The NCSC’s first ‘UK cyber survey’ published alongside global password risk list. The UK government’s cybersecurity organisation National Cyber Security Centre (NCSC) provides cybersecurity support and guidance to the private and public sectors.
The survey identified exploitable gaps in personal level security management. The study was carried out between November 2018 and January 2019 and revealed that 89% of the respondents used the Internet and only 15% acknowledged a greater understanding of personal security measures.
The NCSC also published an analysis of the 100,000 most commonly used passwords that have been accessed by third parties in global cyber breaches. The analysis shows that less than half of the respondents do are not concerned about the strength of passwords for their emails and online accounts. Some examples of commonly used passwords used by people rely on their own names, Premier League football teams, musicians and fictional characters for inspiration.
This general lack of understanding of the cyber world can be harmful to individuals but can be devastating to organisations. A chain is no stronger than its weakest link, and insecure passwords may pose a serious security risk to an organisation. “We rely on passwords in all facets of our online world, so this presents a massive risk to anyone taking short-cuts. Unfortunately, if organisations are not prepared, and allow the use of similarly insecure passwords, the flow on effect of a breach can escalate rapidly” says Alex Woerndle, Principal Analyst Cybersecurity, Ecosystm “The passwords in the above list are very weak. Even without the knowledge provided in the list, a hacker would be able to crack these passwords in seconds with the right tools. Even password complexity cannot always protect an organisation. What about a user that re-uses a complex password repeatedly, and that password is part of a breach? That puts all of the organisation’s logins at risk”.
There are some additional steps that system administrators and IT professionals need to consider when it comes to securing passwords and managing logins.
The global Ecosytsm Cybersecurity & Data Privacy study found the most common controls organisations implement to manage data access.
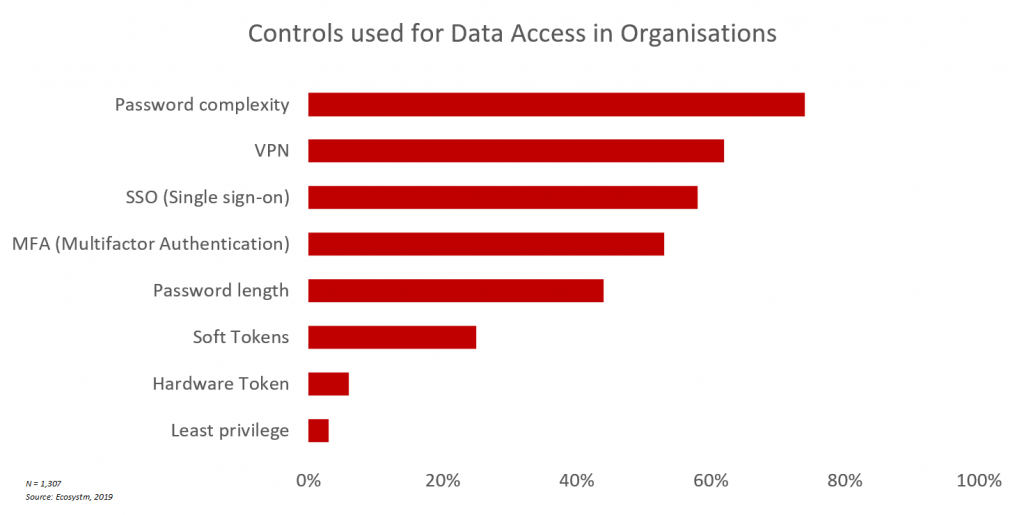
“The main step being used currently is ensuring MFA is enabled wherever possible. While not a perfect solution, it provides a circuit breaker for the most common types of attacks that would get anyone using insecure passwords into trouble” says Woerndle.
The NCSC hopes to reduce the risk of further breaches by building awareness of how attackers use easy-to-guess passwords, or those obtained from breaches and help guide developers and system administrators to protect their users. NCSC has framed guidelines covering multiple aspects of managing and maintaining security on its website.
Ultimately this problem will not go away until we find a genuine replacement for passwords. The pure scale of growth in the number of systems and applications that all users, both at a personal and on a professional level, have access to, makes password management complex and frustrating. While focusing on how to strengthen your passwords and other easy steps to avoid a cyber attack, may be a good start, it will not be enough, as long as systems and applications are dependent on passwords for better security.
The Changing Shape of Asia’s Cybersecurity Landscape
The latest in our Leaders BreakFirst series. Following the launch of our Cybersecurity and Data Privacy study, Ecosystm is delighted to share the insights from almost 7000 deployments globally.Featuring two of Ecosystm’s cybersecurity and data privacy experts on one stage- Claus Mortensen and Carl Woerndle, this session will highlight the findings from our Cybersecurity & Privacy research.
In the last few weeks, there have been announcements in Canada and Denmark on nationwide IoT networks launches. Moving away from pilot projects, test cases, implementations across large factories and campuses or even citywide networks to drive smart city initiatives; these countrywide IoT networks give organisations access to lower cost means to implement large, more integrated, IoT projects.
Sigfox Canada announced the launch of Canada’s first coast to coast low-bandwidth IoT network which is the nation’s first IoT network on such a scale. The network leverages low-power wide area network (LPWAN) technology offering a capacity to support millions of IoT sensors. The solution is anticipated to provide efficient and cost-effective connectivity for businesses looking to adopt IoT technology.
Similarly, Teracom, a Denmark-based telecom operator in partnership with Loriot, (an IoT infrastructure provider) announced an IoT LoRaWAN – Long Range Wide Area Network network in Denmark. We have previously seen the Netherlands implementing a nationwide long range (LoRa) network for IoT and Singtel’s commercially available narrowband Internet of Things (NB-IoT) network in Singapore.
“There is no doubt that services like LoRaWAN will help boost early adoption of IoT services and at this stage, there is a segment of the market which is a good fit. However, the longevity of LoRaWan is less certain. Compared to LoRaWAN, NB-IOT has arguably been too late to the game and it may fail in the short term but may very well win in the long term.” says Copenhagen based Ecosystm Principal Analyst, Claus Mortensen.
Efforts are being made by both the Sigfox and Teracom to enhance the network coverage and quality in the countries. A lot of the focus on IoT in Denmark has been bundled into the future deployment of 5G. However, most IoT applications do not need high bandwidth.
