Telstra, Australia’s leading telecom provider has revealed its plans to split into 3 different units which would operate under the umbrella of the Telstra Group. The restructuring – scheduled to be completed by 2021 – is said to be the telecom giant’s biggest restructuring since 1997. The primary reason behind the move appears to be to spin off its infrastructure assets to realise their full value as competition intensifies.
In 2018, the Telstra2022 plan defined a four-pillar strategy to improve business, network superiority, cost improvements and respond to market dynamics for the next three years including the establishment of InfraCo and Global Business Services. Telstra established its standalone infrastructure unit, Telstra InfraCo to hold its fixed network assets. As a part of its recent announcement, Telstra’s infrastructure business InfraCo will split into two units – InfraCo Fixed which will run and manage Telstra’s physical infrastructure assets including data centres, ducts, fibres, undersea cables, and exchanges; and InfraCo Towers which will own and operate Telstra’s mobile towers and infrastructure. Meanwhile, the third unit ServeCo will focus on products and services for the consumer and retail businesses. The company is also investigating ways to push into renewable energy, with plans to exploit its renewable energy investments to re-sell cheaper energy to its customers.
This restructure, should it go ahead as described, is likely to be the biggest legacy that the current CEO, Andy Penn, leaves on the business. Recent CEOs have left a significant legacy on Telstra. Sol Trujillo – who admittedly had a rocky relationship with the Australian Government, which culminated in the conception of the National Broadband Network (NBN) – drove significant changes in Telstra; rationalising mobile and fixed network investments, driving focus back into the business and building an economically rational business. David Thodey was the great peacemaker, driving pride back into the Telstra staff and customers; he turned Telstra into one of the most customer-centric businesses in Australia in his time, laying the foundation for its ongoing success. Andy Penn has made some significant changes to Telstra, further reducing the cost base to turn it into a more competitive business – but until now, he has not significantly transformed the core business.
This changes now. Telstra ServeCo will build on the customer-obsessed culture of the Telstra sales and service business – one that consistently scores above market average for NPS in both the business/enterprise and the consumer markets. One can even envision a day in the future where ServeCo will be in a position to sell the best network solutions and services in Australia – some of which might not even be owned or controlled by InfraCo. It already does that with the NBN – this may extend to reselling other telecom services too.
InfraCo Fixed will build on the strong engineering legacy that Telstra still has – and will give it the chance to flourish – and not be dictated by customer buying cycles. Ideally investment cycles can be separated from direct customer revenue, and the company can rebuild the network lead that it has traditionally experienced, but which has been eroded over the past 3-4 years (in mobile by Optus and in fixed telecoms by NBN).
InfraCo Towers should be well-positioned to become the core tower provider in Australia. This business makes the most sense to spin off in the medium term. The buildout of multiple – nearly identical – tower networks by the three major 4/5G providers is wasteful and inefficient. 5G in particular, requires a very different tower footprint than 3G or 4G – so having a single provider of shared tower infrastructure will reduce costs for all telecom providers while creating a healthy business for shareholders. As an independent provider of towers, InfraCo Towers should always be the most affordable option – Optus, Telstra and Vodafone would be foolish to attempt to replicate and manage their own similar tower infrastructure.
The NBN-Telstra Dynamics
While Telstra dominates the Australian telecommunications market, their business is also under pressure due to the state-owned NBN. In 2019, Communications Minister Paul Fletcher ruled out selling the NBN to Telstra. However, the new structure has likely been designed with this in mind – with perhaps the option to spin off the InfraCo Fixed unit and merge this with a privatised NBN or perhaps to even the separation of the business units enough to satisfy a future government of the merits of selling NBN to Telstra and merging it with the InfraCo Fixed unit. The question surely needs to be asked what the difference is between a private business with a monopoly on home broadband access and Telstra having that monopoly?
This restructure will help Telstra build a telco for the next ten years. One where agility will be core to its success. The challenge – like with any big transformation – will be to take the employees and the customers on that journey. Employees need to believe that this structure is the right one and that their skills are required and relevant. Customers need to see benefits from this restructure too – ideally, they will see that the service promise of Telstra is delivered in the network and capabilities. Hopefully, they will see a stronger Telstra that can continue to drive the levels of innovation and investment that digitally savvy customers demand.

