Any new technology that changes our businesses or society for the better often has a potential dark side that is viewed with suspicion and mistrust. The media, especially on the Internet, is eager to prey on our fears and invoke a dystopian future where technology has gotten out of control or is used for nefarious purposes. For examples of how technology can be used in an unexpected and unethical manner, one can look at science fiction movies, Artificial Intelligence (AI) vs AI chatbots conversations, autonomous killer robots, facial recognition for mass surveillance or the writings of Sci-Fi authors such as Isaac Asimov and Iain M. Banks that portrays a grim use of technology.
This situation is only exacerbated by social media and the prevalence of “fake news” that can quickly propagate incorrect, unscientific or unsubstantiated rumours.
As AI is evolving, it is raising some new ethical and legal questions. AI works by analysing data that is fed into it and draws conclusions based on what it has learned or been trained to do. Though it has many benefits, it may pose a threat to humans, data privacy, and the potential outcomes of the decisions. To curb the chances of such outcomes, organisations and policymakers are crafting recommendations about ensuring the responsible and ethical use of AI. In addition, governments are also taking initiatives to take it a step further and working on the development of principles, drafting laws and regulations. Tech developers are also trying to self-regulate their AI capabilities.
Amit Gupta, CEO, Ecosystm interviewed Matt Pollins, Partner of renowned law firm CMS where they discussed the implementation of regulations for AI.
To maximise the benefits of science and technology for the society, in May 2019, World Economic Forum (WEF) – an independent international organisation for Public-Private Cooperation – announced the formation of six separate fourth industrial revolution councils in San Francisco.
The goal of the councils is to work on a global level around new technology policy guidance, best policy practices, strategic guidelines and to help regulate technology under six domains – AI, precision medicine, autonomous driving, mobility, IoT, and blockchain. There is participation of over 200 industry leaders from organisations such as Microsoft, Qualcomm, Uber, Dana-Farber, European Union, Chinese Academy of Medical Sciences and the World Bank, to address the concerns around absence of clear unified guidelines.
Similarly, the Organization for Economic Co-operation and Development (OECD) created a global reference point for AI adoption principles and recommendations for governments of countries across the world. The OECD AI principles are called “values-based principles,” and are clearly envisioned to endorse AI “that is innovative and trustworthy and that respects human rights and democratic values.”
Likewise, in April, the European Union published a set of guidelines on how companies and governments should develop ethical applications of AI to address the issues that might affect society as we integrate AI into sectors like healthcare, education, and consumer technology.
The Personal Data Protection Commission (PDPC) in Singapore presented the first edition of a Proposed Model AI Governance Framework (Model Framework) – an accountability-based framework to help chart the language and frame the discussions around harnessing AI in a responsible way. We can several organisations coming forward on AI governance. As examples, NEC released the “NEC Group AI and Human Rights Principles“, Google has created AI rules and objectives, and the Partnership on AI was established to study and plan best practices on AI technologies.
What could be the real-world challenges around the ethical use of AI?
Progress in the adoption of AI has shown some incredible cases benefitting various industries – commerce, transportation, healthcare, agriculture, education – and offering efficiency and savings. However, AI developments are also anticipated to disrupt several legal frameworks owing to the concerns of AI implementation in high-risk areas. The challenge today is that several AI applications have been used by consumers or organisations only for them to later realise that the project was not ethically fit. An example is the development of a fully autonomous AI-controlled weapon system which is drawing criticism from various nations across the globe and the UN itself.
“Before an organisation embarks on the project, it is vital for a regulation to be in place right from the beginning of the project. This enables the vendor and the organisation to reach a common goal and understanding of what is ethical and right. With such practices in place bias, breach of confidentiality and ethics can be avoided” says Ecosystm Analyst, Audrey William. “Apart from working with the AI vendor and a service provider or systems integrator, it is highly recommended that the organisation consult a specialist such as Foundation for Responsible Robotics, Data & Society, AI Ethics Lab that help look into the parameters of ethics and bias before the project deployment.”
Another challenge arises from a data protection perspective because AI models are fed with data sets for their training and learning. This data is often obtained from usage history and data tracking that may compromise an individual’s identity. The use of this information may lead to a breach of user rights and privacy which may leave an organisation facing consequences around legal prosecutions, governance, and ethics.
One other area that is not looked into is racial and gender bias. Phone manufacturers have been criticised in the past on matters of racial and gender bias, when the least errors in identification occur with light-skinned males. This opened conversations on how the technology works on people of different races and genders.
San Francisco recently banned the use of facial recognition by the police and other agencies, proposing that the technology may pose a serious threat to civil liberties. “Implementing AI technologies such as facial recognition solution means organisations have to ensure that there are no racial bias and discrimination issues. Any inaccuracy or glitches in the data may tend to make the machines untrustworthy” says William.
Given what we know about existing AI systems, we should be very concerned that the possibilities of technology breaching humanitarian laws, are more likely than not.
Could strong governance restrict the development and implementation of AI?
The disruptive potential of AI poses looming risks around ethics, transparency, and security, hence the need for greater governance. AI will be used safely only once governance and policies have been framed, mandating its use.
William thinks that, “AI deployments have positive implications on creating better applications in health, autonomous driving, smart cities, and a eventually a better society. Worrying too much about regulations will impede the development of AI. A fine line has to be drawn between the development of AI and ensuring that the development does not cross the boundaries of ethics, transparency, and fairness.”
While AI as a technology has a way to go before it matures, at the moment it is the responsibility of both organisations and governments to strike a balance between technology development and use, and regulations and frameworks in the best interest of citizens and civil liberties.
Singapore is encouraging the adoption of technology in the legal sector for higher efficiencies. In May, the Ministry of Law (MinLaw), Enterprise Singapore, the Infocomm Media Development Authority (IMDA) and the Law Society of Singapore (LawSoc) announced the launch of a new SmartLaw Guild to encourage law firms to adopt technology.
The SmartLaw Guild brings together case studies from the legal industry and organises knowledge sharing sessions. Speaking at the launch of SmartLaw Guild, Communications and Information Minister S Iswaran, said that the majority of legal practices in Singapore are catered to the SME sector given that 90% of organisations in Singapore fall under the category. The Government is making an effort in the evolution of technology to support the SME legal practices. Mr. Iswaran also encouraged practicing lawyers to take advantage of the skills training provided by the IMDA’s Techskills Accelerator initiative in areas such as cybersecurity, AI and data science.
