AI has become a business necessity today, catalysing innovation, efficiency, and growth by transforming extensive data into actionable insights, automating tasks, improving decision-making, boosting productivity, and enabling the creation of new products and services.
Generative AI stole the limelight in 2023 given its remarkable advancements and potential to automate various cognitive processes. However, now the real opportunity lies in leveraging this increased focus and attention to shine the AI lens on all business processes and capabilities. As organisations grasp the potential for productivity enhancements, accelerated operations, improved customer outcomes, and enhanced business performance, investment in AI capabilities is expected to surge.
In this eBook, Ecosystm VP Research Tim Sheedy and Vinod Bijlani and Aman Deep from HPE APAC share their insights on why it is crucial to establish tailored AI capabilities within the organisation.

Trust in the Banking, Financial Services, and Insurance (BFSI) industry is critical – and this amplifies the value of stolen data and fuels the motivation of malicious actors. Ransomware attacks continue to escalate, underscoring the need for fortified backup, encryption, and intrusion prevention systems. Similarly, phishing schemes have become increasingly sophisticated, placing a burden on BFSI cyber teams to educate employees, inform customers, deploy multifactor authentication, and implement fraud detection systems. While BFSI organisations work to fortify their defences, intruders continually find new avenues for profit – cyber protection is a high-stakes game of technological cat and mouse!
Some of these challenges inherent to the industry include the rise of cryptojacking – the unauthorised use of a BFSI company’s extensive computational resources for cryptocurrency mining.
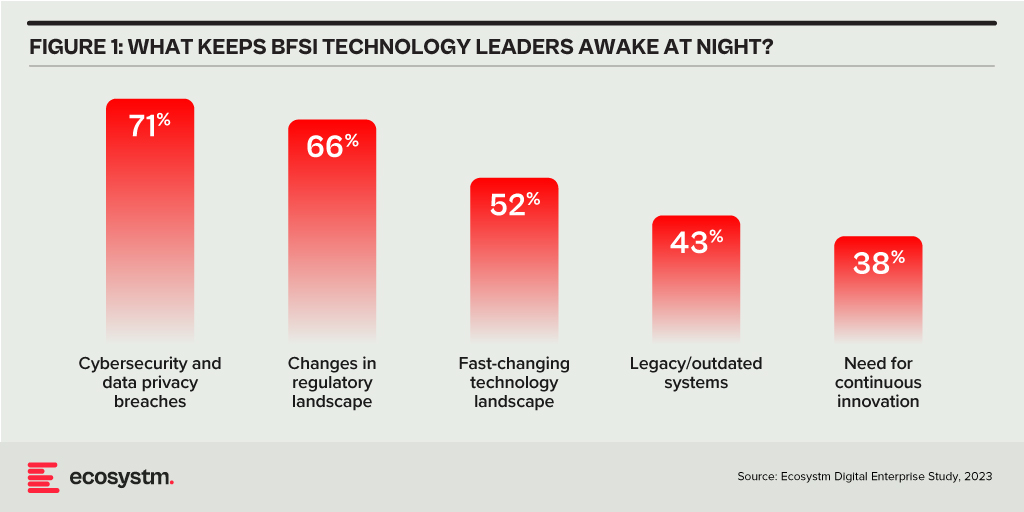
Building Trust Amidst Expanding Threat Landscape
BFSI organisations face increasing complexity in their IT landscapes. Amidst initiatives like robo-advisory, point-of-sale lending, and personalised engagements – often facilitated by cloud-based fintech providers – they encounter new intricacies. As guest access extends to bank branches and IoT devices proliferate in public settings, vulnerabilities can emerge unexpectedly. Threats may arise from diverse origins, including misconfigured ATMs, unattended security cameras, or even asset trackers. Ensuring security and maintaining customer trust requires BFSI organisations to deploy automated and intelligent security systems to respond to emerging new threats.
Ecosystm research finds that nearly 70% of BFSI organisations have the intention of adopting AI and automation for security operations, over the next two years. But the reality is that adoption is still fairly nascent. Their top cyber focus areas remain data security, risk and compliance management, and application security.
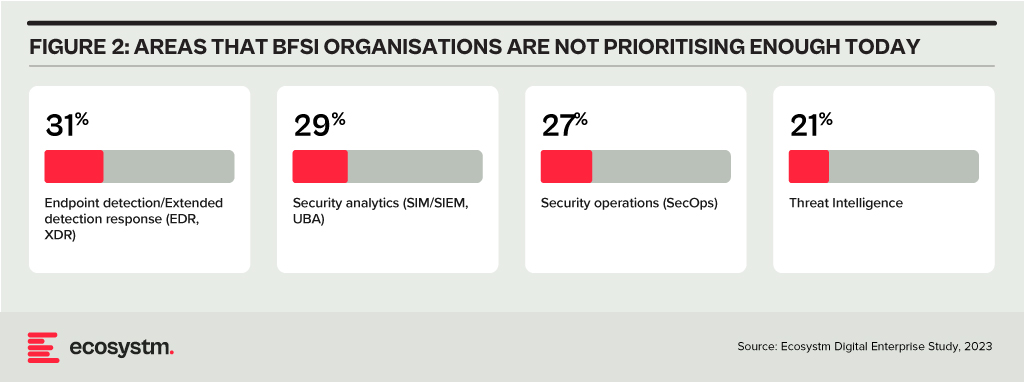
Addressing Alert Fatigue and Control Challenges
According to Ecosystm research, 50% of BFSI organisations use more than 50 security tools to secure their infrastructure – and these are only the known tools. Cyber leaders are not only challenged with finding, assessing, and deploying the right tools, they are also challenged with managing them. Management challenges include a lack of centralised control across assets and applications and handling a high volume of security events and false positives.
Software updates and patches within the IT environment are crucial for security operations to identify and address potential vulnerabilities. Management of the IT environment should be paired with greater automation – event correlation, patching, and access management can all be improved through reduced manual processes.
