First example. Bunnings started using a service called FlexBooker to support their click-and-collect service.
To do this, they share personal information with the company for the service to work correctly. But hackers have stolen data for over three million customers from FlexBooker in a recent data breach.
How many of Bunnings’ customers were aware that their data was being shared with FlexBooker? How many would have cared if they had known?
I have only read the comments from Bunnings included in the Stuff report but I believe the reported reaction lacks the level of concern that this breach warrants. What did Bunnings do to verify FlexBooker’s privacy and security standards before sharing their customers’ data with them? What is going to change now that the vulnerability has been identified?
Neither of these things is clear. It is not clear if Bunnings have advised their customers that they could have been affected. There is no clear message on the Bunnings New Zealand site on the details of the breach.
In “Privacy is Power”, the author makes a strong case for customers to demand protection of their privacy. Organisations that use other companies as part of their services must be as demanding of their suppliers as their own customers would be of them.
Is Crypto Mining part of antivirus?
The second example is a little different. Norton has released crypto mining software as part of their antivirus suite. This crypto mining software uses the spare capacity of your computer to join with a pool of computers that are working to create a new blockchain block. Each time a new block is added, you would earn some cryptocurrency that you could change to a fiat currency, i.e. normal cash.
But I question why a crypto miner is part of an antivirus suite. Norton makes the case that they are a trusted partner, so can deliver a safer mining experience than other options.
Norton have made the use of this software optional, but to me, it does indicate the avarice of companies where they see a potential income opportunity. If they had included the software in their internet security suite, then there may be some logic in adding the capability. But to antivirus?
The Verge did some unscientific measurements on the value to a user of running this software. They found the cost of the electricity used during the operation of Norton’s mining software was about the same as what they earned. So Norton, with their 15% fee, would be the only ones making money.
The challenge remains for most of us. Our software vendors are adding new functionality to our services regularly because it is what we as customers expect. But I rarely check to see what has been changed in a new release as normally you will only see a “bugs squashed, performance improved” messaging. We have no guarantee that they have not implemented some new way of using our information or assets without gaining explicit approval from the user for this new use.
To Norton’s credit, they have made crypto mining optional and do not activate the software without their users’ consent. Others are less likely to be as ethical.
Summary
Both of these examples show how vulnerable customers of companies are to the exposure of their private data and assets. All organisations are increasing their use of different external services as SaaS options become more attractive. Commercial terms are the critical points of negotiation, not customer privacy. What assurance do customers get that their privacy is being maintained as they would expect?
One point that is often overlooked is that many cloud service contracts define the legal jurisdiction as being either the cloud provider’s home jurisdiction or one that is more advantageous for them. So, any intended legal action could be taking place in a foreign jurisdiction with different privacy laws.
Customer service organisations (i.e. pretty much all organisations) need to look after their customers’ data much more effectively. Customers need to demand to know how their rights are being protected, and governments have to put in place appropriate consequences for organisations where breaches occur outside that government’s jurisdiction.

Ecosystm recently partnered with Asavie to conduct a study into the opportunity and outlook for the “Branch of One”. One of the challenges was actually defining what the Branch of One is. Here’s what we came up with:
Branch of One enables Office Anywhere by delivering secure, frictionless access to all business resources, with full mobility – meeting the security and manageability requirements of CIOs and CISOs.
Basically it is all the data and systems you need to get your job done, in your pocket. Secure. Easy to manage.
What I really like about the idea is that it describes what business is trying to achieve and it gives a common language and outcome for IT and business leaders. Consider all the things that IT and security teams need to do to enable access to applications and data in remote branches – from connectivity to security to data and system access. Often it takes days, weeks or months to open a new office or branch, or to provision a new retail store. Now, imagine having the ability to roll out all of these systems and services in seconds. To a single user or to thousands. Without consideration for location. Business leaders will understand this benefits and will support it.
It also has the opportunity to help nearly every business today. Of the 1005 businesses we interviewed across the globe in our Global CxO Study 2020, 44% admitted to suffering cyber-attack incidents during COVID-19 due to employees working from home – and over half of these attacks were on mobile devices. Compromised devices were the number one target for cyber-attacks in 2020.