Why have Law Firms been Slow in Tech Uptake?
A LawSoc survey held in 2018 showed that the adoption of technology helps in the delivery of legal services but only an estimated 12% of law firms in Singapore appears to have adopted digital technology till date. Hence, to encourage digitalisation of the legal industry, legal firms in Singapore will benefit from the SGD 3.68 million fund that has been set aside, to provide them with funding support for adopting technology solutions.
Commenting on the announcement, Ecosystm VP & General Counsel, Nandini Navale said “Across jurisdictions, law firms are bound to licensing and regulatory conditions and have to follow strict standards of professional ethics, confidentiality, and care to clients. This could be a possible reason for their ‘abundantly cautious’ approach towards the adoption of new technology and digitalisation. A glitch or even a minor fault in the technology could result in the loss of license to practise, breach of regulatory obligations, reputational damage or can compromise the interest/privacy of clients. Therefore, AI and technology in systems and processes will have to be proven reliable and fail-safe as a condition for the implementation in the legal sector.”
Law has been a conservative industry. This is fast changing, however with the “BigLaw” in countries investing heavily in technology and looking to implement AI to help their legal staff perform due diligence and research, provide additional legal insights and in process automation in legal work.
Advanced technology solutions powered by AI are enhancing business capabilities and the adoption of AI in the legal industry can help in a quicker resolution of disputes and more consistent outcomes. “AI is capable of transforming the legal sector. The technology could be used to sift through volumes of case law and litigation history, and help lawyers to interpret, prepare and support their positions. Legal issues spotters are being utilised in the contract due diligence and review, legal-tech being deployed for routine and low-value work. Applications for time trackers, billing and invoicing, and legal data analytics are also being adopted” says Navale “The Singapore Government is indeed walking the talk – an example of this is the introduction of the Venture Capital Investment Model Agreements (VIMA) documentation.” The initiative was launched in 2018 by the Singapore Academy of Law (SAL) and the Singapore Venture Capital & Private Equity Association (SVCA) which comprises a set of standard documents that improve the process of structuring a deal and transactions for venture capital firms, start-ups, and SMEs. The core working group for the initiative adopted technology and created a questionnaire that guides through the documentation with auto-versioning and customisation to save time, cost and effort.
How have some Disruptive Technologies Impacted the Legal Industry?
Amit Gupta, CEO, Ecosystm interviewed Matt Pollins, Partner of renowned law firm CMS where they discussed the legal implications of AI as well as the uptake of new technologies in the legal industry.
What do you think are the implications of technology adoption in the legal industry?
Let us know in your comments below.
Over the last few years, there has been a noticeable increase in the number of educational institutions adopting technology to deliver solutions such as learning management, collaboration and support activities. The ubiquity of cloud solutions allows institutions to focus on enhancing the educational experience for students, teachers and administration through emerging teaching methods such as online platforms, interactive systems, and remote management of mission-critical projects and research.
Drivers of Transformation in Education
Education systems, depending on the country, face several problems ranging from achieving universal education goals, limited access to resources, student retention, student recruitment, to conducting cutting-edge research. Moreover, today’s students are millennials and post-millennials, who are digital natives – pushing educational institutions to adopt technology to attract the right cohort and provide an education that equips the students for the workplace of the future. The industry is being driven to transform to keep up with student expectations on delivery, access to the resource, and how they choose to communicate with their educators and peers. Cloud-based offerings are helping educational institutions to overcome these challenges. The top drivers of Education are:
- Personalised Learning. Modern pedagogy encourages personalised learning, where students can choose their own learning path. With the growth of virtual learning environments and eLearning technologies, institutions are able to change the ways they teach, tailoring the curriculum to individual needs, monitoring an individual’s learning journey and providing just-in-time feedback.
- Collaborative Education. Collaborative education principles are based on the premise that many students learn better by communicating with their peer network and not in silos. Also, increasingly, especially at the primary and secondary levels, parents are regarded as a significant stakeholder in a child’s education.
- Efficient Delivery. Most educational institutions are focused on efficient delivery, not only to be more financially sustaining but also so that students, teachers and administration have the ability to access information, including content and learning management systems, anytime and anywhere. The focus is on creating more a flexible work environment and increasing practicality and ease of use for students and educators.
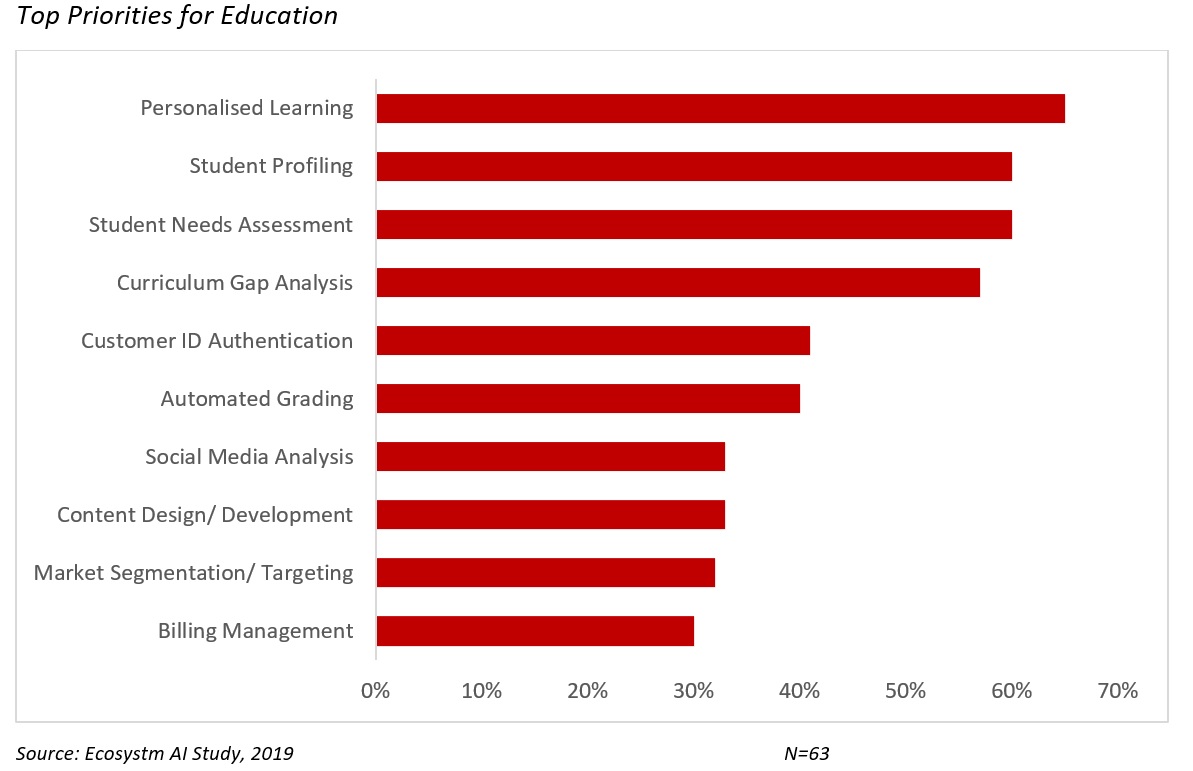
The global Ecosystm AI study reveals the top priorities for educational institutions focused on adopting emerging technologies.
