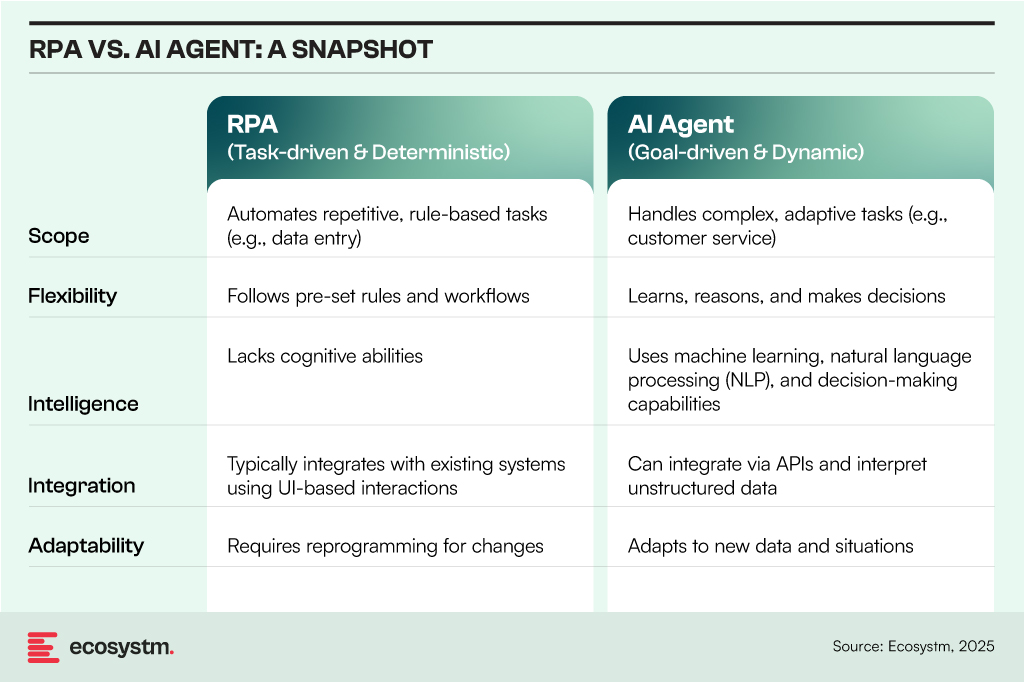
The promise of AI agents – intelligent programs or systems that autonomously perform tasks on behalf of people or systems – is enormous. These systems will augment and replace human workers, offering intelligence far beyond the simple RPA (Robotic Process Automation) bots that have become commonplace in recent years.
RPA and AI Agents both automate tasks but differ in scope, flexibility, and intelligence:
7 Lessons for AI Agents: Insights from RPA Deployments
However, in many ways, RPA and AI agents are similar – they both address similar challenges, albeit with different levels of automation and complexity. RPA adoption has shown that uncontrolled deployment leads to chaos, requiring a balance of governance, standardisation, and ongoing monitoring. The same principles apply to AI agent management, but with greater complexity due to AI’s dynamic and learning-based nature.
By learning from RPA’s mistakes, organisations can ensure AI agents deliver sustainable value, remain secure, and operate efficiently within a governed and well-managed environment.
#1 Controlling Sprawl with Centralised Governance
A key lesson from RPA adoption is that many organisations deployed RPA bots without a clear strategy, resulting in uncontrolled sprawl, duplicate bots, and fragmented automation efforts. This lack of oversight led to the rise of shadow IT practices, where business units created their own bots without proper IT involvement, further complicating the automation landscape and reducing overall effectiveness.
Application to AI Agents:
- Establish centralised governance early, ensuring alignment between IT and business units.
- Implement AI agent registries to track deployments, functions, and ownership.
- Enforce consistent policies for AI deployment, access, and version control.
#2 Standardising Development and Deployment
Bot development varied across teams, with different toolsets being used by different departments. This often led to poorly documented scripts, inconsistent programming standards, and difficulties in maintaining bots. Additionally, rework and inefficiencies arose as teams developed redundant bots, further complicating the automation process and reducing overall effectiveness.
Application to AI Agents:
- Standardise frameworks for AI agent development (e.g., predefined APIs, templates, and design patterns).
- Use shared models and foundational capabilities instead of building AI agents from scratch for each use case.
- Implement code repositories and CI/CD pipelines for AI agents to ensure consistency and controlled updates.
#3 Balancing Citizen Development with IT Control
Business users, or citizen developers, created RPA bots without adhering to IT best practices, resulting in security risks, inefficiencies, and technical debt. As a result, IT teams faced challenges in tracking and supporting business-driven automation efforts, leading to a lack of oversight and increased complexity in maintaining these bots.
Application to AI Agents:
- Empower business users to build and customise AI agents but within controlled environments (e.g., low-code/no-code platforms with governance layers).
- Implement AI sandboxes where experimentation is allowed but requires approval before production deployment.
- Establish clear roles and responsibilities between IT, AI governance teams, and business users.
#4 Proactive Monitoring and Maintenance
Organisations often underestimated the effort required to maintain RPA bots, resulting in failures when process changes, system updates, or API modifications occurred. As a result, bots frequently stopped working without warning, disrupting business processes and leading to unanticipated downtime and inefficiencies. This lack of ongoing maintenance and adaptation to evolving systems contributed to significant operational disruptions.
Application to AI Agents:
- Implement continuous monitoring and logging for AI agent activities and outputs.
- Develop automated retraining and feedback loops for AI models to prevent performance degradation.
- Create AI observability dashboards to track usage, drift, errors, and security incidents.
#5 Security, Compliance, and Ethical Considerations
Insufficient security measures led to data leaks and access control issues, with bots operating under overly permissive settings. Also, a lack of proactive compliance planning resulted in serious regulatory concerns, particularly within industries subject to stringent oversight, highlighting the critical need for integrating security and compliance considerations from the outset of automation deployments.
Application to AI Agents:
- Enforce role-based access control (RBAC) and least privilege access to ensure secure and controlled usage.
- Integrate explainability and auditability features to comply with regulations like GDPR and emerging AI legislation.
- Develop an AI ethics framework to address bias, ensure decision-making transparency, and uphold accountability.
#6 Cost Management and ROI Measurement
Initial excitement led to unchecked RPA investments, but many organisations struggled to measure the ROI of bots. As a result, some RPA bots became cost centres, with high maintenance costs outweighing the benefits they initially provided. This lack of clear ROI often hindered organisations from realising the full potential of their automation efforts.
Application to AI Agents:
- Define success metrics for AI agents upfront, tracking impact on productivity, cost savings, and user experience.
