In this blog, our guest authors Randeep Sudan and Yamin Oo talk about the pervasiveness of the Digital Economy, and the key trends that will determine its future trajectory. “That the world in 2030 will be very different from today is obvious. We may, however, be surprised by the extent and sweep of the change ahead of us.”


The Digital Economy – a term first coined by Don Tapscott in 1994 – is not easy to define or measure. At one end, it is limited to the production and consumption of digital goods and services. On the other end, according to the European Parliament, “The digital economy is increasingly interwoven with the physical or offline economy making it more and more difficult to clearly delineate the digital economy“. We are, however, witnessing the Digital Economy transitioning to an economy that is digital.
Given the pervasiveness of the Digital Economy, its future will be determined by the complex interplay of several trends. Some of the trends that illustrate the future trajectory of the Digital Economy are:
Technology
We will see AI becoming ubiquitous as it is leveraged in every sector and sphere of activity. According to one estimate, AI is estimated to contribute USD 15.7 trillion to the global economy by 2030, which is more than the current GDP of China and India combined! We are also likely to see rapid progress in technologies related to Extended Reality (XR) in the coming years. COVID-19 is accelerating this trend, as we can see from the offerings of companies like Spatial and MeetinVR that facilitate virtual business meetings. The analog world’s rendering into its digital twin will see us moving towards a metaverse – a virtual shared space imagined in Neal Stephenson’s novel Snowcrash. Some of the biggest names in the tech industry – Apple (Apple glass), Facebook (Oculus), Sony (Playstation) – are assiduously working towards this direction.
Given the importance of telecom infrastructure to the Digital Economy, 5G networks are being rolled out in countries worldwide (Figure 1). However, even as 5G is being deployed, the buzz around 6G is getting louder. 6G may transmit data 100 times faster than 5G and may see deployment by 2030 given the decadal cycles for telecom: 1G in the 80s, 2G in the 90s, 3G in the decade following 2000, 4G in the decade starting 2010, and 5G beginning in the 2020s.
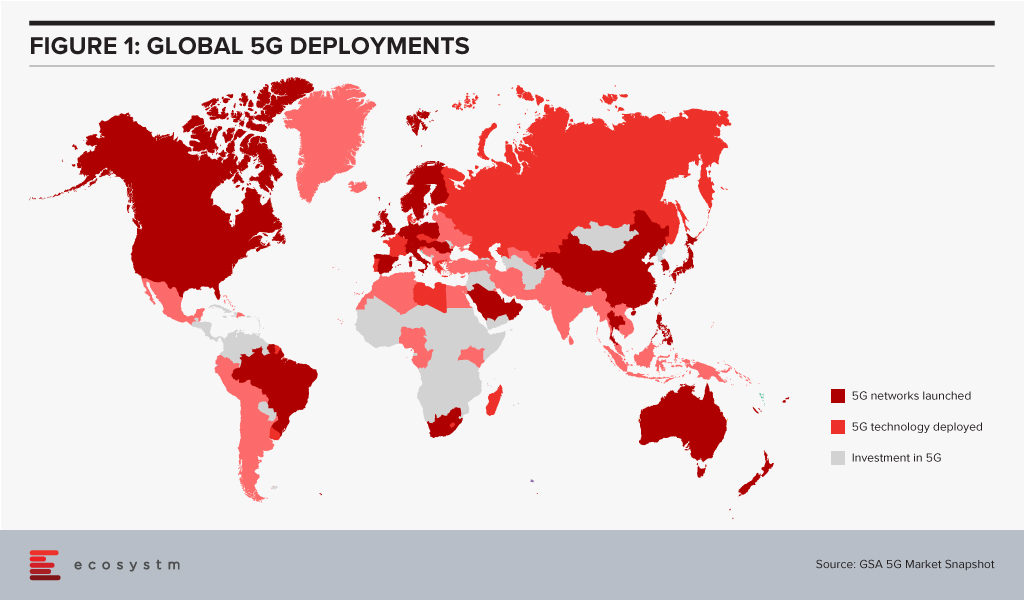
The availability of high bandwidth, low latency networks could lead to newer applications and further breakthroughs in innovative technologies.
The Future of Work
With the rapid growth in automation and AI, we are likely to see significant labour market disruptions. Moreover, COVID-19 has been a watershed for the global economy – its impacts will continue to be felt for many years to come. According to the International Labor Organization, 495 million full-time jobs were lost in the first two quarters of 2020 due to COVID-19. Lower and middle-income countries have suffered the most, with an estimated 23.3% drop in working hours – equivalent to 240 million jobs.
A recent report from the World Economic Forum estimates that by 2025, 85 million jobs may be displaced due to automation and AI, while 97 million new roles may emerge. We will see significant changes and turbulence in labour markets across multiple industries and geographies in the years ahead. If we look at how the top ten skills required by the top 10 US companies have been changing over time, we get an indication of the Future of Work. Companies are more focused on “soft” skills, that are not easily addressed by AI & Automation.
We are also likely to see a shift from humans adapting to technology to technologies adapting to humans. For example, the acceleration in digital twins combined with advancements in XR could allow unskilled workers to do skilled jobs. AR could guide a worker to repair a piece of mechanical equipment without long years of previous training. Similarly, the emergence of ‘Low Code No Code’ (LCNC) applications will allow ordinary individuals to do tasks that previously required specialised training.
Climate Change
Scientists have long focused our attention to limit the carbon dioxide in the atmosphere to 450 parts per million to avoid catastrophic climate change. In 2016, the World Meteorological Organization reported this concentration had crossed 400 parts per million, leaving us with a shorter runway to prevent calamitous climate change. We are, therefore, likely to see increased efforts to tackle climate change in the decade ahead.
Digital technologies can impact the global climate agenda in multiple ways: smart grids, smart buildings, smart appliances, intelligent transport systems, shared mobility, and 3D printing, to name a few. Digital technologies will also allow new sources of renewable energy to be tapped. For example, the molten core of the earth is over 6,000°C. “Just 0.1% of the heat content of Earth could supply humanity’s total energy needs for 2 million years,” according to AltaRock Energy. Advances in the use of digital technologies that allow for precise directional drilling will allow for advanced geothermal systems to be established as reliable power sources.
Splinternet
Tech bloggers like Doc Searls and Stephen Lewis had begun to theorise about a Splinternet as early as 2008. There was a danger of governments carving the world into geopolitical blocks and creating technology barriers. China’s Great Firewall and the US’s recent responses under the Trump administration are likely to hurtle us in the direction of a fractured internet. We may end up with the US dominating the western internet and China dominating a competing block of countries. The Digital Economy’s evolution would fracture into different camps, making it very different from what it is today.
Tech Regulation
The most valuable companies in the world today are in tech. Seven of the top ten companies in the world by market cap in 2020 are tech companies.