Cloud as an Enabler of Transformation
Cloud gives access to an immense knowledge base that students, educators, and institutions as a whole can leverage. The reach and availability of connectivity has increased the number of users of cloud-based education solutions for remote learning, which helps in the goal of personalised learning. Cloud solutions can also fulfil the demand for collaborative education with reliable and scalable infrastructure. It enables a more collaborative teaching and learning approach, with easy maintenance and management of monitoring and control solutions. Moreover, it promotes efficient delivery as educational institutions look to migrate legacy systems onto the cloud, and increasingly procure SaaS solutions. Cloud not only reduces the burden on an institution’s CapEx but is increasingly being seen as an essential enabler of digital transformation (DX).
In fact, the key benefits that educational institutions are realising from cloud adoption, according to the global Ecosystm Cloud study, are:
- Increased work process efficiency. As the industry becomes more complicated with the advances in pedagogy and technology, cloud is helping institutions to streamline workflows and enabling the participation of multiple stakeholders, some on campus and some remote. One must not forget that education requires an immense amount of administrative work, by both teachers and allied workforce.
- Improved service levels and business agility. The scalability that Cloud provides, especially during high-volume periods such as admissions and examinations, gives educational institutions the ability to be agile. Also, back-up and disaster recovery are key in education, and many institutions start their Cloud journey with storage and back up.
- Simplified sharing of systems/information across departments. Information sharing across different departments becomes easier with the rising penetration of mobile devices such as phones, tablets, and laptops in the classrooms for both students and teachers. Cloud technology ensures that the data shared between devices occurs safely and efficiently.
Examples of Transformation in Education
Virtual Classrooms and Schools
Unlike traditional methods of teaching, virtual classrooms are enabling students to learn and access content without their presence in schools or universities and from anywhere across the globe. The benefit of virtual schools and classrooms is that they do not require any heavy infrastructure or technical equipment to run. In a virtual world, teachers and students can connect with each other in a fast, flexible, and cost-effective way. It enables teachers to host live chats, share lectures and videos, create interactive learning activities and receive instant student feedback.
For example, Florida Virtual School is a full-time online school providing virtual K-12 education to students all over the world. It is a recognised eLearning school and provides custom solutions to meet students’ requirements. This model is being replicated globally especially in remote areas where an actual school premise may not be feasible or is too expensive.
Research & Experimentation
The remote handling of projects and experiments is enabling education institutions to overcome the challenge of carrying them out in a controlled and safe environment. ChemCollective, a project of the National Science Digital Library in the US, enables students to interact with a flexible learning environment in which students can access online chemistry labs to apply formulas, perform experiments and learn in realistic and engaging ways, like working scientists.
Open Education Resources
Cloud is enabling the development of open source content for schools and colleges. The challenge with the existing books and lectures is that they get dated. Cloud is enabling a wealth of content through open repositories and legal protocols to allow a community to collaborate and update the information. Open educational resources (OERs) are developed and can be modified by the creators and administrators. The community can contribute to maps, slides, worksheets, podcasts, syllabi or even textbooks. The copyright is associated via legal tools such as Creative Commons licenses, so others can freely access, reuse, translate, and modify them.
As textbooks and course material can now be updated in real-time and offered through a cloud-based subscription model, this now opens up new streams of revenue for publishers. However, this then raises the conversation that textbook prices are increasing while students have no option to purchase second-hand books or sell books once they are done with them.
MOOCs
Massive Open Online Courses (MOOCs) platforms both provide content to students in areas of personal interest and additional sources of revenue to renowned global institutions. A quick look at Coursera’s website shows online courses from reputed institutions such as MIT and Johns Hopkins University. There are still providers such as the Khan Academy that do not actively monetise the material they provide, but increasingly institutions look at MOOC to generate more revenues, by offering remote learning options to individuals, as well as by collaborating with local universities to make their courses available to overseas students – a previously untapped market.
Cloud computing is transforming the classroom and learning experiences the way educators, curriculum leads, and specialists recommend. The technology has a huge role to play in enabling transformation in Education – for national education systems, for educational institutions, and ultimately for the students.
How else do you think Cloud can transform the education industry? Let us know in your comments below.
On 17 May 2019, the New Zealand Prime Minister Jacinda Ardern and the Singapore Prime Minister Lee Hsien Loong signed a formal arrangement, to step up collaboration in the areas of trade, defence, cybersecurity, science and technology, and arts and culture.
To strengthen cybersecurity, the Cyber Security Agency of Singapore (CSA) and the National Cyber Policy Office (NCPO) of New Zealand inked an agreement on information sharing, cybersecurity and capacity building in the region. A new Cyber Security Arrangement will support greater information exchange, including through an annual cybersecurity dialogue between the two countries. The aim of the agreement is to increase information exchange, prevent incidents and threats and follow best practices on data, infrastructure, and systems protection.
Commenting on the announcement Ecosystm Principal Advisor, New Zealand-based Jannat Maqbool, said, “Engaging internationally on cybersecurity research and initiatives is fundamental given the trans-boundary nature of the cyberspace. As both nations become more digitised and connected, a collaboration will enable each to leverage strengths in key areas to develop a multi-pronged approach to cybersecurity. Both countries will also be in a better position to weigh in on the development of rules-based international order for cyberspace.”