“The issues with large countries such as Canada, Australia, and the US is how do you economically cover large geographic area with a very varied population density? In contrast, smaller countries like Denmark can have a mesh thrown over them very easily” says Ecosystm Executive Analyst, Vernon Turner.
With 5G though, the telecom providers appear to be in a better position as they understand that 5G will be driven by the enterprise segment in the short to medium term and they have been actively involved in developing use cases from the get-go which also includes a focus on IoT services.
IoT offers a plethora of opportunities to companies looking to adopt or expand the country-wide networks. Both mature countries and emerging economies are at dissimilar life-cycles in their degree of IoT technology adoption but we expect to witness more technology sharing and network concatenation in the near-future.
AI is powering products, processes, strategies and customer experience in the Banking industry.
The banking industry is all geared up to embrace Artificial Intelligence (AI), to address its business requirements. In general, banks are struggling to implement smart services within their compliance framework, and have an incomplete view of their customer needs from their legacy systems. However, the industry continues to be reliant on legacy systems, largely because of the involvement of too many complex platforms, technologies, and systems which make migration or integration cumbersome.
Meanwhile, modern Digital Banks are aligning their services to customer needs by embedding AI and machine learning within their existing systems. The banking industry’s experimentation with AI is opening new opportunities for improving customer experience (CX).
“We are not too far away from a day where traditional enterprise applications are no longer relevant. The purpose of those traditional systems was to simplify, codify, and automate business and customer processes. But in the mid-term future, we will have a time where the entire process is intelligent – where the system/application creates the best business process for the customer on the fly”, says Tim Sheedy, Principal Advisor, Ecosystm.
Elevating CX and Security
Banks are being transformed through AI adoption, especially in areas such as process automation, cyber security (especially in threat analysis and intelligence, and fraud/transaction security) and better information sharing systems for both their corporate and retail customers.
Business Solutions being Addressed by AI in Banking
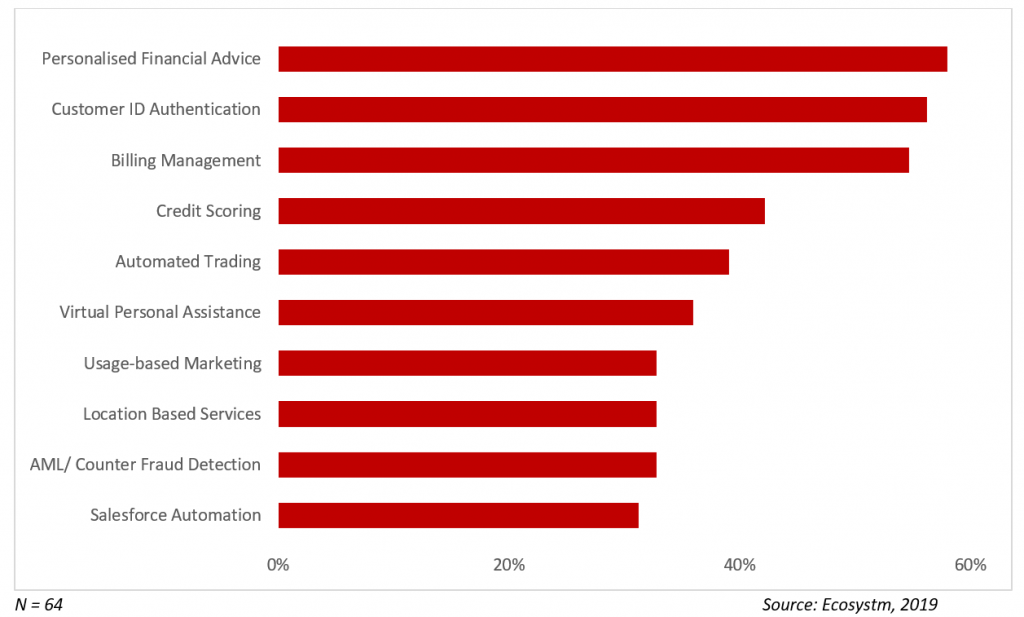
Customer Experience
Customer Service is one of the core banking applications. Adoption of technologies such as virtual assistants and natural language processing (NLP) techniques is redefining CX in the banking industry.
“With emerging technologies setting a new bar for personalisation and value-add, banks looking to stay ahead of the curve simply cannot afford to ignore them,” says Jannat Maqbool, Principal Advisor, Ecosystm.
Personalised financial advice is another area where banks are taking advantage of AI applications. While it might be a perception that AI will reduce the human touch when it comes to CX, in reality, it provides more accurate and timely assistance. For instance, Bank of America has built an AI virtual assistant, “Erica” which actively assists 25 million clients on its mobile platform. Erica searches for past transactions and informs customers on their credit scores and connects with them to provide analytics and information on their account.
Marketing Automation
As profit margins decrease in the Banking sector, and Fintech technologies become more mainstream, banks need to ramp up their marketing initiatives, to remain competitive. AI is helping banks to optimise their marketing dollars. Machine learning algorithms can analyse customers’ entire banking journey involving interactions, transactions, location history, and usage patterns to develop insights and make marketing decisions with unprecedented accuracy. Decisions on a range of marketing initiatives across product improvement, new products and services offerings, and targeted marketing keeping in view customers’ financial goals will be automated. This will impact the profit margin as sales cycles shorten, and customers banking journeys become more satisfying.
Process Automation
There are certain functions in banks which require a lot of manual labour such as billing, generation of reports, account opening operations, KYC, etc. AI is transforming the banking industry with data-driven processes and decision making to automate tasks such as billings, credit scoring, compliance reports and so on. This not only reduces the dependence on tedious manual processes but also creates mechanisms to reduce errors. These errors not only make the organisation less efficient but also has financial ramifications. UBS, as an example, has introduced robots to its workforce, mainly at the back offices, designed to execute more manual and repetitive tasks. This essentially means meeting the right tasks with more speed and accuracy.
Fraud Management
AI improves with data and learns behavioural patterns. Banks are utilising this data or claims management and fraud detection. The AI platform evaluates on certain parameters such as when and how a customer typically accesses services and manage their money – more importantly, how they do not. They are designed to flag transactions with missing information and can alert the bank staff to irregular transactions and suspicious activities to prevent fraud. Increasingly this is evolving a chain of an automated process, without the involvement of banking staff or customer complaints.
