We continue to receive responses from the tech buyer community on the impact of COVID-19 on Digital Transformation initiatives, and the early business and technology measures that were implemented to combat the crisis. As the months go by, it is becoming apparent that organisations have implemented the early measures and are now looking ahead to their journey to recovery.
IT Teams realised that even if they had the right technology solutions, they were unprepared for the scale or capacity to extend these technology offerings to handle the sudden and enormous changes required to manage the crisis. Their cloud business applications, cybersecurity and collaboration solutions were simply not sufficient to meet the needs of the remote workforce. As organisations become more conscious of business continuity planning (BCP) for future eventualities, they will boost their technology capabilities, over the next 12 months.
Another area the study aims to explore is how optimistic is the business outlook, when it comes to expecting a return to normalcy. Only 3% of organisations are expecting a New Normal that is very different from where things were at the beginning of the year. About a third of organisations are expecting a return to normalcy by the end of the year, while the majority expect to recover by the middle of 2021. Also, some industries are more optimistic of a recovery than others. As an example, 35% of healthcare organisations expect a return to normalcy by the end of the year. This is a positive indicator, given that the industry has been in the forefront of the crisis, for nearly 6 months now.
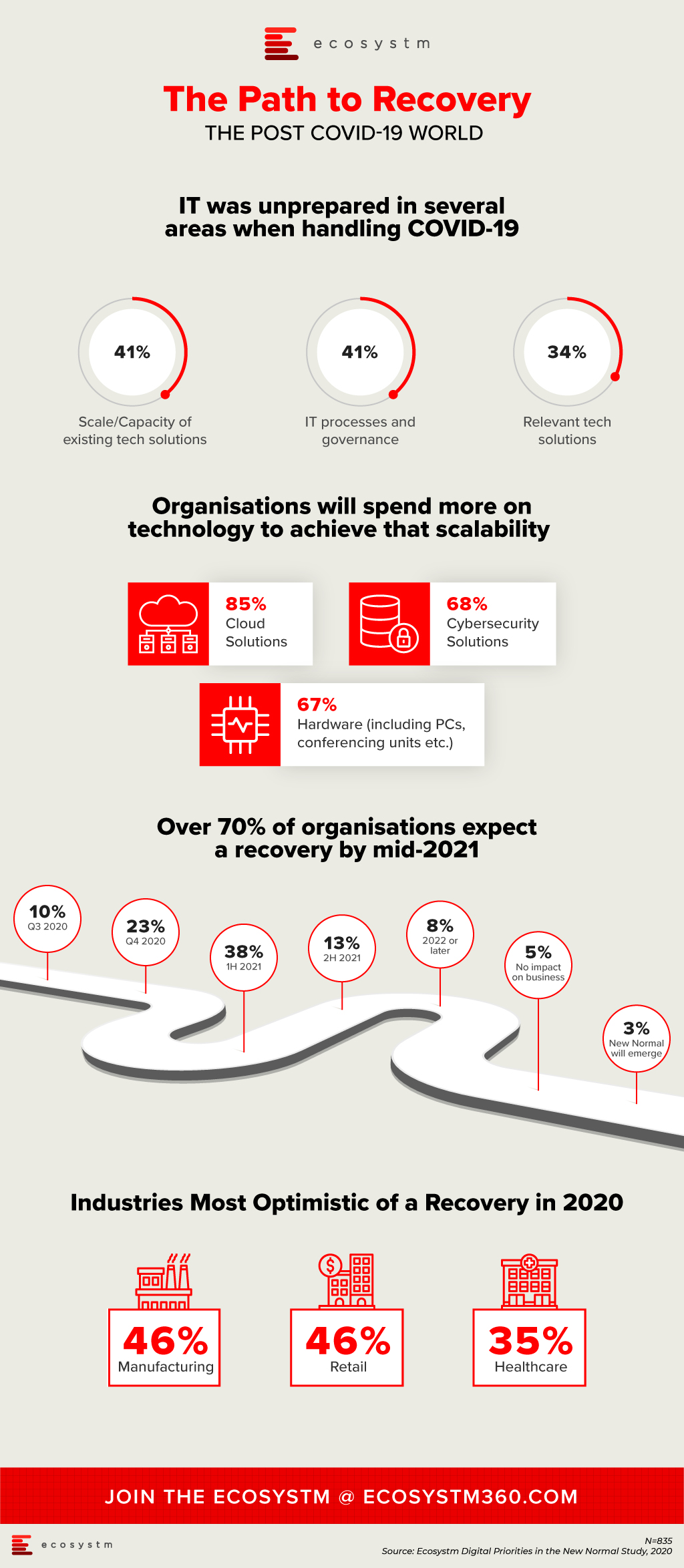
More insights on the impact of the COVID-19 pandemic and technology areas that will see continued investments, as organisations get into the recovery phase, can be found in the Digital Priorities in the New Normal Study.
As organisations stride towards digitalisation, re-evaluate their business continuity plans and define what the Future of Work will look for them, Cloud adoption is expected to surge. In June, there were several announcements that indicate the market is responding to this increased interest.
Cloud Providers Gearing up to Enable Economic Recovery
Global economies are slowly gearing up for a technology-led recovery phase and several organisations are taking advantage of the disruption to start or accelerate their digital transformation plans. Many are looking at this as a good opportunity to replace their legacy systems. Cloud providers are expected to lead from the front when it comes to helping the economy recover.
Government agencies have been immensely impacted by the COVID-19 crisis and will need to shift fast into the recovery mode. Salesforce launched a multi-tenant dedicated Cloud infrastructure for their US Federal, state and local government customers, government contractors, and federally funded research and development centres. Hosted on AWS GovCloud and FedRAMP compliant, it provides customers with a compliant and secure environment to deploy Salesforce’s CRM platform and industry solutions. The launch is expected to empower government agencies with the ability to deliver better services, scale to unprecedented demands and connect to citizens on their channel of choice.
Initiatives such as the UK Crown Commercial Service (CCS) and Google Cloud agreement will also help in the recovery phase. This allows qualified public sector agencies to avail of a discounted price for their Google Cloud deployments. Earlier in the year CCS entered into a price arrangement with Microsoft as well. If Cloud has to be the vehicle for economic recovery, such arrangements will benefit cash-strapped public sector organisations.
The recovery will also require the entire technology ecosystem to engage not only with large enterprises but also small and medium enterprises (SMEs). Alibaba Cloud announced an investment of US$ 283 million to revamp its global partner program. They plan to introduce new partner-customer communication processes to enhance response time and bring more opportunities to independent software vendors (ISVs) managed service providers (MSPs) and system integrators (SIs) as partners.
Europe Emerging as a Cloud Hub
As a fallout of the current political scenario, Europe is pushing for more cloud independence and to become an innovation hub as a vendor-neutral network for cloud computing providers and their customers.