Security operations teams must contend with the thousands of alerts that they receive each day. As a result, security analysts suffer from alert fatigue and struggle to recognise critical issues and novel threats. There is an urgency to deploy solutions that can help to reduce noise. For many organisations, an AI-augmented security team could de-prioritise 90% of alerts and focus on genuine risks.
Taken a step further, tools like AIOps can not only prioritise alerts but also respond to them. Directing issues to the appropriate people, recommending actions that can be taken by operators directly in a collaboration tool, and rules-based workflows performed automatically are already possible. Additionally, by evaluating past failures and successes, AIOps can learn over time which events are likely to become critical and how to respond to them. This brings us closer to the dream of NoOps, where security operations are completely automated.
Threat Intelligence and Visibility for a Proactive Cyber Approach
New forms of ransomware, phishing schemes, and unidentified vulnerabilities in cloud are emerging to exploit the growing attack surface of financial services organisations. Security operations teams in the BFSI sector spend most of their resources dealing with incoming alerts, leaving them with little time to proactively investigate new threats. It is evident that organisations require a partner that has the scale to maintain a data lake of threats identified by a broad range of customers even within the same industry. For greater predictive capabilities, threat intelligence should be based on research carried out on the dark web to improve situational awareness. These insights can help security operations teams to prepare for future attacks. Regular reporting to keep CIOs and CISOs informed of the changing threat landscape can also ease the mind of executives.
To ensure services can be delivered securely, BFSI organisations require additional visibility of traffic on their networks. The ability to not only inspect traffic as it passes through the firewall but to see activity within the network is critical in these increasingly complex environments. Network traffic anomaly detection uses machine learning to recognise typical traffic patterns and generates alerts for abnormal activity, such as privilege escalation or container escape. The growing acceptance of BYOD has also made device visibility more complex. By employing AI and adopting a zero-trust approach, devices can be profiled and granted appropriate access automatically. Network operators gain visibility of unknown devices and can easily enforce policies on a segmented network.
Intelligent Cyber Strategies
Here is what BFSI CISOs should prioritise to build a cyber resilient organisation.
Automation. The volume of incoming threats has grown beyond the capability of human operators to investigate manually. Increase the level of automation in your SOC to minimise the routine burden on the security operations team and allow them to focus on high-risk threats.
Cyberattack simulation exercises. Many security teams are too busy dealing with day-to-day operations to perform simulation exercises. However, they are a vital component of response planning. Organisation-wide exercises – that include security, IT operations, and communications teams – should be conducted regularly.
An AIOps topology map. Identify where you have reliable data sources that could be analysed by AIOps. Then select a domain by assessing the present level of observability and automation, IT skills gap, frequency of threats, and business criticality. As you add additional domains and the system learns, the value you realise from AIOps will grow.
A trusted intelligence partner. Extend your security operations team by working with a partner that can provide threat intelligence unattainable to most individual organisations. Threat intelligence providers can pool insights gathered from a diversity of client engagements and dedicated researchers. By leveraging the experience of a partner, BFSI organisations can better plan for how they will respond to inevitable breaches.
Conclusion
An effective cybersecurity strategy demands a comprehensive approach that incorporates technology, education, and policies while nurturing a culture of security awareness throughout the organisation. CISOs face the daunting task of safeguarding their organisations against relentless cyber intrusion attempts by cybercriminals, who often leverage cutting-edge automated intrusion technologies.
To maintain an advantage over these threats, cybersecurity teams must have access to continuous threat intelligence; automation will be essential in addressing the shortage of security expertise and managing the overwhelming volume and frequency of security events. Collaborating with a specialised partner possessing both scale and experience is often the answer for organisations that want to augment their cybersecurity teams with intelligent, automated agents capable of swiftly

The Banking, Financial Services, and Insurance (BFSI) industry, known for its cautious stance on technology, is swiftly undergoing a transformational modernisation journey. Areas such as digital customer experiences, automated fraud detection, and real-time risk assessment are all part of a technology-led roadmap. This shift is transforming the cybersecurity stance of BFSI organisations, which have conventionally favoured centralising everything within a data centre behind a firewall.
Ecosystm research finds that 75% of BFSI technology leaders believe that a data breach is inevitable. This requires taking a new cyber approach to detect threats early, reduce the impact of an attack, and avoid lateral movement across the network.
BFSI organisations will boost investments in two main areas over the next year: updating infrastructure and software, and exploring innovative domains like digital workplaces and automation. Cybersecurity investments are crucial in both of these areas.
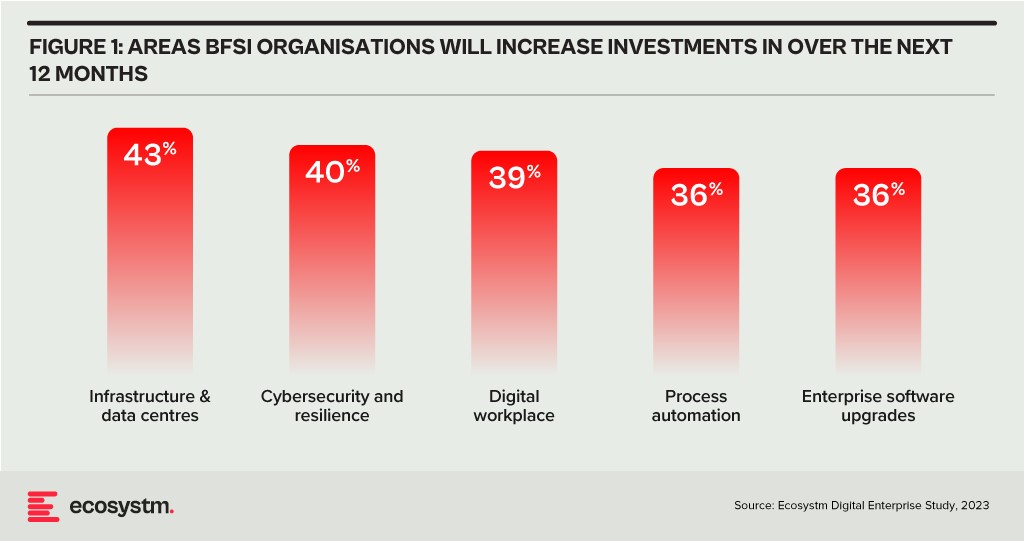
As a regulated industry, breaches come with significant cost implications, underscoring the need to prioritise cybersecurity. BFSI cybersecurity and risk teams need to constantly reassess their strategies for safeguarding data and fulfilling compliance obligations, as they explore ways to facilitate new services for customers, partners, and employees.