The recent investigation into competition in digital markets undertaken by the US House Judiciary Committee observed: “Over the past decade, the digital economy has become highly concentrated and prone to monopolisation. Several markets investigated by the Subcommittee – such as social networking, general online search, and online advertising – are dominated by just one or two firms. The companies investigated by the Subcommittee – Amazon, Apple, Facebook, and Google – have captured control over key channels of distribution and have come to function as gatekeepers. Just a decade into the future, 30% of the world’s gross economic output may lie with these firms, and just a handful of others.“
We have also witnessed the rapid diversification of data monopolies into other sectors. See, for example, the diversification of VC investments by Alibaba’s Ant Group over time. In 2015 they were investing in 5 areas, which has doubled in the last 5 years.
The call for the regulation of big tech will gain momentum in the coming years. The European Union is likely to lead here, just the way just it did in the case of its General Data Protection Regulation.
Governments will also require data monopolies to share data. China mandates its automakers to share data generated by electric vehicles with a government research institute. This data is essential for public safety and planning battery-recharging stations. The Australian Government promotes the concept of sharing “designated datasets” that could include data held by the private sector that has significant community benefits. Similarly, France’s Law for a Digital Republic requires the sharing data by certain categories of the private sector. Such blurring of boundaries between public and private data will become more important.
We will also see the growing importance of data trusts. These are structures where data is placed in the custody of a “Board of Trustees” who have a fiduciary responsibility to look after the interests of data owners. Such data trusts might give individuals better control over their data.
Every aspect of the economy is being digitalised today. In the next decade we are likely to witness foundational shifts in how the Digital or Data Economy is structured. It will also see increasing risks as cyber threats grow exponentially from cybercriminals and state actors. That the world in 2030 will be very different from today is obvious. We may, however, be surprised by the extent and sweep of the change ahead of us.
Singapore FinTech Festival 2020: Economic Summit
For more insights, attend the Singapore FinTech Festival 2020: Economic Summit which will cover topics tied to the state of the economy, path to recovery and re-framing the new financial services landscape

2020 saw a shutdown in both supply and demand which has effectively put the brakes on many economic activities and forced a complete rethink on how to continue doing business and maintain social interactions. The COVID-19 pandemic has accelerated digitalisation of consumers and enterprises, and the telecommunications industry has been the pillar which has kept the world ticking over. The rise in data use coupled with the fervent growth of the digital economy augurs well for the telecom sector in 2021.
Ecosystm Advisors Claus Mortensen, Rahul Gupta, and Shamir Amanullah present the top 5 Ecosystm predictions for Telecommunications & Mobility trends for 2021. This is a summary of the predictions – the full report (including the implications) is available to download for free on the Ecosystm platform.
The Top 5 Telecommunications & Mobility Trends for 2021
- The 5G Divide – Reality for Some and Hype for Others
Despite the economic challenges in 2020, GSMA reports that the global 5G subscriptions doubled QoQ in Q2 2020 to hit at least 137.7 million subscribers. This accounts for 1.5% of total subscribers – and is expected to rise to 30% by 2025.
The value of 5G will become increasingly mainstream in the next few years. 5G offers a tailored user-centric approach to network services, low latency and significantly higher number of connections which will power a new era of mobile Internet of Everything (IoE).
However, there are many operators who are still sceptical about 5G. In the US, many operators failed to get any tangible positives from 5G. In the near term, many operators will continue to evolve their 5G capabilities – a full grown standalone 5G technology implementation in some verticals might take longer.
The unsuccessful launch of 5G by the US operators does not mean that 5G is a failure, however. It also implies that we need to look at other geographies to lead us into 5G – and Asia Pacific may well emerge as a leader in this space. China, for example, leads the drive in 5G adoption; and 5G smartphones account for more than half of global sales in recent months.
- Telecom Operators Will Accelerate Digital Transformation
Telecom operators are facing increasing demands for cutting-edge services and top-notch customer experience (CX). The global pandemic has caused revenue loss, due to struggling economies and many operators will aim to reduce OpEX to circumvent these financial pressures, raise the quality of CX and retain existing customers. To realise this, there will be much focus on improvement in efficiencies, better operations management as well as improving the IT stack. These digital transformation efforts will enable rapid and flexible services provisioning, which will be better prepared for the tailored services customers now demand.
Many operators are increasingly incorporating cloudification alongside the 5G network deployment. Operators are moving towards transforming their operations and business support systems to a more virtualised and software-defined infrastructure. 5G will operate across a range of frequencies and bands – with significantly more devices and connections becoming software-defined with computing power at the Edge. Operators will also harness the power of AI to analyse massive volumes of data from the networks accessed by millions of devices in order to improve CX, ramp up operational efficiencies as well as introduce new services tailored to customer needs to increase revenue.
- Remote Working Will Transform Telecommunications Networks
The changing patterns in peak network traffic and the substantial movement of traffic from central business districts to residential areas require a fundamental rethink in network traffic management. In addition, many businesses continue to ramp up digital transformation efforts to conduct business online as physical channels will remain limited. Consumer onboarding will also be fervent, as organisations look at business recovery – resulting in increase in bandwidth requirements.
The increasing remote working trend is amplifying the need for greater cybersecurity. Cybersecurity has catapulted in importance as the pandemic has seen a worrying increase in attacks on banks, cloud servers and mobile devices, among others. Cyber-attack incidents specifically due to remote working, has seen a rise. A telecom operator’s compromised security can have country-wide, and even global consequences.
- SASE Will Grow – and Sprawl
Although it was perhaps originally seen as an Over-The-Top (OTT) provisioned competitive service to operators’ MPLS services, many telecom service providers have been embracing SD-WAN over the years as part of their managed services portfolio. “Traditional” SD-WAN offers some of the flexibility needed to address the change towards a more distributed access and the workload requirements that the pandemic has accelerated – the technology does not address all of the issues related to this transformed workspace.
Employees are now working from a variety of locations and workloads are becoming increasingly distributed. To address this change, organisations are challenged to move workloads and applications between platforms, potentially compromising security. Despite all the challenges that the pandemic brought with it – both human and technical – it has also provided organisations with an opportunity to rethink their IT and WAN architectures and to adopt an approach that has security at its core.
We believe that secure access service edge (SASE), which is a model for combining SD-WAN and security in a cloud-based environment, will see a drastic rise in adoption in 2021 and beyond.
- OTT Players Will Continue their Expansion in the Telecommunications Space
Facebook, Google, Amazon are no longer considered as web companies as they moved from standalone ‘web’ companies to become OTT providers and are now significant players in telecom space. With the Facebook-Jio deal in India earlier this year, and with Google and Amazon actively eyeing the telecom space, these players will continue to explore this space especially in the emerging markets of Asia and Africa. There are telecom providers in these countries which will be prime targets for partnerships. These operators could be those that have a large customer base, are struggling with their bottom lines or are already looking at exit routes. OTT players were already offering services like voice, messaging, video calling and so on which have been the domain expertise of mobile operators for a long time. The market will see instances where telecom providers will sell small stakes to OTT players at a premium and get access to the vast array of services that these OTT providers offer.