GAIA-X Foundation is a federated data infrastructure project initiated to build a unified system of cloud and data services to be protected by EU Laws – including GDPR, the free flow of non-personal data regulation and the Cybersecurity Act. France and Germany kicked off the GAIA-X cloud project last year and the system is open for participation to national and European initiatives for exchange of data across industries and services such as AI, IoT and data analytics. GAIA-X took another step towards becoming a real option for European organisations with the establishment as a legal entity in June. Various organisations – including Dassault, Orange, Siemens, SAP, Atos, Scaleway and Deutsche Telekom are a part of this non-profit platform, working together on Cloud applications, high-performance computing as well as edge systems. The project is expecting to release a working model by early 2021 and will be further enhanced in phases.
Global Cloud leaders are also focusing on expanding their presence in Europe. In February, Microsoft announced a new data centre in Spain leveraging Telefónica infrastructure. In a similar move, Google Cloud announced its plans to expand in the region in partnership with Telefónica. Telefonica and Google are expected to jointly work on Spain’s digitalisation through edge infrastructure and 5G for consumers and telecom infrastructure.
Cloud Providers Bolstering their Cybersecurity Capabilities
2020 has witnessed a host of cybersecurity threats and data breaches. While Cloud providers have always evolved their cybersecurity capabilities, it has become important for them to become vocal about these measures to build trust in the industry.
To complement the Microsoft Azure IoT security, Microsoft acquired IoT security specialist CyberX, last month. The acquisition will enable greater security for the IoT devices connected to the Microsoft network and will help their customers to gain visibility through a map of devices thus allowing them to gather information on security risks associated with thousands of sensors and connected devices. This will enhance smart grid, smart manufacturing and digital assets and profiles and reduce vulnerabilities across production and supply chain.
In another move which will benefit the ISV and SI ecosystem, NetFoundry’s zero trust networking API is now available on RapidAPI. RapidAPI’s marketplace enables developers to easily find, connect to, and manage the APIs they need to build a range of applications. Now the ISV and developer community can access NetFoundry’s software-only, zero trust models on RapidAPI.
More Partnerships between Software/Industry Solutions Providers and Cloud Providers
The COVID-19 crisis has had a far-reaching impact on several industries. The technologies that are expected to see the most uptake are IoT and Future of Work technologies.
Ecosystm Principal Advisor, Kaushik Ghatak says, “COVID-19 has brought to the fore the need for managing risks better. And the key to managing risks is to have better visibility and drive data-driven decisions; the sweet spot for IoT technologies.”
Last week, Microsoft and Hitachi announced a strategic alliance to accelerate the digital transformation of the Manufacturing and Logistics industries across Southeast Asia, Japan and North America. The first solutions are expected to be made available in Thailand as early as this month. Hitachi brings to the table their industry solutions, such as Lumada, and their IoT-ready industrial controllers HX Series. These solutions will be fully integrated with the Microsoft cloud platform, leveraging Azure, Dynamics 365 and Microsoft 365.
Another sector that has seen significant disruption is Real Estate. Ecosystm Principal Advisor, Andrew Milroy in his blog Proptech: Driving Digital Transformation in the Wake of COVID-19 sees a real opportunity for the sector to transform. “Many activities within the property ecosystem have remained unchanged for decades. There are several opportunities for digital engagement and automation in this sector, ranging from the use of robots in construction to the ‘uberisation’ of the residential property customer journey.”
June saw Honeywell and SAP partner to create a joint cloud-based solution based on Honeywell Forge and SAP cloud. The cloud solution is aimed at real estate operators and customers providing aggregated financial and operational insights in real-time. The solution leverages the Honeywell Forge autonomous buildings solution and the SAP Cloud for Real Estate solution, enabling facility managers and building owners to reposition their real estate portfolios through parameters such as cost savings and energy efficiency and help improve the tenant experience.
As organisations struggle to maintain operations during the ongoing crisis, there has been an exponential increase in employees working from home and relying on the Future of Work technologies. Ecosystm principal Advisor, Audrey William says, “During the COVID-19 pandemic, people have become reliant on voice, video and collaboration tools and even when things go back to normal in the coming months, the blended way of work will be the norm. There has been a surge of video and collaboration technologies. The need to have good communication and collaboration tools whether at home or in the office has become a basic expectation especially when working from home. It has become non-negotiable.”
AWS and Slack announced a multi-year partnership to collaborate on solutions to enable the Workplace of the Future. This will give Slack users the ability to manage their AWS resources within Slack, as well as replace Slack’s voice and video call features with AWS’s Amazon Chime. And AWS will be using Slack for their internal communication and collaboration.
Delivering excellent customer experience in the midst of the crisis has proved to be difficult for organisations. Customer care centres have been especially impacted by high volumes of customer interactions – through voice and non-voice channels. This will see a major rise in adoption of cloud contact centre solutions. Contact centre providers are ramping up their capabilities in anticipation. Genesys selected AWS as their preferred cloud partner to deliver new features to customers and build a global and secure infrastructure.
The industry can expect more news from Cloud providers in the next few months as they ramp up their capabilities and channel their go-to-market messaging.
Gain access to more insights from the Ecosystm Cloud Study

Microsoft announced in 2018 that they were investing US$ 5 billion globally in IoT innovation and research for the next 4 years – the focus being on secure IoT, creating development tools and intelligent services for IoT and the edge, and on growing their partner ecosystem.
Last year Microsoft’s industry updates showcased several IoT implementations across industries and their edge-based solutions portfolio, customers and partner ecosystem. The tech giant revealed nearly 150% YoY growth with customers such as Starbucks, Chevron, Walmart, Walgreens, BMW and Volkswagen added to the Azure platform, leveraging IoT services to accelerate their digital transformation journey. Microsoft also announced more than 70 partnerships with some of the big names in the IoT ecosystem, such as Universal Electronics, SAP, and Cradlepoint to extend solutions and support for the Microsoft IoT business.
Extending IoT Capabilities with Strategic Partnerships
There were several recent announcements which indicate that Microsoft is focused on strengthening their IoT and industry capabilities – and this is a timely move. Ecosystm Principal Advisor, Kaushik Ghatak says, “COVID-19 has brought to the fore the need for managing risks better. And the key to managing risks is to have better visibility and drive data-driven decisions; the sweet spot for IoT technologies. IoT is at the core of the Industry 4.0 story where deep domain expertise in industry verticals is a pre-requisite to success. It is heartening to see that Microsoft is taking the lead in building a powerful ecosystem by developing key partnerships with leading providers of Industry solutions.”
Last week, Microsoft and Hitachi announced a strategic alliance to accelerate the digital transformation of the Manufacturing and Logistics industries across Southeast Asia, Japan and North America. The first solutions are expected to be made available in Thailand as early as this month. Hitachi brings to the table their industry solutions, such as Lumada, and their IoT-ready industrial controllers HX Series. These solutions will be fully integrated with the Microsoft cloud platform, leveraging Azure, Dynamics 365 and Microsoft 365.