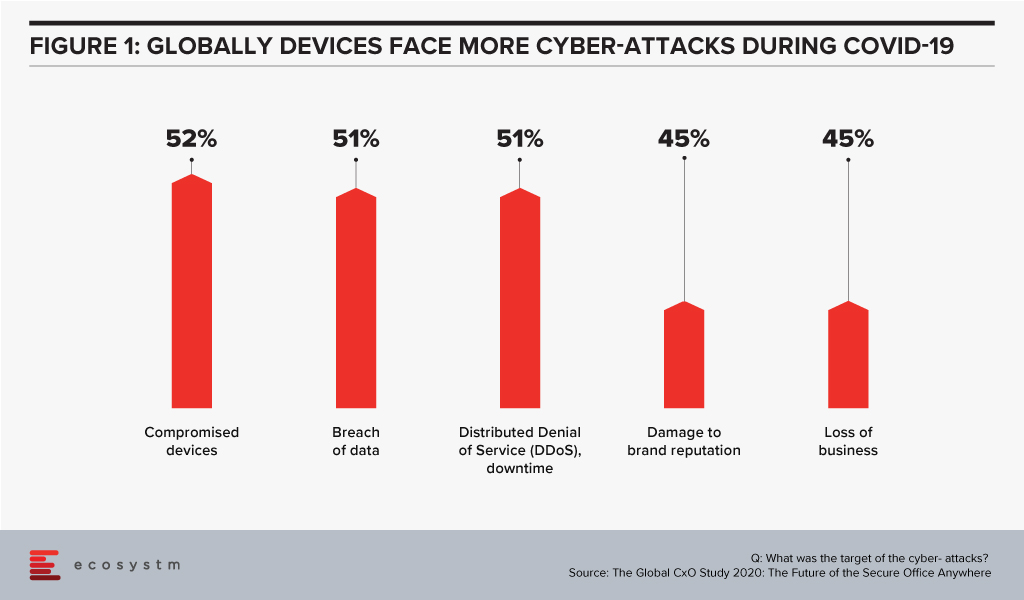
Businesses need a new way to manage the devices and applications of their remote employees. They need to be able to extend the benefits of the WAN to them without the downsides of VPNs. Every business we interviewed saw benefits of bringing devices, locations and offices inside the WAN. Turning every device and office into a Branch of One.
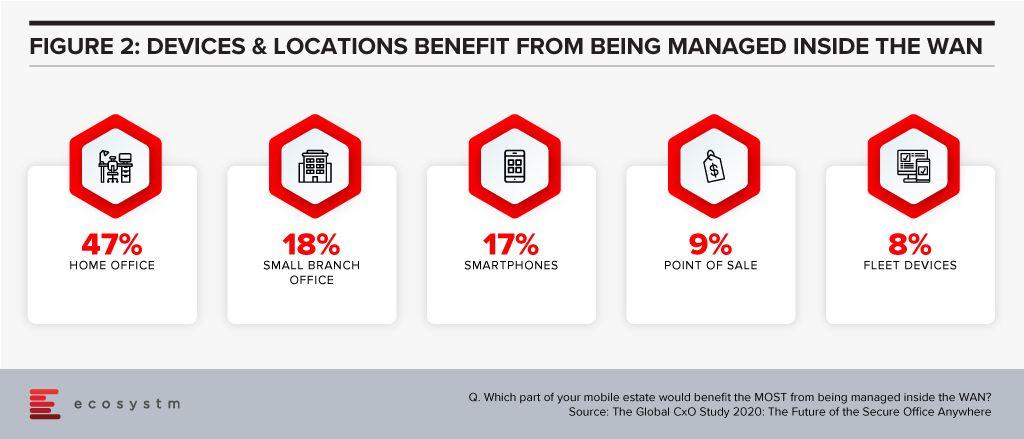
A few security and network technologies have promised this capability – SDNs can offer a similar service, but they require client software to be installed. 78% of businesses we interviewed are using VPNs to bring devices inside the WAN – but again, they require client software, and can be inconsistent (and insecure!) on mobile devices.
Companies that embrace the Branch of One can provision new users in a few clicks. No software to install, no cables to connect, no hardware to provision – it makes life easier for technology and security professionals. The Branch of One gives your employees the systems and data they need to get their job done – delivered securely across the mobile network.
Download the report based on ‘The Global CxO Study 2020: The Future of the Secure Office Anywhere’, conducted by Ecosystm on behalf of Asavie. The report presents the key findings of the study and analyses the market perceptions of Office Anywhere and the need for a ‘Branch of One’, which will be the foundation of enterprise mobile security in the future.