Banks have a difficult job delivering better service while remaining compliant, and AI-driven AML and KYC initiatives, helps prevent fraud, and flag suspicious activities such as money laundering.
Market Trends
Current Focus on AI – The banking industry’s focus on customer service and automating manual processes is reflected in the top AI solutions that they are currently adopting. Chatbots and virtual assistants are being improved through natural language generation (NLG) and speech analytics capabilities. Process automation through RPA is being integrated into the organisations’ digital journeys due to its relative ease of deployment and measurable ROI.
Current & Planned Adoption of AI Solutions in Banking
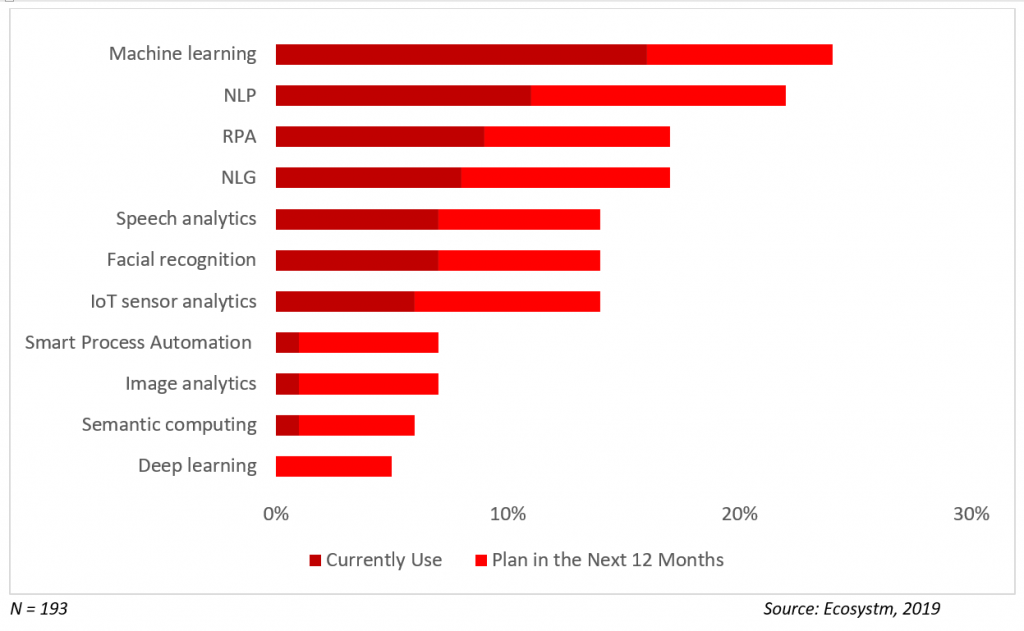
Future Focus on AI – Banks will continue to focus on CX and strengthening the capabilities of their customer service team through AI. Niche solutions such as facial recognition will also improve their front-end operations, especially in customer identity authentication. Banks will also go beyond customer management to asset management, with AI-enabled IoT systems.
What’s Next?
AI is fast evolving and there are some excellent opportunities for banks to explore on what AI has to offer. Banks are working on feeding data into AI systems with advanced algorithms to better understand their customers and improve their services. Banks should focus on getting quality inputs on inquiries, interactions, transactions or another way that can collect insights.
Consumers are looking for operations and systems that are simple to operate and directed towards them. The greatest potential for AI in banking is to deliver personalised and automated services to consumers in a cost-effective and efficient way.
AI is allowing banks to do quicker operations at much lower cost, what remains to be seen is how banks further leverage AI to extend its products and services offerings.
The future of food, medicine, and digital technology has been marked as prime research targets to maintain Singapore’s competitiveness in the coming years. Recently, Singapore Government convened a panel discussion on the Research, Innovation and Enterprise (RIE) 2020 plan where Singapore’s Finance Minister Mr Heng Swee Keat delivered an update on Singapore’s science and technology research plan.
Mr. Heng conveyed that more than S$500 million is set-aside to shape up the artificial intelligence systems and to fulfill the nation’s cyber-security requirements. The fund will also improve Singapore’s supercomputing capabilities and the deployment of automation and robotics.
A further $144 million will be allocated towards food research to increase sustainable urban food production, and another $80 million will be contributed to the cell-therapy research in the biopharmaceutical sector.
How Singapore will benefit in terms of technology from this announcement?
The Government has clearly spent a lot of time to determine how to get Singaporean companies to invest in research that can benefit the country, and identifying areas that the industries can benefit in return.
Investment in Digital Technology
The Government believes that it is important to invest in the areas of Artificial Intelligence, Supercomputing and Robotics and hope that there will be more success stories for these industries. The S$500 million set aside will aim to increase the funding already set back in the RIE 2020 for the Digital Intelligence.
Speaking on the subject, Mervyn Cheah, Principal Advisor ,Ecosystm, says that “The Government aims to entice more Industry to invest in R&D in Singapore. PM Lee has mentioned that the industry today is investing just 1.2 to 1.4 of Singapore’s GDP in R&D in Singapore, and he wants the Industry to do more. It is a bit like playing roulette you place your bets on many numbers and hope that one of them will blossom and give you the returns and success. It is not possible that all R&D will come to fruition practically.”
Scenario for Businesses
The RIE 2020 is an initiative taken by the Singapore Government to make the nation a hub for R&D. By setting aside funds for both local industries and MNCs the government hopes that the industries will be able to invest and grow.
“There are a number of new start-ups being created as Singaporeans start to recognise that the government is putting in more R&D funding. At the same time, existing businesses will expand to take advantage of this announcement” says Cheah.
What to Expect – RIE2020
Currently, the local Industries in Singapore do not have a large appetite for investing in R&D in Singapore although there is a 50% spike from 2016 to 2018. The government’s aim is to invest in the Science, Engineering, and Biomedical fields industries, with the intent that they can increase their revenue.
Cheah says “the Government is looking at getting Multi-national Corporations (MNCs) to invest in Singapore for their R&D and believes that the industry can do better. So, the Government (National Research Foundation under the Prime Minister’s Office) is pushing the Industry to do more, and on their pro-active part, they have announced setting aside another S$700 million R&D funding to A*STAR, to the Singapore Food Agency, and other R&D agencies, with the hope that the Industries will further spend R&D in Singapore.”