- Use AI workload optimisation tools to manage computing costs and avoid overconsumption of resources.
- Regularly review AI agents’ utility and retire underperforming ones to avoid AI bloat.
#7 Human Oversight and Hybrid Workflows
The assumption that bots could fully replace humans led to failures in situations where exceptions, judgment, or complex decision-making were necessary. Bots struggled to handle scenarios that required nuanced thinking or flexibility, often leading to errors or inefficiencies. The most successful implementations, however, blended human and bot collaboration, leveraging the strengths of both to optimise processes and ensure that tasks were handled effectively and accurately.
Application to AI Agents:
- Integrate AI agents into human-in-the-loop (HITL) systems, allowing humans to provide oversight and validate critical decisions.
- Establish AI escalation paths for situations where agents encounter ambiguity or ethical concerns.
- Design AI agents to augment human capabilities, rather than fully replace roles.
The lessons learned from RPA’s journey provide valuable insights for navigating the complexities of AI agent deployment. By addressing governance, standardisation, and ethical considerations, organisations
can shift from reactive problem-solving to a more strategic approach, ensuring AI tools deliver value while operating within a responsible, secure, and efficient framework.

The global data protection landscape is growing increasingly complex. With the proliferation of privacy laws across jurisdictions, organisations face a daunting challenge in ensuring compliance.
From the foundational GDPR, the evolving US state-level regulations, to new regulations in emerging markets, businesses with cross-border presence must navigate a maze of requirements to protect consumer data. This complexity, coupled with the rapid pace of regulatory change, requires proactive and strategic approaches to data management and protection.
GDPR: The Catalyst for Global Data Privacy
At the forefront of this global push for data privacy stands the General Data Protection Regulation (GDPR) – a landmark legislation that has reshaped data governance both within the EU and beyond. It has become a de facto standard for data management, influencing the creation of similar laws in countries like India, China, and regions such as Southeast Asia and the US.
However, the GDPR is evolving to tackle new challenges and incorporate lessons from past data breaches. Amendments aim to enhance enforcement, especially in cross-border cases, expedite complaint handling, and strengthen breach penalties. Amendments to the GDPR in 2024 focus on improving enforcement efficiency. The One-Stop-Shop mechanism will be strengthened for better handling of cross-border data processing, with clearer guidelines for lead supervisory authority and faster information sharing. Deadlines for cross-border decisions will be shortened, and Data Protection Authorities (DPAs) must cooperate more closely. Rules for data transfers to third countries will be clarified, and DPAs will have stronger enforcement powers, including higher fines for non-compliance.
For organisations, these changes mean increased scrutiny and potential penalties due to faster investigations. Improved DPA cooperation can lead to more consistent enforcement across the EU, making it crucial to stay updated and adjust data protection practices. While aiming for more efficient GDPR enforcement, these changes may also increase compliance costs.
GDPR’s Global Impact: Shaping Data Privacy Laws Worldwide
Despite being drafted by the EU, the GDPR has global implications, influencing data privacy laws worldwide, including in Canada and the US.
Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA) governs how the private sector handles personal data, emphasising data minimisation and imposing fines of up to USD 75,000 for non-compliance.
The US data protection landscape is a patchwork of state laws influenced by the GDPR and PIPEDA. The California Privacy Rights Act (CPRA) and other state laws like Virginia’s CDPA and Colorado’s CPA reflect GDPR principles, requiring transparency and limiting data use. Proposed federal legislation, such as the American Data Privacy and Protection Act (ADPPA), aims to establish a national standard similar to PIPEDA.
The GDPR’s impact extends beyond EU borders, significantly influencing data protection laws in non-EU European countries. Countries like Switzerland, Norway, and Iceland have closely aligned their regulations with GDPR to maintain data flows with the EU. Switzerland, for instance, revised its Federal Data Protection Act to ensure compatibility with GDPR standards. The UK, post-Brexit, retained a modified version of GDPR in its domestic law through the UK GDPR and Data Protection Act 2018. Even countries like Serbia and North Macedonia, aspiring for EU membership, have modeled their data protection laws on GDPR principles.
Data Privacy: A Local Flavour in Emerging Markets
Emerging markets are recognising the critical need for robust data protection frameworks. These countries are not just following in the footsteps of established regulations but are creating laws that address their unique economic and cultural contexts while aligning with global standards.
Brazil has over 140 million internet users – the 4th largest in the world. Any data collection or processing within the country is protected by the Lei Geral de Proteção de Dados (or LGPD), even from data processors located outside of Brazil. The LGPD also mandates organisations to appoint a Data Protection Officer (DPO) and establishes the National Data Protection Authority (ANPD) to oversee compliance and enforcement.
Saudi Arabia’s Personal Data Protection Law (PDPL) requires explicit consent for data collection and use, aligning with global norms. However, it is tailored to support Saudi Arabia’s digital transformation goals. The PDPL is overseen by the Saudi Data and Artificial Intelligence Authority (SDAIA), linking data protection with the country’s broader AI and digital innovation initiatives.
Closer Home: Changes in Asia Pacific Regulations
The Asia Pacific region is experiencing a surge in data privacy regulations as countries strive to protect consumer rights and align with global standards.
Japan. Japan’s Act on the Protection of Personal Information (APPI) is set for a major overhaul in 2025. Certified organisations will have more time to report data breaches, while personal data might be used for AI training without consent. Enhanced data rights are also being considered, giving individuals greater control over biometric and children’s data. The government is still contemplating the introduction of administrative fines and collective action rights, though businesses have expressed concerns about potential negative impacts.
South Korea. South Korea has strengthened its data protection laws with significant amendments to the Personal Information Protection Act (PIPA), aiming to provide stronger safeguards for individual personal data. Key changes include stricter consent requirements, mandatory breach notifications within 72 hours, expanded data subject rights, refined data processing guidelines, and robust safeguards for emerging technologies like AI and IoT. There are also increased penalties for non-compliance.
China. China’s Personal Information Protection Law (PIPL) imposes stringent data privacy controls, emphasising user consent, data minimisation, and restricted cross-border data transfers. Severe penalties underscore the nation’s determination to safeguard personal information.
Southeast Asia. Southeast Asian countries are actively enhancing their data privacy landscapes. Singapore’s PDPA mandates breach notifications and increased fines. Malaysia is overhauling its data protection law, while Thailand’s PDPA has also recently come into effect.