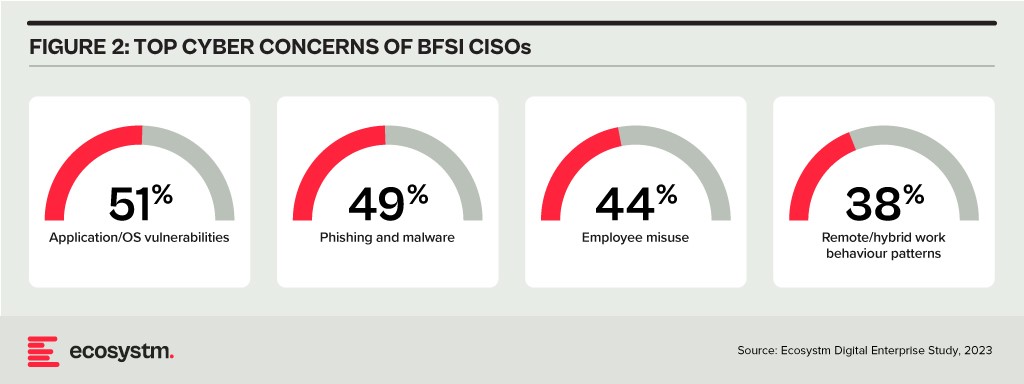
The primary concerns of BFSI CISOs can be categorised into two distinct groups:
- Expanding Technology Use. This includes the proliferation of applications and devices, as well as data access beyond the network perimeter.
- Employee-Related Vulnerabilities. This involves responses to phishing and malware attempts, as well as intentional and unintentional misuse of technology.
Vulnerabilities Arising from Employee Actions
Security vulnerabilities arising from employee actions and unawareness represent a significant and ongoing concern for businesses of all sizes and industries – the risks are just much bigger for BFSI. These vulnerabilities can lead to data breaches, financial losses, damage to reputation, and legal ramifications. A multi-pronged approach is needed that combines technology, training, policies, and a culture of security consciousness.
Training and Culture. BFSI organisations prioritise comprehensive training and awareness programs, educating employees about common threats like phishing and best practices for safeguarding sensitive data. While these programs are often ongoing and adaptable to new threats, they can sometimes become mere compliance checklists, raising questions about their true effectiveness. Conducting simulated phishing attacks and security quizzes to assess employee awareness and identify areas where further training is required, can be effective.
To truly educate employees on risks, it’s essential to move beyond compliance and build a cybersecurity culture throughout the organisation. This can involve setting organisation-wide security KPIs that cascade from the CEO down to every employee, promoting accountability and transparency. Creating an environment where employees feel comfortable reporting security concerns is critical for early threat detection and mitigation.
Policies. Clear security policies and enforcement are essential for ensuring that employees understand their roles within the broader security framework, including responsibilities on strong password use, secure data handling, and prompt incident reporting. Implementing the principle of least privilege, which restricts access based on specific roles, mitigates potential harm from insider threats and inadvertent data exposure. Policies should evolve through routine security audits, including technical assessments and evaluations of employee protocol adherence, which will help organisations with a swifter identification of vulnerabilities and to take the necessary corrective actions.
However, despite the best efforts, breaches do happen – and this is where a well-defined incident response plan, that is regularly tested and updated, is crucial to minimise the damage. This requires every employee to know their roles and responsibilities during a security incident.
Tech Expansion Leading to Cyber Complexity
Cloud. Initially hesitant to transition essential workloads to the cloud, the BFSI industry has experienced a shift in perspective due to the rise of inventive SaaS-based Fintech tools and hybrid cloud solutions, that have created new impetus for change. This new distributed architecture requires a fresh look at cyber measures. Secure Access Service Edge (SASE) providers are integrating a range of cloud-delivered safeguards, such as FWaaS, CASB, and ZTNA with SD-WAN to ensure organisations can securely access the cloud without compromising on performance.
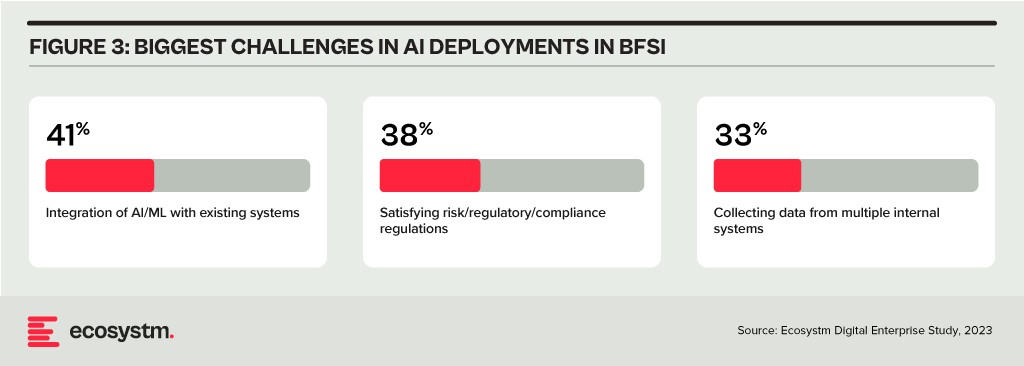
Data & AI. Data holds paramount importance in the BFSI industry for informed decision-making, personalised customer experiences, risk assessment, fraud prevention, and regulatory compliance. AI applications are being used to tailor products and services, optimise operational efficiency, and stay competitive in an evolving market. As part of their technology modernisation efforts, 47% of BFSI institutions are refining their data and AI strategies. They also acknowledge the challenges associated – and satisfying risk, regulatory, and compliance requirements is one of the biggest challenges facing BFSI organisations in the AI deployments.