Telstra and Microsoft have extended their partnership to jointly build solutions harnessing the capabilities of AI, IoT, and Digital Twin technologies in Australia. The partnership will also enable both companies to work on sustainability, emission reduction, and digital transformation initiatives.
The adoption of cloud and 5G technology is already on the rise and creating opportunities across the globe. The Microsoft-Telstra partnership is set to bring together the capabilities of both providers for businesses in Australia and globally. Their focus on AI, IoT, cloud and 5G will enable Australia’s developers and independent software vendors (ISVs) to leverage AI with low latency 5G access to drive efficiency, and enhance decision making. This will also see practical applications and new solutions in areas like asset tracking, supply chain management, and smart spaces to enhance customer experience.
Technology Enhancing the Built Environment
Microsoft Azure and Telstra’s 5G capabilities will come together to develop new industry solutions – the combination of cloud computing power and telecom infrastructure will enable businesses and industries to leverage a unified IoT platform where they can get information through sensors, and perform real-time compute and data operations. Telstra and Microsoft will also build digital twins for Telstra’s customers and Telstra’s own commercial buildings which will be initially deployed at five buildings. Upon completion, the digital twin will enable Telstra to form a digital nerve centre and map physical environments in a virtual space based on real-world models and plot what-if scenarios.
Telstra CEO, Andy Penn says, “If you think about the physical world – manufacturing, cities, buildings, mining, logistics – the physical world hasn’t really been digitised yet. So, how do you digitise the physical world? Well, what you do is put sensors into physical assets. Those sensors can draw information around that physical asset, which you can then capture and then understand.”
Ecosystm Principal Advisor, Mike Zamora finds the comment interesting and says, “It isn’t so much that the physical world is digitized – it is more about how digital tools enhance and enable the physical world to be more effective to help the occupier of the space. This has been the history of the physical space. There have been many ‘tools’ over time to help the physical world – the elevator in the late 1880s enabled office buildings to be taller; the use of steel improved structural support, allowing structural walls to be thinner and buildings taller. These two ‘tools’ enabled the modern skyscraper to be born. The HVAC system developed in the early 1900s, enabled occupants to be more comfortable inside a building year-round in any climate.”
“Digital tools (sensors, etc) are just the latest to be used to enhance the physical space for the occupant. Digital twins enable an idea to be replicated in 3D – prior to having to spend millions of dollars and hundreds of man hours to see if a new idea is viable. Its advent and use enable more experimentation at a lower cost and faster set up. This equates into a lower risk. It is a welcomed tool which will propel the experimentation in the physical world.”
Talking about emerging technologies, Zamora says, “Digital twins along with other digital tools, such as 3D printing, AI, drones with 4K cameras and others will enable the built environment to develop at a very quick pace. It is the pace that will be welcomed, as the built environment is typically a slow-moving asset (pardon the pun).”
“Expect the Built Environment developers, designers, investors, and occupiers to welcome the concept. It will allow them to dream of the possible.”
Telstra and Microsoft – Joint Goals
Telstra and Microsoft have partnered over the years over multiple projects. Last year, the companies partnered to bring Telstra’s eSIM functionality to Windows devices for data and wireless connectivity; they have also worked on Telstra Data Hub for secured data sharing between data producers, businesses and government agencies; and most recently collaborated on Telstra’s exclusive access to Xbox All Access subscription service to Australian gamers with the announcement of Microsoft’s Xbox Series X and Xbox Series S gaming consoles expected to release in November.
This announcement also sees them work jointly towards their sustainability goals. Both companies are committed to sustainability and addressing climate change. Earlier this year, Microsoft announced its plans to be carbon negative by 2030, while Telstra has also set a target to generate 100% renewable energy by 2025 and reducing its absolute carbon emissions by 50% by the same time. To enable sustainability, Telstra and Microsoft are exploring technology to reduce carbon emissions. This includes further adoption of cloud for operations and services, remote working, and piloting on real-time data reporting solutions.
Telstra also aims to leverage Microsoft technology for its ongoing internal digital transformation, adopting Microsoft Azure as its cloud platform to streamline operations, and infrastructure modernisation, including transition from legacy and on-premise infrastructure to cloud based applications.