Artificial Intelligence (AI) is becoming embedded in financial services across consumer interactions and core business processes, including the use of chatbots and natural language processing (NLP) for KYC/AML risk assessment.
But what does AI mean for financial regulators? They are also consuming increasing amounts of data and are now using AI to gain new insights and inform policy decisions.
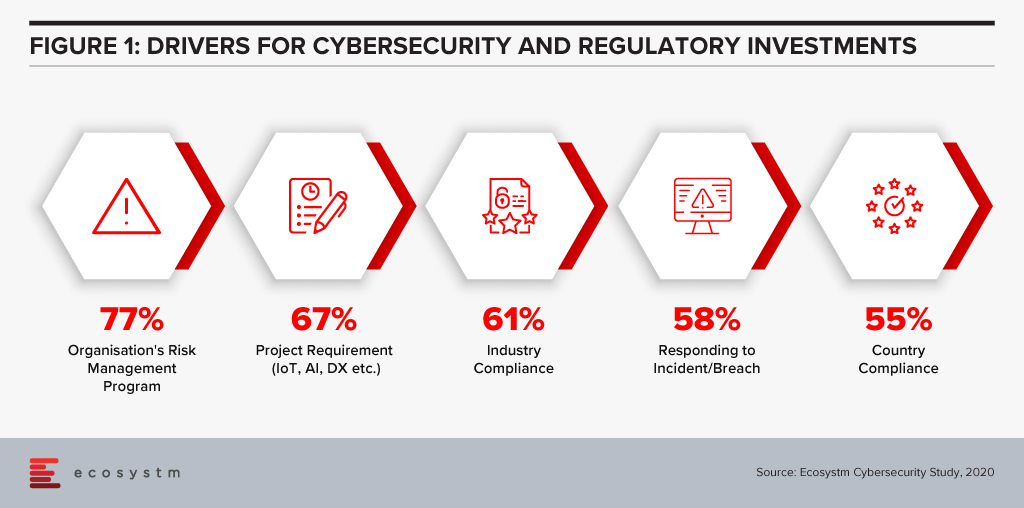
The efficiencies that AI offers can be harnessed in support of compliance within both financial regulation (RegTech) and financial supervision (SupTech). Authorities and regulated institutions have both turned to AI to help them manage the increased regulatory requirements that were put in place after the 2008 financial crisis. Ecosystm research finds that compliance is key to financial institutions (Figure 1).
SupTech is maturing with more robust safeguards and frameworks, enabling the necessary advancements in technology implementation for AI and Machine Learning (ML) to be used for regulatory supervision. The Bank of England and the UK Financial Conduct Authority surveyed the industry in March 2019 to understand how and where AI and ML are being used, and their results indicated 80% of survey respondents were using ML. The most common application of SupTech is ML techniques, and more specifically NLP to create more efficient and effective supervisory processes.
Let us focus on the use of NLP, specifically on how it has been used by banking authorities for policy decision making during the COVID-19 crisis. AI has the potential to read and comprehend significant details from text. NLP, which is an important subset of AI, can be seen to have supported operations to stay updated with the compliance and regulatory policy shifts during this challenging period.
Use of NLP in Policy Making During COVID-19
The Financial Stability Board (FSB) coordinates at the international level, the work of national financial authorities and international standard-setting bodies in order to develop and promote the implementation of effective regulatory, supervisory and other financial sector policies. A recent FSB report delivered to G20 Finance Ministers and Central Bank Governors for their virtual meeting in October 2020 highlighted a number of AI use cases in national institutions.
We illustrate several use cases from their October report to show how NLP has been deployed specifically for the COVID-19 situation. These cases demonstrate AI aiding supervisory team in banks and in automating information extraction from regulatory documents using NLP.
De Nederlandsche Bank (DNB)
The DNB is developing an interactive reporting dashboard to provide insight for supervisors on COVID-19 related risks. The dashboard that is in development, enables supervisors to have different data views as needed (e.g. over time, by bank). Planned SupTech improvements include incorporating public COVID-19 information and/or analysing comment fields with text analysis.
Monetary Authority of Singapore (MAS)
MAS deployed automation tools using NLP to gather international news and stay abreast of COVID-19 related developments. MAS also used NLP to analyse consumer feedback on COVID-19 issues, and monitor vulnerabilities in the different customer and product segments. MAS also collected weekly data from regulated institutions to track the take-up of credit relief measures as the pandemic unfolded. Data aggregation and transformation were automated and visualised for monitoring.
US Federal Reserve Bank Board of Governors
One of the Federal Reserve Banks in the US is currently working on a project to develop an NLP tool used to analyse public websites of supervised regulated institutions to identify information on “work with your customer” programs, in response to the COVID-19 crisis.
Bank of England
The Bank developed a Policy Response Tracker using web scraping (targeted at the English versions of each authority/government website) and NLP for the extraction of key words, topics and actions taken in each jurisdiction. The tracker pulls information daily from the official COVID-19 response pages then runs it through specific criteria (e.g. user-defined keywords, metrics and risks) to sift and present a summary of the information to supervisors.
Market Implications
Even with its enhanced efficiencies, NLP in SupTech is still an aid to decision making and cannot replace the need for human judgement. NLP in policy decision is performing clearly defined information gathering tasks with greater efficiency and speed. But NLP cannot change the quality of the data provided, so data selection and choice are still critical to effective policy making.
For authorities, the use of SupTech could improve oversight, surveillance, and analytical capabilities. These efficiency gains and possible improvement in quality arising from automation of previously manual processes could be consideration for adoption.
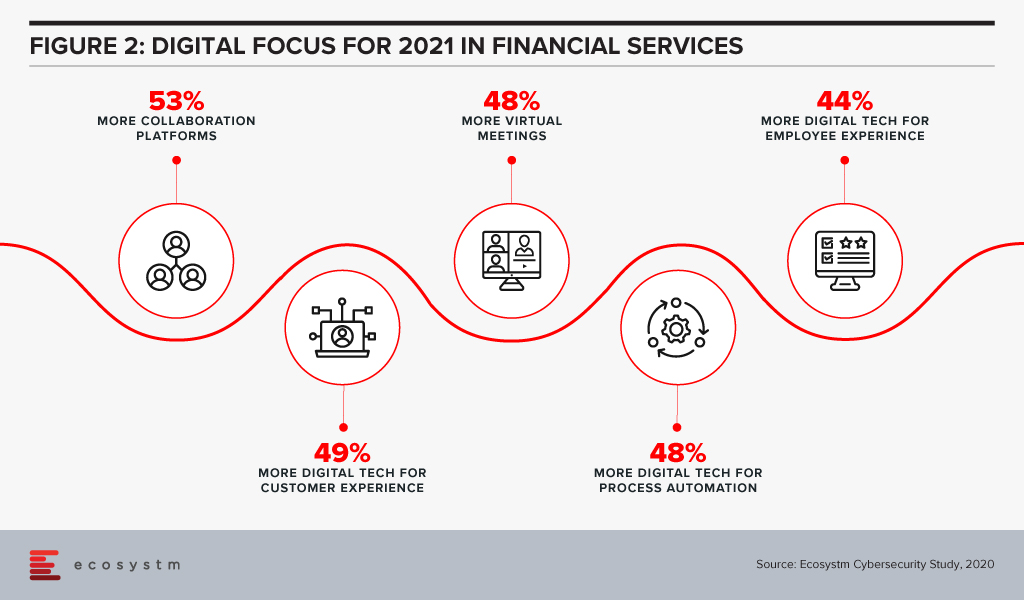
Attention will be paid in 2021 to focusing on automation of processes using AI (Figure 2).