The rush to experiment with Generative AI and foundation models to assist customers and employees is only heightening these concerns. There is an urgent need for policies around the use of these emerging technologies. Initiatives such as the Monetary Authority of Singapore’s Veritas that aim to enable financial institutions to evaluate their AI and data analytics solutions against the principles of fairness, ethics, accountability, and transparency (FEAT) are expected to provide the much-needed guidance to the industry.
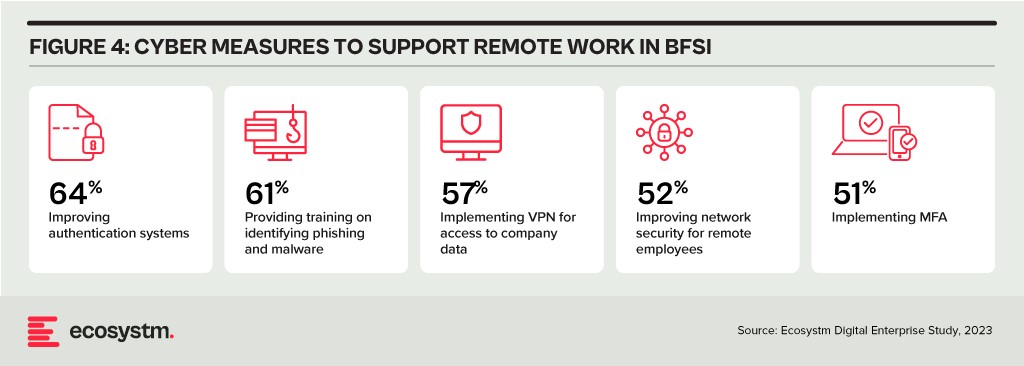
Digital Workplace. As with other industries with a high percentage of knowledge workers, BFSI organisations are grappling with granting remote access to staff. Cloud-based collaboration and Fintech tools, BYOD policies, and sensitive data traversing home networks are all creating new challenges for cyber teams. Modern approaches, such as zero trust network access, privilege management, and network segmentation are necessary to ensure workers can seamlessly but securely perform their roles remotely.
Looking Beyond Technology: Evaluating the Adequacy of Compliance-Centric Cyber Strategies
The BFSI industry stands among the most rigorously regulated industries, with scrutiny intensifying following every collapse or notable breach. Cyber and data protection teams shoulder the responsibility of understanding the implications of and adhering to emerging data protection regulations in areas such as GDPR, PCI-DSS, SOC 2, and PSD2. Automating compliance procedures emerges as a compelling solution to streamline processes, mitigate risks, and curtail expenses. Technologies such as robotic process automation (RPA), low-code development, and continuous compliance monitoring are gaining prominence.
The adoption of AI to enhance security is still emerging but will accelerate rapidly. Ecosystm research shows that within the next two years, nearly 70% of BFSI organisations will have invested in SecOps. AI can help Security Operations Centres (SOCs) prioritise alerts and respond to threats faster than could be performed manually. Additionally, the expanding variety of network endpoints, including customer devices, ATMs, and tools used by frontline employees, can embrace AI-enhanced protection without introducing additional onboarding friction.
However, there is a need for BFSI organisations to look beyond compliance checklists to a more holistic cyber approach that can prioritise cyber measures continually based on the risk to the organisations. And this is one of the biggest challenges that BFSI CISOs face. Ecosystm research finds that 72% of cyber and technology leaders in the industry feel that there is limited understanding of cyber risk and governance in their organisations.
In fact, BFSI organisations must look at the interconnectedness of an intelligence-led and risk-based strategy. Thorough risk assessments let organisations prioritise vulnerability mitigation effectively. This targeted approach optimises security initiatives by focusing on high-risk areas, reducing security debt. To adapt to evolving threats, intelligence should inform risk assessment. Intelligence-led strategies empower cybersecurity leaders with real-time threat insights for proactive measures, actively tackling emerging threats and vulnerabilities – and definitely moving beyond compliance-focused strategies.

A lot gets written about cybersecurity – and organisations spend a lot on it! Ecosystm research finds that 63% of organisations across Asia Pacific are planning to increase their cyber budget for the next year. As budgets continue to rise, the threat landscape continues to get more complex and difficult to navigate. Despite increasing spend, 69% of organisations believe a breach is inevitable. And breaches can be EXPENSIVE! Medibank, in Australia, was breached in (or around) October, 2022. The cost of the breach is expected to reach around USD 52 million when everything is done and dusted – and this does not include the impacts of any potential findings or outcomes from regulatory investigations or litigation.
Recovering Strong
While cybersecurity is still crucially important, the ability to recover from breaches quickly and cost-effectively is also imperative. How you recover from a breach will ultimately determine your organisation’s long-term viability and success. The capabilities needed to recover quickly include:
- A well-documented and practices incident response plan. The plan should outline the roles and responsibilities of all team members, communication protocols, and steps to be taken in the event of a breach.
- Backup and Disaster Recovery (DR) solutions. Regular backups of critical data and systems are essential to quickly recover from a breach. Backup solutions should include offsite or cloud-based options that are isolated from the main network. DR solutions ensure that critical systems can be quickly restored and made operational after a breach.
- Cybersecurity awareness training. Investing in regular training for all employees is crucial to ensure they are aware of the latest threats and know how to respond in the event of a breach.
- Automated response tools. Automation can help speed up the response time during a breach by automatically blocking malicious IPs, quarantining infected devices, or taking other predefined actions based on the nature of the attack.
- Threat intelligence. This can help organisations stay ahead of the latest threats and vulnerabilities and frame quicker responses if a breach occurs.