The three areas where the Hitachi solution is expected to bring strength to Microsoft’s industry offering are:
- Process optimisation and increased manufacturing productivity. Hitachi Digital Supply Chain and Azure IoT leveraged to analyse 4M data collected from manufacturing sites for visualisation/ analysis of production processes
- Logistics optimisation. Digital technologies such as Azure Maps and Hitachi Digital Solution for Logistics/Delivery Optimisation Service to analyse data on parameters such as traffic congestion, storage locations and delivery locations, to enabling smart routing
- Predictive maintenance and remote assist. HoloLens 2, Dynamics 365 Remote Assist and other smart devices, to empower first-line workers
Ecosystm Principal Advisor, Niloy Mukherjee feels that with projections of 43 – 100 billion IoT connected devices in the next few years, IoT is obviously a hot space. “We can think of IoT as a stack with four layers – the devices/sensors, the connection layer, the cloud and computing layer and the business apps layer. With Azure, Microsoft is very well positioned in the cloud and compute layer and can grab a large chunk of this fast-growing market. Tying with players like Hitachi allows Microsoft to integrate with the business apps layer and perhaps also some devices. It is absolutely the right strategy and I would expect them to go for many more such alliances. With Microsoft’s strength in the enterprise market, IoT gives them a great opportunity to increase their share of cloud workloads with customers.”
Addressing the Challenges of IoT Adoption
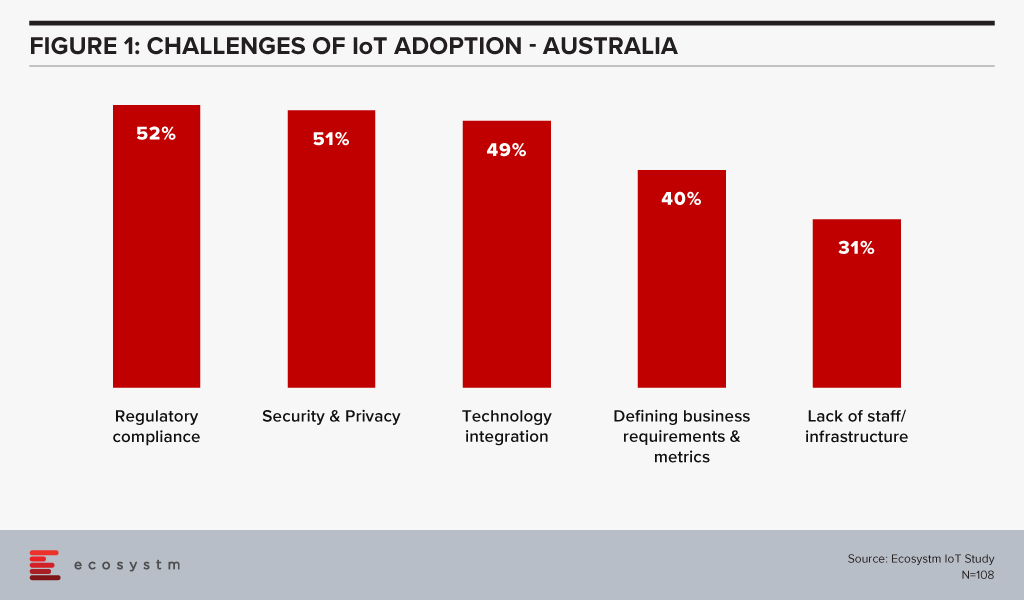
Ecosystm research shows that the biggest challenges in IoT adoption are security and integration concerns (Figure 1).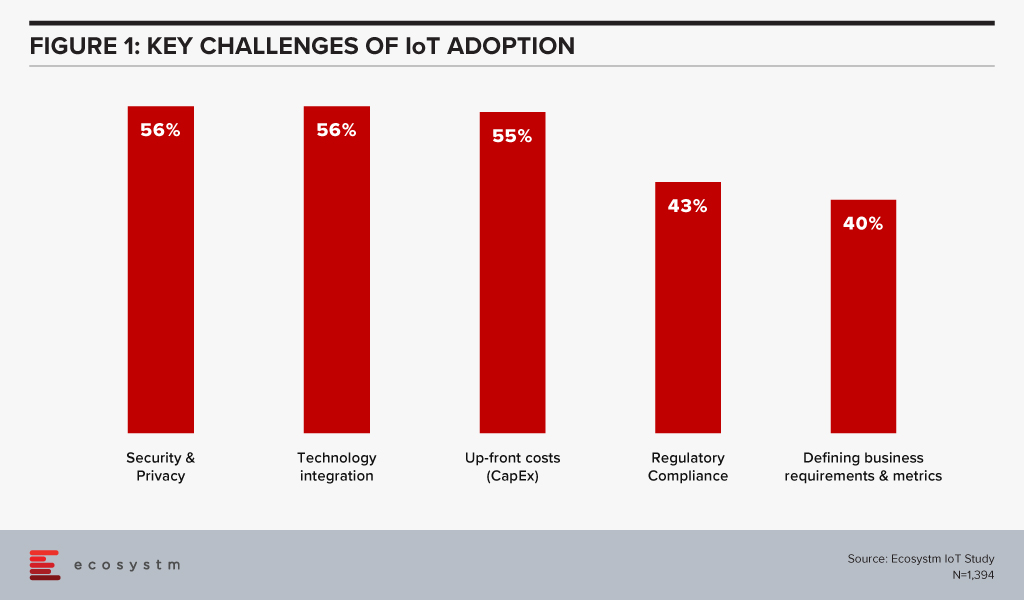
In 2018, when Microsoft started actively focusing on IoT, they also launched the Azure Certified for IoT program to maintain consistency and enhanced interoperability across their device partner ecosystem. This addresses the integration challenges that organisations face when deploying IoT. Microsoft continues to grow their IoT ecosystem, ensuring faster IoT deployments, with hardware and software that has been pre-tested and verified to work with Microsoft Azure IoT services. Last week also saw Cyient joining Microsoft Azure as a certified partner for IoT. Cyient IoT Edge Gateway 5400, their flagship IoT gateway product is now Microsoft Azure Certified for IoT. This is expected to accelerate IoT deployment for Cyient customers and enable a seamless integration of edge devices to the cloud.
Ghatak says, “To scale up their IoT business, Microsoft would need to develop a substantially large ecosystem, beyond few key players such as Hitachi, who dominate at the large enterprise segment of the market. That is where partnerships with smaller and niche industry solutions providers such as Cyient fits in. More niche providers such as Cyient will increase Microsoft’s reach into medium and smaller segments of the enterprise market.”
Addressing the Increasing Threat Landscape
Recent cyber-attack trends and security breach statistics reveal a huge increase in cybercrime activities, in the wake of the COVID-19 pandemic. As the number of IoT sensors, devices and gateways increase, so does the risk of security breaches. As shown in figure 1, cybersecurity concerns are real and can act as a barrier to IoT adoption, despite the benefits that the technology brings. Automated vulnerability management capabilities, that allow risk assessment and patch installation where necessary will see an increase in IoT adoption.
To complement Microsoft Azure IoT security, Microsoft acquired IoT security specialist CyberX, last month. The acquisition will enable greater security for the IoT devices connected to the Microsoft network and will help their customers to gain visibility through a map of devices thus allowing them to gather information on security risks associated with thousands of sensors and connected devices. This will enhance smart grid, smart manufacturing and digital assets and profiles and reduce vulnerabilities across production and supply chain.