Spotlight: India’s DPDP Act
The Digital Personal Data Protection Act, 2023 (DPDP Act), officially notified about a year ago, is anticipated to come into effect soon. This principles-based legislation shares similarities with the GDPR and applies to personal data that identifies individuals, whether collected digitally or digitised later. It excludes data used for personal or domestic purposes, aggregated research data, and publicly available information. The Act adopts GDPR-like territorial rules but does not extend to entities outside India that monitor behaviour within the country.
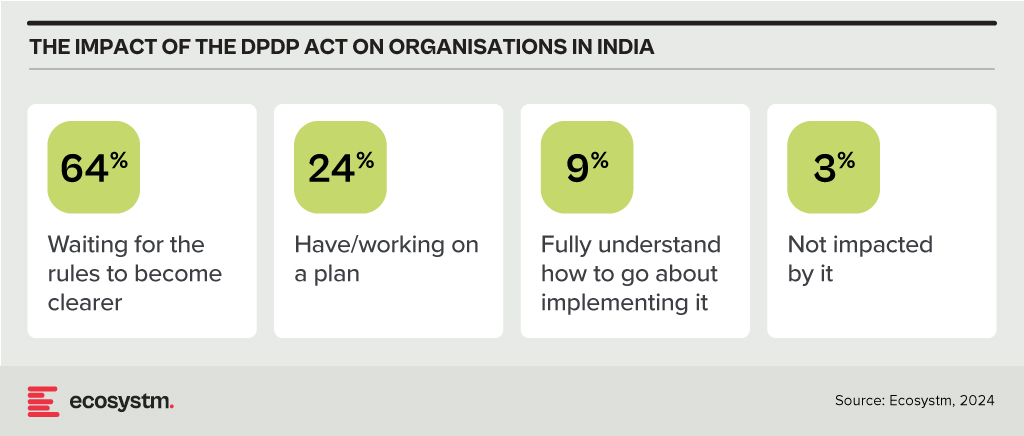
Consent under the DPDP Act must be free, informed, and specific, with companies required to provide a clear and itemised notice. Unlike the GDPR, the Act permits processing without consent for certain legitimate uses, such as legal obligations or emergencies. It also categorises data fiduciaries based on the volume and sensitivity of the data they handle, imposing additional obligations on significant data fiduciaries while offering exemptions for smaller entities. The Act simplifies cross-border data transfers compared to the GDPR, allowing transfers to all countries unless restricted by the Indian Government. It also provides broad exemptions to the State for data processing under specific conditions. Penalties for breaches are turnover agnostic, with considerations for breach severity and mitigating actions. The full impact of the DPDP Act will be clearer once the rules are finalised and the Board becomes operational, but 97% of Indian organisations acknowledge that it will affect them.
Conclusion
Data breaches pose significant risks to organisations, requiring a strong data protection strategy that combines technology and best practices. Key technological safeguards include encryption, identity access management (IAM), firewalls, data loss prevention (DLP) tools, tokenisation, and endpoint protection platforms (EPP). Along with technology, organisations should adopt best practices such as inventorying and classifying data, minimising data collection, maintaining transparency with customers, providing choices, and developing comprehensive privacy policies. Training employees and designing privacy-focused processes are also essential. By integrating robust technology with informed human practices, organisations can enhance their overall data protection strategy.

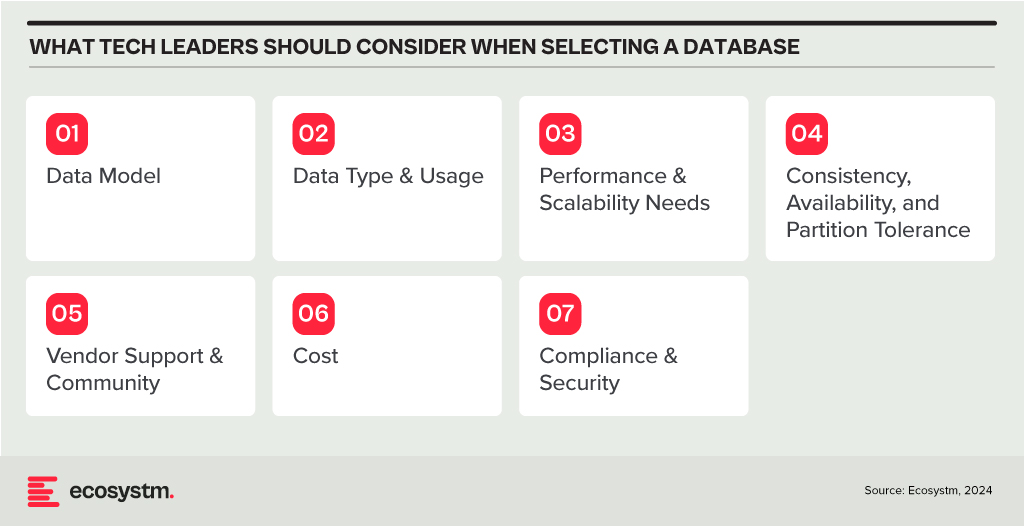
In my last Ecosystm Insights, I outlined various database options available to you. The challenge lies in selecting the right one. Selecting the right database is crucial for the success of any application or project. It involves understanding your data, the operations you’ll perform, scalability requirements, and more. Here is a guide that will walk you through key considerations and steps to choose the most suitable database from the list I shared last week.
Understand Your Data Model
Relational (RDBMS) vs. NoSQL. Choose RDBMS if your data is structured and relational, requiring complex queries and transactions with ACID (Atomicity, Consistency, Isolation, Durability) properties. Opt for NoSQL if you have unstructured or semi-structured data, need to scale horizontally, or require flexibility in your schema design.
Consider the Data Type and Usage
Document Databases are ideal for storing, retrieving, and managing document-oriented information. They’re great for content management systems, ecommerce applications, and handling semi-structured data like JSON, XML.
Key-Value Stores shine in scenarios where quick access to data is needed through a key. They’re perfect for caching and storing user sessions, configurations, or any scenario where the lookup is based on a unique key.
Wide-Column Stores offer flexibility and scalability for storing and querying large volumes of data across many servers, suitable for big data applications, real-time analytics, and high-speed transactions.
Graph Databases are designed for data intensely connected through relationships, ideal for social networks, recommendation engines, and fraud detection systems where relationships between data points are key.
Time-Series Databases are optimised for storing and querying sequential data points indexed in time order. Use them for monitoring systems, IoT applications, and financial trading systems where time-stamped data is critical.
Spatial Databases support spatial data types and queries, making them suitable for geographic information systems (GIS), location-based services, and applications requiring spatial indexing and querying capabilities.
Assess Performance and Scalability Needs
In-Memory Databases like Redis offer high throughput and low latency for scenarios requiring rapid access to data, such as caching, session storage, and real-time analytics.