Backup and Disaster Recovery is Evolving
Most organisations already have backup and disaster recovery capabilities in place – but too often they are older systems, designed more as a “just in case” versus a “will keep us in business” capability. Backup and DR systems are evolving and improving – and with the increased likelihood of a breach, it is a good time to consider what a modern Backup and DR system can provide to your organisation. Here are some of the key trends and considerations that technology leaders should be aware of:
- Cloud-based solutions. More organisations are moving towards cloud-based backup and DR solutions. Cloud solutions offer several advantages, including scalability, cost-effectiveness, and the ability to access data and systems from anywhere. However, technology leaders need to consider data security, compliance requirements, and the reliability of the cloud service provider.
- Hybrid options. As hybrid cloud becomes the norm for most organisations, hybrid solutions backup and DR that combine on-premises and cloud-based backups are becoming more popular. This approach provides the best of both worlds – the security and control of on-premises backups with the scalability and flexibility of the cloud.
- Increased use of automation. Automation is becoming more prevalent in backup and DR solutions. Automation helps reduce the time it takes to backup data, restore systems, and test DR plans. It also minimises the risk of human error. Technology leaders should look for solutions that offer automation capabilities while also allowing for manual intervention when necessary.
- Cybersecurity integration. With the rise of cyberattacks, especially ransomware, it is crucial that backup and DR solutions are integrated with an organisation’s cybersecurity strategy. Backup data should be encrypted and isolated from the main network to prevent attackers from accessing or corrupting it. Regular testing of backup and DR plans should also include scenarios where a cyberattack, such as ransomware, is involved.
- More frequent backups. Data is becoming more critical to business operations, so there is a trend towards more frequent backups, even continuous backups, to minimise data loss in the event of a disaster. Technology leaders need to balance the need for frequent backups with the cost and complexity involved.
- Super-fast data recovery. Some data recovery platforms can recover data FAST – in as little as 6 seconds. The ability to recover data faster than the bad actors can delete it makes organisations less vulnerable and buys more time to plug the gaps that the attackers are exploiting to gain access to data and systems.
- Monitoring and analytics. Modern backup and DR solutions offer advanced monitoring and analytics capabilities. This allows organisations to track the performance of their backups, identify potential issues before they become critical, and optimise their backup and DR processes. Technology leaders should look for solutions that offer comprehensive monitoring and analytics capabilities.
- Compliance considerations. With the increasing focus on data privacy and protection, organisations need to ensure that backup and DR solutions are compliant with relevant regulations, often dictated at the industry level in each geography. Technology leaders should work with their legal and compliance teams to ensure that their backup and DR solutions meet all necessary requirements.
The sooner you evolve and modernise your backup and disaster recovery capabilities, the more breathing room your cybersecurity team has, to improve the ability to repel threats. New security architectures and postures – such as Zero Trust and SASE are emerging as better ways to build your cybersecurity capabilities – but they won’t happen overnight and require significant investment, training, and business change to implement.

Organisations in Australia and New Zealand (ANZ) are focusing their digital transformation efforts on continued innovation in the experiences they deliver to their customers and employees.
Innovation has been at the core of organisations’ survival strategies – now it will be the means to gain competitive advantage and is getting prioritised over resiliency, business continuity and compliance.
Here are 5 insights on where ANZ organisations are headed in the tech priorities and investments, based on the findings of the Ecosystm Digital Enterprise Study, 2022.
- Tech Teams in ANZ are restructuring after a two-year struggle and as they face skills shortage.
- Tech investments are focusing on experience and digital workplace and customer experience technologies are seeing continued growth.
- Hybrid cloud investments are focused on augmenting existing infrastructure – whether public or on-prem
- Sales & Marketing are leveraging data & AI solutions the most; IT Ops and SecOps will see un uptick in 2023
- Cybersecurity practices are not evolving fast enough with only 9% of organisations having implemented Zero Trust
More insights into the ANZ tech market below.
Click here to download The Future of the Digital Enterprise – Australia & New Zealand as a PDF

While Vodafone remains one of the leading global telecommunications providers, they face the need to transform their services and reach out to a wider audience. The customer base of a typical telecom provider is shifting, and they can no longer afford to just focus on consumers and need to include enterprises in their go-to-market strategy. Beyond the usual offerings of connectivity and mobile plans, Vodafone Business has solutions for Unified Communications, IoT and Cloud, to help grow their enterprise customer base. Ecosystm Principal Advisor, Tim Sheedy says, “Vodafone is one of the most successful telecom providers in the business space. Vodafone Business already represents around 30% of the Vodafone Group revenue, and unlike most in the telecommunications sector, they are showing growth (albeit moderate!).”
The Role of Telecom Providers in the Cybersecurity Market
An area where enterprises continue to need guidance and support is cybersecurity. The results of the UK Government’s Cyber Security Breaches Survey 2019 found that 32% of UK businesses had experienced a cyber-attack in the previous 12 months. More than a third of UK organisations have made changes in their cyber policies because of the GDPR – a majority focusing on policies first. It is not surprising therefore that Vodafone should identify cybersecurity as the next area of focus for their enterprise offerings.
Sheedy says, ”Cybersecurity services are one of the fastest-growing areas in technology. But because of this, it is a also a crowded market with everyone – from the big telecom providers, IT services providers, big audit firms, mid-sized technology providers down to the smaller cybersecurity experts – playing for this growing spend. It can, however, be argued that telecom providers have some of the deepest experience in cybersecurity and managing the risks – their networks are probably the most targeted by hackers and malicious actors. Telecom providers have massive teams just to stop threats from one or two countries. With all the work they do to protect their own network, they should have the skills to help protect the networks and assets of their clients.”
Ecosystm Principal Advisor, Alex Woerndle concurs, “Telecom providers are perfectly positioned to transition into managed security service providers (MSSPs). They already have the experience in providing a range of managed services, the ability to scale to support clients and some ready-made expertise internally in their in-house cybersecurity capabilities.”