Smarter buildings and public facilities have long been of interest to architects and developers. Innovators can see that the promise of intelligent data used for spatial design can transform how we work, live and play.
How can Big Data be used for intelligent building design? There are a consortia of companies trying to figure this out together. I will discuss the Building 4.0 Co-operative Research Centre (CRC) in Australia.
I have already been examining the new approaches to using big data in facilities management. This is done by developing smarter office spaces, embedded with devices employing Ambient Intelligence (AmI). Research looked at how the intelligent use of big data contributed to building an environment with greater energy efficiency, optimised space utilisation, enhanced workplace experience and occupants’ comfort. This includes sound masking, the use of lighting for enhance environments, and sensors for occupancy for hygiene controls.
Ambient Intelligence (AmI)
AmI refers to electronic environments that are sensitive and responsive to the presence of employees, residents or visitors. These environments can have ecosystems (pun intended) of different IoT devices communicating with each other.
There is a real emphasis here on edge computing, sensors and other IoT devices, and building intelligence into the edge for near real-time decision making closer to where the problem may sit. Ecosystm research finds that construction firms focus a significant amount of IoT investment for building management and energy management (Figure 1).
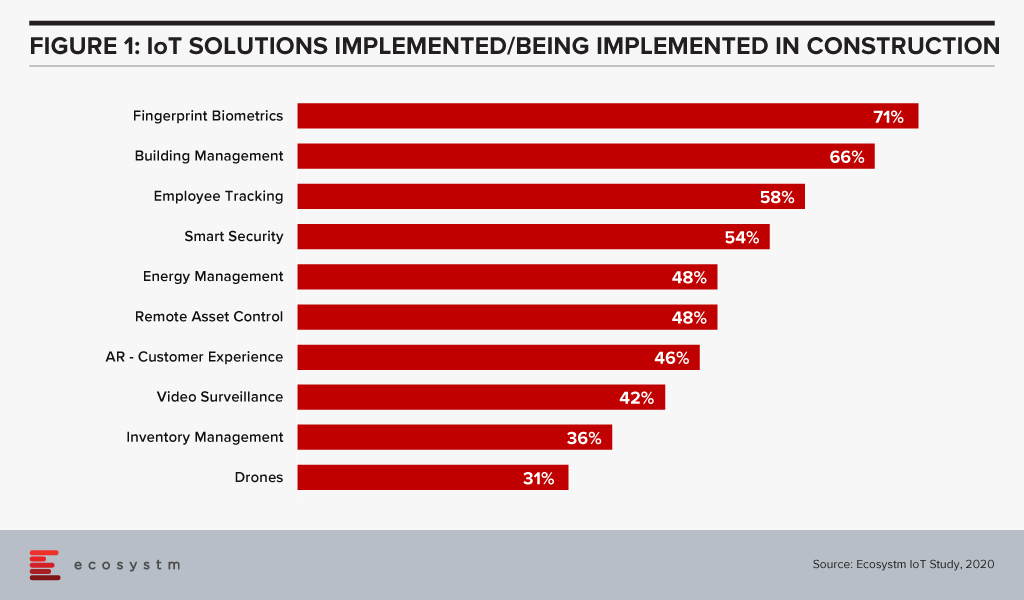
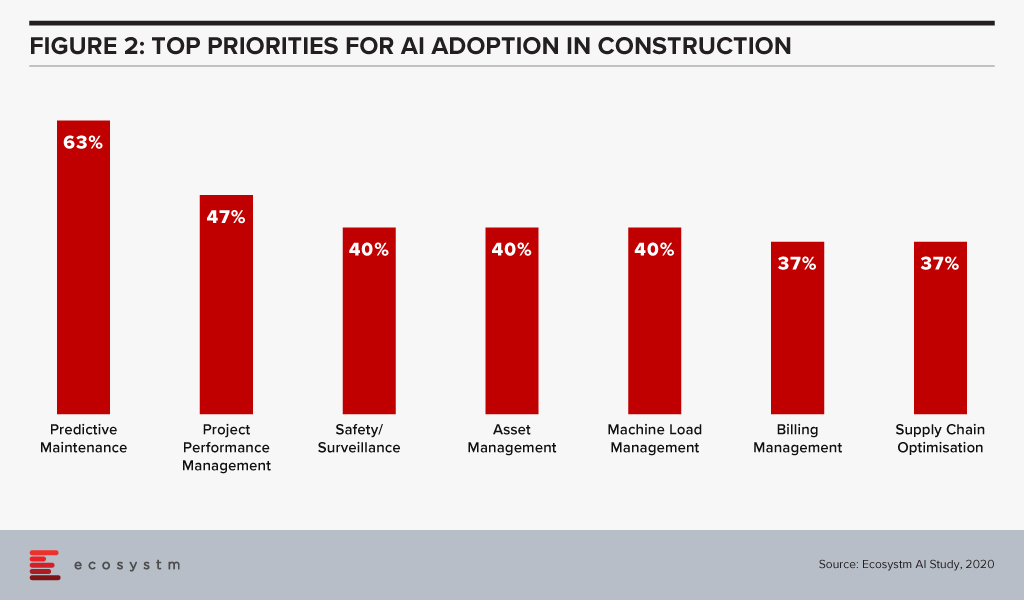
For example, if an HVAC system is on the verge of malfunction, the system could send a message for a repair intervention. When it comes to AI, predictive maintenance and surveillance are two of the leading use cases in the construction industry (Figure 2).