Distributed Databases like Cassandra or CouchDB are designed to run across multiple machines, offering high availability, fault tolerance, and scalability for applications with global reach and massive scale.
Evaluate Consistency, Availability, and Partition Tolerance (CAP Theorem)
Understand the trade-offs between consistency, availability, and partition tolerance. For example, if your application requires strong consistency, consider databases that prioritise consistency and partition tolerance (CP) like MongoDB or relational databases. If availability is paramount, look towards databases that offer availability and partition tolerance (AP) like Cassandra or CouchDB.
Other Considerations
Check for Vendor Support and Community. Evaluate the support and stability offered by vendors or open-source communities. Established products like Oracle Database, Microsoft SQL Server, and open-source options like PostgreSQL and MongoDB have robust support and active communities.
Cost. Consider both initial and long-term costs, including licenses, hardware, maintenance, and scalability. Open-source databases can reduce upfront costs, but ensure you account for support and operational expenses.
Compliance and Security. Ensure the database complies with relevant regulations (GDPR, HIPAA, etc.) and offers robust security features to protect sensitive data.
Try Before You Decide. Prototype your application with shortlisted databases to evaluate their performance, ease of use, and compatibility with your application’s requirements.
Conclusion
Selecting the right database is a strategic decision that impacts your application’s functionality, performance, and scalability. By carefully considering your data model, type of data, performance needs, and other factors like cost, support, and security, you can identify the database that best fits your project’s needs. Always stay informed about the latest developments in database technologies to make educated decisions as your requirements evolve.

The Banking, Financial Services, and Insurance (BFSI) industry, known for its cautious stance on technology, is swiftly undergoing a transformational modernisation journey. Areas such as digital customer experiences, automated fraud detection, and real-time risk assessment are all part of a technology-led roadmap. This shift is transforming the cybersecurity stance of BFSI organisations, which have conventionally favoured centralising everything within a data centre behind a firewall.
Ecosystm research finds that 75% of BFSI technology leaders believe that a data breach is inevitable. This requires taking a new cyber approach to detect threats early, reduce the impact of an attack, and avoid lateral movement across the network.
BFSI organisations will boost investments in two main areas over the next year: updating infrastructure and software, and exploring innovative domains like digital workplaces and automation. Cybersecurity investments are crucial in both of these areas.
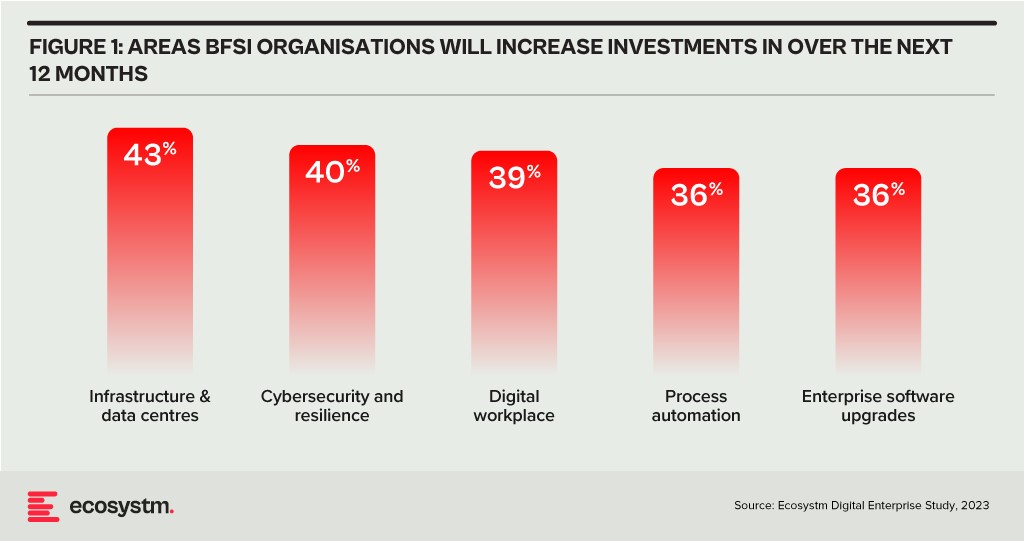
As a regulated industry, breaches come with significant cost implications, underscoring the need to prioritise cybersecurity. BFSI cybersecurity and risk teams need to constantly reassess their strategies for safeguarding data and fulfilling compliance obligations, as they explore ways to facilitate new services for customers, partners, and employees.
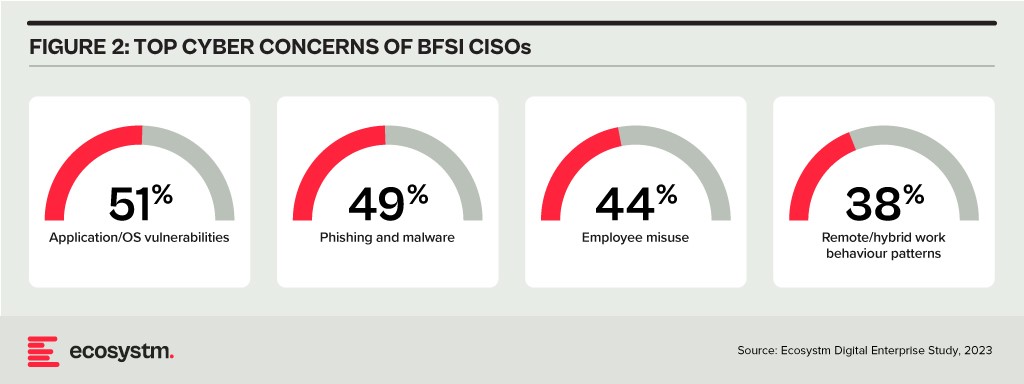
The primary concerns of BFSI CISOs can be categorised into two distinct groups:
- Expanding Technology Use. This includes the proliferation of applications and devices, as well as data access beyond the network perimeter.
- Employee-Related Vulnerabilities. This involves responses to phishing and malware attempts, as well as intentional and unintentional misuse of technology.
Vulnerabilities Arising from Employee Actions
Security vulnerabilities arising from employee actions and unawareness represent a significant and ongoing concern for businesses of all sizes and industries – the risks are just much bigger for BFSI. These vulnerabilities can lead to data breaches, financial losses, damage to reputation, and legal ramifications. A multi-pronged approach is needed that combines technology, training, policies, and a culture of security consciousness.