Vodafone’s Foray into Cybersecurity
Vodafone Cyber Enhanced focuses on selected cybersecurity areas – threat analysis and intelligence, managed firewall and managed security services. The global Ecosystm Cybersecurity study finds that the solutions that organisations will invest in most in 2020 are Security Operations (SecOps) & Incident Response (by a third of global organisations) and Threat Analysis & Intelligence (by 20% of global organisations).
Commenting on the areas Vodafone is focusing on, Woerndle says, “Threat analysis and intelligence is where a lot of established SecOps providers and MSSPs are really focusing now. Previously it was simply a matter of monitoring alerts and reporting. Businesses and in-house security teams are now seeking more proactive assistance in searching for threats, before they become attacks. The challenge they face is catching up – effectively jumping from just being another SecOps centre (SOC) monitoring and reporting alerts, to matching the more mature SOCs with proactive threat intelligence to help clients mitigate before an attack is launched. This takes time, as it needs maturity of the SOC and the team, and also data, which established providers have accrued plenty of, over an extended period. While a managed firewall is not really a new service, it makes some sense to couple it with other managed security services to deliver a broader program. Vodafone is absolutely targeting the areas that businesses are looking into presently.”
Woerndle adds, “MSSPs will be crucial to the security sector moving forward. There has been a rapid growth of vendor solutions creating a very confusing market for tech buyers. This is coupled with a tight labour market for skilled people who can manage the tools. It is not surprising , therefore, that 86% of organisations across the world will look to engage with an MSSP when deploying a cybersecurity solution, according to Ecosystm research.”
Sheedy sees an opportunity for Vodafone to go global with their cybersecurity capabilities. “If Vodafone can compete with the bigger players (and perhaps partner with or complement the offerings of the smaller ones), then they should find a significant opportunity, especially within their larger clients – particularly as they move into the software-defined networking space. However, given the confusion around cybersecurity, they should expand their focus beyond larger enterprises to businesses over about 100 employees. As one of the largest global telecom providers, with one of the largest networks, they can be an important player in the cybersecurity space – growing the spend in their business clients. And while this is a UK play for now, one assumes that they will look to expand across their operating countries as Vodafone Cyber Enhanced gains traction.”
In our blog, Artificial Intelligence – Hype vs Reality, published last month we explored why the buzz around AI and machine learning have got senior management excited about future possibilities of what technology can do for their business. AI – starting with automation – is being evaluated by organisations across industries. Several functions within an organisation can leverage AI and the technology is set to become part of enterprise solutions in the next few years. AI is fast becoming the tool which empowers business leaders to transform their organisations. However, it also requires a rethink on data integration and analysis, and the use of the intelligence generated. For a successful AI implementation, an organisation will have to leverage other enabling technologies.
Technologies Enabling AI
IoT
Organisations have been evaluating IoT – especially for Industry 4.0 – for the better part of the last decade. Many organisations, however, have found IoT implementations daunting for various reasons – concerns around security, technology integration challenges, customisation to meet organisational and system requirements and so on. As the hype around what AI can do for the organisation increases, they are being forced to re-look at their IoT investments. AI algorithms derive intelligence from real-time data collected from sensors, remote inputs, connected things, and other sources. No surprise then that IoT Sensor Analytics is the AI solution that is seeing most uptake (Figure 1).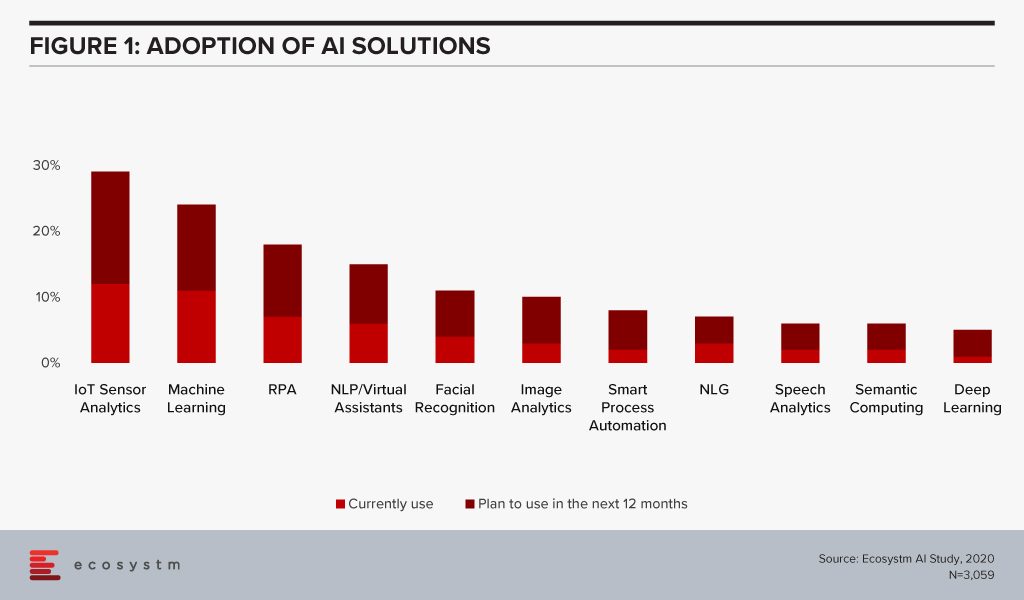
This is especially true for asset and logistics-driven industries such as Resource & Primary, Energy & Utilities, Manufacturing and Retail. Of the AI solutions, the biggest growth in 2020 will also come from IoT Analytics – with Healthcare and Transportation ramping up their IoT spend. And industries will also look at different ways they can leverage the IoT data for operational efficiency and improved customer experience (CX). For instance, in Transportation, AI can use IoT sensor data from a fleet to help improve time, cost and fuel efficiency – suggesting less congested routes with minimal stops through GPS systems, maintaining speeds with automated speed limiters – and also in predictive fleet maintenance.
IoT sensors are already creating – and will continue to create large amounts of data. As organisations look to AI-enabled IoT devices, there will be a shift from one-way transactions (i.e. collecting and analysing data) to bi-directional transactions (i.e. sensing and responding). Eventually, IoT as a separate technology will cease to exist and will become subsumed by AI.