The Hamburg State Commissioner for Data Protection and Freedom of Information (HmbBfDI) imposed a fine of USD 41.3 million on Swedish MNC, Hennes & Mauritz (H&M) for illegal surveillance of employees in H&M Germany’s service centre at Nuremberg.
The data privacy violations reportedly began in 2014 when the company started collecting employee data including their personal information, holidays, medical records, informal chats and other private details. It was found that the information was unlawfully recorded and stored; and was further opened to managers. The violations were discovered in October 2019 when due to a computing error the data became accessible company-wide for a short span.
Ecosystm Principal Analyst Claus Mortensen says. “This is one of those cases that are so blatant that you cannot really say it is setting a precedent for future cases. All the factors that would constitute a breach of the GDPR are here: it involves several types of data that shouldn’t be collected; poorly managed storage and access control; and to finish it all off, a data leak. So even though the fine is relatively high, H&M should probably be happy that it was not bigger – the GDPR authorises fines of up to 4% of a company’s global annual turnover.”
Mortensen adds, “It should also be said that H&M has handled the aftermath well by accepting full blame and by offering compensation to all affected employees. It is possible that these intentions were considered by the HmbBfDI and prevented an even higher fine.”
The penalty on the Swedish retailer is the highest in Germany linked to the General Data Protection Regulation (GDPR) legislation since it came into effect in 2018 and the second highest throughout the continent. Last year, France’s data protection watchdog fined Google USD 58.7 million for not appropriately disclosing data collection practices to users across its services to personalise advertising.
Talking about the growing significance of fines for data breaches, Ecosystm Principal Advisor Andrew Milroy says, “To be effective, GDPR needs to be enforced consistently across the board and have a significant impact. It is too easy to ‘corner cut’ data protection activities. Some breaches may not have an operational impact. For this reason, the cost of being caught needs to be sufficiently large so that it makes commercial sense to comply.”
According to Milroy, “The sizeable fine meted out to H&M together with the publicity it has generated shows that the regulators are serious about GDPR and enforcing it. Other regulators around the world need to make sure that their jurisdictions don’t become ‘soft touches’ for malicious actors.”
EU Proposing New Data Sharing Rules
We are also seeing the European Union (EU) make moves to regulate digital services and customer data use by technology providers, as part of the European Union Digital Strategy. The EU is drafting new rules under the Digital Services Act to force larger technology providers to share their customer data across the industry, to create an even playing field for smaller providers and SMEs. The aim is to make the data available to all for both commercial use and innovation. This is being driven by the EU’s antitrust arm, aimed to reduce the competitive edge tech giants have over their competition and they may be banned from preferential treatment of their own services on their sites or platforms. The law, which is expected to be formalised later this year, is also expected to prohibit technology providers from pre-installing applications or exclusive services on smartphones, laptops or devices. The measures will support users to move between platforms without losing access to their data.

One of the questions that organisations are asked in the global Ecosystm Cybersecurity Study, is how they rate their cybersecurity measures and controls (on a scale of 1-10, where 10 is extremely mature). Organisations that rate themselves at an 8-10, are considered ‘mature’ in their cybersecurity measures while those that rate themselves at 1-7 are evolving their cybersecurity practices. Clear differences in priorities and investments can be seen between the mature and evolving adopters of cybersecurity measures.
Here are the key differences that emerge and should allow organisations to benchmark their cybersecurity practices against those of the mature adopters of cybersecurity solutions.
#1 Do you have the Right Motives?
There is no denying that organisations have to continue to evolve their cybersecurity measures with the evolving threat landscape. There is a need to have a continued focus on cybersecurity. However, are they doing it to address the right issues and threats? Mature organisations have their cybersecurity measures entrenched within the organisation’s risk management programs which help them align their investments to their risk position (Figure 1). Very often these programs have their technology landscape – special projects for digital transformation (DX) – and industry compliance laws built into them. Mature organisations also have a proactive approach to incidents and breaches, continuing to evolve their cybersecurity practices.