Autonomous vehicles are a natural component of any smart city/smart transportation strategy. City traffic congestion is a well-known problem that can make or break the reputation of a city as being a liveable place. Any major initiative that makes moving the public from one point to another in the most efficient manner is good for everyone.
Singapore has always taken steps to improve public transport and provide a viable alternative to owning a vehicle. These initiatives are renowned worldwide, and Singapore’s public transport and road management held up as best practice globally. To enhance commuters experience Singapore has already introduced smart bus stops a year ago and in the future, we may see a complete ecosystem of smart bus stops.
Following a similar theme, a number of projects have been announced in the last few years to take public transport to the next level. Singapore is also embracing autonomous vehicles, with a number of initiatives launched over the last few years. Singapore’s Nanyang Technological University (NTU), and Volvo Buses in partnership with Singapore’s Land Transport Authority (LTA) have launched the world’s first full-size autonomous electric bus stretching 12 metres long with a capacity of around 80 passengers. As a part of public trials, the bus is being tested on fixed routes and services will subsequently extend to the public roads.
The buses are equipped with autonomous driving functionality and provide a quiet, emission-free operation and save up to 80% energy compared to an equivalent sized diesel bus. The bus has advanced features such as light detection and ranging sensors (LIDARS), 3D stereo-vision cameras, and an advanced GPS system that uses real-time kinematics which are connected to an inertial management unit (IMU) to measure the lateral and angular and help in navigation over varied terrains.
Real-world concerns for autonomous buses
The bus has undergone preliminary rounds of rigorous testing at the Centre of Excellence for Testing and Research of Autonomous vehicles at NTU (CETRAN). Confirming maximum safety and reliability, the AI system in the bus is protected with industry-leading cybersecurity measures. Speaking on the subject, Ecosystm’s Executive Analyst, Vernon Turner says that “While safety will always be the leading concern, software and hardware security and reliability will be the underpinning forces that make passengers comfortable with autonomous vehicles. The autonomous vehicle’s ecosystem is complex because the reliability of the vehicle is as much an IT and telecom function as it is an industrial manufacturing process.”What
What do Autonomous buses mean for the industry and how will it benefit the industry?
In most cities, public transportation is conducted in ‘restricted’ lanes (especially for buses), and therefore the routes are often consistent, and the operating environments can be continually monitored and matched for exceptions. The legislation for autonomous vehicles has to be carefully crafted to ensure the highest level of public safety while not stifling innovation.
“The digital impact of autonomous buses opens up a host of new services both for the transportation companies as well as the passengers. I wouldn’t be surprised to see transportation companies being sold public transportation vehicles such as buses as ‘buses as a service’ whereby the vehicles are managed in a 100% OPEX manner and have no CAPEX value! There will be a rich source of operational data from IoT-based sensors that the suppliers and the transportation companies will agree to pay for multiple usage metrics,” Says Turner. “Innovation will also appear in the transportation workflow – thus creating investment in real-time mapping, high-speed telecom networks, and in the case of an ‘EV’ or electric bus, the charging/recharging energy network. As the IT infrastructure is implemented, I would anticipate efficiencies in bus usage would increase with better route management. Passengers, buses and the routes become integrated into a better passenger and city life experience.”
To that end, the industry is excited to use public transportation for their autonomous vehicle programs.
Environmental Impact of autonomous buses
The government of various nations is spending enormous amounts on reducing emission and buses are inherently inefficient when it comes to diesel consumption, only getting between 1 to 4 kilometres/litre. “Switching them to electric vehicles while at the same time running them as autonomous vehicles in a very efficient manner could have a marked impact on the environment,” says Turner. “While the heavy workload for buses might quickly drain any EV batteries, having them work in a fully autonomous, dedicated bus lane should mitigate that energy cost. This could make it a feasible alternative to combustion engine vehicles while at the same time being highly friendly to the environment.”
AT&T became the first North American operator to join the ranks of the Global Telco Security Alliance formed by Singtel, Etisalat, Softbank, and Telefónica. The alliance which was formed last year in April 2018 in a pact to amalgamate the capabilities of telecommunications operators on security aspects and fight collectively against cyber attacks.
AT&T joined as an equal member with other founding members of the group. Over the past few years, AT&T has been building its cybersecurity capabilities and has recently acquired AlienVault– a commercial and open source developer – to offer a platform that integrates and automates point security products to manage cyber attacks. AlienVault has been rebranded as AT&T Cybersecurity, and includes consulting and managed security services. Similarly, at the end of 2018, Singtel revealed the brand ‘Trustwave’ that combines the capabilities of partners such as Optus and NCS, to provide a comprehensive security suite and services to help organisations fight cybercrime.
With the rising risks of cyber-attacks, these initiatives are providing a synergistic front and helping organisations to analyse and act faster against cyber threats. The alliance plans to expand its global footprint and span across APAC, Europe, MEA and America.
Speaking about the alliance, Alex Woerndle, Principal Analyst Cybersecurity, Ecosystm says that, “Similar collaborations exists within other industries already – most commonly they use regular information-sharing sessions with the collective security teams to discuss what each is experiencing, what strategies and tactics have worked or failed, and provide details on the type and nature of attacks. The telcos – at a minimum – should be collaborating at that level. But given the global nature of this alliance, they will need to consider how they can aggregate threat information and share it in a more agile way on a day to day, hour to hour and minute to minute basis.”
The alliance accounts for a significant percentage of the overall traffic and is a tangible example of companies taking steps to fight cyber attacks. “As the threat landscape continues to expand there is an opportunity to broaden the intelligence – sharing what they collectively gather and analyse, to strengthen the defences of the broader market not just in their local geographies, and to impact globally”, says Woerndle. “Think of the immense opportunities to share intelligence gathered collectively by all the major telcos, to proactively prevent attacks on their clients – from other enterprises down to small/medium businesses and consumers. Law enforcement could benefit from the global telco collaboration, also”
We’ve been hearing about Augmented Reality and Virtual Reality for a while now. The future of the virtual world is being built today and as AR/ VR become more mainstream and prices decrease, there’s a new technology trying to fit in somewhere, to perform its magic – Mixed Reality.
What is Mixed Reality, however? Is it just another marketing jargon for the same technology wrapped in new covers?