Cloud
AI is changing the way organisations need to store, process and analyse the data to derive useful insights and decision-making practices. This is pushing the adoption of cloud, even in the most conservative organisations. Cloud is no longer only required for infrastructure and back-up – but actually improving business processes, by enabling real-time data and systems access.
Over the next decades, IoT devices will grow exponentially. Today, data is already going into the cloud and data centres on a real-time basis from sensors and automated devices. However, as these devices become bi-directional, decisions will need to be made in real-time as well. This has required cloud environments to evolve as the current cloud environments are unable to support this. Edge Computing will be essential in this intelligent and automated world. Tech vendors are building on their edge solutions and tech buyers are increasingly getting interested in the Edge allowing better decision-making through machine learning and AI. Not only will AI drive cloud adoption, but it will also drive cloud providers to evolve their offerings.
The global Ecosystm AI study finds that four of the top five vendors that organisations are using for their AI solutions (across data mining, computer vision, speech recognition and synthesis, and automation solutions) today, are also leading cloud platform providers (Figure 2).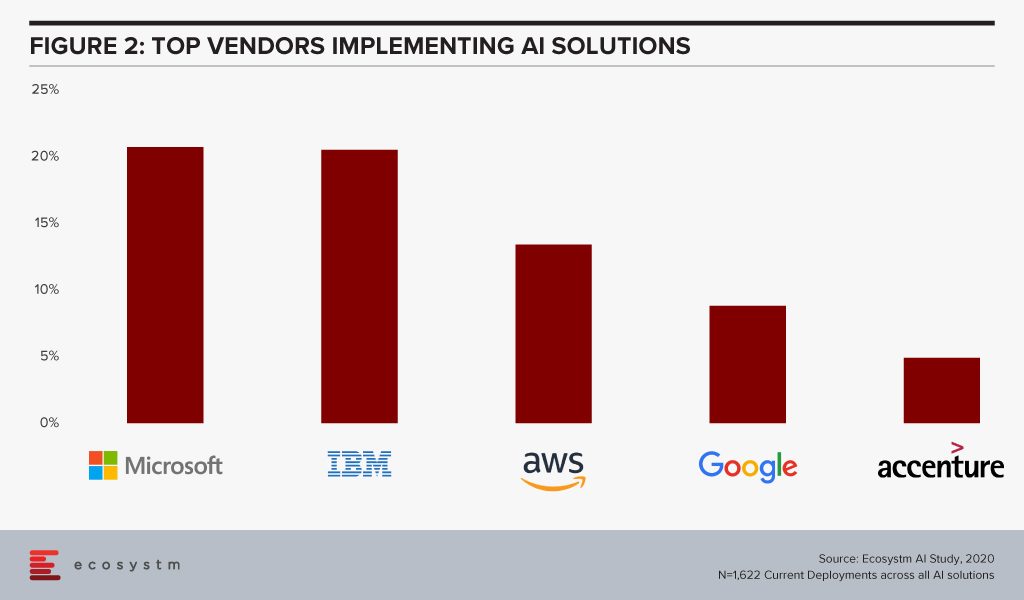
The fact that intelligent solutions are often composed of multiple AI algorithms gives the major cloud platforms an edge – if they reside on the same cloud environment, they are more likely to work seamlessly and without much integration or security issues. Cloud platform providers are also working hard on their AI capabilities.
Cybersecurity & AI
The technology area that is getting impacted by AI most is arguably Cybersecurity. Security Teams are both struggling with cybersecurity initiatives as a result of AI projects – and at the same time are being empowered by AI to provide more secure solutions for their organisations.
The global Ecosystm Cybersecurity study finds that one of the key drivers that is forcing Security Teams to keep an eye on their cybersecurity measures is the organisations’ needs to handle security requirements for their Digital Transformation (DX) projects involving AI and IoT deployments (Figure 3).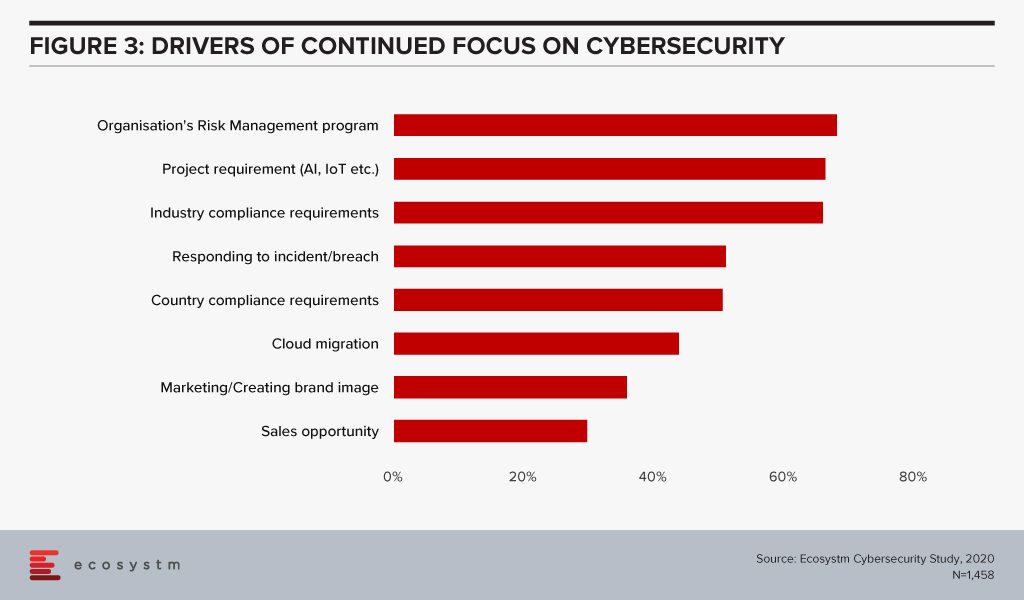
While AI deployments keep challenging Security Teams, AI is also helping cybersecurity professionals. Many businesses and industries are increasingly leveraging AI in their Security Operations (SecOps) solutions. AI analyses the inflow and outflow of data in a system and analyses threats based on the learnings. The trained AI systems and algorithms help businesses to curate and fight thousands of daily breaches, unsafe codes and enable proactive security and quick incident response. As organisations focus their attention on Data Security, SecOps & Incident Response and Threat Analysis & Intelligence, they will evaluate solutions with embedded AI.