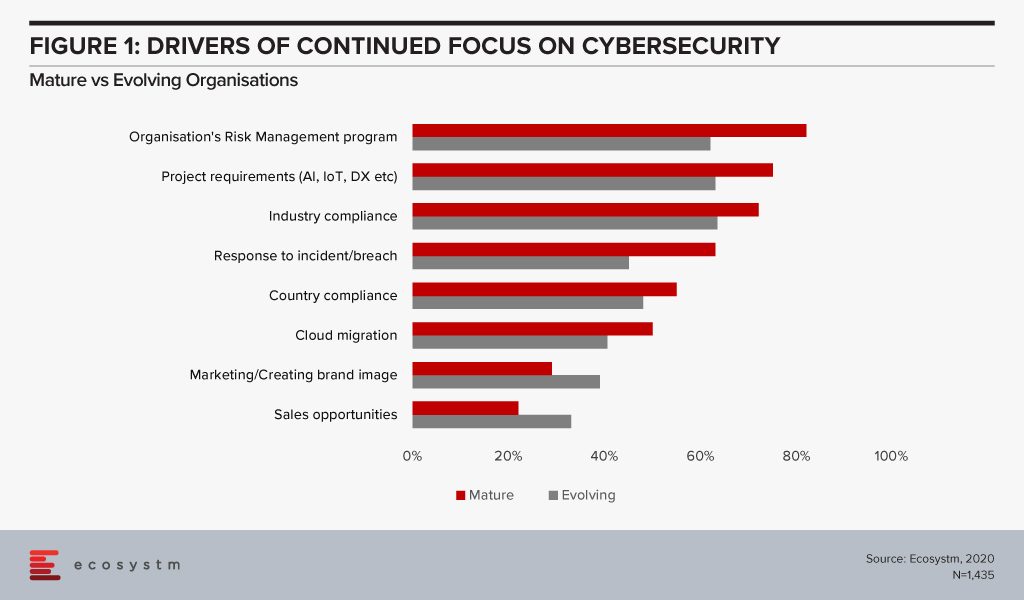
While cybersecurity practices can help with an organisation’s go-to-market messaging, the reasons for investing in robust cybersecurity practices should be more aligned to the organisation’s risk strategies. Also, it should not be restricted to compliance alone and should be much more proactive than merely ticking the right boxes.
#2 Are you focusing on the Right Challenges?
As solution complexity increases, organisations are challenged by their cybersecurity deployments (Figure 2). Cybersecurity measures must be applied across the entire organisation and systems, including applications, database, and storage whether on-prem or on cloud (public, private or hybrid). This adds to the complexity of the solutions and the associated integration challenges.
While it is not possible to have an unlimited budget for cybersecurity measures, once it is treated like a business issue, and the risks associated (including financial and reputational) are conveyed to the key stakeholders cybersecurity budgets become part of the organisational strategy consideration. If your security team is still struggling to procure what they think is the right budget, there is a mismatch in expectations and miscommunication between the security team and executive management. “A risk focussed approach enables organisations to understand the ROI on security measures and therefore invest in the most impactful areas of cyber risk for their business”, says Alex Woerndle, Principal Advisor Ecosystm.
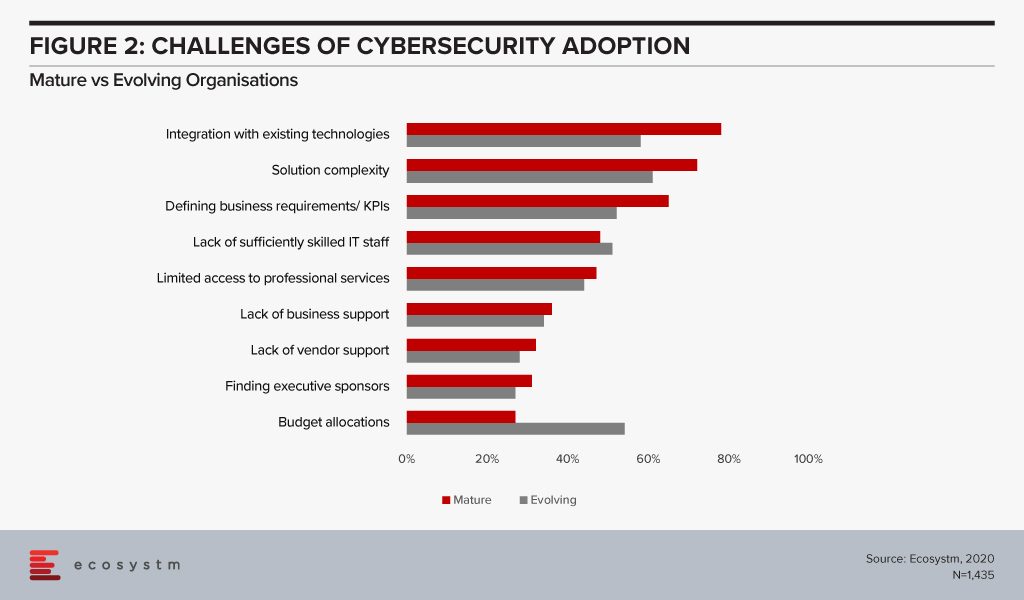
A real challenge that all organisations face is skills shortage. However, it is time to align business and security strategies and look beyond IT for security analysts – professionals who can translate what the Board’s priorities are into defining the security strategy.