Before diving deep into mixed reality , let us revisit the fundamentals of the virtual world technologies.
Virtual Reality
Virtual Reality replaces your world with a digital world and has been in the market from some time. VR is achieved through the use of a virtual headset which in combination with an image/video (either through phone or direct source connection) produces multi-projected environments with lenses to generate a virtual environment. It provides real-world experience and some of the use cases include driving and flight simulators, virtual tours, 360° videos, and in healthcare, training and more. There are a variety of VR devices available today from known manufacturers such as Facebook ‘s Oculus, Samsung Gear, Google Cardboard, Sony’s PlayStation VR, HTC Vive and others, offering different features, and addressing different requirements and comfort.
Augmented Reality
Augmented Reality is a direct or indirect view of physical world elements augmented through the digital environment. Basically, AR supplements the real world with digital objects of any sort. It is already being used in the Aviation industry, where data is displayed within the pilots’ helmet view as they fly.
An example of AR is Ikea’s mobile app developed specifically to showcase its furniture catalogue – A piece of furniture such as a dining table or a television cabinet can be virtually displayed as a digital image overlaid on top of the real image of your home space. This lets you easily judge the appearance or gauge how it will fit in your home space.
Some of the more well-know AR devices include Google Glass, Microsoft HoloLens, and Sony Leap. AR is also used in mobile gaming applications such as Pokemon GO, where virtual creatures are placed into the real world.
Where does Mixed Reality fit?
As an independent notion, Mixed Reality combines the best of both worlds and covers all the possible disparities of the physical and the simulated worlds.
Also known as hybrid reality, Mixed Reality covers the spectrum where physical and digital objects co-exist and interact in real time. Somewhere, between AR and VR, there is an overlap between the physical and the virtual worlds – that is where Mixed Reality comes in.
Both AR and VR require users to step out of their own reality – or to use another device (typically a smartphone) to access digital or “virtual” content. The experience is either all-encompassing (with VR – where the content overrides your current reality), or underwhelming (with AR – where the content is limited, does not understand your current reality and/or is at arm’s length on a relatively small screen).
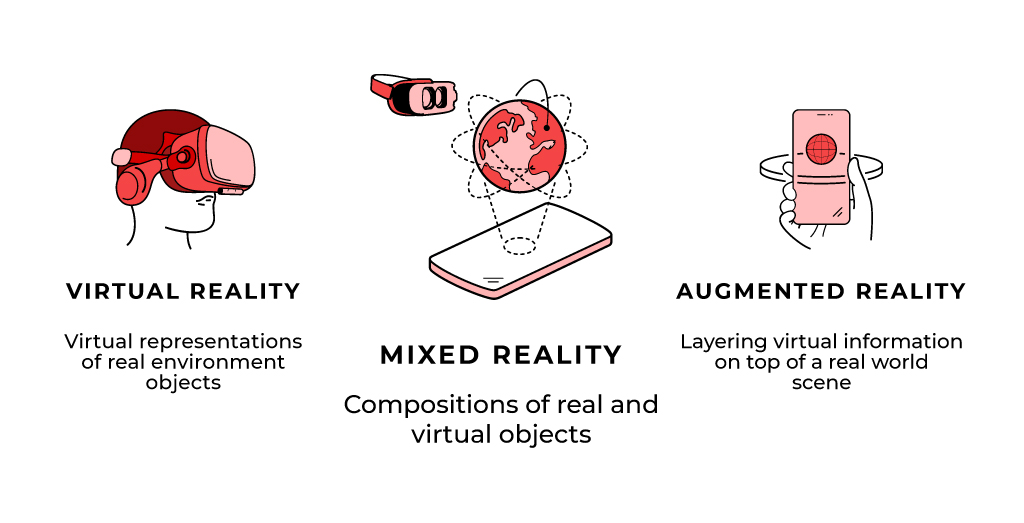
Mixed Reality is designed to add digital assets to your current environment. It adds to the current environment in a natural way that gives the user benefits that non-users would not have.
For businesses, Mixed Reality can offer the most benefit and potentially offer limitless opportunities. Defining the polar ends of AR and VR spectrum Microsoft introduced Hololens in late 2016 as a groundbreaking device and showcased capabilities blending the real and virtual world. Despite being a promising product, there have been hiccups such as a limited field of view (FOV) restricted to only 30°, scaling and sizing holograms and others.
Learning from the failures, Microsoft recently released a new version of its Mixed Reality device – the Hololens2. Microsoft’s Hololens2 takes Mixed Reality beyond niche use cases using more natural gestures, a larger FOV and a multi-user environment – powered by Azure Mixed Reality services.
Mixed Reality in the Enterprise
The use cases of Mixed Reality are many and as the continuum builds, the testing, adoption and deployment cases will become wider. Microsoft’s device is not aimed for the consumer market and is primarily targeted towards business use cases.
Tim Sheedy, Principal Advisor, Ecosystm, believes, “Most of the short and medium-term use cases are really suited to businesses. There are definitely some longer-term opportunities for consumers, but that will require substantial miniaturisation of the hardware and change of form factor. Current MR systems won’t become mainstream devices in the consumer market.”
With Mixed Reality in the play, organisations will be able to explore newer ways of doing things:
Training. Training is a perfect use case. If you can imagine taking a typical guided software where tips pop up on a screen (such as “click this button to personalise your experience, click here to see current leads, click here to add an opportunity) and move this training to the real world (this lever shuts down the machine, this valve reduces pressure etc) then you can get an idea of what is possible.
Engineering. This applies to any job that requires engineers or repairers to work on equipment, where they can be guided through a fix. Any sensor that sends information back to a computer can now be visualised – a mechanic may look at a car and see green for all the components operating within standard range and red for those that need attention or repair.
Construction. A construction worker or site manager can see the entire building or components of the building in advance and make plans for the location of materials, staff, safety etc.
Graphics Designing. A designer can picture how a new product might look in an environment and can design the product with respect to the actual surroundings.
Healthcare. A surgeon could have a CT or MRI scan overlaid onto the patient as they operate to ensure they are targeting the right area.
Anywhere that digital assets or information can assist a worker or drive a more effective, faster or safer outcome are all potential use cases for Mixed Reality services.