Mukherjee says, “The key concern for the expansion of IoT into more and more use cases in the next few years is really going to be security. New areas like VR and AR are emerging from futuristic fantasy to real-world reality. These will tempt many enterprises – but security will be the key concern to address. And so, Microsoft’s simultaneous push on security completely aligns with this. As the Ecosystm MSSP VendorScope results show Microsoft’s strategy on cybersecurity seems to be working.”
Talking about Microsoft’s go-to-market strategy, Mukherjee adds, “Microsoft is obviously spreading its net far and wide for all cloud applications including IoT, to go-to-market with partners. One of the key focus area here is the SME segment, which is forecast to be one of the hot growing segments for IoT in the next few years. The more offerings from the business apps layer that Microsoft integrates, the more they enable their partners to sell to their customers.”

Technologies to automate IT systems and relieve over-stretched IT operations teams have been moving into the mainstream over the last few years. Several factors, driven by the digital era, have made this necessary. Firstly, digital transformation is creating ever-larger IT environments and volumes of data that cannot be managed by manual processes. These distributed systems are also becoming more complex, incorporating IoT, mobile, multi-cloud, containers, and APIs. Moreover, for digital businesses, the financial impact of an outage makes time to resolution critical. Identifying and remediating issues before they affect the user is now paramount. AIOps provides intelligence to the IT operations team that allows them to proactively resolve events before they become outages.
Augmenting IT Operations with AIOps
AIOps allows IT operations teams to not only ensure observability of their systems and reduce noise but to also understand how events are interacting together to affect performance and take corrective action quickly. The primary features of AIOps are:
- Noise reduction. AIOps ingests systems data, surfaces priority anomalies and correlates them together. This brings the number of incidents to investigate back down to a human level. Rackspace recently announced that AIOps helped it reduce alert noise by 99% during the initial stage of its rollout. Successful vendor references typically cite similar figures between 95-99%.
- Root cause analysis. Once priority events have been correlated, AIOps identifies a root cause to enable the operations team to focus its efforts on a resolution. This is a task that proves challenging to perform at speed for a human operator considering the complexity of today’s systems.
- Proactive response. A range of responses is available with AIOps, from directing issues to the appropriate people, to recommending actions that can be taken by operators directly in a collaboration tool, to rules-based workflows performed automatically, such as spinning up additional AWS EC2 instances.
- Learning. By evaluating past failures and successes, AIOps can learn over time which events are likely to become critical and how to respond to them. This brings us closer to the dream of NoOps, where operations are completely automated.
The Impact of COVID-19 on IT Operations
The Ecosystm Digital Priorities in the New Normal study launched this month, asks technology users about how their digital priorities have shifted during the pandemic. Despite pressure to shift to digital delivery, almost 40% of participants reported that their organisations cut headcount in the IT department (Figure 1). Furthermore, over one third had been forced to cut their employees’ salaries. As we have seen in previous crises, IT operations teams are being asked to do more with less and will need automation to bridge the gaps.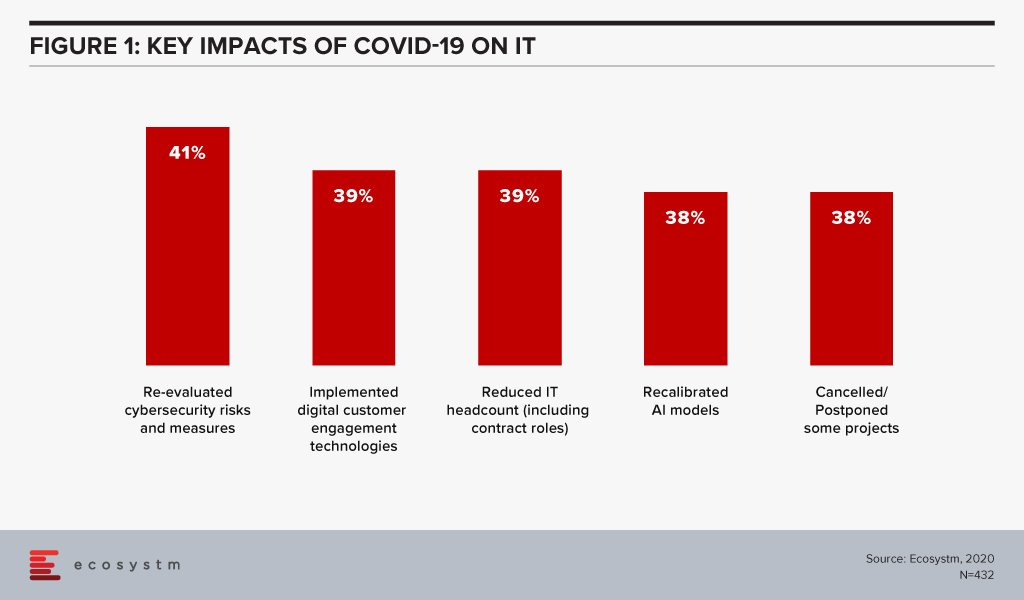
As we begin to move into the next phase of the COVID-19 reality and businesses continue to open, we will see many launch digital services that were conceived of during the crisis. One of the greatest challenges that IT departments face will be scalability as digital businesses grow. AIOps will be a go-to tool for IT operations to ensure uptime and improve user experience. It is likely that the next 12-18 months will be a watershed moment for AIOps.
NLP and the Democratisation of Data
Natural Language Processing (NLP) will be the next string in the bow of AIOps. While the ultimate goal of IT operations is to identify and remediate situations before they have an impact on the user, oftentimes it is the service desk that generates the initial barrage of alerts. AIOps equipped with NLP can extract relevant data from user tickets, correlate them with other system events and potentially even suggest a resolution to the user. Here, ChatOps can help to reduce the workload on the service desk and bring relevant events to the attention of the operations team faster. NLP will also help democratise IT operations data within the organisation. As they digitalise, lines of business (LoBs) besides IT will need access to system health and user experience data but business managers may not have the necessary technical skills to extract them. Chatbots that can return these metrics to non-technical users will begin to proliferate.
AIOps Recommendations
Most IT departments would have discovered the limitations of their current systems during the upheaval caused by recent lockdowns. Only about 7% of organisations in our study reported that they were well-prepared across all areas of IT, to handle the COVID-19 crisis. For those organisations that have yet to invest in AIOps, we recommend starting now but starting small. Develop a topology map to understand where you have reliable data sources that could be analysed by AIOps. Then select a domain by assessing the present level of observability and automation, IT skills gap, frequency of outages, and business criticality. As you add additional domains and the system learns, the value you realise from AIOps will grow.
The power of collaborative AIOps tools would have been undeniable as the COVID-19 crisis began and IT departments were forced to work in a distributed manner. When evaluating a system, carefully consider how it will integrate into your organisation’s preferred collaboration suite, whether it be the AIOps vendor’s proprietary situation tool or a third-party provider like Slack or Microsoft Teams. The ability for operations teams to collaborate effectively reduces time to resolution.