Training and Culture. BFSI organisations prioritise comprehensive training and awareness programs, educating employees about common threats like phishing and best practices for safeguarding sensitive data. While these programs are often ongoing and adaptable to new threats, they can sometimes become mere compliance checklists, raising questions about their true effectiveness. Conducting simulated phishing attacks and security quizzes to assess employee awareness and identify areas where further training is required, can be effective.
To truly educate employees on risks, it’s essential to move beyond compliance and build a cybersecurity culture throughout the organisation. This can involve setting organisation-wide security KPIs that cascade from the CEO down to every employee, promoting accountability and transparency. Creating an environment where employees feel comfortable reporting security concerns is critical for early threat detection and mitigation.
Policies. Clear security policies and enforcement are essential for ensuring that employees understand their roles within the broader security framework, including responsibilities on strong password use, secure data handling, and prompt incident reporting. Implementing the principle of least privilege, which restricts access based on specific roles, mitigates potential harm from insider threats and inadvertent data exposure. Policies should evolve through routine security audits, including technical assessments and evaluations of employee protocol adherence, which will help organisations with a swifter identification of vulnerabilities and to take the necessary corrective actions.
However, despite the best efforts, breaches do happen – and this is where a well-defined incident response plan, that is regularly tested and updated, is crucial to minimise the damage. This requires every employee to know their roles and responsibilities during a security incident.
Tech Expansion Leading to Cyber Complexity
Cloud. Initially hesitant to transition essential workloads to the cloud, the BFSI industry has experienced a shift in perspective due to the rise of inventive SaaS-based Fintech tools and hybrid cloud solutions, that have created new impetus for change. This new distributed architecture requires a fresh look at cyber measures. Secure Access Service Edge (SASE) providers are integrating a range of cloud-delivered safeguards, such as FWaaS, CASB, and ZTNA with SD-WAN to ensure organisations can securely access the cloud without compromising on performance.
Data & AI. Data holds paramount importance in the BFSI industry for informed decision-making, personalised customer experiences, risk assessment, fraud prevention, and regulatory compliance. AI applications are being used to tailor products and services, optimise operational efficiency, and stay competitive in an evolving market. As part of their technology modernisation efforts, 47% of BFSI institutions are refining their data and AI strategies. They also acknowledge the challenges associated – and satisfying risk, regulatory, and compliance requirements is one of the biggest challenges facing BFSI organisations in the AI deployments.
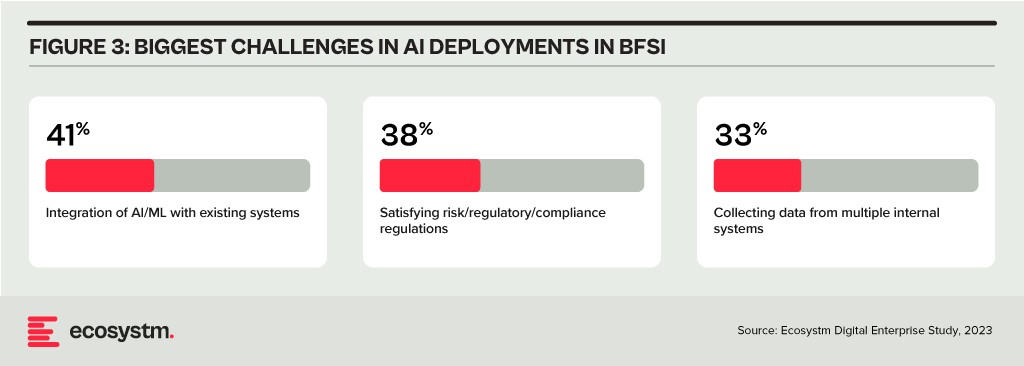
The rush to experiment with Generative AI and foundation models to assist customers and employees is only heightening these concerns. There is an urgent need for policies around the use of these emerging technologies. Initiatives such as the Monetary Authority of Singapore’s Veritas that aim to enable financial institutions to evaluate their AI and data analytics solutions against the principles of fairness, ethics, accountability, and transparency (FEAT) are expected to provide the much-needed guidance to the industry.
Digital Workplace. As with other industries with a high percentage of knowledge workers, BFSI organisations are grappling with granting remote access to staff. Cloud-based collaboration and Fintech tools, BYOD policies, and sensitive data traversing home networks are all creating new challenges for cyber teams. Modern approaches, such as zero trust network access, privilege management, and network segmentation are necessary to ensure workers can seamlessly but securely perform their roles remotely.
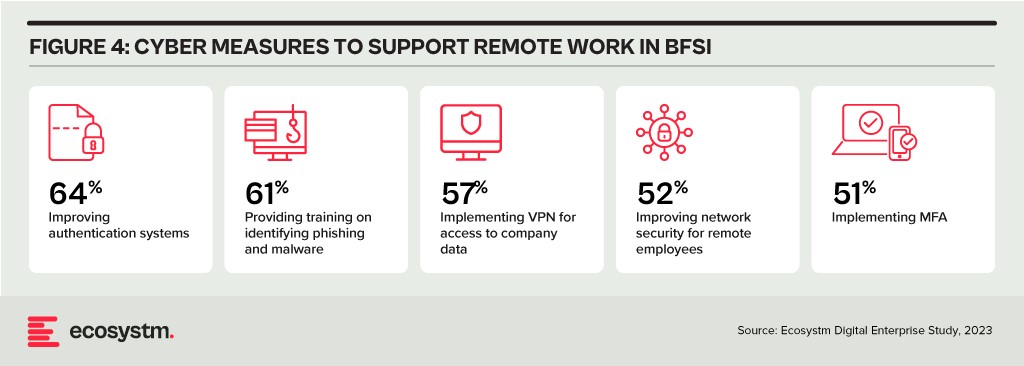
Looking Beyond Technology: Evaluating the Adequacy of Compliance-Centric Cyber Strategies
The BFSI industry stands among the most rigorously regulated industries, with scrutiny intensifying following every collapse or notable breach. Cyber and data protection teams shoulder the responsibility of understanding the implications of and adhering to emerging data protection regulations in areas such as GDPR, PCI-DSS, SOC 2, and PSD2. Automating compliance procedures emerges as a compelling solution to streamline processes, mitigate risks, and curtail expenses. Technologies such as robotic process automation (RPA), low-code development, and continuous compliance monitoring are gaining prominence.
The adoption of AI to enhance security is still emerging but will accelerate rapidly. Ecosystm research shows that within the next two years, nearly 70% of BFSI organisations will have invested in SecOps. AI can help Security Operations Centres (SOCs) prioritise alerts and respond to threats faster than could be performed manually. Additionally, the expanding variety of network endpoints, including customer devices, ATMs, and tools used by frontline employees, can embrace AI-enhanced protection without introducing additional onboarding friction.