Building 4.0 Co-operative Research Centre (CRC)
In Australia, this push for sustainable and smarter building development is being driven by a consortium of companies looking at Big Data and infrastructure development for buildings. This year, the Building 4.0 Co-operative Research Centre (CRC) has been awarded a USD 19.5 million grant to focus on medium to long-term industry-led collaborations that can assist in driving the growth of new industries. The Australian building and construction industry is a major economic engine that contributes 13% of GDP and employs over 1.4 million Australians. Development of the Building 4.0 CRC makes sense and is timely given the current pandemic and economic conditions.
Part of its research program focus on develop new building processes and techniques through leveraging the latest technologies, data science and AI to ultimately improve all aspects of the key building phases. Their overall ecosystem is designed for enablement of several use cases (Figure 3).
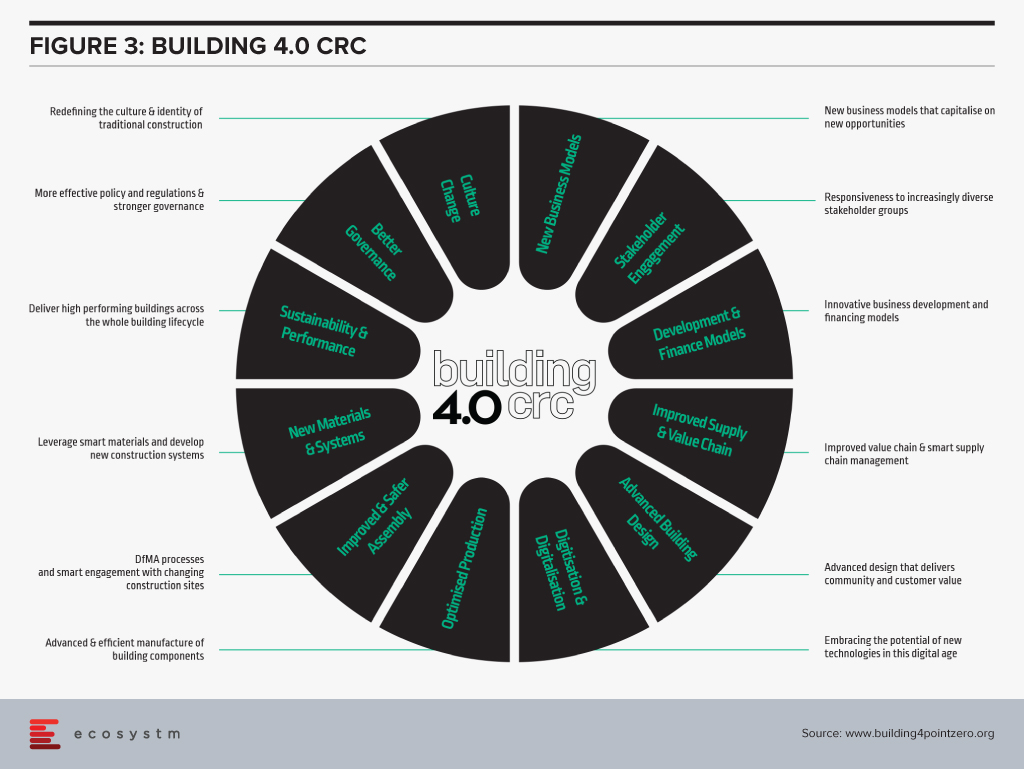
The Building 4.0 CRC’s principle aims are “to decrease waste; create buildings that are faster, cheaper, and smarter; and capture new opportunities by facilitating collaborative work between stakeholders across the whole value chain in cooperation with government and research organisations.”