#3 Do you have a dedicated Cybersecurity Role?
While the Board will often be involved in evaluating the risk exposure of an organisation, there is need for a dedicated role that can traverse both the business and the technological needs in deciding the right cybersecurity framework.
Organisations should have a dedicated responsibility for their cybersecurity practice – the CISO/CSO is the key data protection lead in mature organisations (Figure 3). CISOs should be reporting into the CFO, Chief Risk Officer or the CEO and not the CIO to avoid a conflict of interest. Alex says, “While the most common reporting line for CISOs is still to the CIO, there is a fundamental conflict of interest with this model – being part of the risk function, or reporting directly to the CEO, provides the level of independence required for good governance of cyber risk.”
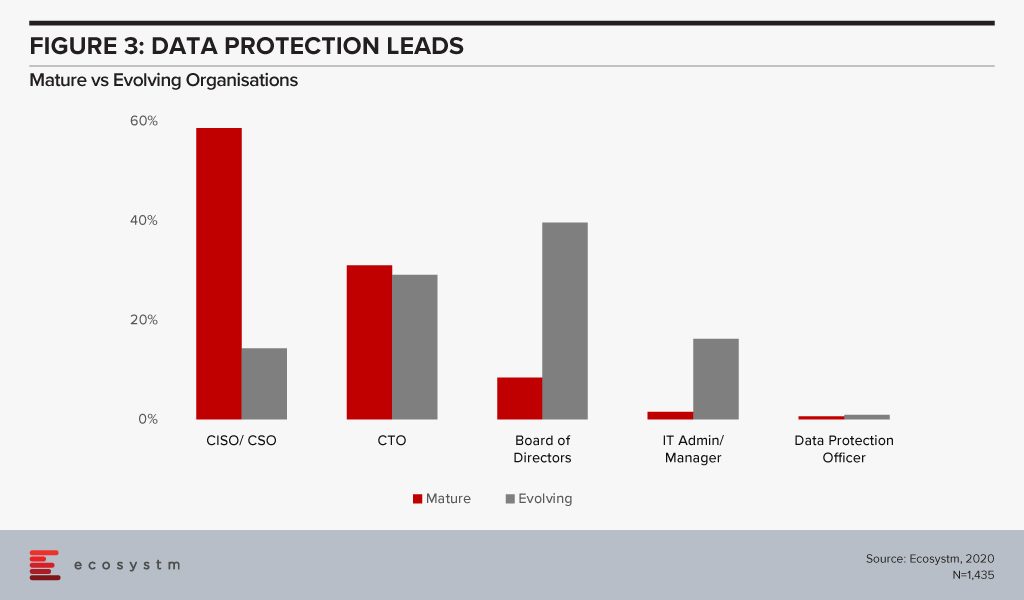
The reality is that many organisations – especially small and medium enterprises that have small dedicated security teams – will find it difficult to appoint a dedicated CSO/CISO. The study also finds that 80% of evolving organisations have less than 10 employees in their security teams as compared to only a third of mature organisations. Carl Woerndle, Principal Advisor Ecosystm, suggests these organisations look at the option of hiring a vCISO (virtual CISO). “A vCISO can help your organisation deliver a full security program within a fixed budget. Hiring someone external also has the added benefits of bringing objectivity to your security strategies and providing guidance on newer skills and technologies to your security teams.”
#4 Are you aware of Cloud Risk?