AI and the Experience Economy
AI has an immense role to play in improving CX and employee experience (EX) by giving access to real-time data and bringing better decision-making capabilities.
Enterprise mobility was a key area of focus when smartphones were introduced to the modern workplace. Since then enterprise mobility has evolved as business-as-usual for IT Teams. However, with the introduction of AI, organisations are being forced to re-evaluate and revamp their enterprise mobility solutions. As an example, it has made mobile app testing easier for tech teams. Mobile automation will help automate testing of a mobile app – across operating systems (Figure 4). While more organisations tend to outsource their app development functions today, mobile automation reduces the testing time cycle, allowing faster app deployments – both for internal apps (increasing employee productivity and agility) and for consumer apps (improving CX).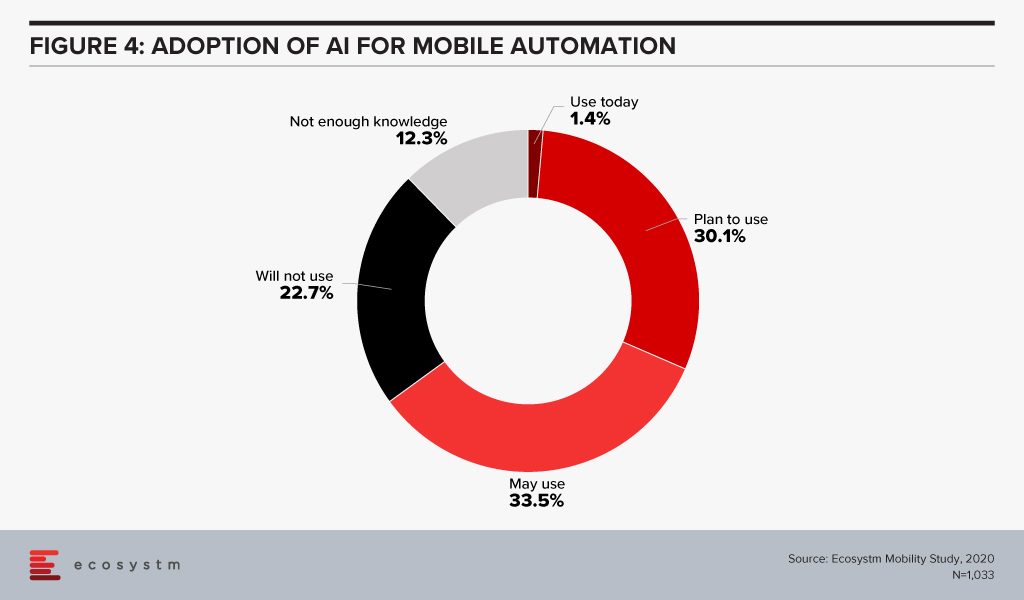
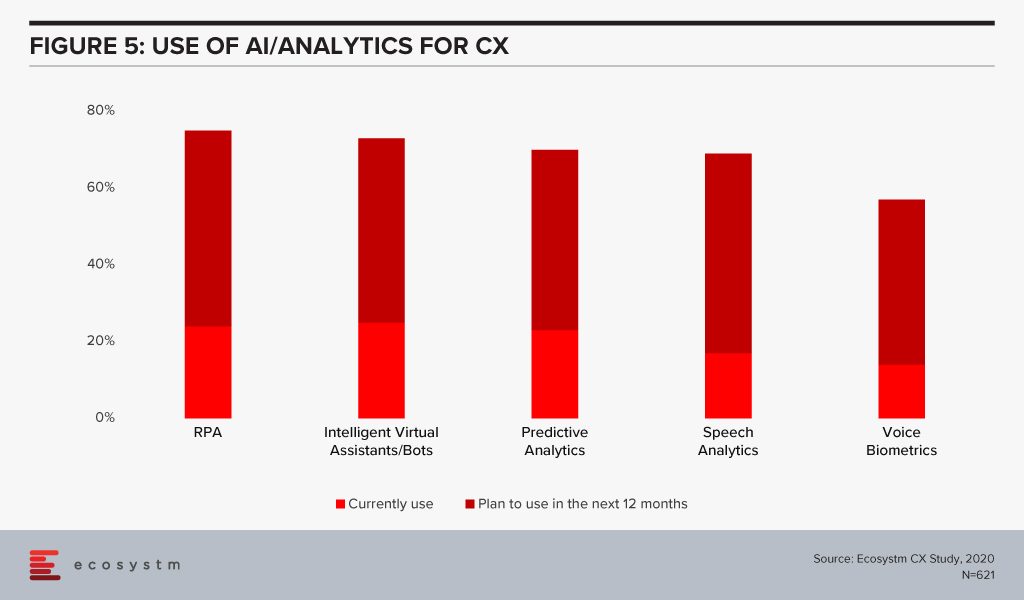
CX Teams within organisations are especially evaluating AI technologies. Visual and voice engagement technologies such as NLP, virtual assistants and chatbots enable efficient services, real-time delivery and better customer engagement. AI also allows organisations to offer personalised services to customers providing spot offers, self-service solutions and custom recommendations. Customer centres are re-evaluating their solutions to incorporate more AI-based solutions (Figure 5).
The buzz around AI is forcing tech teams to evaluate how AI can be leveraged in their enterprise solutions and at enabling technologies that will make AI adoption seamless. Has your organisation started re-evaluating other tech areas because of your AI requirements? Let us know in the comments below.






























