Authored by Alea Fairchild and Audrey William
Video conferencing company Zoom hosted its virtual Zoomtopia user conference lasts week. Given the attention the company has received as the de-facto standard video communication service for the many stranded work-from-home folks, Zoom has been using the event to launch a number of new products. This includes bringing into general availability its OnZoom events platform and marketplace, and introducing Zapps which brings apps from other providers into the Zoom experience.
ZaaP!
In this age of work-from-home connectivity, we are all asked to multi-platform depending on customer preference, company standards and choice of scale-out from a licensing perspective. But will video-led unified communications help position Zoom to be the infrastructure platform of choice of the workforce? Will Zoom as a Platform (ZaaP!) become a well-used phrase to discuss unified collaboration infrastructures?
The agenda of Zoomtopia, covering healthcare, government, financial services, sales engagement, blending learning in education, mindfulness, CSR, and a whole gambit of other vertical topics, demonstrates a virtual play to highlight use cases where other platforms have focused on the horizontal aspect of productivity.
If you compare Microsoft’s horizontal approach with Cisco’s networking approach, both come from places of productivity. Zoom, being video-led and UC oriented, comes from a place of communication and collaboration. Is collaboration now the real driver for the future of work?
Zoom connects the dots with these two product introductions. Zapps is designed to link productivity tools directly into the Zoom experience for user access to multiple applications from the platform. OnZoom allows hosts to run one-time events or event series with up to 100 or 1,000 attendees (depending on their license) and sell tickets for them. Zoom is also integrating the ability to receive donations through events via Pledgeling. Think a combination of EventBrite meeting GoFundMe meeting Facebook Events.
Zooming Ahead
With the wide variety of activities during this social distancing period around the world that have been Zoom-powered, familiarity leads to experimentation and early adoption.
Without using the word ‘portal’ – Zoom as a Platform (ZaaP!) enforces the drive for a main infrastructure for live interaction via video as the main means of communication over written material or pre-recorded media materials. And many of us are video-led, more than ever.
Zoom is scaling rapidly. When it started out many years ago, they were known as a company that offered video sessions for free and everyone was wondering who this new kid on the block was. In a span of a few years, they have become a powerhouse.
The announcement of OnZoom is something that marketeers will take note of. Many marketeers are Zoom users but could be using other platforms for hosting events. The solution will have in-built tools for selling tickets, scheduling, gifting tickets, promotional activities, etc. Zoom is thinking about video and layering that with added functionality to run a large-scale event. You can see them going into using AI to churn out rich analytics on attendees, attendance rates, effectiveness of campaigns and so on. All of a sudden it is about hosting an event with in-built rich features plus analytics so events can be run better. They are reaching a new audience and making it a fully built all-purpose solution for event organisers and marketeers.
Security Front and Centre
Ecosystm research shows that security has been a key component in organisation’s COVID-19 responses – and rightly so (Figure 1).
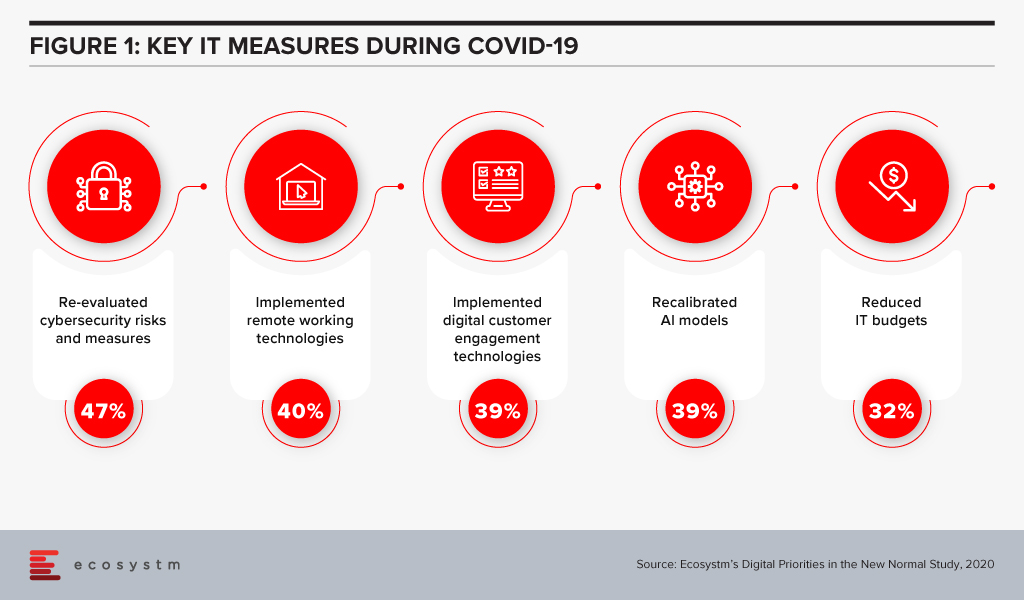
While Zoom received some negative publicity this year around security, they were quick to admit the issues and made incremental changes in the subsequent months including an acquisition. With E2EE, no third party including Zoom is provided with access to the meeting’s private keys. Zoom’s E2EE ensures that communication between meeting participants using Zoom applications is encrypted using cryptographic keys known only to the devices of those participants. Zoom is starting to penetrate larger accounts and the security aspect is important as it is the top of the mind discussion for every business leader.