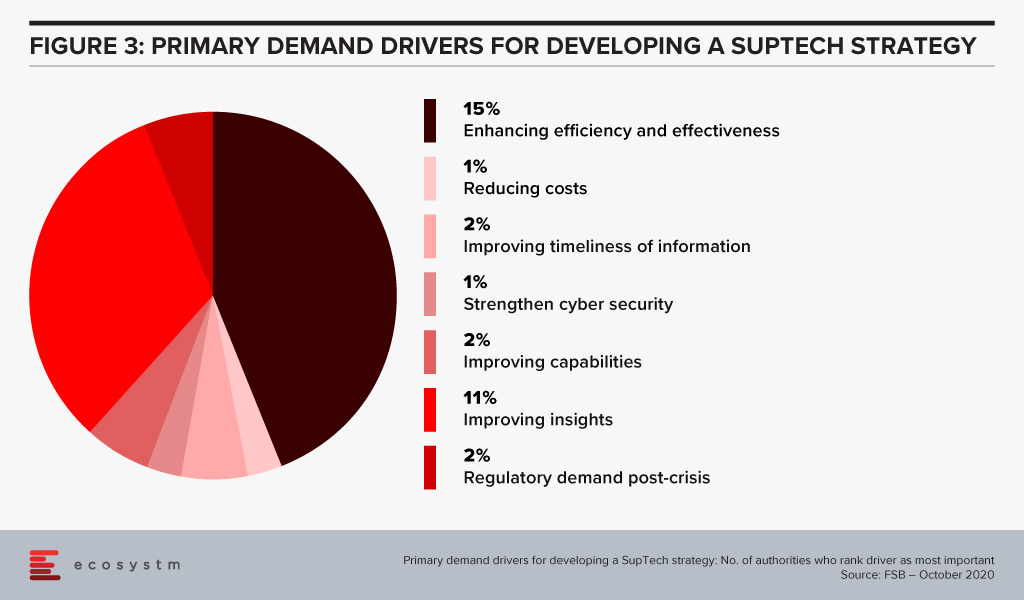
Based on a survey done by the FSB of its members (Figure 3), the majority of their respondents had a SupTech innovation or data strategy in place, with the use of such strategies growing significantly since 2016.
Summary
For more mainstream adoption, data standards and use of effective governance frameworks will be important. As seen from the FSB survey, SupTech applications are now used in reporting, data management and virtual assistance. But institutions still send the transaction data history in different reporting formats which results in a slower process of data analysing and data gathering. AI, using NLP, can help with this by streamlining data collection and data analytics. While time and cost savings are obvious benefits, the ability to identify key information (the proverbial needle in the haystack) can be a significant efficiency advantage.
Singapore FinTech Festival 2020: Infrastructure Summit
For more insights, attend the Singapore FinTech Festival 2020: Infrastructure Summit which will cover topics tied to creating infrastructure for a digital economy; and RegTech and SupTech policies to drive innovation and efficiencies in a co-Covid-19 world.

In the recently published the Top 5 Cybersecurity & Compliance Trends for 2021 report Ecosystm predicts that 2021 is when M&As will ramp up in earnest to consolidate the fragmented cybersecurity market. The pandemic has slowed down M&A activities in 2020. Early signs of what we can expect from the market when we emerge from COVID-19 can be seen in the recent acquisition of Asavie by Akamai Technologies. The market is realising the full implication of the shift to remote working and the potential of increased cyber threats – and this acquisition is a sign that larger vendors will continue to strengthen their cybersecurity capabilities by acquiring vendors, with complementary capabilities.
Asavie Enabling the Secure Office Anywhere
Asavie, headquartered in Ireland, offers a global platform that manages the security, performance, and access policies for mobile and internet-connected devices. Asavie delivers secure access to business resources for a mobile workforce – without requiring installation and management of client software. Increasing mobile workloads and Office Anywhere trends mean that the enterprise private network is no longer just PCs/laptops. All enterprise endpoints must be considered to be a part of the enterprise network – and security and authentication solutions must be able to handle this. Organisations will need to explore options where they can give seamless access to their employees without straining their IT and cybersecurity teams – a rapidly installable, scalable, and cloud-managed solution will become a necessity.
More than ever before, enterprises will have to treat all endpoints as branches of the organisation, and the Future of Work goes beyond enabling home offices. The Global CXO Study: The Future of the Secure Office Anywhere finds that 66% of IT and business leaders think of multiple locations, when they think of Office Anywhere. Employees will work wherever they get the best work experience and are most productive. Future work patterns will require that all endpoints are considered as extended branches of the organisation. This involves the ability to extend the enterprise WAN – with speed, flexibility, and security in mind – whether it is a temporary or a home office, an ad-hoc point of sales or an employee on the go. Every employee or device should be treated like a Branch of One.
Ecosystm Comments

“Akamai has been diversifying away from its well-known content delivery network (CDN) offering and has successfully built its security business offering in recent years. In 2019, the company nearly doubled its security revenue to USD 849 million from just USD 488 million in 2017. In their 3rd quarter financial results reported in end October 2020, the Cloud Security Solutions revenue was US$266 million, up 23% year-over-year.”
“The move into the mobile security segment has been timely for Akamai as enterprise application and content is moving from behind the firewall to the cloud; adding to the criticality of the cybersecurity threat management. The COVID-19 pandemic has further driven the onboarding of businesses and consumers alike, adding to significant addressable market opportunities.”
“The acquisition of Asavie is a strategic move. Asavie’s solution effectively extends the enterprise security management to incorporate mobile devices as a ‘Branch of One’ enabling CIOs and CISOs to manage security and policies the same way as traditional enterprise network resources. The growth of 5G will further drive IoT devices and a myriad of applications and use cases which will provide for a significant growth opportunity for Akamai – the acquisition of Asavie is a positive move to support this trend.”
Akamai Strengthens Intelligent Edge Capabilities
Asavie’s mobile, IoT and security solutions will integrate with Akamai’s Security and Personalisation Services (SPS) product line sold to carrier partners that embed the solution within the technology bundle sold to their subscribers. With the Asavie acquisition, Akamai intends to help their carrier partners address enterprise and mid-market customer demand for IoT and mobile device security and management services.