Cloud adoption has become mainstream, especially as organisations ramp up their digitalisation initiatives. It adds scale and agility to the organisation’s transformation investments. While security remains a key concern when it comes to cloud adoption, cloud is often regarded as a more secure option than on-premise. Cloud providers have dedicated security focus, constantly upgrade their security capabilities in response to newer threats and evolve their partner ecosystem. There is also better traceability with cloud as every virtual activity can be tracked, monitored, and is loggable.
However, mature organisations not only use on-prem options more for their sensitive data storage (Figure 4), they are also more skeptical about relying only on public cloud security features. Only 34% of mature organisations feel that public cloud security features do not need to be complemented while 52% of evolving organisations share that perception.
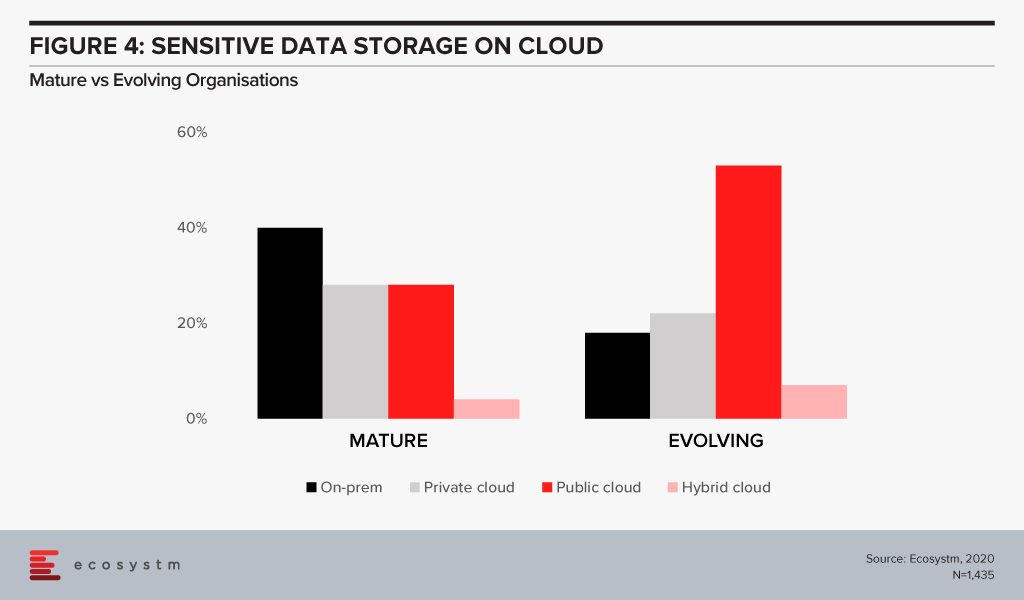
The cloud is as secure as an organisation makes it. The perception that there is no need to supplement public cloud security features can have disastrous outcomes. It is important to supplement the cloud provider’s security with event-driven security measures within an organisation’s applications and cloud interface. Alex says, “Assuming the big cloud providers have security covered for you is a huge mistake. Understanding the shared responsibility model is crucial in your public cloud adoption journey. The tools are available – but typically at an extra cost, and you need to employ, configure and continually manage them for effective security.”
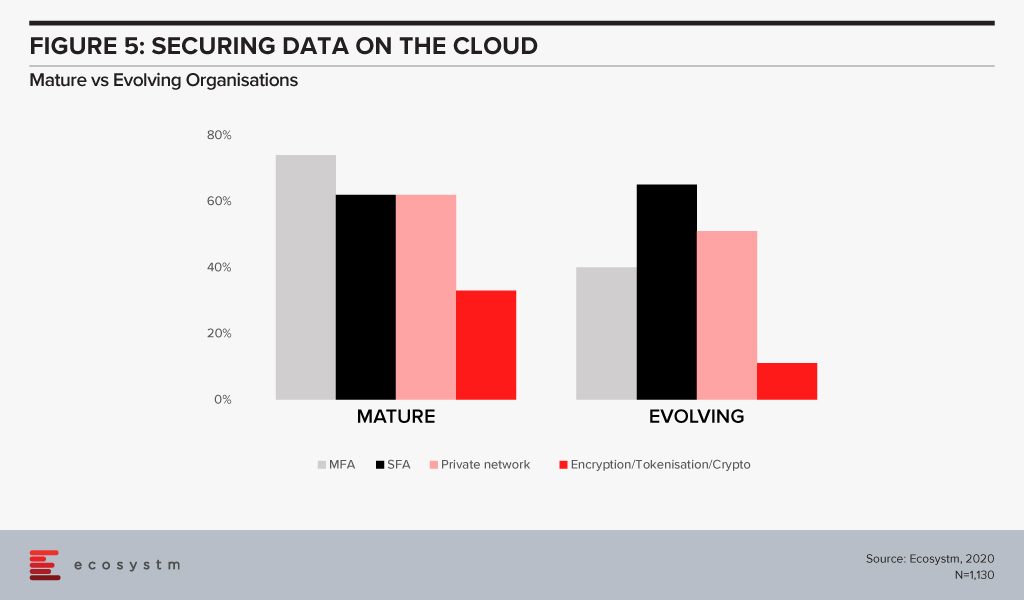
The big differentiator between mature and evolving organisations in securing cloud environments is in the use of multi-factor authentication (Figure 5). With 3/4th of mature organisations employing this as a control, it highlights that passwords – even strong passwords – alone, are not sufficient in 2020. Mature organisations are increasingly investing in encryption. But the perception of the complexity in deploying and managing encryption (and the keys) has been a challenge especially for organisations with smaller teams and less in-house technical capabilities.