Echoing these comments, Ecosystm Board Advisor, and former Global Head, Digital Development Unit at the World Bank, Randeep Sudan explains how cybersecurity is critical to the growth and development of the digital economy. “Mitigating cyber risks will require coordinated action by multiple stakeholders, including governments, the private sector, academia, and non-governmental organisations,” Sudan says. These bilateral and multilateral G2G partnerships are, therefore, an essential piece in tackling cyber threats. “Given that Singapore and New Zealand are leading players in cyberspace, a G2G collaboration between them will offer learnings of immense value to other governments,” Sudan continues.
Due to Ecosystm’s own close ties with New Zealand, and considering that we are headquartered in Singapore, we are ourselves actively engaged in promoting the dialogue between New Zealand and Singapore. Ecosystm CEO Amit Gupta and Chief Operating Officer, Ullrich Loeffler are in New Zealand this week to participate in Techweek New Zealand (an annual initiative to promote and build awareness for new technologies and innovation in New Zealand) to meet key stakeholders and attend industry events.
 |
 |
Commenting on the sidelines of Techweek, Amit Gupta gave his thoughts on the agreement, “Both New Zealand and Singapore are in hyper-innovation mode at the moment. With the advent of Blockchain and AI especially spurring the growth of the Fintech ecosystem in New Zealand, there is strong potential gains in engaging with the already thriving Singapore Fintech ecosystem.”
New Zealand and Singapore are not only model free markets, but also have been key proponents of data privacy over the years, an area that requires a serious look, as we start to apply new emerging technologies such as AI. “There is an opportunity for these two forward-looking nations to take it a step further to build an actionable Data Privacy Corridor to streamline the Fintech collaboration between them,” Gupta added. “With New Zealand being an export economy and Singapore, a strong services economy, this would enable a much more seamless collaboration between these two countries.”
The collaboration does not end at cybersecurity and Fintech. As part of the partnership, a joint work programme is being negotiated, starting with two flagship collaborations – an advanced data science research platform to build New Zealand’s data science capability; and a food and nutrition cooperative science programme with a focus on ‘future foods’. Both countries have different areas of expertise, and collaborative measures such as these, give them an opportunity to share best practices that will prove mutually beneficial.
With understanding and acceptance of blockchain increasing, enterprises have started adopting blockchain to store digital records in a secure and auditable manner. In May 2018, we saw Microsoft’s blockchain workbench focused on integrating data and systems and deployment of contracts and blockchain networks. In October 2018, Microsoft Azure joined forces with Nasdaq to integrate blockchain technology into Nasdaq’s framework with an expectancy to speed-up transactions on the stock exchange.
Following these announcements, this month Microsoft unveiled its fully managed Azure Blockchain Service, a package designed to simplify the processes and eliminate the pain points of blockchain networks. Microsoft Azure blockchain service will provide the required infrastructure, connection to services to develop, run and take advantage of applications on its Cloud-based platform.
To leverage blockchain Microsoft and J.P. Morgan announced a partnership to accelerate the adoption of enterprise blockchain. Quorum, an Ethereum-based distributed ledger protocol developed by J.P. Morgan will be the first ledger available through Azure Blockchain Service, on the cloud.
Joining the bandwagon, Starbucks will use Azure and the Ethereum blockchain to track coffee from farm to the cup. In the same way, with a forward-thinking approach, Microsoft and GE Aviation collaborated to bring blockchain into aviation. GE Aviation has built a supply chain track-and-trace blockchain with the help of Microsoft Azure to monitor and collate data in relation to aircraft engine parts, life cycle, when to repair, this technology that the group has come up with is termed as ‘TRUEngine’.
Unfolding blockchain for “regular” businesses and SMEs
Blockchain technology, by its very nature leads itself to the digital transformation journey of an enterprise. Blockchain can address some of the pitfalls of digital transformation such as identity, security, and trust. From digital identity to tokenisation to using smart contracts to automate businesses, blockchain technology is swiftly establishing itself as a key enabler of the emerging digitised enterprise.
 |
Speaking on the subject, Ecosystm’s Principal Advisor, Amit Sharma thinks that “For Small and Mid-Size Enterprise (SMEs), blockchain can simplify and automate processes related to Trade Finance which would mean less paperwork and automation in supply chains and it also opens up a huge alternative finance channel to deal with their cash flow challenges.” |
Overall the blockchain network should facilitate the interworking between IT systems, financial systems and ledgers that are today primarily managed in silos and require heavy manual processes.
Are we already there?
“All disruptive technology has a ‘tipping point’ – the exact moment when it moves from early adopters to widespread acceptance. We are now approaching the tipping point for blockchain. Even though the development of blockchain for business is still in its early stages, business leaders have swiftly moved from understanding blockchain and its potential uses to running pilots,” says Sharma.
Blockchain has attracted attention across industries such as financial services, transportation and shipping, healthcare, energy and utilities, and supply chain management.
These share some common themes. Blockchain is a natural fit for use cases that are transactional but with a high degree of process complexity or volume. Blockchain will become the default technology wherever there is a need to ensure the integrity of data.
Blockchain Adoption by Organisations
Despite the flurry of activity and promising initial developments, blockchain faces a number of obstacles that will need to be overcome before companies choose to adopt it on a broader scale. Its decentralised network runs counter to the current business emphasis on centralising data or functions to support security efforts. Users and operators alike must shift their mindset to embrace and trust the system.“Among blockchain’s selling points is its security: high encryption and protocols. Since the general public largely doesn’t understand how the technology works, many still have concerns with data privacy and cyber security” says Sharma. “As with all new technology, when it comes to blockchain, business leaders should view any initial use cases as part of their enterprise risk management. Executives are attuned to the business and risk implications of blockchain. And in many cases, blockchain, like other technology platforms and systems, can be covered under existing insurance programs.”
Implementation by the large technology providers
“With the large technology providers such as Microsoft and AWS now offering BaaS (Blockchain-as-a-Service) over multiple frameworks supported by a ‘Pay as you use’ model, this technology is much more accessible. Pre-built integrations to the network and infrastructure services that are being offered by some of these players will significantly reduce the development time and cost for enterprise customers” says Sharma.
The next several years could see blockchain move from testbed to becoming an essential business tool, so staying abreast of the latest developments and how it is being used will be critical.