Ecosystm Comments

“The addition of Asavie to Akamai’s SPS product line provides synergy for the company to expand into new addressable markets for the remote workforce and internet-connected devices to deliver superior experience in a multi-cloud environment. The Global CXO Study conducted by Ecosystm found that three quarters of the organisations rate mobile security as an important or very important part of their digital transformation strategy. Secure mobile experiences will be a core element of the enterprise going forward in the post COVID-19 business environment – driven by employee needs for mobile services and corporate resources from remote locations, with superior identity and policy management, in a frictionless manner.”
“There is an opportunity for mobile service providers and mobile virtual network operators (MVNOs) to leverage the Asavie solution combined with Akamai’s strength at the edge with over 1,500 networks worldwide to offer cloud-based value-added cybersecurity services. The Global CXO Study also found that scaling of endpoint security was a major pain point for half the organisations with more than 100 branches. Service providers can become the enabler by offering services for small and medium enterprises (SMEs) to dynamically adapt their network and security services to fluctuating demand conditions.”

“Although Akamai does offer CDN services for the SME segment, the company heavily relies on service providers and carriers to address this segment in the CDN, cloud security and its burgeoning IoT Edge offerings. Asavie’s market approach is similar and its products and services portfolio appears to complement Akamai’s very well, making it a very good fit for the company. Not only will it enhance Akamai’s SME positioning on the secure connectivity space, but it will also boost its offerings for carriers in the IoT space.”
“Carriers have had a checkered history at best, in understanding and making the most of data services. Mobile Internet took off because of smartphone manufacturers (Apple) and Internet companies – not through carrier offerings. Although carriers appear to be more proactive and forward-looking with regards to IoT, they should not expect to have the foresight to see what services and business cases will make 5G and IoT truly profitable. Rather, their main focus should be on enabling the secure and flexible infrastructure that can ultimately enable others to develop the use cases. The next logical step would then be for carriers to develop IoT orchestration platforms that can manage much larger parts of the IoT value chain. If they succeed in this (and even if they don’t) it could result in a major boost for Akamai’s CDN business.”
“In other words, carriers need help with IoT and to that end, Akamai’s acquisition of Asavie may strengthen its ability to support carriers to reach that goal.”
The full findings and implications of The top 5 Cybersecurity & Compliance Trends For 2021 are available for download from the Ecosystm platform. Sign up for Free to download the report.

Running a contact centre has been extremely challenging in 2020. Contact centres have had to ensure business continuity, keep the focus on customer experience, and manage and motivate a largely remote workforce. Since the outbreak of COVID-19, not only have contact centres seen high inbound activity, but they have also had to manage agents who are dispersed and working remotely. 2020 has seen many contact centres starting, accelerating or re-focusing their digital transformation initiatives (Figure 1).
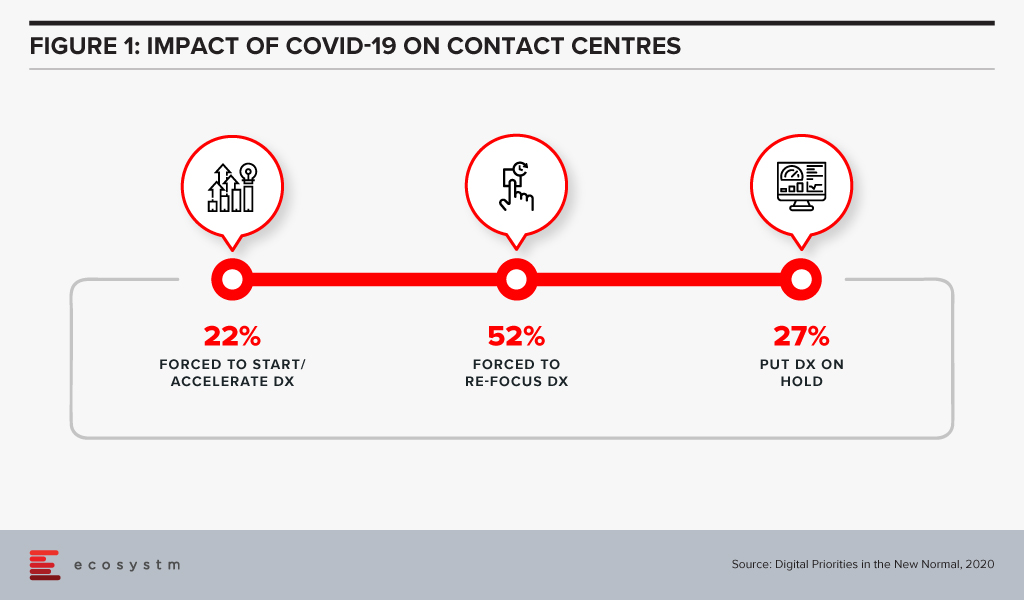
2021 will see contact centres focusing on transformation, not only to survive but also because their organisations and clients will expect more process efficiency and better customer experience. Ecosystm Advisors Audrey William and Ravi Bhogaraju present the top 5 Ecosystm predictions for Contact Centres Trends in 2021.
This is a summary of our predictions on the top 5 Contact Centre Trends for 2021 – the full report (including the implications) is available to download for free on the Ecosystm platform here.
The Top 5 Contact Centre Trends for 2021
- Remote Working Will Force Contact Centres to Re-evaluate Security Measures
Security has always been a concern for contact centre leaders. Improper data use by agents and agents breaching confidentiality are the biggest security challenges for contact centres. This has been further heightened, especially the fear of agents purposely breaching confidentiality while working from home.
Contact centres are still trying to figure out the best security measures when managing customer data, especially in the work-from-home environment. There is greater scrutiny over security and compliance measures – what agents view, how agents access the data, when agents log in and out of the system. Outsourcing providers will also have to guarantee high levels of security – a trusted relationship and defining the best practices on working from home will not be sufficient.
Many contact centres will trial different methods – from installing video surveillance cameras, desktop monitoring tools and access controls. Others will test technologies that can mask the information captured through mobile devices. This presents immense opportunities for vendors, as contact centres will rely heavily on technology to re-invent their security practices.
- Contact Centres will Invest in Conversational AI – Chatbots will No Longer be Enough
Many enterprises have rushed into deploying chatbots with expectations that these engines can solve the problem of high call volumes. The outcomes have often been poor, leaving customers frustrated and opting to interact with a live agent instead. Implementing a basic chatbot does not fully solve the problem and will force companies back to the drawing board.
Conversational AI offers a different experience by designing multiple forms of dialogues and conversations. It requires conversational design and the algorithms go through rigour from the start. The aim should be to make the channel irresistible – one that customers have confidence in, and that can reduce the need to email or call an agent. Successful uses cases have shown that conversational AI can reduce calls and repetitive queries by 70-90%. Ecosystm research finds that contact centres are ramping up their self-service capabilities and their adoption of AI and machine learning.