#5 Are you Breach Ready?
Global organisations generally consider a data breach as inevitable – largely believing that “it is not about if, but when”(Figure 6). All organisations will face some incident, attempted breach or a breach, at some point. It is necessary to have the right cybersecurity measures to avoid breaches – but it is equally important to be prepared for when a breach actually happens. A majority of organisations, regardless of maturity, are worried about (and expect) a breach. For evolving organisations this is a troubling statistic given their use of public cloud with limited security understanding or controls – better education is needed from the public cloud providers but also the security industry.
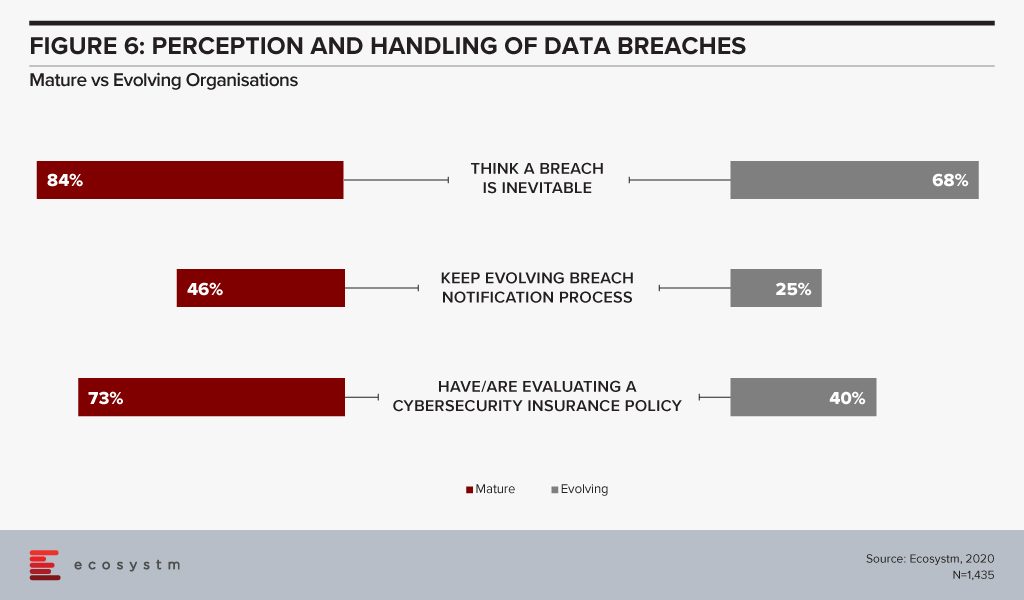
Breach notification processes need to keep evolving – and they must also include employees. Organisations should be aware of the need for people management during an incident. Policies might be clear and adhered to, but it is substantially harder to train the stakeholders involved, on how they will handle the breach emotionally. It extends to how an organisation manages their welfare both during an incident, and long after the incident response has been closed off.
“Cyber insurance has rapidly become a must-have as part of an organisation’s layered defence. While it provides a layer of support in the event of a breach, you should not rely on it as your only safety net,” Carl adds. “It is also important to ensure that your cyber cover is appropriate to your risks and organisational needs and policies should be evaluated carefully.”