Green Star, the rating system which was created by Green Building Council of Australia (GBCA) in 2003, rates the sustainability of buildings, fit outs and communities through Australia’s largest national, voluntary, holistic rating system. The GBCA is a partner organisation in the Building 4.0 CRC – as are many other major organisations in construction and trade, all pulling together here, for innovative efforts for the industry.
Where might the Building 4.0 CRC effort make an impact? Its collaborative structure of industry, academia, vocational trade organisation and governmental bodies harness innovative ideas to transmit them to transformative practices of industry and construction partners.
To be smarter, one must work smarter and more efficiently. A consortia such as this pulls the best minds together to try to accelerate industry efforts for intelligent design with data.

The National Australia Bank (NAB) and Microsoft announced a strategic partnership last week, to develop and architect a multicloud environment to be used by both NAB and its New Zealand counterpart, Bank of New Zealand (BNZ).
The five-year partnership will involve Microsoft and NAB sharing development costs and investments to migrate around 1,000 out of 2,600 applications from the NAB and BNZ stacks, on Microsoft Azure. By 2023, NAB aims to run 80% of its application on the cloud, build a robust cloud foundation, and enable customers to access applications and services on the cloud.
The partnership aims to support NAB’s commitment to continuous improvement and innovation, leveraging the Microsoft global engineering team. It also involves setting up of the NAB Cloud Guild program, where Microsoft will train 5,000 NAB and BNZ technologists to equip them on cloud and allied technology skills.
NAB and Microsoft have previously collaborated to improve the experience for NAB customers, through cloud-based applications. NAB’s cloud-based AI powered ATM was the result of a proof-of-concept (PoC) developed on Microsoft Azure’s cognitive services, in 2018. It involved general ATM security captures along with facial biometrics to enable customers to withdraw cash without a card or a phone.
Besides the partnership with Microsoft, NAB also uses Google Cloud for multicloud workloads as well as AWS for its AI competencies and resources across platforms. In February, NAB launched an AI-based voice service to boost the bank’s contact centre experience along with AWS.
Ecosystm Comments
Ecosystm Principal Advisor, Tim Sheedy says, “If ever there was a sign that multicloud is the predominant approach for businesses, this is it. NAB is a big AWS client – in Australia and New Zealand. They lead the way for businesses in training thousands of employees on AWS technologies through their Cloud Guild. But now Azure is also developing a strong foothold in NAB – the public cloud services market is not a one-horse race!”
“Many businesses that have standardised on – or preferred – a single cloud vendor will find that they will likely use multiple cloud environments, in the future. The key to enabling this will be the adoption of modern development environments and architectures. Containers, microservices, open-source, DevOps and other technologies and capabilities will help them run their applications, data and processes across the best cloud for them at the time – not just the one that they have used in the past.”
Sheedy thinks, “NAB’s competitive advantage will not come from whether they are using AWS or Azure – it will come from the significant time and effort they are investing in giving their employees the skills they need to take advantage of these environments to drive change at pace. Too many businesses are increasing their cloud usage without making the necessary investments to upskill their employees – if you know you are planning to spend more on the cloud, then start now in reskilling and upskilling your staff. There is already a real shortage of cloud skills and it is only going to get worse.”
Gain access to more insights from the Ecosystm Cloud Study

Last week, the Australia Government announced that they have been monitoring persistent and increasing volumes of cyber-attacks by a foreign state-based actor on both government and private sector businesses. The Australian Cyber Security Centre (ACSC) reported that most of the attacks make use of existing open-source tools and packages, which ACSC has dubbed as “copy-paste compromises”. The attackers are also using other methods to exploit such as spear phishing, sending malicious files and using various websites to harvest passwords and more, to exploit systems.