Internet of Things (IoT) is changing how companies do business, across industries. Using connected sensors, better data processing capabilities and automation, industries are looking to achieve workforce optimisation, improved customer experience, and cost savings in the short term. In the long-term organisations are looking for service and product innovation, as well as a competitive edge from their IoT investments.
In the global Ecosystm IoT study, participants revealed the IoT solutions that are part of their larger IoT deployment projects. Here are the top 5 solutions that industries are implementing, and how they are benefitting from them.
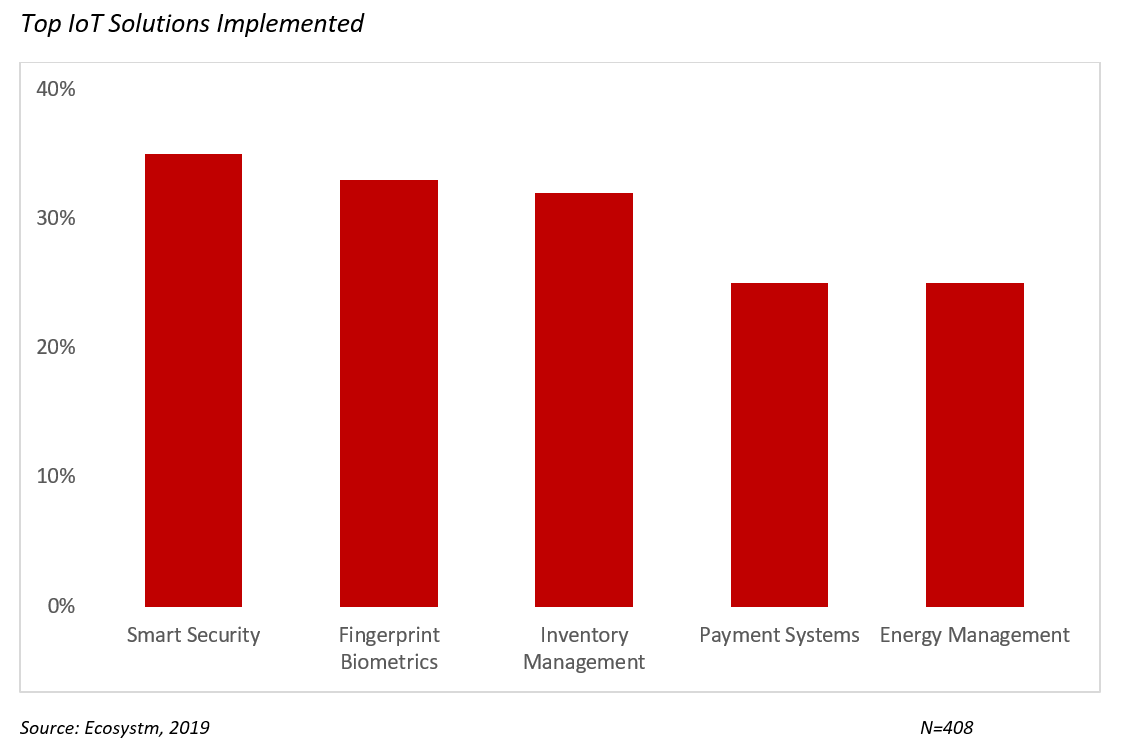
Smart Security
Smart Security is being adopted in several enterprises, especially in the Financial and Hospitality industries. Aside from improved safety, Smart Security solutions have the potential to deliver more personalised service and better customer experience (CX).
Maintaining security for the guests is one of the top concerns for hotels and smart video surveillance systems, motion detection, audio detection, and alert systems are helping hotels to identify possible threats and get early alerts on potential events.
Hotel chains Hilton and Marriott are leveraging Smart Security IoT solutions to create better travel and stay experiences for guests. They are working on creating enhanced security for their visitors by replacing card-based door keys. Simultaneously, smartphone applications connected with hotel sensors and devices are offering a seamless experience to guests with automated room settings such as HVAC, lighting, and blinds.
The Banking industry is incorporating Smart Security as well. Banking and financial institutions attract criminals for obvious reasons and to improve security, smart CCTV surveillance, wedge barriers, laser scanner detectors, light barriers, and quick folding gates are embedded with sensors and connected to safeguard against potential attacks. IoT-enabled network security measures to provide intelligent Perimeter Security is also seeing an uptake in the industry.
However, the proliferation of ubiquitous devices also leaves organisations vulnerable to data breaches. Digital and electronic devices incorporated into a hotel’s infrastructure can be exploited by hackers or may jeopardise the security of guests. The now-famous incident of the casino in the US that was hacked into through the IoT-enabled temperature control system in the fish tank is a case in point.
Fingerprint Biometrics
While Fingerprint Biometrics is often a part of a Smart Security solution, it is being used more often for asset management, as well as access control. This is fairly common in industries where multiple people fill a particular role, such as Manufacturing, Retail, and Healthcare. In hospitals, for example, multiple clinicians work on the same patient order entry system. Using fingerprint biometrics ensures that there is full accountability for care delivery at any given point, irrespective of the clinician.
Biometrics and its application are redefining the banking experience for rural and the unbanked population – in emerging countries especially – as one of the key authentication methods. Biometrics is helping in e-KYC, often used to open a bank account, on-site cash delivery by scanning fingerprints, opening a bank’s wallet with fingerprint authentication, fingerprint-based ATM kiosks and fingerprint mobile ID all connected through the IoT Solutions.
Governments use fingerprint biometrics to accurately authenticate the identity of travelers, implement biometric voting systems for fair and credible elections, develop fingerprint-based national identification cards and create a composite individual identity. But with this advantage, there could be associated challenges of managing personal databases in a safe and secure environment.
Inventory Management
Better supply chain visibility and management is considered one of the most common benefits of IoT deployments, and has use cases in several industries, including Transport & Logistics, and Primary industries. Inventory management became a lot easier and reliable, when IoT sensors and devices can do remote stock taking and track inventory movement.
IoT will enable more holistic inventory management, as asset tracking, asset management and eventually predictive maintenance, are incorporated within the IoT system. Supply chain requirements of Manufacturing organisations can vary vastly – a discrete manufacturing supply chain will vary from a FMCG supply chain. IoT sensors have made ‘track and trace’ more reliable, and easy to customise. eCommerce giant Amazon’s inventory management and warehousing system is a good example. To manage the large stock, the storage facilities employ pickers (robots) to pick items from and replenish stock on shelves which in turn improves receiving, pick-up, and shipping times. The inventory is scanned through barcodes which also helps in aggregating information from other warehouses for stock maintenance.