However, there is a need for BFSI organisations to look beyond compliance checklists to a more holistic cyber approach that can prioritise cyber measures continually based on the risk to the organisations. And this is one of the biggest challenges that BFSI CISOs face. Ecosystm research finds that 72% of cyber and technology leaders in the industry feel that there is limited understanding of cyber risk and governance in their organisations.
In fact, BFSI organisations must look at the interconnectedness of an intelligence-led and risk-based strategy. Thorough risk assessments let organisations prioritise vulnerability mitigation effectively. This targeted approach optimises security initiatives by focusing on high-risk areas, reducing security debt. To adapt to evolving threats, intelligence should inform risk assessment. Intelligence-led strategies empower cybersecurity leaders with real-time threat insights for proactive measures, actively tackling emerging threats and vulnerabilities – and definitely moving beyond compliance-focused strategies.

In this blog, our guest authors Randeep Sudan and Yamin Oo talk about the pervasiveness of the Digital Economy, and the key trends that will determine its future trajectory. “That the world in 2030 will be very different from today is obvious. We may, however, be surprised by the extent and sweep of the change ahead of us.”


The Digital Economy – a term first coined by Don Tapscott in 1994 – is not easy to define or measure. At one end, it is limited to the production and consumption of digital goods and services. On the other end, according to the European Parliament, “The digital economy is increasingly interwoven with the physical or offline economy making it more and more difficult to clearly delineate the digital economy“. We are, however, witnessing the Digital Economy transitioning to an economy that is digital.
Given the pervasiveness of the Digital Economy, its future will be determined by the complex interplay of several trends. Some of the trends that illustrate the future trajectory of the Digital Economy are:
Technology
We will see AI becoming ubiquitous as it is leveraged in every sector and sphere of activity. According to one estimate, AI is estimated to contribute USD 15.7 trillion to the global economy by 2030, which is more than the current GDP of China and India combined! We are also likely to see rapid progress in technologies related to Extended Reality (XR) in the coming years. COVID-19 is accelerating this trend, as we can see from the offerings of companies like Spatial and MeetinVR that facilitate virtual business meetings. The analog world’s rendering into its digital twin will see us moving towards a metaverse – a virtual shared space imagined in Neal Stephenson’s novel Snowcrash. Some of the biggest names in the tech industry – Apple (Apple glass), Facebook (Oculus), Sony (Playstation) – are assiduously working towards this direction.
Given the importance of telecom infrastructure to the Digital Economy, 5G networks are being rolled out in countries worldwide (Figure 1). However, even as 5G is being deployed, the buzz around 6G is getting louder. 6G may transmit data 100 times faster than 5G and may see deployment by 2030 given the decadal cycles for telecom: 1G in the 80s, 2G in the 90s, 3G in the decade following 2000, 4G in the decade starting 2010, and 5G beginning in the 2020s.
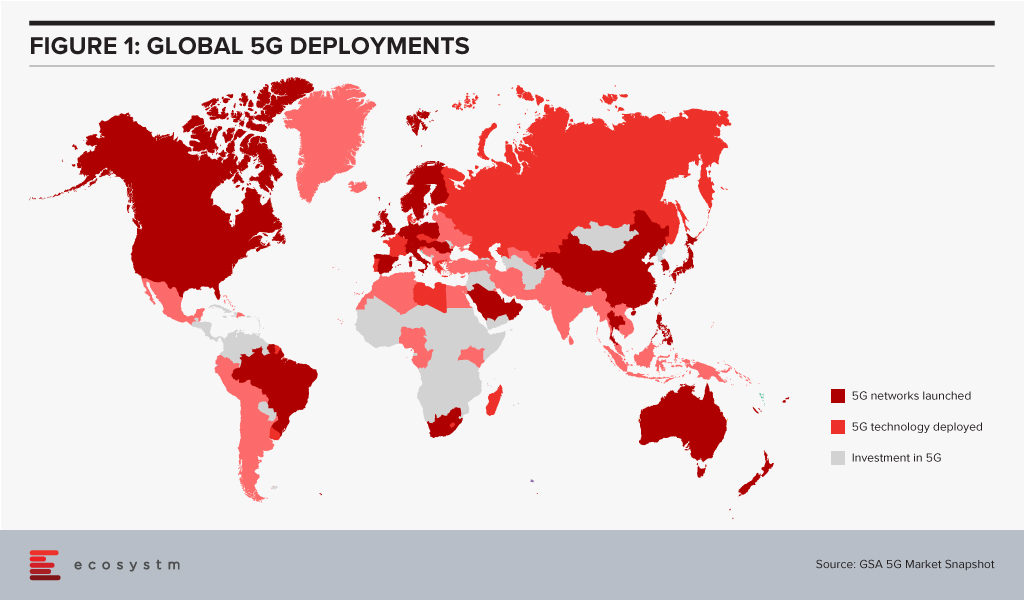
The availability of high bandwidth, low latency networks could lead to newer applications and further breakthroughs in innovative technologies.
The Future of Work
With the rapid growth in automation and AI, we are likely to see significant labour market disruptions. Moreover, COVID-19 has been a watershed for the global economy – its impacts will continue to be felt for many years to come. According to the International Labor Organization, 495 million full-time jobs were lost in the first two quarters of 2020 due to COVID-19. Lower and middle-income countries have suffered the most, with an estimated 23.3% drop in working hours – equivalent to 240 million jobs.
A recent report from the World Economic Forum estimates that by 2025, 85 million jobs may be displaced due to automation and AI, while 97 million new roles may emerge. We will see significant changes and turbulence in labour markets across multiple industries and geographies in the years ahead. If we look at how the top ten skills required by the top 10 US companies have been changing over time, we get an indication of the Future of Work. Companies are more focused on “soft” skills, that are not easily addressed by AI & Automation.
We are also likely to see a shift from humans adapting to technology to technologies adapting to humans. For example, the acceleration in digital twins combined with advancements in XR could allow unskilled workers to do skilled jobs. AR could guide a worker to repair a piece of mechanical equipment without long years of previous training. Similarly, the emergence of ‘Low Code No Code’ (LCNC) applications will allow ordinary individuals to do tasks that previously required specialised training.
Climate Change
Scientists have long focused our attention to limit the carbon dioxide in the atmosphere to 450 parts per million to avoid catastrophic climate change. In 2016, the World Meteorological Organization reported this concentration had crossed 400 parts per million, leaving us with a shorter runway to prevent calamitous climate change. We are, therefore, likely to see increased efforts to tackle climate change in the decade ahead.