Cybercrime has been escalating in other parts of the world as well. The World Health Organisation (WHO) witnessed a dramatic increase in cyber-attacks directed with scammers impersonating WHO personnel’s official emails targeting the public. The National Cyber Security Centre (NCSC) in the UK alerted the country’s educational institutions and scientific facilities on increased cyber-attacks attempting to steal research associated with the coronavirus. Earlier this month, the Singapore Computer Emergency Response Team (SingCERT) issued an advisory on potential phishing campaigns targeting six countries, including Singapore that exploit government support initiatives for businesses and individuals in the wake of the COVID-19 crisis.
Such announcements are a timely reminder to government agencies and private organisations to implement the right cybersecurity measures against the backdrop of an increased attack surface. These cyber attacks can have business impacts such as theft of business data and destruction or impairment to financial data, creating extended business interruptions. The ramifications can be far-reaching including financial and reputational loss, compliance breaches and potentially even legal action.
A Rise in Spear-Phishing
In Australia, we’re seeing attackers targeting internet-facing infrastructure relating to vulnerabilities in Citrix, Windows IIS web server, Microsoft Sharepoint, and Telerik UI.
Where these attacks fail, they are moving to spear-phishing attacks. Spear phishing is most commonly an email or SMS scam targeted towards a specific individual or organisation but can be delivered to a target via any number of electronic communication mediums. In the spear-phishing emails, the attacker attaches files or includes links to a variety of destinations that include:
- Credential harvesting sites. These genuine-looking but fake web sites prompt targets to enter username and password. Once the gullible target provides the credentials, these are then stored in the attackers’ database and are used to launch credential-based attacks against the organisation’s IT infrastructure and applications.
- Malicious files. These file attachments to emails look legitimate but once downloaded, they execute a malicious malware on the target device. Common file types are .doc, .docx, .xls, .xlsx, .ppt, .pptx, .jpg, .jpeg, .gif, .mpg, .mp4, .wav
- OAuth Token Theft. OAuth is commonly used on the internet to authenticate a user to a wide variety of other platforms. This attack technique uses OAuth tokens generated by a platform and shares with other platforms. An example of this is a website that asks users to authenticate using their Facebook or Google accounts in order to use its own services. Faulty implementation of OAuth renders such integration to cyber-attacks.
- Link Shimming. The technique includes using email tracking services to launch an attack. The attackers send fake emails with valid looking links and images inside, using email tracking services. Once the user receives the email, it tracks the actions related to opening the email and clicking on the links. Such tracking services can reveal when the email was opened, location data, device used, links clicked, and IP addresses used. The links once clicked-on, can in- turn, lead to malicious software being stealthily downloaded on the target system and/or luring the user for credential harvesting.
How do you safeguard against Cyber-Attacks?
The most common vectors for such cyber-attacks are lack of user awareness AND/OR exploitable internet-facing systems and applications. Unpatched or out-of-support internet-facing systems, application or system misconfiguration, inadequate or poorly maintained device security controls and weak threat detection and response programs, compound the threat to your organisation.
Governments across the world are coming up with advisories and guidelines to spread cybersecurity awareness and prevent threats and attacks. ACSC’s Australian Signals Directorates ‘Essential 8’ are effective mitigations for a large majority of present-day attacks. There were also guidelines published earlier this year, specifically with the COVID-19 crisis in mind. The Cyber Security Agency in Singapore (CSA) promotes the ‘Go Safe Online’ campaign that provides regular guidance and best practices on cybersecurity measures.
Ecosystm’s ongoing “Digital Priorities in the New Normal” study evaluates the impact of the COVID-19 pandemic on organisations, and how digital priorities are being initiated or aligned to adapt to the New Normal that has emerged. 41% of organisations in Asia Pacific re-evaluated cybersecurity risks and measures, in the wake of the pandemic. Identity & Access Management (IDAM), Data Security and Threat Analytics & Intelligence saw increased investments in many organisations in the region (Figure 1).