Ecosystm Comments
With the hybrid work model evolving between home and work, and work patterns changing, one thing that is going to stay is the use of video and collaboration tools and it is only going to accelerate (Figure 2).
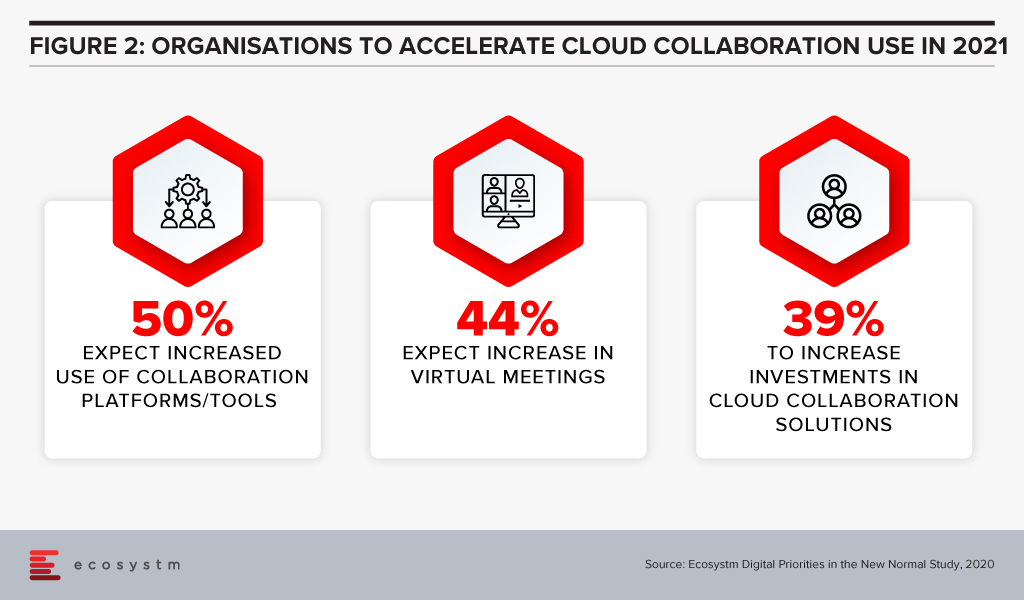
What Zoom is doing well is how they take workflows and APIs seriously, making productivity flow into UC and UX, and not the other way around.
With longer work hours becoming a norm, growing instances of emotional stress and mental fatigue, UX becomes paramount. Knowledge workers want to seamlessly move between workflows and still find the experience simple and not tiring. Zoom is building on that vision as a platform enabler and infrastructure provider.

As organisations aim to maintain operations during the ongoing crisis, there has been an exponential increase in employees working from home and relying on the Workplace of the Future technologies. 41% of organisations in an ongoing Ecosystm study on the Digital Priorities in the New Normal cited making remote working possible as a key organisational measure introduced to combat current workplace challenges.
Ecosystm Principal Advisor, Audrey William says, “During the COVID-19 pandemic, people have become reliant on voice, video and collaboration tools and even when things go back to normal in the coming months, the blended way of work will be the norm. There has been a surge of video and collaboration technologies. The need to have good communication and collaboration tools whether at home or in the office has become a basic expectation especially when working from home. It has become non-negotiable.”
William also notes, “We are living in an ‘Experience Economy’ – if the user experience around voice, video and collaboration is poor, customers will find a platform that gives them the experience they like. To get that equation right is not easy and there is a lot of R&D, partnerships and user experience design involved.”