Digital technologies can impact the global climate agenda in multiple ways: smart grids, smart buildings, smart appliances, intelligent transport systems, shared mobility, and 3D printing, to name a few. Digital technologies will also allow new sources of renewable energy to be tapped. For example, the molten core of the earth is over 6,000°C. “Just 0.1% of the heat content of Earth could supply humanity’s total energy needs for 2 million years,” according to AltaRock Energy. Advances in the use of digital technologies that allow for precise directional drilling will allow for advanced geothermal systems to be established as reliable power sources.
Splinternet
Tech bloggers like Doc Searls and Stephen Lewis had begun to theorise about a Splinternet as early as 2008. There was a danger of governments carving the world into geopolitical blocks and creating technology barriers. China’s Great Firewall and the US’s recent responses under the Trump administration are likely to hurtle us in the direction of a fractured internet. We may end up with the US dominating the western internet and China dominating a competing block of countries. The Digital Economy’s evolution would fracture into different camps, making it very different from what it is today.
Tech Regulation
The most valuable companies in the world today are in tech. Seven of the top ten companies in the world by market cap in 2020 are tech companies.
The recent investigation into competition in digital markets undertaken by the US House Judiciary Committee observed: “Over the past decade, the digital economy has become highly concentrated and prone to monopolisation. Several markets investigated by the Subcommittee – such as social networking, general online search, and online advertising – are dominated by just one or two firms. The companies investigated by the Subcommittee – Amazon, Apple, Facebook, and Google – have captured control over key channels of distribution and have come to function as gatekeepers. Just a decade into the future, 30% of the world’s gross economic output may lie with these firms, and just a handful of others.“
We have also witnessed the rapid diversification of data monopolies into other sectors. See, for example, the diversification of VC investments by Alibaba’s Ant Group over time. In 2015 they were investing in 5 areas, which has doubled in the last 5 years.
The call for the regulation of big tech will gain momentum in the coming years. The European Union is likely to lead here, just the way just it did in the case of its General Data Protection Regulation.
Governments will also require data monopolies to share data. China mandates its automakers to share data generated by electric vehicles with a government research institute. This data is essential for public safety and planning battery-recharging stations. The Australian Government promotes the concept of sharing “designated datasets” that could include data held by the private sector that has significant community benefits. Similarly, France’s Law for a Digital Republic requires the sharing data by certain categories of the private sector. Such blurring of boundaries between public and private data will become more important.
We will also see the growing importance of data trusts. These are structures where data is placed in the custody of a “Board of Trustees” who have a fiduciary responsibility to look after the interests of data owners. Such data trusts might give individuals better control over their data.
Every aspect of the economy is being digitalised today. In the next decade we are likely to witness foundational shifts in how the Digital or Data Economy is structured. It will also see increasing risks as cyber threats grow exponentially from cybercriminals and state actors. That the world in 2030 will be very different from today is obvious. We may, however, be surprised by the extent and sweep of the change ahead of us.
Singapore FinTech Festival 2020: Economic Summit
For more insights, attend the Singapore FinTech Festival 2020: Economic Summit which will cover topics tied to the state of the economy, path to recovery and re-framing the new financial services landscape

The Hamburg State Commissioner for Data Protection and Freedom of Information (HmbBfDI) imposed a fine of USD 41.3 million on Swedish MNC, Hennes & Mauritz (H&M) for illegal surveillance of employees in H&M Germany’s service centre at Nuremberg.
The data privacy violations reportedly began in 2014 when the company started collecting employee data including their personal information, holidays, medical records, informal chats and other private details. It was found that the information was unlawfully recorded and stored; and was further opened to managers. The violations were discovered in October 2019 when due to a computing error the data became accessible company-wide for a short span.
Ecosystm Principal Analyst Claus Mortensen says. “This is one of those cases that are so blatant that you cannot really say it is setting a precedent for future cases. All the factors that would constitute a breach of the GDPR are here: it involves several types of data that shouldn’t be collected; poorly managed storage and access control; and to finish it all off, a data leak. So even though the fine is relatively high, H&M should probably be happy that it was not bigger – the GDPR authorises fines of up to 4% of a company’s global annual turnover.”
Mortensen adds, “It should also be said that H&M has handled the aftermath well by accepting full blame and by offering compensation to all affected employees. It is possible that these intentions were considered by the HmbBfDI and prevented an even higher fine.”
The penalty on the Swedish retailer is the highest in Germany linked to the General Data Protection Regulation (GDPR) legislation since it came into effect in 2018 and the second highest throughout the continent. Last year, France’s data protection watchdog fined Google USD 58.7 million for not appropriately disclosing data collection practices to users across its services to personalise advertising.
Talking about the growing significance of fines for data breaches, Ecosystm Principal Advisor Andrew Milroy says, “To be effective, GDPR needs to be enforced consistently across the board and have a significant impact. It is too easy to ‘corner cut’ data protection activities. Some breaches may not have an operational impact. For this reason, the cost of being caught needs to be sufficiently large so that it makes commercial sense to comply.”
According to Milroy, “The sizeable fine meted out to H&M together with the publicity it has generated shows that the regulators are serious about GDPR and enforcing it. Other regulators around the world need to make sure that their jurisdictions don’t become ‘soft touches’ for malicious actors.”
EU Proposing New Data Sharing Rules
We are also seeing the European Union (EU) make moves to regulate digital services and customer data use by technology providers, as part of the European Union Digital Strategy. The EU is drafting new rules under the Digital Services Act to force larger technology providers to share their customer data across the industry, to create an even playing field for smaller providers and SMEs. The aim is to make the data available to all for both commercial use and innovation. This is being driven by the EU’s antitrust arm, aimed to reduce the competitive edge tech giants have over their competition and they may be banned from preferential treatment of their own services on their sites or platforms. The law, which is expected to be formalised later this year, is also expected to prohibit technology providers from pre-installing applications or exclusive services on smartphones, laptops or devices. The measures will support users to move between platforms without losing access to their data.

The Malaysia Digital Economy Corporation (MDEC) has estimated that the country’s Digital Economy is worth USD3 trillion. Several initiatives have been introduced to promote the vision of a Digital Economy including: creating the Malaysia Tech Entrepreneur Programme (MTEP) aimed at tech founders who want to make Malaysia their base; the Malaysia Innovation Policy Council for industry collaboration on digital technology initiatives and streamlining policy/regulatory issues to support innovation; and the National eCommerce Roadmap aimed at small and medium enterprises (SMEs) to promote cross-border eCommerce.