- Offshore Centres will Re-invent Themselves and Make a Comeback
2020 has seen contact centres in offshore locations struggle to offer services to global clients. Many of these operators have been plagued by poor internet connectivity at agents’ homes, and unfavourable home working environments. These outsourcing locations remain vital however, for multiple reasons – for example the range of services offered, agent specialisation, costs or diversity in agent profile.
Contact centre outsourcing providers will make a comeback in 2021 and we can expect new models to appear. Many providers across the globe have been running successful work-from-home only operations for years – other outsourcing providers will learn from these best practices. Organisations will find that bringing jobs back to high-cost locations will incur more costs. A full onshore model may not be the right model for business continuity, and organisations will prefer to have back-up locations to ensure continuity of services if another pandemic or catastrophe happens. Organisations will want to see the outsourcing providers offer them a choice of location – they will prefer some services to be delivered from offshore locations and others to remain onshore.
- Digital and Mobile will be the Cornerstone of Deeper Customer Engagement
COVID-19 has changed how customers want to be served, and organisations have had to re-evaluate how they use their channels – e.g. email, web, chat and voice. Customer profiles and expectations have changed over the year and they are more digital savvy and are more likely to interact with brands through digital and mobile apps. They will expect a single point of interaction – for their enquiries and to complete their transactions. For instance, they will expect to chat while filling up shopping carts. Introducing chat capabilities within mobile apps is a good way to impress customers – this can be an effective way to push promotions and upsell. Capabilities such as the ability to directly place a call from a website will make the customer experience exceptional. Customers will expect to move between channels easily when interacting with a brand.
- Workplace Collaboration Will be Fully Integrated into Contact Centres
Contact centres will reassess their business and talent models. The focus on employees will be in two major areas:
- Productivity. The contact centre floor dynamics have changed in how agents are spread out across outsourcing locations and in-house contact centres. Agents are no longer located in the same room or floor and do not have access to their usual way of work – continual training, digital signage that provides guidance and demonstrates KPIs, conversations with supervisors, managers, and team members for guidance or assistance, easy access to back-office functions and so on. This can impact their productivity.
- Engagement. Contact centre staff often work in high-stress environments -chasing sales targets and deadlines, handling complaints – and it is important for managers and supervisors to be able to engage and motivate them constantly. Remote working has further exacerbated the stress for those agents who do not have a conducive working environment at home.
Contact centres will increasingly look to workplace collaboration platforms and tools to improve employee productivity and experience.

Authored by Alea Fairchild and Audrey William
Video conferencing company Zoom hosted its virtual Zoomtopia user conference lasts week. Given the attention the company has received as the de-facto standard video communication service for the many stranded work-from-home folks, Zoom has been using the event to launch a number of new products. This includes bringing into general availability its OnZoom events platform and marketplace, and introducing Zapps which brings apps from other providers into the Zoom experience.
ZaaP!
In this age of work-from-home connectivity, we are all asked to multi-platform depending on customer preference, company standards and choice of scale-out from a licensing perspective. But will video-led unified communications help position Zoom to be the infrastructure platform of choice of the workforce? Will Zoom as a Platform (ZaaP!) become a well-used phrase to discuss unified collaboration infrastructures?
The agenda of Zoomtopia, covering healthcare, government, financial services, sales engagement, blending learning in education, mindfulness, CSR, and a whole gambit of other vertical topics, demonstrates a virtual play to highlight use cases where other platforms have focused on the horizontal aspect of productivity.
If you compare Microsoft’s horizontal approach with Cisco’s networking approach, both come from places of productivity. Zoom, being video-led and UC oriented, comes from a place of communication and collaboration. Is collaboration now the real driver for the future of work?
Zoom connects the dots with these two product introductions. Zapps is designed to link productivity tools directly into the Zoom experience for user access to multiple applications from the platform. OnZoom allows hosts to run one-time events or event series with up to 100 or 1,000 attendees (depending on their license) and sell tickets for them. Zoom is also integrating the ability to receive donations through events via Pledgeling. Think a combination of EventBrite meeting GoFundMe meeting Facebook Events.
Zooming Ahead
With the wide variety of activities during this social distancing period around the world that have been Zoom-powered, familiarity leads to experimentation and early adoption.
Without using the word ‘portal’ – Zoom as a Platform (ZaaP!) enforces the drive for a main infrastructure for live interaction via video as the main means of communication over written material or pre-recorded media materials. And many of us are video-led, more than ever.
Zoom is scaling rapidly. When it started out many years ago, they were known as a company that offered video sessions for free and everyone was wondering who this new kid on the block was. In a span of a few years, they have become a powerhouse.
The announcement of OnZoom is something that marketeers will take note of. Many marketeers are Zoom users but could be using other platforms for hosting events. The solution will have in-built tools for selling tickets, scheduling, gifting tickets, promotional activities, etc. Zoom is thinking about video and layering that with added functionality to run a large-scale event. You can see them going into using AI to churn out rich analytics on attendees, attendance rates, effectiveness of campaigns and so on. All of a sudden it is about hosting an event with in-built rich features plus analytics so events can be run better. They are reaching a new audience and making it a fully built all-purpose solution for event organisers and marketeers.
Security Front and Centre
Ecosystm research shows that security has been a key component in organisation’s COVID-19 responses – and rightly so (Figure 1).
While Zoom received some negative publicity this year around security, they were quick to admit the issues and made incremental changes in the subsequent months including an acquisition. With E2EE, no third party including Zoom is provided with access to the meeting’s private keys. Zoom’s E2EE ensures that communication between meeting participants using Zoom applications is encrypted using cryptographic keys known only to the devices of those participants. Zoom is starting to penetrate larger accounts and the security aspect is important as it is the top of the mind discussion for every business leader.
Ecosystm Comments
With the hybrid work model evolving between home and work, and work patterns changing, one thing that is going to stay is the use of video and collaboration tools and it is only going to accelerate (Figure 2).
What Zoom is doing well is how they take workflows and APIs seriously, making productivity flow into UC and UX, and not the other way around.
With longer work hours becoming a norm, growing instances of emotional stress and mental fatigue, UX becomes paramount. Knowledge workers want to seamlessly move between workflows and still find the experience simple and not tiring. Zoom is building on that vision as a platform enabler and infrastructure provider.

There has been a heightened interest in the cloud in EMEA in recent times, triggered by several regional and country level announcements.
The European Union (EU) founded the GAIA-X Foundation to build a unified system of cloud and data services to be protected by EU Laws – including GDPR, the free flow of non-personal data regulation and the Cybersecurity Act. France and Germany kicked off the GAIA-X cloud project last year and the system is open for participation to national and European initiatives for exchange of data across industries and services such as AI, IoT and data analytics. GAIA-X took another step towards becoming a real option for European organisations with the establishment as a legal entity in June. Founding members of GAIA-X include Atos, Bosch, BMW, Deutsche Telekom, EDF, German Edge Cloud, Orange, OVHcloud, SAP, and Siemens. Non-European providers, such as AWS, Microsoft, Google, and IBM will also have the opportunity to join GAIA-X. The UK Crown Commercial Service (CCS) has also been entering into agreements with public cloud platform providers to encourage increased cloud adoption in cash-strapped public sector organisations. It is a good time to evaluate organisations’ perception on cloud and their adoption patterns.