Several Retail organisations make full use of IoT for inventory management. G-Star Raw, for example, uses garment RFID tags to track inventory movements across the supply chain and store shelves. Being able to locate clothes on the basis of style, colour and size in the stores makes the order fulfillment reliable and more real-time.
Payment Systems
Several industries other than Financial Services, such as Hospitality, Services, Healthcare and Government are evaluating IoT-enabled payment systems such as mobile points of sale and NFC payments.
On most occasions, these are being promoted by financial institutions. As an example, MasterCard has created a Mastercard Engage platform with technology partners resulting in innovations which include contactless payments (with Coin), smart refrigerators that can re-order groceries (with Samsung) and IoT-connected key fobs (with General Motors). Capital One has made it possible for its customers to pay bills via Alexa, whereas Starling is experimenting with integration with Google Home to enable queries on payments and balances on the Google Home platform.
There are also several use cases that are not so obvious –Amazon Go offers a shopping experience where no check-out is required. Your Amazon account, wallet and phone are all inter-connected. When a consumer arrives at a store the application allows store entry, tracks the consumer through the shopping journey and requires no formal check-out at the end of the shopping trip.
However, IoT-enabled payment systems will have to evolve as industries become increasingly services based. There needs to be a focus on the business and not just technology – defining workflows with the right alerts that will automate bill generation and the payment process, irrespective of how complicated the service delivered is.
Energy Management
Resource shortage and the ever-increasing price of energy has forced organisations to identify innovative ways of conserving energy. A Smart energy management system can help to reduce the costs and energy consumption while still meeting energy needs. IoT is helping companies to achieve their energy goals, predict maintenance needs, and increase the reliability of energy assets. Smart energy solutions continuously analyse energy data to ensure dynamic performance which in turn manages energy requirements.
Take an example of a smart building management system where date from various sensors is collected and analysed, such as from HVAC, air-quality monitors, and other equipments, and lighting, heating, air ventilation, elevators, room equipment are remotely operated according to the building energy requirements at the moment. This technology helps make smart decisions and provides energy efficiency.
Capital Tower in Singapore, a 52-storey high building, is not alone in being energy efficient. It has a number of in-built smart energy solutions for energy and water efficiency. The building has motion detectors in elevators, smart car parking system, exterior structure glasses which help reduce energy consumption, and water conservation through condensation of air conditioning units. The building has devices to monitor oxygen and carbon dioxide levels ensuring optimal air quality which results in significant energy savings while delivering comfort for tenants.
As is clear from the solutions that are being currently deployed, IoT adoption is at its nascency. As IoT deployments mature, there will be more industry-specific uses of IoT, and a shift of focus from asset management to people management (including customers).
What IoT solutions do you use/ intend to use in your organisation? Let us know in your comments section below.
The NCSC’s first ‘UK cyber survey’ published alongside global password risk list. The UK government’s cybersecurity organisation National Cyber Security Centre (NCSC) provides cybersecurity support and guidance to the private and public sectors.
The survey identified exploitable gaps in personal level security management. The study was carried out between November 2018 and January 2019 and revealed that 89% of the respondents used the Internet and only 15% acknowledged a greater understanding of personal security measures.
The NCSC also published an analysis of the 100,000 most commonly used passwords that have been accessed by third parties in global cyber breaches. The analysis shows that less than half of the respondents do are not concerned about the strength of passwords for their emails and online accounts. Some examples of commonly used passwords used by people rely on their own names, Premier League football teams, musicians and fictional characters for inspiration.
This general lack of understanding of the cyber world can be harmful to individuals but can be devastating to organisations. A chain is no stronger than its weakest link, and insecure passwords may pose a serious security risk to an organisation. “We rely on passwords in all facets of our online world, so this presents a massive risk to anyone taking short-cuts. Unfortunately, if organisations are not prepared, and allow the use of similarly insecure passwords, the flow on effect of a breach can escalate rapidly” says Alex Woerndle, Principal Analyst Cybersecurity, Ecosystm “The passwords in the above list are very weak. Even without the knowledge provided in the list, a hacker would be able to crack these passwords in seconds with the right tools. Even password complexity cannot always protect an organisation. What about a user that re-uses a complex password repeatedly, and that password is part of a breach? That puts all of the organisation’s logins at risk”.
There are some additional steps that system administrators and IT professionals need to consider when it comes to securing passwords and managing logins.
The global Ecosytsm Cybersecurity & Data Privacy study found the most common controls organisations implement to manage data access.
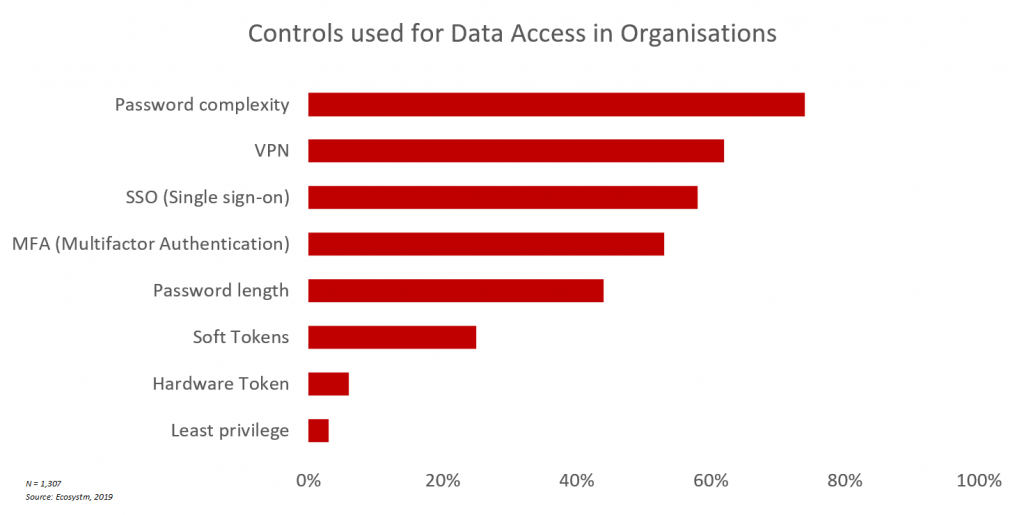
“The main step being used currently is ensuring MFA is enabled wherever possible. While not a perfect solution, it provides a circuit breaker for the most common types of attacks that would get anyone using insecure passwords into trouble” says Woerndle.