A Look at the Field
The theory behind Mixed Reality is that it adds to the user experience in a natural way. Organisations are exploring opportunities to leverage these technologies in the real world. Despite numerous use cases and de facto descriptors, the technology cannot be manifested until it comes to real use.
“Mixed Reality will be a success when it is seamless to use for the first line workers – when it doesn’t feel like a computer you wear on your head!” says Sheedy. “You should be able to interact with these assets in a standard way – and this is where Hololens2 is a big step above the first iteration – as it will allow more natural interactions with the digital objects – you push something or turn something and it moves, versus the “finger click” approach of the first version.”
Imagine your first day at work at a new employer, and instead of a person showing up to give you the tour, you put on a Mixed Reality device (standard or industrialised for those in mining, construction etc) and you are given a tour with virtual overlay and audio guidance.
Sheedy believes that “Mixed Reality may never be a mainstream technology – well not in our generation at least. But that doesn’t mean it won’t be a commercial success. If it is easy to deploy, manage, use, and code for and makes financial sense for businesses to deploy them then these devices will be used. The previous Hololens had commercial users – but Hololens2 should see more success as it is a better solution that can help businesses overcome even more challenges.”
The longer-term success of Mixed Reality will be how well it works with existing software platforms out-of-the-box. Support by SAP, Oracle, Salesforce, IBM and others will help to drive adoption.
How is it going to evolve in the future?
At present, the mobile device is the interface of choice for consumers and workers. But voice is quickly taking off (e.g. Google Home ). Mixed Reality adds an extra impetus to devices that are looking to supplant the smartphone as the interface to information, entertainment and data.
The longer-term future will likely see the emergence of standards that deliver the right information at the right time on the device of choice – whether that device be one with a screen, a microphone and a speaker (smart speaker like the Amazon Alexa), a screen and a speaker (such as a Hololens device), a smartwatch or another form factor.
“Mixed Reality devices will get smaller, smarter, faster, have better resolution, be more integrated (with cloud services and software platforms) and more integrated with another non-screen interface” says Sheedy.
“Access to the right information at the right time on the best device that drives the right outcomes will be the ultimate goal – and Mixed Reality will be one of the form factors that help consumers and businesses achieve that goal.”
It’s still too early to tell the direction this technology will take but the promises surely appear to be overwhelming. What do you think will be the future of Mixed Reality – is it another gimmick or will it really live up to its promise?
Let us know in your comments below.
Vodafone and Arm announced a strategic agreement at MWC19 to work on simplifying IoT services and reduce the costs confronted by the organisations on the implementation of IoT.
The Vodafone-Arm agreement expands on the previous collaboration which was on integrated SIM (iSIM) technology, a system on chip(SOC) design which can be reprogrammed with respect to the requirements. The iSIM allows customers to remotely provision and manage IoT devices across the globe which proposes reduced complexities and offers significant cost reduction.
To carry on the existing relationships this agreement is expected to bring Vodafone’s IoT global platform and Arm’s IoT software services to offer organisations a world of connected systems. This characterises a major initiative enabling a wide ecosystem of manufacturers to tap into the potential of trillions of connected devices.
Speaking on the subject, Ecosystm’s Executive Analyst, Vernon Turner thinks that “this announcement will help customers who look to and need a cellular-based IoT solution. Traditionally, mobile devices require a physical process to change their SIM (Subscriber Identity Module) card when there is a change of ownership or carrier, but in a world of trillions of connected devices, this is just not practical.”
Arm’s announcement of its iSIM is the latest in a series of announcements to resolve the size, cost, and scalability of SIM cards. SIM cards are critical for secure identity so the challenge has been to create a cost-effective IoT System On Chip (SOC) that has the SIM function embedded on it. Through its Kigen product family, Arm’s tech buyers will be able to build solutions on the latest cellular standards and specification suitable to run on 5G and backward compatible networks.
Vodafone’s customers will now be able to create a cellular-based IoT solution that can be continuously connected and deployed globally, giving them better investment protection and reduced operational costs. In addition, customers will have the choice of managing these devices through a ‘single pane of glass’ on either Vodafone’s IoT platform or Arm’s Pelion IoT Platform.
“Any time complexity is removed from an IT or mobile solution, customers respond by deploying and using that solution more” says Vernon. “ SoC-based solutions tend to have more functionality that allows for innovation, so we should expect to see an uptick in cellular-based IoT deployments”
The cyber world is ever growing and in this vast world, no business is 100% safe & insured against cyber attacks. With so many threats out there incurred every minute, it is hard to detect each one and prevent them all. In this world of disruptive technology if organisations want to remain competitive, keeping their IT infrastructure security up-to-date is a must.
The Government, cybersecurity experts & other groups are taking various initiatives to spread awareness on cyber attacks but despite these attempts, organisations fail to take their cybersecurity seriously, we may say this is due to lack of awareness, increase in expense or companies simply not wanting to take the pains to prevent breaches.
“When things are going well, it is hard to sell the message of security to stakeholders and get support from across the business. When things are not going so well (e.g. you’ve had a breach), it means high pressure and a lot of focus on your performance” says Alex Woerndle, Principal Analyst Cybersecurity, Ecosystm.
Cyber attacks happen without notice. While there are many cyber experts present to help and provide consultation to the organisations, knowing beforehand about the attacks and strengthening your cybersecurity will safeguard you against serious ramifications.
Let’s Understand – What is a Cyber Attack?
A cyber attack is a deliberate attempt by an individual or a community working together to tap into an existing or a newly discovered vulnerability in the system, network, firmware or software resulting in complete control or gaining information from the victim’s system. While measuring the ill-effects of a cyber attack, we can say that with access to critical data one can exploit sensitive information, identity and may cause serious damage to an organisation or personal identity. Sometimes, a cyber attack is also referred to as computer network exploitation (CNE) or a computer network attack (CNA).
The other common terms used in association with a cyber attack are threat, vulnerability, and risk. Often these terms are mingled together in our day-to-day usage, but they all mean something different. Let’s try to uncover the basic difference between a threat, a vulnerability, and a risk.
A threat can be explained as an activity to exploit a weakness in a system, to cause harm or reveal the underlying assets. It always involves a person responsible for performing threat actions to impact the system’s security known as a threat actor.
A vulnerability is an unknown system flaw or a known weakness that could potentially be exploited by a person also known as a hacker. In other words, it can be known or unknown issues within a system or its software that can be exploited by hackers.