Last week, the Australia government joined other countries in the Asia Pacific region in highlighting the growth of attack surface in the midst of the COVID-19 pandemic.
In our recently launched study Digital Priorities in the New Normal, we find that 87% of organisations in the Asia Pacific have increased investments in one or more cybersecurity solutions. However, this has to be backed by a reassessment of organisations’ risk positions and a re-evaluation of data protection and compliance policies.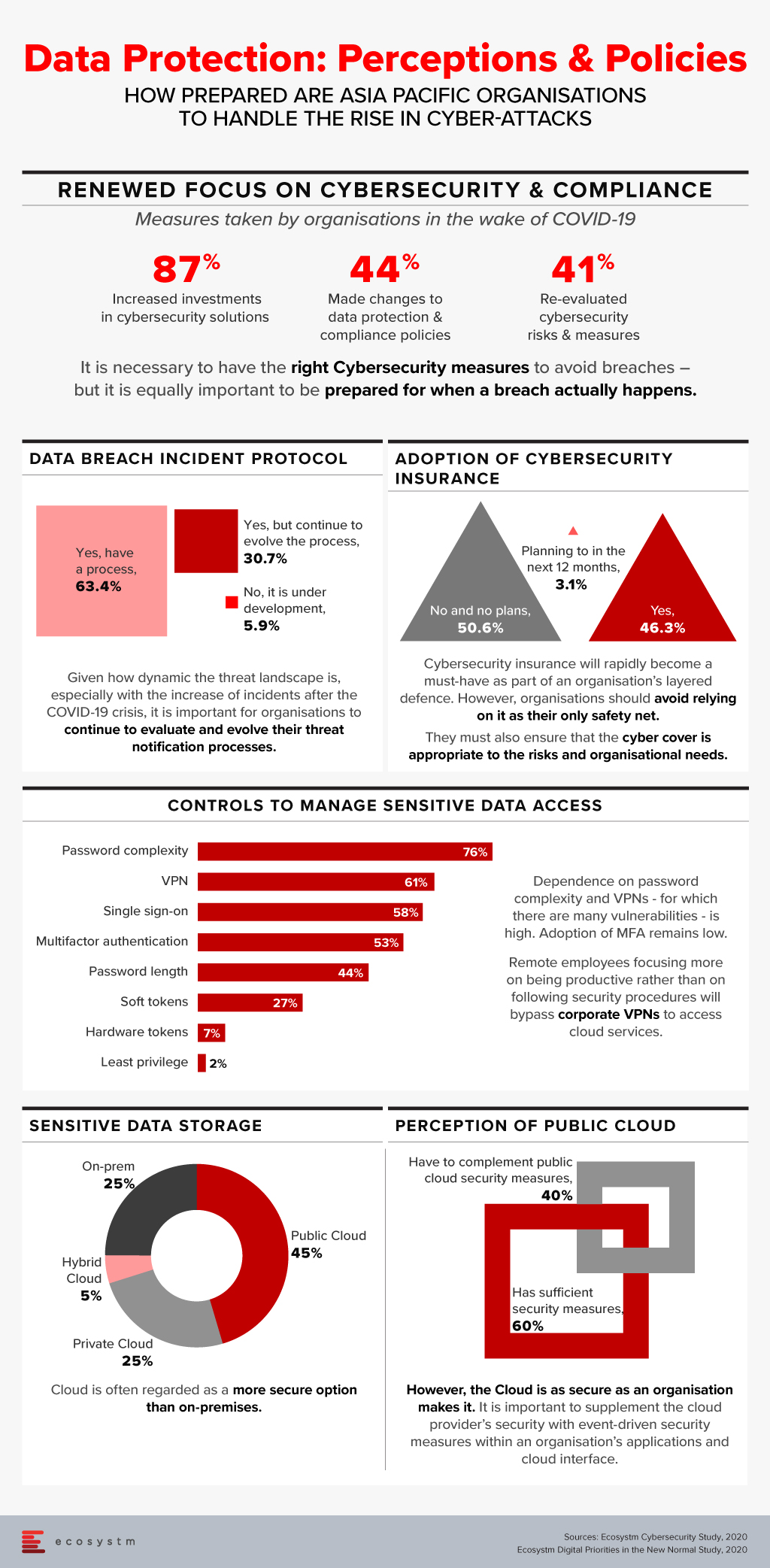

Last week, the Australia Government announced that they have been monitoring persistent and increasing volumes of cyber-attacks by a foreign state-based actor on both government and private sector businesses. The Australian Cyber Security Centre (ACSC) reported that most of the attacks make use of existing open-source tools and packages, which ACSC has dubbed as “copy-paste compromises”. The attackers are also using other methods to exploit such as spear phishing, sending malicious files and using various websites to harvest passwords and more, to exploit systems.
Cybercrime has been escalating in other parts of the world as well. The World Health Organisation (WHO) witnessed a dramatic increase in cyber-attacks directed with scammers impersonating WHO personnel’s official emails targeting the public. The National Cyber Security Centre (NCSC) in the UK alerted the country’s educational institutions and scientific facilities on increased cyber-attacks attempting to steal research associated with the coronavirus. Earlier this month, the Singapore Computer Emergency Response Team (SingCERT) issued an advisory on potential phishing campaigns targeting six countries, including Singapore that exploit government support initiatives for businesses and individuals in the wake of the COVID-19 crisis.
Such announcements are a timely reminder to government agencies and private organisations to implement the right cybersecurity measures against the backdrop of an increased attack surface. These cyber attacks can have business impacts such as theft of business data and destruction or impairment to financial data, creating extended business interruptions. The ramifications can be far-reaching including financial and reputational loss, compliance breaches and potentially even legal action.
A Rise in Spear-Phishing
In Australia, we’re seeing attackers targeting internet-facing infrastructure relating to vulnerabilities in Citrix, Windows IIS web server, Microsoft Sharepoint, and Telerik UI.
Where these attacks fail, they are moving to spear-phishing attacks. Spear phishing is most commonly an email or SMS scam targeted towards a specific individual or organisation but can be delivered to a target via any number of electronic communication mediums. In the spear-phishing emails, the attacker attaches files or includes links to a variety of destinations that include:
- Credential harvesting sites. These genuine-looking but fake web sites prompt targets to enter username and password. Once the gullible target provides the credentials, these are then stored in the attackers’ database and are used to launch credential-based attacks against the organisation’s IT infrastructure and applications.
- Malicious files. These file attachments to emails look legitimate but once downloaded, they execute a malicious malware on the target device. Common file types are .doc, .docx, .xls, .xlsx, .ppt, .pptx, .jpg, .jpeg, .gif, .mpg, .mp4, .wav
- OAuth Token Theft. OAuth is commonly used on the internet to authenticate a user to a wide variety of other platforms. This attack technique uses OAuth tokens generated by a platform and shares with other platforms. An example of this is a website that asks users to authenticate using their Facebook or Google accounts in order to use its own services. Faulty implementation of OAuth renders such integration to cyber-attacks.