The NCSC hopes to reduce the risk of further breaches by building awareness of how attackers use easy-to-guess passwords, or those obtained from breaches and help guide developers and system administrators to protect their users. NCSC has framed guidelines covering multiple aspects of managing and maintaining security on its website.
Ultimately this problem will not go away until we find a genuine replacement for passwords. The pure scale of growth in the number of systems and applications that all users, both at a personal and on a professional level, have access to, makes password management complex and frustrating. While focusing on how to strengthen your passwords and other easy steps to avoid a cyber attack, may be a good start, it will not be enough, as long as systems and applications are dependent on passwords for better security.
The Changing Shape of Asia’s Cybersecurity Landscape
The latest in our Leaders BreakFirst series. Following the launch of our Cybersecurity and Data Privacy study, Ecosystm is delighted to share the insights from almost 7000 deployments globally.Featuring two of Ecosystm’s cybersecurity and data privacy experts on one stage- Claus Mortensen and Carl Woerndle, this session will highlight the findings from our Cybersecurity & Privacy research.
In the last few weeks, there have been announcements in Canada and Denmark on nationwide IoT networks launches. Moving away from pilot projects, test cases, implementations across large factories and campuses or even citywide networks to drive smart city initiatives; these countrywide IoT networks give organisations access to lower cost means to implement large, more integrated, IoT projects.
Sigfox Canada announced the launch of Canada’s first coast to coast low-bandwidth IoT network which is the nation’s first IoT network on such a scale. The network leverages low-power wide area network (LPWAN) technology offering a capacity to support millions of IoT sensors. The solution is anticipated to provide efficient and cost-effective connectivity for businesses looking to adopt IoT technology.
Similarly, Teracom, a Denmark-based telecom operator in partnership with Loriot, (an IoT infrastructure provider) announced an IoT LoRaWAN – Long Range Wide Area Network network in Denmark. We have previously seen the Netherlands implementing a nationwide long range (LoRa) network for IoT and Singtel’s commercially available narrowband Internet of Things (NB-IoT) network in Singapore.
“There is no doubt that services like LoRaWAN will help boost early adoption of IoT services and at this stage, there is a segment of the market which is a good fit. However, the longevity of LoRaWan is less certain. Compared to LoRaWAN, NB-IOT has arguably been too late to the game and it may fail in the short term but may very well win in the long term.” says Copenhagen based Ecosystm Principal Analyst, Claus Mortensen.
Efforts are being made by both the Sigfox and Teracom to enhance the network coverage and quality in the countries. A lot of the focus on IoT in Denmark has been bundled into the future deployment of 5G. However, most IoT applications do not need high bandwidth.
“The issues with large countries such as Canada, Australia, and the US is how do you economically cover large geographic area with a very varied population density? In contrast, smaller countries like Denmark can have a mesh thrown over them very easily” says Ecosystm Executive Analyst, Vernon Turner.
With 5G though, the telecom providers appear to be in a better position as they understand that 5G will be driven by the enterprise segment in the short to medium term and they have been actively involved in developing use cases from the get-go which also includes a focus on IoT services.
IoT offers a plethora of opportunities to companies looking to adopt or expand the country-wide networks. Both mature countries and emerging economies are at dissimilar life-cycles in their degree of IoT technology adoption but we expect to witness more technology sharing and network concatenation in the near-future.
AI is powering products, processes, strategies and customer experience in the Banking industry.
The banking industry is all geared up to embrace Artificial Intelligence (AI), to address its business requirements. In general, banks are struggling to implement smart services within their compliance framework, and have an incomplete view of their customer needs from their legacy systems. However, the industry continues to be reliant on legacy systems, largely because of the involvement of too many complex platforms, technologies, and systems which make migration or integration cumbersome.
Meanwhile, modern Digital Banks are aligning their services to customer needs by embedding AI and machine learning within their existing systems. The banking industry’s experimentation with AI is opening new opportunities for improving customer experience (CX).
“We are not too far away from a day where traditional enterprise applications are no longer relevant. The purpose of those traditional systems was to simplify, codify, and automate business and customer processes. But in the mid-term future, we will have a time where the entire process is intelligent – where the system/application creates the best business process for the customer on the fly”, says Tim Sheedy, Principal Advisor, Ecosystm.
Elevating CX and Security
Banks are being transformed through AI adoption, especially in areas such as process automation, cyber security (especially in threat analysis and intelligence, and fraud/transaction security) and better information sharing systems for both their corporate and retail customers.
Business Solutions being Addressed by AI in Banking
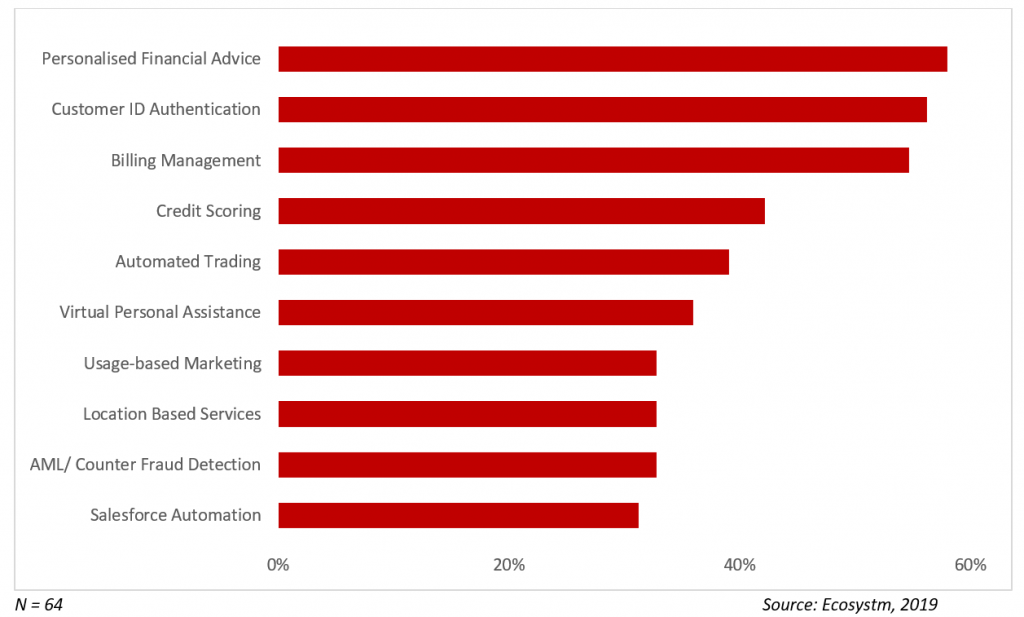
Customer Experience
Customer Service is one of the core banking applications. Adoption of technologies such as virtual assistants and natural language processing (NLP) techniques is redefining CX in the banking industry.