AWS and Slack Partnership
Amid a rapid increase in remote working requirements, AWS and Slack announced a multi-year partnership to collaborate on solutions to enable the Workplace of the Future. This will give Slack users the ability to manage their AWS resources within Slack, as well as replace Slack’s voice and video call features with AWS’s Amazon Chime. And AWS will be using Slack for their internal communication and collaboration.
Slack already uses AWS cloud infrastructure to support enterprise customers and have committed to spend USD 50 million a year over five years with AWS. However, the extended partnership is promising a new breed of solutions for the future workforce.
Slack and AWS are also planning to tightly integrate key features such as: AWS Key Management Service with Slack Enterprise Key Management (EKM) for better security and encryption; AWS Chatbot to push AWS Virtual machines notifications to Slack users; and AWS AppFlow to secure data flow between Slack, AWS S3 Storage and AWS Redshift data warehouse.
The Competitive Landscape
The partnership between AWS and Slack has enabled Slack to scale and compete with more tools in its arsenal. The enterprise communication and collaboration market is heating up with announcements such as Zoom ramping up its infrastructure on Oracle Cloud. The other major cloud platform players already have their own collaboration offerings, with Microsoft Teams and Google Meet. The AWS-Slack announcement is another example of industry players looking to improve their offerings through partnership agreements. Slack is already integrated with a number of Microsoft services such as OneDrive, Outlook and SharePoint and there was talk of being integrated with Microsoft Teams earlier this year. Similarly, Slack has also integrated some GSuite tools on its platform.
“There is a battle going on now in the voice, video and collaboration space and there are many players that offer rich enterprise grade capabilities in this space. AWS is already Slack’s “preferred” cloud infrastructure provider, and the two companies have a common rival in Microsoft, competing with its Azure and Teams products, respectively,” says William.
The Single Platform Approach
The competition in the video, voice and collaboration market in becoming increasingly intense and the ability to make it easy for users across all functions on one common platform is the ideal situation. This explains why we have seen vendors in recent months adding greater capabilities to their offerings. For instance, Zoom added Zoom phone functionality to expand its offerings to users. Avaya released Spaces – an integrated cloud meeting and team collaboration solution with chat, voice, video, online meetings, and content sharing capabilities. The market also has Cisco as an established presence, providing video and voice solutions to many large organisations.
Organisations want an all-in-one platform for voice, video and collaboration if possible as it makes it easier for management. Microsoft Teams is a single platform for enterprise communications and collaboration. William says, “Teams has seen steady uptake since its launch and for many IT managers the ability to capture all feedback, issues/logs on one platform is important. Other vendors are pushing the one vendor platform option heavily; for example, 8×8 has been able to secure wins in the market because of the one vendor platform push.”
“As the competition heats up, we can expect more acquisitions and partnerships in the communications and collaboration space, in an effort to provide all functions on a single platform,” says William. “However, irrespective of what IT Teams want, we are still seeing organisations use different platforms from multiple vendors. This is a clear indication that in the end there is only one benefit that organisations seek – quality of experience.”
Organisations across the globe, are facing disruption on a scale never seen before, and are urgently seeking ways of remaining viable. Predictably, cybersecurity is a secondary concern and is often handled reactively. To make matters worse, a chronic cybersecurity skills shortage is being made much more severe by the crisis.
Remote working has reached unprecedented levels as organisations try hard to keep going. This is massively expanding the attack surface for cyber criminals, weakening security and leading to a cybercrime pandemic. Hacking activity and phishing, inspired by the COVID-19 crisis, are growing rapidly. Containing and suppressing this cybercrime pandemic is proving to be almost impossible.
Remote working intensifies known threats posed by phishing and ransomware. More alarming are the distinctive cybersecurity vulnerabilities associated with home working including reliance on home Wi-Fi, increased use of unpatched VPNs and devices, and the exponential growth of network access points. These vulnerabilities increase the likelihood of a breach enormously.
Corporate IT is in a very challenging position. It needs to ensure that organisations can operate in a way that they have never operated before, while ensuring that their assets are secure – a very difficult, if not an impossible task for which there is no precedent.