- Link Shimming. The technique includes using email tracking services to launch an attack. The attackers send fake emails with valid looking links and images inside, using email tracking services. Once the user receives the email, it tracks the actions related to opening the email and clicking on the links. Such tracking services can reveal when the email was opened, location data, device used, links clicked, and IP addresses used. The links once clicked-on, can in- turn, lead to malicious software being stealthily downloaded on the target system and/or luring the user for credential harvesting.
How do you safeguard against Cyber-Attacks?
The most common vectors for such cyber-attacks are lack of user awareness AND/OR exploitable internet-facing systems and applications. Unpatched or out-of-support internet-facing systems, application or system misconfiguration, inadequate or poorly maintained device security controls and weak threat detection and response programs, compound the threat to your organisation.
Governments across the world are coming up with advisories and guidelines to spread cybersecurity awareness and prevent threats and attacks. ACSC’s Australian Signals Directorates ‘Essential 8’ are effective mitigations for a large majority of present-day attacks. There were also guidelines published earlier this year, specifically with the COVID-19 crisis in mind. The Cyber Security Agency in Singapore (CSA) promotes the ‘Go Safe Online’ campaign that provides regular guidance and best practices on cybersecurity measures.
Ecosystm’s ongoing “Digital Priorities in the New Normal” study evaluates the impact of the COVID-19 pandemic on organisations, and how digital priorities are being initiated or aligned to adapt to the New Normal that has emerged. 41% of organisations in Asia Pacific re-evaluated cybersecurity risks and measures, in the wake of the pandemic. Identity & Access Management (IDAM), Data Security and Threat Analytics & Intelligence saw increased investments in many organisations in the region (Figure 1).
However, technology implementation has to be backed by a rigorous process that constantly evaluates the organisation’s risk positions. The following preventive measures will help you address the risks to your organisation:
- Conduct regular user awareness training on common cyber threats
- Conduct regular phishing tests to check user awareness level
- Patch the internet-facing products as recommended by their vendors
- Establish baseline security standards for applications and systems
- Apply multi-factor authentication to access critical applications and systems – especially internet-facing and SaaS products widely used in the organisation like O365
- Follow regular vulnerability scanning and remediation regimes
- Conduct regular penetration testing on internet-facing applications and systems
- Apply security settings on endpoints and internet gateways that disallow download and execution of files from unfamiliar sources
- Maintain an active threat detection and response program that provides for intrusion detection, integrity checks, user and system behaviour monitoring and tools to maintain visibility of potential attacks and incidents – e.g Security Information & Event Monitoring (SIEM) tools
- Consider managed services such as Managed Threat Detection and Response delivered via security operations (SOC)
- Maintain a robust incident management program that is reviewed and tested at least annually
- Maintain a comprehensive backup regime – especially for critical data – including offsite/offline backups, and regular testing of backups for data integrity
- Restrict and monitor the usage of administrative credentials

The 5G rollouts in Australia by Telstra, Optus and Vodafone will impact consumers and enterprises alike. It is expected that enterprises will see an uptick in IoT adoption, leveraging the lower latency to connect devices for real-time data transfer and insights. Industries, especially those that operate in remote and rural regions of the country such as Agriculture and Mining are expected to benefit immensely.
“However, there are challenges to leveraging digitalisation effectively, including a lack of awareness, knowledge and skills, and funding to support innovation and scale, in aligning with the growing pressure within sectors to meet increasing productivity and compliance requirements,” says Ecosystm Principal Advisor, Jannat Maqbool. “Adoption of IoT specifically is resulting in new data supply chains, that those operating in many industries cannot cater for with respect to infrastructure and also the skills necessary to process and extract valuable insights from the data.”
Ecosystm research shows that only 37% of organisations looking to adopt IoT in Australia have a strategic internal team to create the roadmap and manage the deployment. This indicates a lack of skills that organisations can utilise, depending on external resources such as consulting firms and ISVs instead. To cater to the expected growth in Australia’s IoT market, IoT Alliance Australia (IoTAA) – that represents more than 500 participating organisations and 1,000 individual participants – has come forward with the IoT Australia Skills Barometer survey.
The survey created in association with La Trobe University aims to gauge the IoT skills gap, to inform educators and adopters on the potential areas of focus for future skills development. It covers questions on IoT adoption, challenges expected, solutions being evaluated, and courses needed.
Addressing the Skills Gap
As the adoption of IoT increases, there will be added requirement for skills in data storage, infrastructure management and creating frameworks. The survey is expected to help the industry determine the skills gap, isolate training and re-skilling requirements and develop courses and hands-on sessions to address the end-to-end services requirements and better utilisation of data gathered from the devices.
There are some courses that are already available – mostly run in collaboration with industry. Last year, Rio Tinto, the Western Australia Government and South Metropolitan TAFE developed Australia’s first nationally-recognised remote operations course. Earlier this year, RMIT partnered with IBM to deliver the IoT and 5G business opportunity courses to equip business professionals with the right technology and business skills for IoT projects.
“Awareness of the potential of emerging technologies needs to target both non-technical and technical members of the organisation. This wider buy-in is needed to drive thinking around the ‘why’ from stakeholders across the business, enabling a more informed decision around the potential impact on existing resources, infrastructure, processes, products, required investment and business outcomes,” says Maqbool. “Any education and training program needs to allow for this focus on awareness, then provide opportunities to build on this for those that then want to gain the deeper knowledge and technical skills required to effectively leverage the IoT.”
“Education and training programs to support the uptake of digital technologies across the wider population and traditionally non-digital industries require a contextual learning and a flexible delivery approach.”
Government and Industry working together
“A digital divide exists in many countries – especially for those in rural communities. They are often not in a position to access the infrastructure necessary to support a real-world connection in a contextual learning environment, let alone having the digital literacy and scaffolding to get to a point where they can effectively consider leveraging emerging technologies,” says Maqbool.
This is where governments play a larger role. To accelerate innovation and make better use of technology the Australian Government is supporting clear communication and a better understanding of IoT, implementing standards and regulations, upgrading digital infrastructure, creating opportunities for economic and social benefits and collaborating with research and education institutes to deliver skills, innovation and growth in the IoT sector.
One of the key areas of focus will have to be cybersecurity. Regulatory compliance and security & privacy issues are the key barriers of IoT adoption in Australia (Figure 1).
Last year, the Australian government released a draft code of practice to enable businesses implementing IoT solutions to follow certain principles as a voluntary measure to defend against threats.
The Government is also seeing a larger potential for IoT in some industries. To support the Agriculture industry, the Australia Government has allocated USD 90 million to the Smart Farms program to support the development and uptake of best practices and technologies in farms, fisheries and forestry, with a special focus on regional communities. In its FY2019-20 federal budget, the Government announced plans to invest USD 1.4 million for a feasibility study and assess ways on improving digital on-farm connectivity. Similarly, Australia’s National Landcare Program (NLP) delivered by the Department of Agriculture, Water and the Environment (DAWE) is receiving financial support until June 2023.