“With emerging technologies setting a new bar for personalisation and value-add, banks looking to stay ahead of the curve simply cannot afford to ignore them,” says Jannat Maqbool, Principal Advisor, Ecosystm.
Personalised financial advice is another area where banks are taking advantage of AI applications. While it might be a perception that AI will reduce the human touch when it comes to CX, in reality, it provides more accurate and timely assistance. For instance, Bank of America has built an AI virtual assistant, “Erica” which actively assists 25 million clients on its mobile platform. Erica searches for past transactions and informs customers on their credit scores and connects with them to provide analytics and information on their account.
Marketing Automation
As profit margins decrease in the Banking sector, and Fintech technologies become more mainstream, banks need to ramp up their marketing initiatives, to remain competitive. AI is helping banks to optimise their marketing dollars. Machine learning algorithms can analyse customers’ entire banking journey involving interactions, transactions, location history, and usage patterns to develop insights and make marketing decisions with unprecedented accuracy. Decisions on a range of marketing initiatives across product improvement, new products and services offerings, and targeted marketing keeping in view customers’ financial goals will be automated. This will impact the profit margin as sales cycles shorten, and customers banking journeys become more satisfying.
Process Automation
There are certain functions in banks which require a lot of manual labour such as billing, generation of reports, account opening operations, KYC, etc. AI is transforming the banking industry with data-driven processes and decision making to automate tasks such as billings, credit scoring, compliance reports and so on. This not only reduces the dependence on tedious manual processes but also creates mechanisms to reduce errors. These errors not only make the organisation less efficient but also has financial ramifications. UBS, as an example, has introduced robots to its workforce, mainly at the back offices, designed to execute more manual and repetitive tasks. This essentially means meeting the right tasks with more speed and accuracy.
Fraud Management
AI improves with data and learns behavioural patterns. Banks are utilising this data or claims management and fraud detection. The AI platform evaluates on certain parameters such as when and how a customer typically accesses services and manage their money – more importantly, how they do not. They are designed to flag transactions with missing information and can alert the bank staff to irregular transactions and suspicious activities to prevent fraud. Increasingly this is evolving a chain of an automated process, without the involvement of banking staff or customer complaints.
Banks have a difficult job delivering better service while remaining compliant, and AI-driven AML and KYC initiatives, helps prevent fraud, and flag suspicious activities such as money laundering.
Market Trends
Current Focus on AI – The banking industry’s focus on customer service and automating manual processes is reflected in the top AI solutions that they are currently adopting. Chatbots and virtual assistants are being improved through natural language generation (NLG) and speech analytics capabilities. Process automation through RPA is being integrated into the organisations’ digital journeys due to its relative ease of deployment and measurable ROI.
Current & Planned Adoption of AI Solutions in Banking
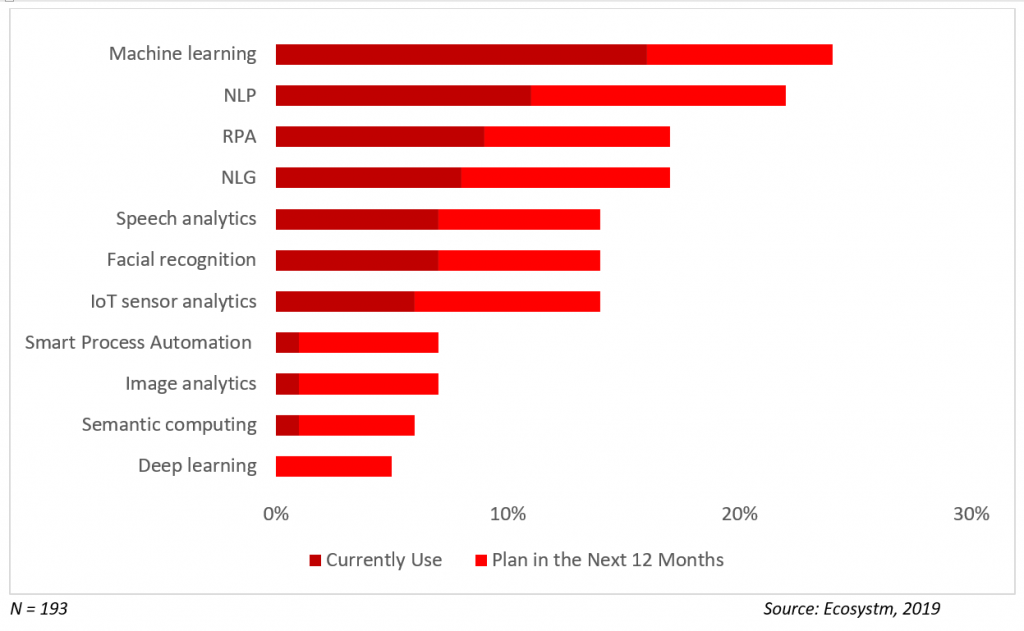
Future Focus on AI – Banks will continue to focus on CX and strengthening the capabilities of their customer service team through AI. Niche solutions such as facial recognition will also improve their front-end operations, especially in customer identity authentication. Banks will also go beyond customer management to asset management, with AI-enabled IoT systems.
What’s Next?
AI is fast evolving and there are some excellent opportunities for banks to explore on what AI has to offer. Banks are working on feeding data into AI systems with advanced algorithms to better understand their customers and improve their services. Banks should focus on getting quality inputs on inquiries, interactions, transactions or another way that can collect insights.
Consumers are looking for operations and systems that are simple to operate and directed towards them. The greatest potential for AI in banking is to deliver personalised and automated services to consumers in a cost-effective and efficient way.
AI is allowing banks to do quicker operations at much lower cost, what remains to be seen is how banks further leverage AI to extend its products and services offerings.