Some important cybersecurity considerations, during and after the COVID-19 pandemic include:
Re-enforce Basic Cyber Hygiene
As massive numbers of people work from home, basic cyber hygiene becomes more critical than ever before. Organisations must maintain awareness of security threats among employees, ensure security policies are being followed and be certain that corporate software is being updated and patched on time. With a dispersed workforce, these basic practices are more challenging, and training becomes more critical. Phishing attacks are often the primary attack vector for malicious actors, so employees must be able to identify these attacks. They increasingly exploit shortages of goods such as protective equipment and sometimes claim to offer official information relating to COVID-19.
Remote employees often access sensitive business data through home Wi-Fi networks that will not have the same security controls – such as firewalls – that are used in offices. There is more connectivity from remote locations, which requires greater focus on data privacy, and hunting for intrusions from a much larger number of entry points.
Place More Focus on Endpoint Security
The unprecedented switch to remote working is radically increasing the number of vulnerable endpoints. Given that endpoints are located at a distance from corporate premises, it is frequently difficult for IT departments to configure endpoint systems and install necessary security software.
It is vital to assess the security posture of all endpoints connecting to the corporate network. This practice enables an organisation to determine whether or not an endpoint requesting to access internal resources meets security policy requirements. It requires the ability to monitor and enforce policy across all devices, while making onboarding and offboarding seamless.
It is essential that endpoint solutions can be rapidly deployed for remote workers, as needed on both personal and corporate devices. Devices used for remote work need much more than the basic antivirus and antispyware protection. Multi-factor authentication (MFA) and on-board endpoint detection and response (EDR) capabilities are crucial.
Be More Selective About How and When Video Conferencing and Collaboration Platforms are Used
Since lockdowns spread around the world, the use of video conferencing and collaboration tools has grown beyond the wildest expectations of suppliers of these tools. The extraordinary growth of Zoom has made it a target for attackers. Many security vulnerabilities have been discovered with Zoom such as, a vulnerability to UNC path injection in the client chat feature, which allows hackers to steal Windows credentials, keeping decryption keys in the cloud which can potentially be accessed by hackers and gives the ability for trolls to ‘Zoombomb’ open and unprotected meetings. Zoom has so far managed to augment its security features in part by its recent acquisition of Keybase, a secure messaging service.
Switching to an alternative video conferencing platform will not necessarily offer greater levels of security as privacy is typically not a strength of any collaboration platform. Collaboration platforms tend to tread a fine line between a great experience and security. Too much security can cause performance and usability to be impacted negatively. Too little security, as we have seen, allows hackers to find vulnerabilities. If data privacy is critical for a meeting, then perhaps collaboration platforms should not be used, or organisations should not share critical information on them.
Protect all Cloud Workloads
In today’s remote working paradigm, cloud computing is being used more than ever. This frequently exposes organisations to risks that are not adequately mitigated.
Organisations typically need to manage a mix of on-premises technology together with multiple clouds, which are often poorly integrated. These complexities are compounded by the increasing risk from cyberattacks associated with cloud migration and hybrid cloud implementations. In cloud environments, the leading cybersecurity risks include insecure interfaces and APIs, data breaches and data loss, unauthorised access, DDoS attacks, and a lack of a unified view of assets.
Protection requirements for securing hybrid multicloud environments are evolving rapidly. In addition to tightening up endpoint security, organisations must also place greater emphasis on cloud workload protection. Cloud security solutions need to offer a unified and consistent view across all physical machines, virtual machines, serverless workloads and containers, used by an organisation.
Amend Incident Response Plans
It is the containment of breaches that often determines the success of security policies and procedures. Basic cyber hygiene as well as changes to IT architecture, such as micro segmentation, play an essential role in breach containment. But incident response plans also need to be made relevant to the current pandemic scenario.
Employees and IT teams are now working in a completely different environment than envisaged by most incident response plans. Existing plans may now be obsolete. At the very least, they will need to be modified. Usually, incident response plans are designed to respond to threats when most employees are operating in a corporate environment. This clearly needs to change. Employees need to be trained in the updated plan and know how to reach support if they believe that a security breach has occurred in their remote location.
Critically, new alert and warning systems need to be established, which can be used by employees to warn of threats as well as to receive information on threats and best practices.
Organisations are struggling to keep the lights on. In this battle to remain operational, cybersecurity has been taking a back seat. This cannot last for long as the deluge of new vulnerabilities is creating easy pickings for attackers. Cyber hygiene, endpoint security, cloud security, security policies and incident response plans must be continually reviewed.
Click here to download the full report ?