However, technology implementation has to be backed by a rigorous process that constantly evaluates the organisation’s risk positions. The following preventive measures will help you address the risks to your organisation:
- Conduct regular user awareness training on common cyber threats
- Conduct regular phishing tests to check user awareness level
- Patch the internet-facing products as recommended by their vendors
- Establish baseline security standards for applications and systems
- Apply multi-factor authentication to access critical applications and systems – especially internet-facing and SaaS products widely used in the organisation like O365
- Follow regular vulnerability scanning and remediation regimes
- Conduct regular penetration testing on internet-facing applications and systems
- Apply security settings on endpoints and internet gateways that disallow download and execution of files from unfamiliar sources
- Maintain an active threat detection and response program that provides for intrusion detection, integrity checks, user and system behaviour monitoring and tools to maintain visibility of potential attacks and incidents – e.g Security Information & Event Monitoring (SIEM) tools
- Consider managed services such as Managed Threat Detection and Response delivered via security operations (SOC)
- Maintain a robust incident management program that is reviewed and tested at least annually
- Maintain a comprehensive backup regime – especially for critical data – including offsite/offline backups, and regular testing of backups for data integrity
- Restrict and monitor the usage of administrative credentials

In his blog, The Cybercrime Pandemic, Ecosystm Principal Advisor, Andrew Milroy says, “Remote working has reached unprecedented levels as organisations try hard to keep going. This is massively expanding the attack surface for cybercriminals, weakening security and leading to a cybercrime pandemic. Hacking activity and phishing, inspired by the COVID-19 crisis, are growing rapidly.” Remote working has seen an increase in adoption of cloud applications and collaborative tools, and organisations and governments are having to re-think their risk management programs.
We are seeing the market respond to this need and May saw initiatives from governments and enterprises on strengthening risk management practices and standards. Tech vendors have also stepped up their game, strengthening their Cybersecurity offerings.
Market Consolidation through M&As Continues
The Cybersecurity market is extremely fragmented and is ripe for consolidation. The last couple of years has seen some consolidation of the market, especially through acquisitions by larger platform players (wishing to provide an end-to-end solution) and private equity firms (who have a better view of the Cybersecurity start-up ecosystem). Cybersecurity providers continue to acquire niche providers to strengthen their end-to-end offering and respond to market requirements.
As organisations cope with remote working, network security, threat identification and identity and access management are becoming important. CyberArk acquired Identity as a Service provider Idaptive to work on an AI-based identity solution. The acquisition expands its identity management offerings across hybrid and multi-cloud environments. Quick Heal invested in Singapore-based Ray, a start-up specialising in next-gen wireless and network technology. This would benefit Quick Heal in building a safe, secure, and seamless digital experience for users. This investment also shows Quick Heal’s strategy of investing in disruptive technologies to maintain its market presence and to develop a full-fledged integrated solution beneficial for its users.
Another interesting deal was Venafi acquiring Jetstack. Jetstack’s open-source Kubernetes certificate manager controller – cert-manager – with a thriving developer community of over 200 contributors, has been used by many global organisations as the go-to tool for using certificates in the Kubernetes space. The community has provided feedback through design discussion, user experience reports, code and documentation contributions as well as serving as a source for free community support. The partnership will see Venafi’s Machine Identity Protection having cloud-native capabilities. The deal came a day after VMware announced its intent to acquire Octarine to extend VMware’s Intrinsic Security Capabilities for Containers and Kubernetes and integrate Octarine’s technology to VMware’s Carbon Black, a security company which VMware bought last year.
Cybersecurity vendors are not the only ones that are acquiring niche Cybersecurity providers. In the wake of a rapid increase in user base and a surge in traffic, that exposed it to cyber-attacks (including the ‘zoombombing’ incidents), Zoom acquired secure messaging service Keybase, a secure messaging and file-sharing service to enhance their security and to build end-to-end encryption capability to strengthen their overall security posture.
Governments actively working on their Cyber Standards
Governments are forging ahead with digital transformation, providing better citizen services and better protection of citizen data. This has been especially important in the way they have had to manage the COVID-19 crisis – introducing restrictions fast, keeping citizens in the loop and often accessing citizens’ health and location data to contain the disaster. Various security guidelines and initiatives were announced by governments across the globe, to ensure that citizen data was being managed and used securely and to instil trust in citizens so that they would be willing to share their data.