Ecosystm research finds that while most organisations have migrated at least some simple workloads to the cloud, the sophistication of these systems ranges from SaaS deployed as shadow IT, all the way up to cloud-native applications that are core to a digital business strategy. When asked about the maturity of their cloud deployments, 36% of organisations in EMEA consider themselves advanced, leaving the remaining 64% with more basic environments. These figures vary by business size with only 31% of SMEs considering their deployments advanced, rising to 40% for large enterprises.
Cloud technology providers should segment the market according to the maturity of their client’s systems. Those in the early stages of modernising their infrastructure will be seeking different benefits and will have different concerns than those already using cloud to underpin their digital transformation.
In the mature economies in the region, 75% of those with advanced deployments, considered improved service levels and agility as a key benefit of cloud. These organisations have moved beyond simply replacing legacy systems with cloud infrastructure and now look to the IT department to provide a platform on which new, client-facing services can be delivered. In the emerging economies, the most-reported benefits of cloud are flexibility and scalability, and standardised systems, both at 68% of respondents. These could be viewed as benefits expected from organisations not as far along in the cloud journey. The benefit of reduced IT costs was important in both mature EMEA (67%) and emerging EMEA (62%).
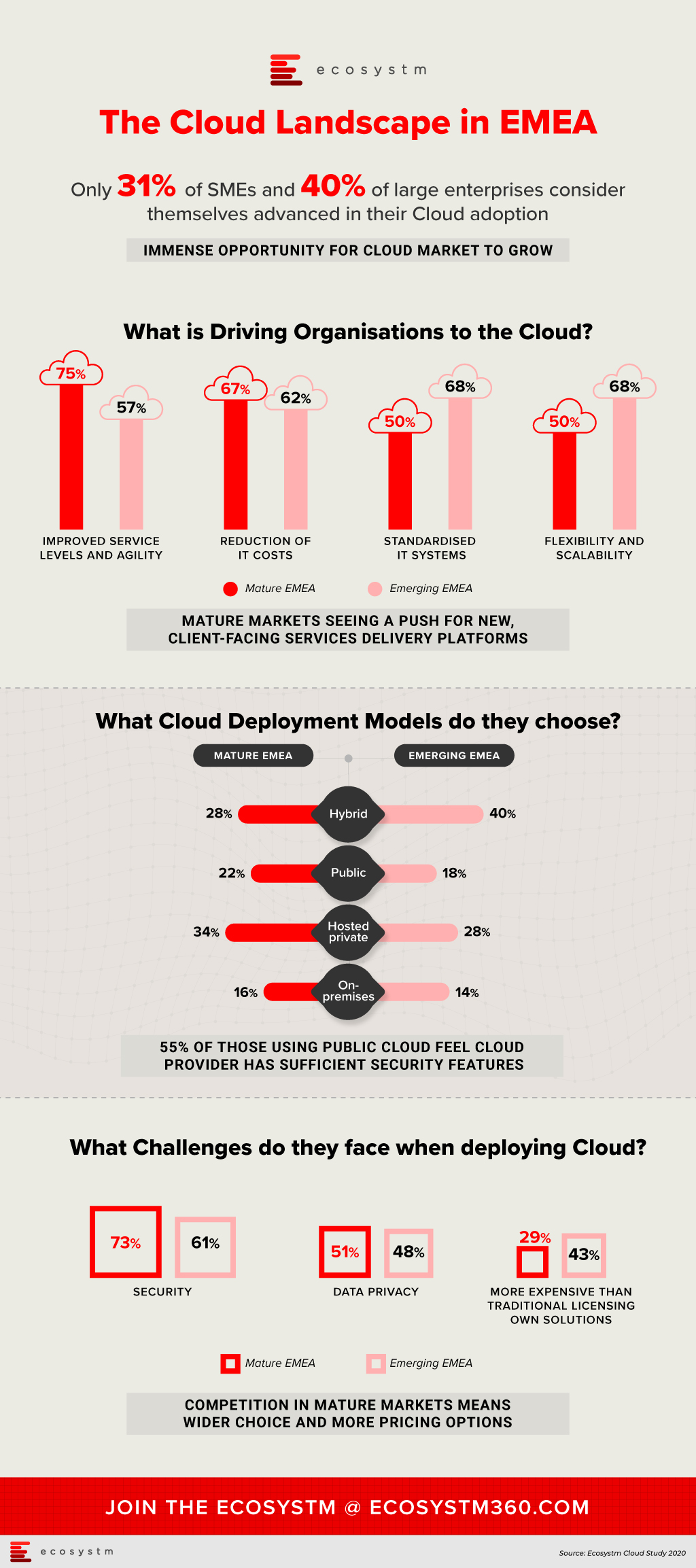
Looking at those who consider their cloud deployments as still basic, security is the leading challenge to greater adoption and by a large margin. Of those respondents in mature EMEA, 73% cited security as a key challenge, more than 20 percentage points higher than the next greatest difficulty. In emerging EMEA, a similar trend was evident, with 61% of respondents considering security as a key challenge. Moreover, data privacy is the second-most significant concern for those who do not consider their cloud deployments advanced. This was visible in both mature EMEA (51%) and emerging EMEA (48%). As organisations look to shift more critical workloads to the cloud, they will be increasing their attack surfaces and at the same time will face greater consequences if a breach does occur.
Services providers targeting organisations with less developed cloud environments should include security early in the conversation to push them along to the next stage of maturity.
The challenge that varied most according to market maturity and business size was the concern that cloud-based services were more expensive that traditional licencing or in-house solutions. Only 29% of respondents with basic cloud deployments in the mature economies, held this view, while in emerging economies the figure rose to 43%. Competition in those mature markets has in some cases put pressure on prices or at least resulted in wider choice. While 29% of SME respondents considered cost a key challenge, 41% of large enterprises did. Migrating larger, more complex environments to cloud will be viewed as more costly than the status quo due to organisational inertia.
The perception that cloud can be more costly, provides an opportunity for cloud management including expense optimisation services.
Organisations looking to move from a basic cloud environment to one that adopts a cloud-first model should begin with a maturity assessment. Understand what your systems will look like at the next stage, what the benefits will be, and what are the risks. More importantly, decide on the long-term business goal that you are trying to achieve, particularly how IT can be a critical player in the organisation’s digital strategy.
Note: Mature economies – France, Germany and the UK/ Emerging economies – Middle Eastern countries, Russia and South AfricaIdentify emerging cloud computing trends that can help you drive digital business decision making, vendor and technology platform selection and investment strategies.Gain access to more insights from the Ecosystm Cloud Study.