Data Protection Laws for a Digital Economy
However, any country that aspires to be a Digital Economy, must have robust data protection laws that safeguards its citizens’ data. Malaysia’s Personal Data Protection Act 2010 (PDPA), was passed by the Malaysian Parliament in 2010 and came into force in late 2013. While the PDPA does provide guidelines for personal data protection to some extent, in light of technological advances, newer laws such as GDPR that are shaping the industry, and to keep up with the aspirations of creating a Digital Economy, there is a need for more comprehensive privacy laws.
“Growing the Digital Economy is a key agenda for Malaysia and a revised PDPA is a key component in ensuring trust and transparency,” says Shamir Amanullah, Principal Advisor Ecosystm. “The increasing and complex use of data and the proliferation of devices pose serious challenges which the data protection laws have to address. The recent US Federal Trade Commission’s hefty fines on Facebook and Equifax highlight the need to protect data of consumers and businesses alike.”
The PDPA is clearly a work in progress where while fast-growing areas such as electronic marketing and online privacy are mentioned in the act, there are no specific provisions to deal with breaches in these areas.
Updating the PDPA
In the last few years, Malaysia has realised that the PDPA fails to cover some areas. As an example, it does not take into consideration the proliferation of biometric data. The national ID card (MyKad) stores data using biometrics (thumbprints) and there is a clear rise in use of facial recognition technology in the country. Grab partnered with the Ministry of Transport last year, to use facial recognition technology to protect their drivers.
Malaysia is committed to their Digital Economy vision and is looking to update the PDPA, to make it more appropriate for contemporary needs and technology. The Government is consulting its citizens on possible ways to improve the PDPA. Between 14-28 February, the public can provide feedback on their thoughts and requirements on data privacy, through the Ministry of Communications and Multimedia’s web portal.
Some of the areas that have been found lacking and where feedback is being sought are expanding applications of the PDPA to data processors, making it compulsory to notify data breaches and simplifying cross-border personal data transfer.
Speaking about the areas that are likely to be addressed, Amanullah notes, “The review of the PDPA and the ongoing public consultation will deliberate extending the PDPA to non-commercial transactions. The existing PDPA does not cover non-commercial transactions involving charities, religious activities and even social media. The EU, Japan and – closer home – the Philippines have data protection acts which regulate both commercial and non-commercial transactions.”
Malaysia’s Communications & Multimedia Minister, Gobind Singh Deo, has from the start spoken about the need to update and bring the PDPA up to speed. “The goal of the Digital Economy is to take Malaysian enterprises beyond the country to Southeast Asian and global markets,” says Amanullah. “The EU GDPR is recognised as a leading global framework for data protection and is set to play a big role in the revised PDPA, to ensure that Malaysian companies adhere to the same data protection standards as global organisations.”
“The appointment of Data Protection Officers will be a major move to ensure that companies that hold sensitive private data have the necessary skills, processes and technology in place to comply with data protection laws.”

It’s been a tough couple of years for British Airways (BA). 2017 saw an IT failure that resulted in 726 flights getting cancelled and 75,000 passengers being stranded on a busy holiday weekend. The fallout from this incident was around GDP 80 million in compensation paid to passengers and an almost immediate 4% drop in the share price.
Then, in 2018, the British carrier fell victim to a security breach in which around 500,000 people had their personal data, including their credit card details, stolen by hackers.
It is this breach that British Airways is now told that it will be fined 183 million British Pounds for. The fine was announced by the British Information Commissioner’s Office (ICO), and if it stands, it will be the biggest fine ever imposed for a data breach in the UK or elsewhere in Europe. In fact, the fine dwarfs previous fines issued up until now.
The biggest fines issued by the ICO in the UK were to Facebook and Equifax – both of whom were fined GBP 500,000.
Facebook’s fine was for the notorious Cambridge Analytica data scandal, where the information of 87 million Facebook users was shared with the political consultancy through a quiz app that collected data from participants as well as their friends without their consent.
Equifax Ltd. fine was for something more similar to the British Airways case: In May 2017, hackers stole personal data including names, dates of birth, addresses, passwords, driving licences and financial details of 15 million UK customers. In its ruling, the ICO said that Equifax had failed to take appropriate steps to ensure the protection of this sensitive data despite warnings from the US government.
But these fines were all from before the General Data Protection Regulation (GDPR) came into effect. Now, under the new rules, fines can be as high as EUR 10,000,000 or 2% of total global annual turnover for the previous year (whichever is higher) for lesser data breach incidents. For significant data breaches and non-compliance, the fines can be double that: EUR 20,000,000 or 4% of total global annual turnover (whichever is higher).
British Airways’ GBP 183 million fine is the equivalent of 1.5% of its turnover in 2017. Had the ICO gone for the maximum limit, the fine could have been as much as GBP 489 million.
A lot can still happen before the fine is finally issued, and BA is likely to dispute the decision in court (Willie Walsh, the CEO of BA’s parent company, IAG, has said they will). But even if the fine ends up being significantly lower, there are obvious lessons to be learned from this case:
- “People’s personal data is just that—personal.” These were the words spoken by Elizabeth Denham, the ICO Information Commissioner, in response to media enquiries on the fine. In other words: companies will need to take data privacy extremely seriously from now on or expect very hefty fines.
- Attitude matters. British Airways chairman and chief executive, Alex Cruz, said in a statement that BA was “…surprised and disappointed in this initial finding from the ICO. British Airways responded quickly to a criminal act to steal customers’ data. We have found no evidence of fraud/fraudulent activity on accounts linked to the theft. We apologize to our customers for any inconvenience this event caused.”
Although we can’t know this for certain, the response may reflect what could be described as an “attitude problem” in how BA has been dealing with the ICO: a whiff of arrogance, blaming the breach on criminal hackers and failing to accept any blame or real responsibility for the incident.
We know from other GDPR cases in other countries that any failure to cooperate with the authorities may result in larger fines. Full transparency, full cooperation and accepting responsibility are the way to go. If it’s your data, then the buck stops with you.
- The risks associated with IT cutbacks just went through the roof. The operating losses following the financial crises of 2008 made the carrier slash back its IT budgets (as well as other “expenditures”). Airlines, in general, are notorious for under-spending on IT, but when combining that with further cutbacks on IT expenditure, disaster may ensue. BA’s recent IT related woes may or may not be a direct result of under-spending on IT, but in the court of public opinion, this connection has been made.
In any case, with the new fine regime under the GDPR, the risks associated with under-spending on IT – and on IT security in particular – have now gotten substantially bigger.
More than ever, the notion that IT is an expenditure that can be cut back on is a false economy.