The Wireless Broadband Alliance (WBA) was formed in 2003 to enable a seamless and interoperable Wi-Fi experience across the global wireless ecosystem. The key objective of the alliance was to bring together multiple stakeholders – such as telecom providers, technology vendors and enterprises – to work on areas such as industry guidelines, pilot projects, standards to promote end-to-end services and drive adoption in Wi-Fi, 5G, IoT and others.
WBA OpenRoaming™
Ecosystm Principal Advisor, Ashok Kumar says, “Wi-Fi has gained increasing popularity worldwide over the last two decades and has now become an essential network technology with ubiquitous service that it is utilitarian. However, it has been viewed as a collection of islands of heterogenous networks, requiring re-authentication each time a mobile user transits from one network and re-connects with another Wi-Fi network, with the associated hurdles of logging back in, making it cumbersome.”
“The lack of interoperability between Wi-Fi networks has been a drawback for service providers, compared to the ease of use associated with global mobile networks, such as 4G, LTE, 5G, and so on, which offer seamless roaming connectivity.”
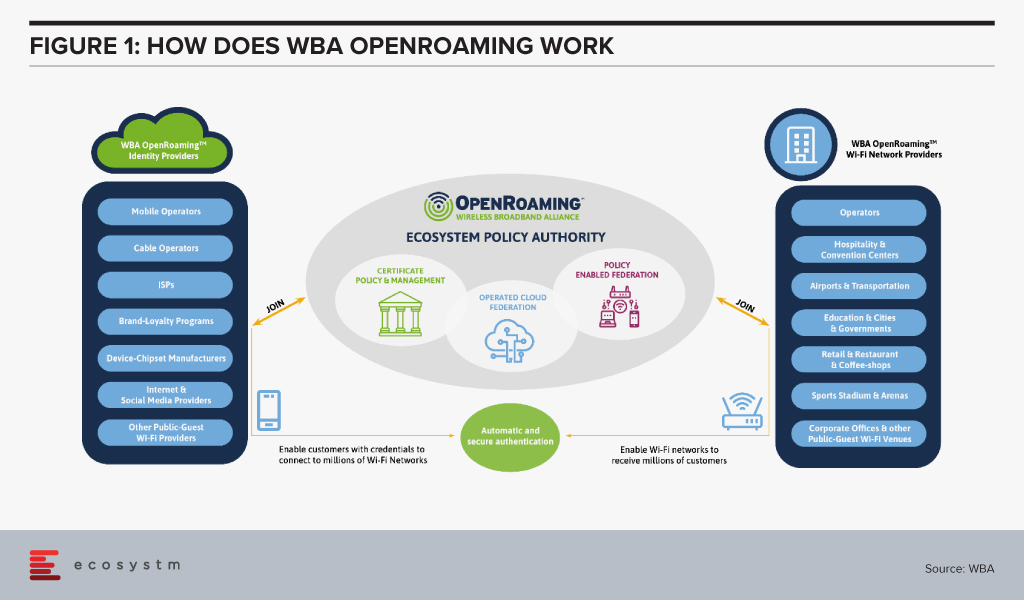
The WBA OpenRoaming™ initiative was announced last month, to create a globally available Wi-Fi ecosystem that offers a federation of automatic and secure connections for billions of devices to millions of Wi-Fi networks. It provides a new global standards-led approach, removing public-guest Wi-Fi connectivity barriers and brings greater convenience and security to the wireless ecosystem. WBA OpenRoaming™ removes the need to search for Wi-Fi networks, to repeatedly enter or create login credentials, or to constantly reconnect or re-register to public Wi-Fi networks.
Several leading technology companies and telecom service providers have extended support to WBA OpenRoaming™ standards – Samsung, Google, Cisco, Intel, Aptilo, AT&T, Boingo Wireless, Broadcom, Comcast, Deutsche Telekom and Orange to name a few.
“Wi-Fi is arguably the most ground-breaking wireless technology of our time. From the first public Wi-Fi hotspots in the early 2000s which enabled radically increased productivity on the move, through to the role Wi-Fi has in today’s pandemic environment. With WBA OpenRoaming™ we want to revolutionise how individual users as well as businesses engage with Wi-Fi, removing the need to repeatedly log in, re-connect, share passwords or re-register for Wi-Fi networks as we travel locally, nationally or internationally”, said Tiago Rodrigues, CEO of the WBA, “Instead, no matter where we are, the new framework automates how users connect to Wi-Fi while seamlessly aligning to cellular network connectivity. It does so by bringing together a federation of trusted identity providers so that individual users are allowed to automatically join any network managed by a federation member.”
WBA OpenRoaming™ can simplify Wi-Fi, much like the cellular roaming experience. Kumar says, “ The WBA OpenRoaming™, with support from major global service providers, network solution vendors, and authentication & security firms, has the potential to address the issue of seamless interoperability in the Wi-Fi networks ecosystem with ease-of-use and security.”
WBA OpenRoaming™ Framework
The framework and standards are based on cloud federation, consisting of a global database of networks and identities, dynamic discovery and the Wireless Roaming Intermediary Exchange (WRIX); cybersecurity consisting of Public Key Infrastructure a RadSec providing the certificate policy, management and brokerage services; and network automation facilitated by an automated roaming consortium framework and policy and Wi-Fi CERTIFIED Passpoint®*.
The Impact of WBA OpenRoaming™
“Enterprises are expected to benefit enormously from the opportunity to create new commercial business models and innovative services with speed and simplicity,” says Kumar.
Maturing mobile technologies such as 5G and Wi-Fi 6 along with next generation wireless devices, could make OpenRoaming™ more seamless and extend its applications further.
Cisco in particular has been leading the charge with several pilots that showcase the benefits of OpenRoaming™. Earlier this year, it partnered with Oxbotica, an autonomous vehicle software provider, to demonstrate how OpenRoaming™ can unlock the potential of autonomous vehicle fleets, allowing a seamless and secure sharing of high-volume data while on the move.
Last year, Cisco also showcased the benefits of OpenRoaming™ in a pilot at the Mobile World Congress in Barcelona with Samsung as the identity provider. Attendees were connected to the network throughout the venue, with connectivity extended to even local train stations and the airport. This unified experience was possible despite the fact that at least three network providers were involved. Pilots such as these gives the industry a glimpse of what benefits lie ahead.
Kumar sees the impact being extended across industries. “The impact of WBA OpenRoaming™ will be in the introduction of innovative services for consumers and enterprise users in public Wi-Fi networks in industries such as Hospitality, Transportation (airport and rail), Retail outlets, Smart City solutions, and local community networks.”
Learn more about WBA OpenRoaming™, visit www.openroaming.org
*Wi-Fi CERTIFIED Passpoint® is a registered trademark of the Wi-Fi Alliance
In his blog, The Cybercrime Pandemic, Ecosystm Principal Advisor, Andrew Milroy says, “Remote working has reached unprecedented levels as organisations try hard to keep going. This is massively expanding the attack surface for cybercriminals, weakening security and leading to a cybercrime pandemic. Hacking activity and phishing, inspired by the COVID-19 crisis, are growing rapidly.” Remote working has seen an increase in adoption of cloud applications and collaborative tools, and organisations and governments are having to re-think their risk management programs.