Singapore, following its Smart Nation initiative, introduced a set of enhanced data security measures for public sector. There have been a few high-profile data breaches (especially in the public healthcare sector) in the last couple of years and the Government rolled out a common security framework for public agencies and their officials making them all accountable to a common code of practice. Measures include clarifying the roles and responsibilities of public officers involved in managing data security, and mandating that top public sector leadership be accountable for creating a strong organisational data security regime. The Government has also empowered citizens to raise a flag against unauthorised data disclosures through a simple incident report form available on Singapore’s Smart Nation Website.
Australia is also ramping up measures to protect the public sector and the country’s data against threats and breaches by issuing guidelines to Australia’s critical infrastructure providers from cyber-attacks. The Australian Cyber Security Centre (ACSC) especially aims key employees working in services such as power and water distribution networks, and transport and communications grids. In the US agencies such as the Cybersecurity and Infrastructure Security Agency (CISA) and the Department of Energy (DOE) have issued guidelines on safeguarding the country’s critical infrastructure. Similarly, UK’s National Cyber Security Centre (NCSC) issued cybersecurity best practices for Industrial Control Systems (ICS).
Cyber Awareness emerges as the need of the hour
While governments will continue to strengthen their Cybersecurity standards, the truth is Cybersecurity breaches often happen because of employee actions – sometimes deliberate, but often out of unawareness of the risks. As remote working becomes a norm for more organisations, there is a need for greater awareness amongst employees and Cybersecurity caution should become part of the organisational culture.
Comtech received a US$8.4 million in additional orders from the US Federal Government for a Joint Cyber Analysis Course. The company has been providing cyber-training to government agencies in the communications sector. Another public-private partnership to raise awareness on Cybersecurity announced in May was the MoU between Europol’s European Cybercrime Centre (EC3) and Capgemini Netherlands. With this MoU, Capgemini and Europol are collaborating on activities such as the development of cyber simulation exercises, capacity building, and prevention and awareness campaigns. They are also partnered on a No More Ransomware project by National High Tech Crime Unit of the Netherlands’ Police, Kaspersky and McAfee to help victims fight against ransomware threats.
The Industry continues to gear up for the Future
Technology providers, including Cybersecurity vendors, continue to evolve their offerings and several innovations were reported in May. Futuristic initiatives such as these show that technology vendors are aware of the acute need to build AI-based cyber solutions to stay ahead of cybercriminals.
Samsung introduced a new secure element (SE) Cybersecurity chip to protect mobile devices against security threats. The chip received an Evaluation Assurance Level (EAL) 6+ certification from CC EAL – a technology security evaluation agency which certifies IT products security on a scale of EAL0 to EAL7. Further applications of the chip could include securing e-passports, crypto hardware wallets and mobile devices based on standalone hardware-level security. Samsung also introduced a new smartphone in which Samsung is using a chipset from SK Telecom with quantum-crypto technology. This involves Quantum Random Number Generator (QRNG) to enhance the security of applications and services instead of using normal random number generators. The technology uses LED and CMOS sensor to capture quantum randomness and produce unpredictable strings and patterns which are difficult to hack. This is in line with what we are seeing in the findings of an Ecosystm business pulse study to gauge how organisations are prioritising their IT investments to adapt to the New Normal. 36% of organisations in the Asia Pacific region invested significantly in Mobile Security is a response to the COVID-19 crisis.
The same study reveals that nearly 40% of organisations in the region have also increased investments in Threat Analysis & Intelligence. At the Southern Methodist University in Texas, engineers at Darwin Deason Institute for Cybersecurity have created a software to detect and prevent ransomware threats before they can occur. Their detection method known as sensor-based ransomware detection can even spot new ransomware attacks and terminates the encryption process without relying on the signature of past infections. The university has filed a patent for this technique with the US Patent and Trademark Office.
Microsoft and Intel are working on a project called STAMINA (static malware-as-image network analysis). The project involves a new deep learning approach that converts malware into grayscale images to scan the text and structural patterns specific to malware. This works by converting a file’s binary form into a stream of raw pixel data (1D) which is later converted into a photo (2D) to feed into image analysis algorithms based on a pre-trained deep neural network to scan and classify images as clean or infected.