Together, when a threat acts and exploits a vulnerability, this may result in the development of a situation known as a risk. A risk could lead to potential loss or damage to a business.
Understanding threats, vulnerabilities, risks and other components will help you to act against cyber attacks but this may raise another question on why someone would try to harm your business.
So Why do Cyber Attacks Happen?
The people behind a cyber attack could be hackers, a team or a dark web organisation who work with an ulterior motive to commit a digital crime or to gain access to one’s system through a cyber attack. Collectively we may refer to them as cyber criminals. Cyber criminals try to identify vulnerability to crackdown a system.Below are some of the common reasons why a cyber attack happens.
Financial Gain
This is one of the most well-known types of cyber crime. The motive of cyber criminals here is to get easy access to money and the ways they make this happen is through frauds, demands, data breaches or direct attacks. What attackers try to steal are the business’ financial details or sensitive data/intellectual property, customer financial data or databases, staff or client credentials. By gaining access to these, the attackers get in a position to easily access a secured system and exploit it for their financial gains.
Hacktivism – Political or Social
Hacktivism is an activity involving anonymous organisations breaking into an organisation’s IT infrastructure for political or social reasons. Hacktivists mount cyber attacks to access information that can damage the intended target or perform activities to hurt or lower the reputation of certain bodies. Government and political bodies are often the targets of hacktivism.
Intellectual Challenge
Cyber world experts are sometimes challenged by the thrill of hacking or may develop a personality living in a virtual world pushing them to hack into a network with an intention of identifying system vulnerabilities. Generally, hackers are referred to as people with bad motives but hackers are not necessarily criminals as some of them help organisations to test systems, recognise backdoors, loopholes or vulnerabilities in a system which is termed as ‘white hat’ hacking. Knowing the vulnerabilities in the existing IT infrastructure and services may protect organisations from some serious future consequences.
Espionage
Stealing classified information, sensitive data or intellectual property from a government entity or a competitive organisation is a common form of espionage attack. The examples of an espionage attack could be stealing trade and military secrets or technologies or potential system flaws which may pose an influential threat to a nation.
Organised Cyber Crime
Digital technology has empowered individuals with some serious fire-power. IMs and chat technology have made it easy for individuals to form teams or an organisation to commit crimes on the web. Sometimes several groups form communities to commit a serious cyber crime – planned, coordinated and conducted together at a macro level.
Disruption
Aiming to disrupt business, or the operations of critical infrastructure, can be undertaken just to demonstrate security weaknesses, the hacker’s general disapproval for the business, or even to cause extensive operational, financial and physical damage to their target.
The Vulnerabilities that a Business can Experience
Data breaches occur every minute and unknown threats and vulnerabilities always pose a risk for a business. To stay protected, it is always better to know and understand the types of threats or vulnerabilities that a business can experience rather than later raising questions on how the attackers got in.
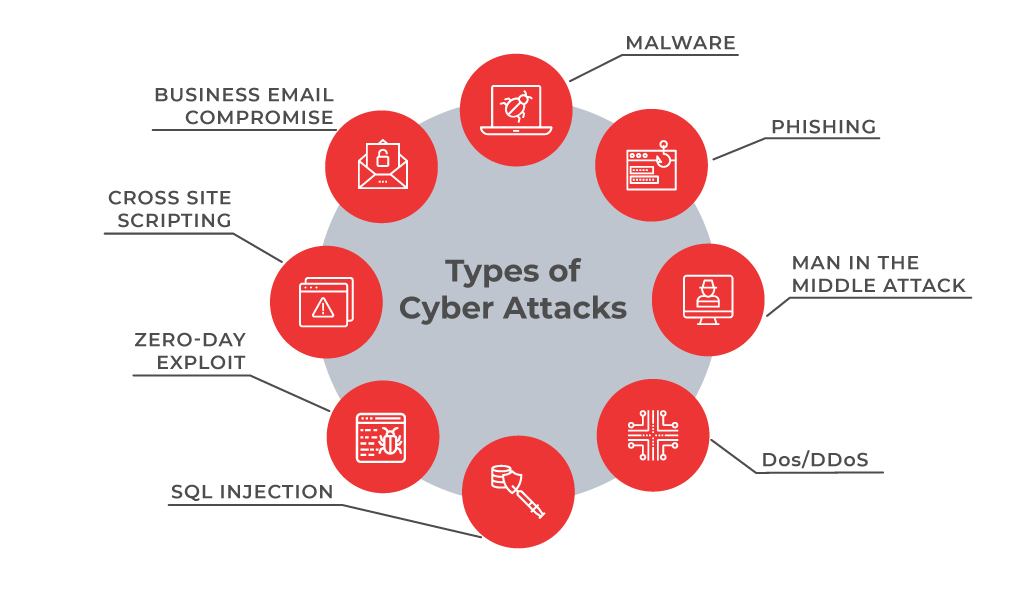
- Malware . A malware is a type of cyber attack where malicious software is installed on the victim’s systems through executable files usually without the user’s knowledge. Malware includes malicious software, including spyware, ransomware, viruses, and worms. After installation, a malware can keep track of the user’s activity or can trigger codes resulting into access to sensitive information, login details, credit cards or intellectual properties by the hacker.
- Phishing. Phishing refers to spoofing or deceptive communications activities performed by the attackers that appear to originate from a credible source such as emails, messages, legitimate websites that are disguised. Through phishing, attackers try to fetch sensitive information, user details, credit card numbers or make fraudulent attempts.
- Man-in-the-middle attack. These attacks happen with relaying or altering the communication channels. This can be communication between organisations and cloud server or over unsecured networks.
- DoS/DDoS. A DoS/DDoS attack aims at flooding the target website with overwhelming traffic to exhaust resources and bandwidth of the system. These are not to bring down a website but to breach a security perimeter and smoke out the online systems. This can reduce a user base or may bring down the entire network.
- SQL Injection. This is injecting a nefarious code or statements into SQL queries or a database server to extract information from the database or to take a data dump of the complete database.
- Zero-day exploit. Zero-day is a software security flaw which is known to the software developers. Attackers try to exploit a vulnerability before a patch or solution is implemented to capture the system with known weaknesses.