Last week, trading on the New Zealand Exchange (NZX) was disrupted on four consecutive days as a result of a sustained cyber-attack on to push market updates to the public as their website crashed and as a precautionary measure, NZX halted the trading sessions. Ecosystm Principal Advisor, Andrew Milroy says, “The recent NZX attack overwhelmed its public-facing NZX.com website and its Market Announcement Platform (MAP). This meant that investors could not see company announcements in real-time, preventing NZX from complying with regulatory requirements for continuous disclosure.”
The attacks which began on Tuesday came from overseas and made NZX struggle in recovering connectivity, over a five-day period. The cyber-attackers targeted NZX through distributed denial-of-service (DDoS) attacks which is a common way to overwhelm the network with sheer amount of traffic until it disrupts the services.
Milroy says, “It is not clear yet clear who launched the attack, but it is likely to be either an extortion attempt by a large cyber gang or a nation state attack. The attack was a very large, persistent, and sophisticated volumetric DDoS attack. A typical response to such an attack is to increase network bandwidth. However, additional bandwidth is becoming less effective at preventing DDoS attacks. DDoS attacks are getting larger and no amount of bandwidth can address the largest attacks, some of which exceed 1Tbps. DDoS attackers are increasingly focusing on the harder to protect application layer, rather than the network layers.”
The Government Communications Security Bureau (GCSB), network provider Spark, and international bodies provided assistance to NZX to mitigate the attack. Milroy adds, “NZX has also turned to Akamai for additional DDoS protection. Akamai’s Kona Site Defender is understood to be the solution being used. The product is designed to deflect network-layer DDoS traffic and absorb application-layer DDoS traffic at the edge. Mitigation capabilities aim to protect against attacks in the cloud.”
Growing Importance of Government Advisories and Investments
In November 2019, CERT NZ warned financial organisations of several global attacks including ransomware. The attacks were reportedly from Russia-based hacking groups. In an advisory, CERT NZ suggested businesses should implement DDoS protection services, and check network ports connected to avoid vulnerabilities and not pay any ransom to cybercriminals.
Following the CERT NZ warning last year, and considering the recent cyberattacks, GCSB has issued a security advisory to all businesses in New Zealand to be cautious on cyber incidents such as DDoS and ransomware attacks. The advisory comes from the GCSB’s National Cyber Security Centre. This is particularly aimed at small businesses that might have limited cybersecurity resources. The agency has asked them to report such incidents to Cert NZ. Advice includes:
- Approaching cybersecurity services providers to immediately implement any responsive actions (warning that organisations might incur additional fees)
- Temporarily transferring online services to a cloud-based hosting service
- Avoiding the disclosure of the IP address of the origin web server, and using a firewall, if using a content delivery network
- Using a DDOS mitigation service for the duration of attacks, in case they face attacks
- Disabling functionality or removing content from vulnerable online services
As a part of the New Zealand government’s cybersecurity strategy, last year the Government announced the allocation of USD 5.38 million to focus on security over the next four years, on top of USD 6.26 million funding for CERT NZ. The attack landscape and frequency has since increased in the aftermath of COVID-19.
Milroy says, “It will become increasingly important for governments the world over to make a concerted effort to protect their critical infrastructure, data assets and especially empower their SME communities with the right cybersecurity measures and timely guidance.”

Organisations are on a fast track to digitalisation. The Ecosystm Digital Priorities in the New Normal study finds that 60% of organisations anticipate increased use of digital technologies for process automation, even after the COVID-19 restrictions are lifted. One of the key challenges that these organisations will face is the lack of internal digital skills – especially in emerging technologies. One of the success metrics of any technology adoption is employee uptake. Without the necessary skills or understanding of the benefits of emerging technology, employees will largely shy away from digital offerings, even the ones that will make their work more efficient and their lives easier.
Organisations are realising the value of making their workforce future ready.
DBS Instilling Company-Wide Digital Culture
Far-sighted companies are collaborating with technology vendors and professional training providers to promote tech awareness and education to futureproof their workforce. DBS Bank in Singapore has collaborated with AWS to train and upskill 3,000 employees – including the leadership team – with AI and machine learning skills through gamification in a DBS x AWS DeepRacer League.
The AWS DeepRacer Leagues have been previously organised in several parts of the world, but the DBS x AWS DeepRacer will be the first to be organised at this scale. The league will enable DBS employees to get their hands-on AI and machine learning tutorials online. They will then have the opportunity to test out their new skills in programming a 3D racing simulator and iteratively fine-tune their models and compete with each other. The learning program is entirely cloud-based and aims to ingrain digital skills in the workforce.
DBS has won several accolades for their digital transformation and innovation initiatives, and they continue to experiment with emerging technologies. In 2019, DBS digitalised and simplified end-to-end credit processing, setting the foundation for advanced credit risk management using data analytics and machine learning. They have also deployed an AI-powered engine for self-service digital options to its retail banking customers. Taking their employees along with them on this journey is a wise move.
Ecosystm Principal Advisor, Ravi Bhogaraju says, “With the increasing use of automation, AI and machine learning, the nature of work and businesses is transforming rapidly. This is creating opportunities for processes to be automated and increasing the use of AI and Deep Learning into the business processes of the organisation. Industry value chains are transforming – AI and machine learning is adding automation, analytics and predictive intelligence to the portfolio. The recent news of DBS and AWS partnering to upskill the bank’s workforce underscores the value of creating a future ready workforce.”
“Such upskilling efforts add industry-specific context to make them more effective. BCG refers to this as ‘Human + AI’. A recent study from BCG and MIT shows that 18% of companies in the world that are pioneering AI are making money with it. Those companies focus 80% of their AI initiatives on effectiveness and growth, taking better decisions – not replacing humans with AI to save costs.”
Government Focus on Digital Skills Upgrade
This week, Singapore also saw another initiative to bridge digital skills gaps – this time from the public sector. In 2018, the Government launched its Smart Nation Scholarship program to attract and nurture talent, and later involve them in various departments to drive Singapore’s Smart Nation initiatives. The most recent Smart Nation Scholarship program 2020 attracted 723 applicants (17% more than the previous year). This is a slightly different approach, aimed at attracting digital native employees and mentoring them for digital leadership. After completing their studies, the 15 scholarship recipients are set to join public sector agencies such as Cyber Security Agency of Singapore (CSA), Government Technology Agency (GovTech), and Infocomm Media Development Authority (IMDA), to give the younger generation an opportunity to co-create the country’s Smart Nation vision.
Bhagaraju says, “Both private and government institutions are working to enhance workforce skills, improve marketability and making the workforce future ready. Industry 4.0 and the digital revolution have created the need to address the skill gaps that have arisen. Government programs such as the Skills Future program in Singapore, Malaysia’s HRD upskilling program, and the EU-28 European Digital initiative are all making a sustained effort to promote lifelong learning and acquisition/upgrading of skills for their respective citizens with quite successful results, that will have long-term impacts.”