As a health analyst, I have always considered myself lucky that Singapore has been home for the last 9 years, and I have been a witness to the national ehealth initiatives from close quarters. So, when I received the SMS informing me that my son’s name, NRIC (identification number), address, gender, race and birth date are floating around in the cyberspace somewhere it was disconcerting to say the least. True that his medical and financial information had not been breached, but that’s small consolation for someone who took for granted the sophistication of the health records system in Singapore.
A Quick Recap
SingHealth, Singapore’s largest group of healthcare institutions, announced in June 2018 that non-clinical personal data of 1.5 million patients had been “accessed and copied”. Outpatient prescriptions information of 160,000 patients were also compromised. There was no evidence of this breach going deeper into actual patients’ clinical records and the other 2 healthcare groups were not affected. The breach was detected a week later, a relatively short period, but it was not immediate. Security – identification and threat management – is one of the mainstays of any Digital Transformation journey, and Singapore healthcare is considered to be well along on that journey.
It is commonly believed that security breaches are waiting to happen, and that organisations are not concerned with ‘if’ but ‘when’. Moreover, the disparity of the devices used in healthcare makes security a difficult proposition. This will only become more complicated once IoT sensors and devices are used from outside the walls of hospitals. AI-driven breach detection is being portrayed as the hope for the near future.
Why does this continue to concern me, even after 5 months?
- A cautious approach to NEHR. One of the first statements that the government made in the wake of this disaster was that the government is reviewing the ongoing NEHR initiatives. Since then, the Cyber Security Agency (CSA), and PwC have been appointed to identify the weaknesses in the NEHR initiatives, with a view to address them. It is a good time to re-evaluate the possible weak links before going deeper into the program.
But, almost 10 years after the NEHR was launched the country has still not been able to realise the full potential of the initiative, especially because of limited participation from the private sector. Will this lead to a conservative approach to creating the ‘One Patient, One Record’? Will this put on the brakes to ongoing progress of the ehealth initiatives? - Private Participation in NEHR. The private sector accounts for 80% of Singapore’s primary care. It is possible for a citizen who has never stepped into a public polyclinic, choosing the friendly, neighbourhood GP instead, and has had no acute care needs (whether inpatient or outpatient) to not be on the NEHR system. And this would include chronic disease management, which is the primary cause of concern in sustainable healthcare. The Singapore Personal Data Protection Act 2012 (PDPA) law governs the collection, use and disclosure of personal data by all private organisations. The Act, that came into effect in 2014, states that organisations that fail to comply with PDPA may be fined up to $1 million and public reporting of the breach. However, the public sector is not included under the PDPA! So in effect the public healthcare consumers whose data was breached have no recourse under PDPA. But this might deter private healthcare providers with very rudimentary IT systems in place, who are liable under PDPA. The government has already been fighting a reluctance on the part of these private primary care providers to go digital with the patient records, and sharing them with the public system, with a view to build a more comprehensive NEHR.
- ‘Smart nations’ need ‘Smart’ citizens. This has been my mantra regarding Singapore’s Smart Nation initiatives for a while now. And smart citizens are not necessarily only those with access to multiple mobile devices and wireless connectivity. Smart citizens are also people who are aware of the pitfalls in the journey, and of their rights as they travel together with the government on the ride.
What shocked me was the singular lack of concern among the average Singaporean, when I tried to discuss the gravity of the health data breach – which is considered even more dangerous than financial data breaches in most mature countries. The common response I received was that its only personal data. Well, your national identification number, along with your date of birth, in the hands of nefarious agents can do a lot of mischief, I reminded them. And what about the prescription data, I persisted. That got answered by a view that prescription data is not really health data! A lot can be inferred from your prescription data… I persisted with no avail! Healthcare is moving toward giving autonomy and control of health records to individuals. To be able to leverage this control, individuals have to be a) concerned about their health and wellness parameters b) ready to record and share their health data with the right people at the right time, and c) aware that health data is private and needs to be kept secure.
There is no doubt in my mind that Singapore will do all within its capacity to avoid a breach of this level – and other industries are feeling the repercussions too. But the government definitely has to manage the private participation in NEHR more delicately and diligently, in light of this breach. They also have a long way to go in educating the citizens on the privacy and compliance angles to health data.




