- Cross Site Scripting. XSS attacks occur when a web app sends malicious code in the form of a side script to another user thus bypassing access controls of the site to same as the origin.
- Business Email compromise. This is an attack to spoof business emails and gain illegal access to company accounts and ids to defraud the company or its employees.
According to Woerndle, “Nowadays, most of the reported attacks appear to be email-focused either with the intention to encrypt the infected systems to demand payment of a ransom for the keys (i.e. ransomware), to steal credentials (subsequently used for further attacks on other systems and applications) or to steal information that can be sold for profit on the black markets. “
Some of the World’s Largest Data Breaches
Cyber attacks have become a repeated theme every year and we hear quite often about the data breaches. Here’s a visualisation of some of the world’s largest data breaches that have occurred in the past few years.
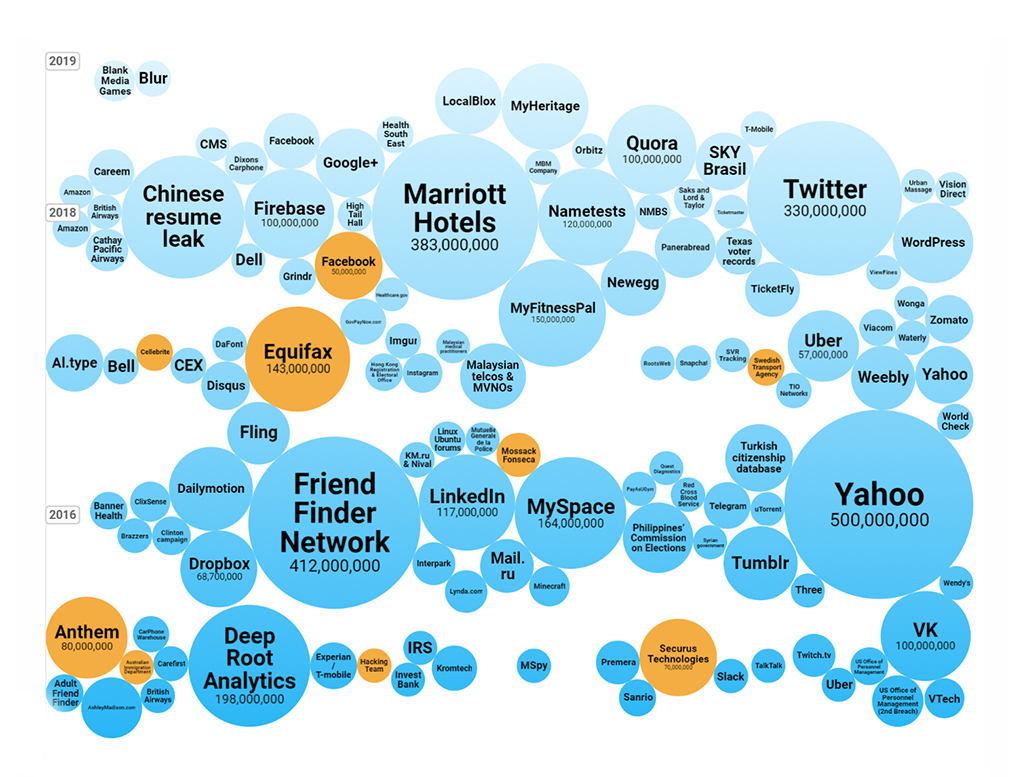
Source: Informationisbeautiful-worlds biggest data breaches hacks
How to Prevent Cyber Attacks?
To minimise cyber attacks, businesses can put some counter-measures in place. It is a smart move to be prepared for serious circumstances and act reactively with security measures.
Secure assets. It is always considered a security best practice to keep your systems and infrastructure updated with latest security patches and updates which are released from vendors or manufacturers on a regular basis.
Conduct threat assessment. Vulnerabilities can arise within your own system or potentially from other sources which are not directly under your control, but they can be identified if you are aware. Perform regular due diligence of your system or network security.
Stay informed on threats. News articles, software companies, cyber security organisations often release information on threats and vulnerabilities that can help you stay informed and act against threats.
Formulate steps to avoid threats. Training and regular information to organisations and employees can prevent many attacks from happening. If your users or employees are aware and informed they can escape the threats. Keep strong passwords, encrypt sensitive information, safeguard accounts, use firewalls to prevent attacks.
Plan an incident response. Create plans and approaches to react against a cyber attack to manage and limit the damage. Always keep your systems backed up online/offline and prepare your IT team to deal with it. You may also take advice or may hire experts to strengthen your infrastructure security.
It is rightly believed that prevention is better than cure. Speaking on the subject, Alex Woerndle, conveys that “the fundamentals are always the most critical starting points – focus on your system and application hardening and patching processes, deploy and actively maintain endpoint protections (e.g. anti-virus), restrict the permissions users have on their devices and invest in regular training and awareness for all staff. Beyond that, ensure all systems are backed up regularly, and deploy (and encourage all users to apply in their everyday lives) multi-factor authentication wherever possible.”
Considering the recent information security breaches, governments around the world are actively forming committees and taking measures to fight against cyber attacks. The governments of various nations have published some guidelines and measures to prevent cyber attacks.
The NIST Cybersecurity Framework, US, provides a policy framework of computer security guidance for organisations to assess and improve their ability to prevent, detect, and respond to cyber-attacks. The framework has been translated into many languages and is used by various governments and organisations across the world.
The Australian Government (via Australian Signals Directorate – part of Defence) has published some very good guidelines – called the ‘Essential 8’ and ‘Strategies to Mitigate Cyber Security Incidents’. The Essential 8 are a very user-friendly guide for businesses and provide protection against 80% of the most common cyber attacks
The UK Government has also come out with very useful information to help organisations.
Recently, Singapore opened a new cybersecurity school and the Ministry of Defence (MINDEF), is planning to hire security experts for their cyber defense strategy.
Cybersecurity is a challenging area and is a very broad discipline that requires skills across technology, forensics, business management, risk and compliance, education, communication, technical support, and others.
Negligence can impair reputation and lead to commercial losses but by understanding the security aspects, one can become aware of the potential threat and be in a better position to counteract it, or even preempt it.
This is just a glimpse to give you some insights into areas of cybersecurity and what goes under the surface. For specific details, you may get in touch with us or speak with a cybersecurity expert.