We are seeing the market respond to this need and May saw initiatives from governments and enterprises on strengthening risk management practices and standards. Tech vendors have also stepped up their game, strengthening their Cybersecurity offerings.
Market Consolidation through M&As Continues
The Cybersecurity market is extremely fragmented and is ripe for consolidation. The last couple of years has seen some consolidation of the market, especially through acquisitions by larger platform players (wishing to provide an end-to-end solution) and private equity firms (who have a better view of the Cybersecurity start-up ecosystem). Cybersecurity providers continue to acquire niche providers to strengthen their end-to-end offering and respond to market requirements.
As organisations cope with remote working, network security, threat identification and identity and access management are becoming important. CyberArk acquired Identity as a Service provider Idaptive to work on an AI-based identity solution. The acquisition expands its identity management offerings across hybrid and multi-cloud environments. Quick Heal invested in Singapore-based Ray, a start-up specialising in next-gen wireless and network technology. This would benefit Quick Heal in building a safe, secure, and seamless digital experience for users. This investment also shows Quick Heal’s strategy of investing in disruptive technologies to maintain its market presence and to develop a full-fledged integrated solution beneficial for its users.
Another interesting deal was Venafi acquiring Jetstack. Jetstack’s open-source Kubernetes certificate manager controller – cert-manager – with a thriving developer community of over 200 contributors, has been used by many global organisations as the go-to tool for using certificates in the Kubernetes space. The community has provided feedback through design discussion, user experience reports, code and documentation contributions as well as serving as a source for free community support. The partnership will see Venafi’s Machine Identity Protection having cloud-native capabilities. The deal came a day after VMware announced its intent to acquire Octarine to extend VMware’s Intrinsic Security Capabilities for Containers and Kubernetes and integrate Octarine’s technology to VMware’s Carbon Black, a security company which VMware bought last year.
Cybersecurity vendors are not the only ones that are acquiring niche Cybersecurity providers. In the wake of a rapid increase in user base and a surge in traffic, that exposed it to cyber-attacks (including the ‘zoombombing’ incidents), Zoom acquired secure messaging service Keybase, a secure messaging and file-sharing service to enhance their security and to build end-to-end encryption capability to strengthen their overall security posture.
Governments actively working on their Cyber Standards
Governments are forging ahead with digital transformation, providing better citizen services and better protection of citizen data. This has been especially important in the way they have had to manage the COVID-19 crisis – introducing restrictions fast, keeping citizens in the loop and often accessing citizens’ health and location data to contain the disaster. Various security guidelines and initiatives were announced by governments across the globe, to ensure that citizen data was being managed and used securely and to instil trust in citizens so that they would be willing to share their data.
Singapore, following its Smart Nation initiative, introduced a set of enhanced data security measures for public sector. There have been a few high-profile data breaches (especially in the public healthcare sector) in the last couple of years and the Government rolled out a common security framework for public agencies and their officials making them all accountable to a common code of practice. Measures include clarifying the roles and responsibilities of public officers involved in managing data security, and mandating that top public sector leadership be accountable for creating a strong organisational data security regime. The Government has also empowered citizens to raise a flag against unauthorised data disclosures through a simple incident report form available on Singapore’s Smart Nation Website.
Australia is also ramping up measures to protect the public sector and the country’s data against threats and breaches by issuing guidelines to Australia’s critical infrastructure providers from cyber-attacks. The Australian Cyber Security Centre (ACSC) especially aims key employees working in services such as power and water distribution networks, and transport and communications grids. In the US agencies such as the Cybersecurity and Infrastructure Security Agency (CISA) and the Department of Energy (DOE) have issued guidelines on safeguarding the country’s critical infrastructure. Similarly, UK’s National Cyber Security Centre (NCSC) issued cybersecurity best practices for Industrial Control Systems (ICS).
Cyber Awareness emerges as the need of the hour
While governments will continue to strengthen their Cybersecurity standards, the truth is Cybersecurity breaches often happen because of employee actions – sometimes deliberate, but often out of unawareness of the risks. As remote working becomes a norm for more organisations, there is a need for greater awareness amongst employees and Cybersecurity caution should become part of the organisational culture.
Comtech received a US$8.4 million in additional orders from the US Federal Government for a Joint Cyber Analysis Course. The company has been providing cyber-training to government agencies in the communications sector. Another public-private partnership to raise awareness on Cybersecurity announced in May was the MoU between Europol’s European Cybercrime Centre (EC3) and Capgemini Netherlands. With this MoU, Capgemini and Europol are collaborating on activities such as the development of cyber simulation exercises, capacity building, and prevention and awareness campaigns. They are also partnered on a No More Ransomware project by National High Tech Crime Unit of the Netherlands’ Police, Kaspersky and McAfee to help victims fight against ransomware threats.
The Industry continues to gear up for the Future
Technology providers, including Cybersecurity vendors, continue to evolve their offerings and several innovations were reported in May. Futuristic initiatives such as these show that technology vendors are aware of the acute need to build AI-based cyber solutions to stay ahead of cybercriminals.
Samsung introduced a new secure element (SE) Cybersecurity chip to protect mobile devices against security threats. The chip received an Evaluation Assurance Level (EAL) 6+ certification from CC EAL – a technology security evaluation agency which certifies IT products security on a scale of EAL0 to EAL7. Further applications of the chip could include securing e-passports, crypto hardware wallets and mobile devices based on standalone hardware-level security. Samsung also introduced a new smartphone in which Samsung is using a chipset from SK Telecom with quantum-crypto technology. This involves Quantum Random Number Generator (QRNG) to enhance the security of applications and services instead of using normal random number generators. The technology uses LED and CMOS sensor to capture quantum randomness and produce unpredictable strings and patterns which are difficult to hack. This is in line with what we are seeing in the findings of an Ecosystm business pulse study to gauge how organisations are prioritising their IT investments to adapt to the New Normal. 36% of organisations in the Asia Pacific region invested significantly in Mobile Security is a response to the COVID-19 crisis.
The same study reveals that nearly 40% of organisations in the region have also increased investments in Threat Analysis & Intelligence. At the Southern Methodist University in Texas, engineers at Darwin Deason Institute for Cybersecurity have created a software to detect and prevent ransomware threats before they can occur. Their detection method known as sensor-based ransomware detection can even spot new ransomware attacks and terminates the encryption process without relying on the signature of past infections. The university has filed a patent for this technique with the US Patent and Trademark Office.
Microsoft and Intel are working on a project called STAMINA (static malware-as-image network analysis). The project involves a new deep learning approach that converts malware into grayscale images to scan the text and structural patterns specific to malware. This works by converting a file’s binary form into a stream of raw pixel data (1D) which is later converted into a photo (2D) to feed into image analysis algorithms based on a pre-trained deep neural network to scan and classify images as clean or infected.












